Microsoft released Windows 10 KB5017308 & Windows 11 KB5017328 on September 2022 Patch Tuesday. 2 Zero-Day vulnerabilities CVE-2022-37969 & CVE-2022-23960 are fixed and 1 Actively Exploited with the September patch Tuesday.
One of the updates from last month caused some sleepless nights for the Workplace support team. August 2022 patch KB5012170 caused Bitlocker recovery key screen prompt issues Error 0x800f0922. This is impacting all Windows 10, 11, and Server Operating Systems.
Another pressing issue for Windows 11 users is a sign-in issue when they try to signin with a newly added Microsoft account after installing KB5016691, and this issue is fixed with Sept CU. Another issue recently mitigated by Microsoft is the new Daylight Savings Time in Chile.
IE mode tabs in Microsoft Edge might stop responding issue is resolved with September 2022 Cumulative Updates. Microsoft also fixed (Sept 2022 LCU) this issue with LSASS (Windows Local Security Authority Subsystem Service) – Explained in CVE-2022-30166.
Windows 11 Windows key + h to open voice typing issue is also fixed with a server-side fix as per Microsoft. More Details are available at WI430063.
2 Zero-Day Vulnerabilities – Fixed & 1 Actively Exploited
As per Microsoft, there are 2 zero-day vulnerabilities fixed and 1 Actively Exploited as part of September 2022 Patch Tuesday. CVE-2022-37969 (Windows Common Log File System Driver Elevation of Privilege Vulnerability) and CVE-2022-23960, Cache Speculation Restriction Vulnerability, are the two zero-day vulnerabilities.
- CVE-2022-37969 – (Actively Exploited = YES) – Windows Common Log File System Driver Elevation of Privilege Vulnerability
- CVE-2022-23960 – (Actively Exploited = NO) – Cache Speculation Restriction Vulnerability
You can check the list of September 2022 CVE Vulnerability Details with Exploitation More Likely in the below section of this post. Microsoft has not yet released any fix for these vulnerabilities, which is why this is categorized as Zero Day Vulnerability. Watch this space for more updates on this.
Improvements with September Patch Tuesday CU KB5017308 and KB5017328
The following is the list of fixes and enhancements documented for the Windows 11/10 operating system with September 2022 Cumulative Update KB5017308 and KB5017328.
The September 2022 CU enables the feature that gives the ability for IT admins to add languages and language-related features remotely. The admins can now manage language scenarios across several endpoint managers.
The size limitation on SMB compress on a single file is removed now. Compress a file regardless of size if you have configured Server Message Block (SMB) Compression. More Details – Configure Windows 11 SMB Compression Improvements to Compress File Aggressively.

There are Enhancements to Microsoft Defender for Endpoint. With this September Cumulative Update, MDE can identify and intercept ransomware and advanced attacks.
Fixes with September 2022 Cumulative Update KB5017308 and KB5017328
Look at the fixes released with September 2022 patch Tuesday Cumulative Update KB5017308 and KB5017328 for Windows 11/10 devices. Note that some fixes only apply to Windows 11 because new features are only available for Windows 11.
| Fixed Issues | Windows 10/11 | Remark |
|---|---|---|
| known issue that causes Microsoft Edge to stop responding when you use IE mode. | Windows 10 and 11 | More details on the issue. |
| When using Windows key + h to open voice typing, you might receive an error. | Windows 11 | Server Side FIX is implemented |
| Fixed the USB printing issue that might cause your printer to malfunction after you restart it or reinstall it. | Windows 11 | This is only applicable to Windows 11. |
| Fixed the issue that prevents Windows 11 SE from trusting some Microsoft Store applications. | Windows 11 | This issue might prevent Windows 11 from downloading the untrusted app. |
| Bluetooth Audio headset issue. | Windows 11 | Certain Bluetooth audio headsets stop playing after a progress bar adjustment. |
| Virtualized App-V Microsoft Office applications from opening or causing them to stop working. | Windows 10 and 11 | Microsoft Office App-V app issue is fixed. |
| It was fixed the issue that degrades BitLocker performance. | Windows 10 and 11 | Bitlocker issues – The recovery key PIN prompt is a different issue. |
| Fixed the Rsop.msc tool stopped working when it processes 1,000 or more “File System” security settings. | Windows 10 and 11 | The resultant Set of Policy tool issue is fixed. |
Known Issues from August 2022 Cumulative Update and Status
Check the current status of known issues after the last patch update on August 2022 CU. There are only two issues that are pending/outstanding, as you can see below. There is only one outstanding known issue with Windows 11/10.
| Known Issue | Status | Originating KB | Originating Build | Originating Date | Resolving KB | Resolved Date | Last Updated |
|---|---|---|---|---|---|---|---|
| Unable to sign in after adding a new Microsoft Account user in Windows | Resolved (with KIR) | KB5016691 | 22000.918 | August 26th | N/A | N/A | Sept 8th, 2022 |
| An update might fail to install and you might receive a 0x800f0922 error | Investigating | KB5012170 | 22000.850 | August 9th | N/A | N/A | August 13, 2022 |
Deploy Windows 10/11 September Patch Tuesday Cumulative Updates using SCCM and WSUS
Let’s check how to Deploy Windows 10 KB5017308 and Windows 11 KB5017328 September Cumulative Updates using SCCM/WSUS. You can deploy Windows 10/11 September 2022 CU KBs using Intune or SCCM.
Using the following methods, you can create a monthly patch package for September 2022. You can also search with Windows 11 LCU for September 2022 KB5017328. The easiest way is to check from the SCCM admin console.
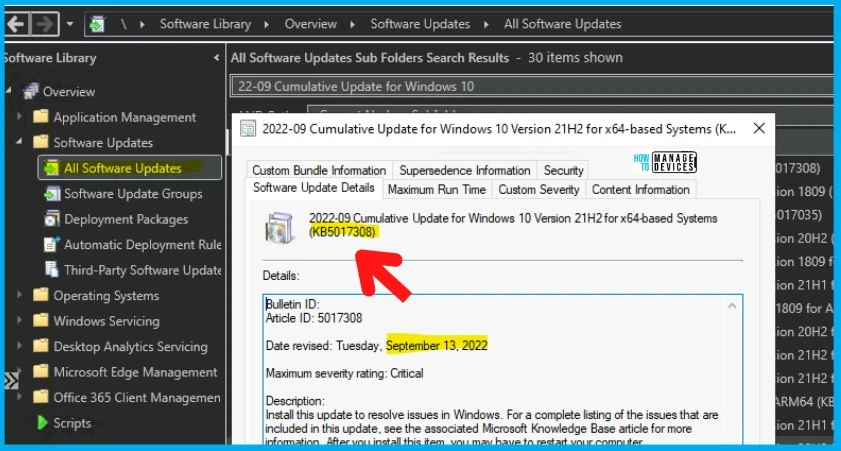
NOTE! – You can verify the Windows 10 versions (OS Builds 19042.2006, 19043.2006, and 19044.2006) and Windows 11 version 22000.978 after installing September 2022 Latest Cumulative Updates.
- Navigate to \Software Library\Overview\Software Updates\All Software Updates.
- You will need to initiate a WSUS Sync from the All Software Updates node (Right-click on the node and initiate the sync).
- Search with the following KB5017308 and KB5017328 Numbers.
- Or you can search with 22-09 Cumulative Update for Windows 10 and Windows 11, as shown in the below screenshot.
- How to Create Deploy New Software Update Patch Package Using SCCM | ConfigMgr
- SCCM ADR Automatic Deployment Rule Creation Process
- ConfigMgr Software Updates Troubleshooting Tips | Fix Installation Issues
The following table gives details of all the KBs articles released on 13th September 2022.
| Title KBs articles released on 13th September 2022 |
|---|
| 2022-09 Cumulative Update for Windows 10 Version 21H1 for x86-based Systems (KB5017308) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 10 Version 20H2 for x64 (KB5017498) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 10 Version 21H1 for ARM64 (KB5017499) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 11 for ARM64 (KB5017497) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 10 Version 21H2 for x64 (KB5017500) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 10 Version 21H2 for ARM64 (KB5017500) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 10 Version 20H2 for ARM64 (KB5017498) |
| 2022-09 Cumulative Update for .NET Framework 4.8 for Windows 10 Version 1607 for x64 (KB5017035) |
| Windows Malicious Software Removal Tool – v5.105 (KB890830) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 10 Version 21H1 for x64 (KB5017499) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.7.2 and 4.8 for Windows 10 Version 1809 for x64 (KB5017528) |
| 2022-09 Cumulative Update for .NET Framework 4.8 for Windows 10 Version 1607 (KB5017035) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.7.2 and 4.8 for Windows 10 Version 1809 (KB5017528) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 10 Version 21H2 (KB5017500) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 11 for x64 (KB5017497) |
| 2022-09 Cumulative Update for .NET Framework 3.5 and 4.7.2 for Windows 10 Version 1809 for ARM64 (KB5017528) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8, and 4.8.1 for Microsoft server operating system version 21H2 for x64 (KB5017501) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 10 Version 20H2 (KB5017498) |
| 2022-09 Cumulative Update for .NET Framework 3.5, 4.8 and 4.8.1 for Windows 10 Version 21H1 (KB5017499) |
| Windows Malicious Software Removal Tool x64 – v5.105 (KB890830) |
| 2022-09 Cumulative Update for Windows 10 Version 21H1 for ARM64-based Systems (KB5017308) |
| 2022-09 Cumulative Update for Windows 10 Version 21H2 for ARM64-based Systems (KB5017308) |
| 2022-09 Cumulative Update for Windows 10 Version 20H2 for x64-based Systems (KB5017308) |
| 2022-09 Cumulative Update for Windows 10 Version 20H2 for ARM64-based Systems (KB5017308) |
| 2022-09 Cumulative Update for Windows 10 Version 21H1 for x64-based Systems (KB5017308) |
| 2022-09 Cumulative Update for Microsoft server operating system version 21H2 for x64-based Systems (KB5017316) |
| 2022-09 Cumulative Update for Windows 10 Version 20H2 for x86-based Systems (KB5017308) |
| 2022-09 Cumulative Update for Windows 10 Version 1607 for x86-based Systems (KB5017305) |
| 2022-09 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB5017396) |
| 2022-09 Cumulative Update for Windows 11 for ARM64-based Systems (KB5017328) |
| 2022-09 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB5017305) |
| 2022-09 Servicing Stack Update for Windows 10 Version 1607 for x86-based Systems (KB5017396) |
| 2022-09 Cumulative Update for Windows 11 for x64-based Systems (KB5017328) |
| 2022-09 Cumulative Update for Windows 10 Version 21H2 for x64-based Systems (KB5017308) |
| 2022-09 Cumulative Update for Windows 10 Version 21H2 for x86-based Systems (KB5017308) |
September 2022 Patch Tuesday LCU Patch Deployment using Intune
Let’s check how to deploy the September 2022 Patch Tuesday (LCU) Deployment using Intune. You can deploy Windows 10/11 CUs using the Microsoft Endpoint Manager Intune. The patch deployment process in Intune is different from that of SCCM.
I don’t think creating a new patch deployment policy to cater to monthly CU deployments is required. The existing patch deployment policy will deliver the patches using WUfB (Windows Update for Business).
Read More – Software Update Patching Options with Intune Setup Guide (anoopcnair.com)
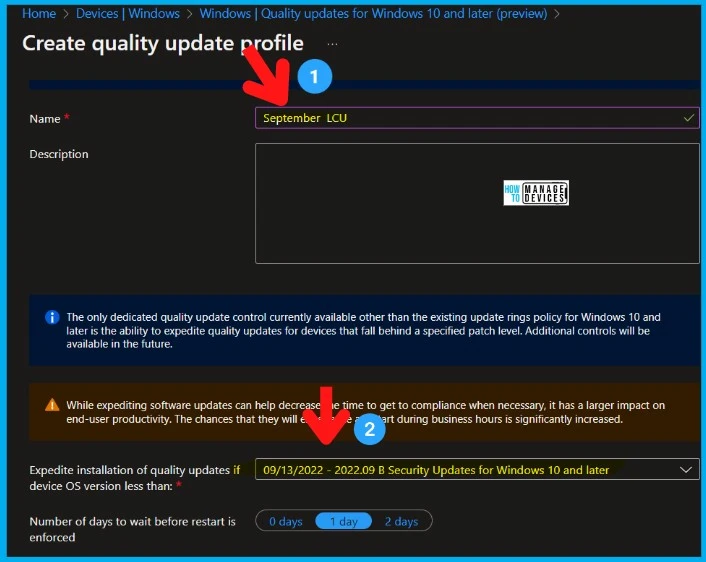
You have an option to expedite the Installation of September 2022 quality updates if the device OS version is less than 2022.07. Create expedited update profiles for Quality updates using the following steps.
- Open https://endpoint.microsoft.com/
- Navigate Device -> Windows 10 quality Updates (preview).
- Click on + Create Profile.
The following are the Settings for Intune quality update profile for the monthly patching process if you want to expedite the deployment of patches. Otherwise, you can use the standard quality updates policy from Intune.
- Name – September 2022 LCU for Windows 10 KB5017308 and Windows 11 KB5017328
- Description—
- Expedite installation of quality updates if device OS version less than 13th September 2022 – 2022.09 B Security Updates for Windows 10 and later
- Number of days to wait before the restart is enforced – 1 Day
More Details on Zero Day Out Of Band Patch Deployment Using Intune MEM Expedite Best Option and Intune Reporting Issue: Expedite Windows Security Patch Deployment.
Windows 11 September 2022 Cumulative Update KB5017328
Let’s check Windows 11 September 2022 Cumulative Update KB5017328 deployment options. Like Windows 10 (KB5016616), you can deploy Windows 11 patches (LCUs) using SCCM and Intune.
Windows 11 patching is also important for the organization. Microsoft has released the latest Cumulative Update, KB5017328, for September 2022. Windows 11 will change its build number to 22000.978 after the cumulative update KB5017328.
- 2022-09 Cumulative Update for Windows 11 for x64-based Systems (KB5017328)
- Article ID:5017328 Date revised: Tuesday, September 13, 2022.
- Maximum Severity Rating: Critical

Direct Download Links of September 2022 Cumulative Updates
Let’s manually download the 2022 September Cumulative Update for Windows 10 (KB5017308), Windows 11 (KB5017328), and Server 2022 (KB5017316) from the Microsoft Update Catalog website.
The following tables contain the direct links to download the September 2022 Cumulative Updates for Windows 10, Windows 11, and Windows Server operating systems.
You can check the Microsoft Update Catalog portal to get the direct download links to the hotfixes for Sept 2022 LCU. Check this out Microsoft Update Catalog – https://www.catalog.update.microsoft.com/
| Title | Products | Size | Direct Download |
|---|---|---|---|
| 2022-09 Cumulative Update for Windows 10 Version 20H2 for x64-based Systems (KB5017308) | Windows 10, version 1903 and later | 677.5 MB | Download |
| 2022-09 Cumulative Update for Windows 10 Version 21H1 for x64-based Systems (KB5017308) | Windows 10, version 1903 and later | 677.5 MB | Download |
| 2022-09 Cumulative Update for Windows 10 Version 21H2 for x64-based Systems (KB5017308) | Windows 10, version 1903 and later | 677.5 MB | Download |
| 2022-09 Cumulative Update for Microsoft server operating system version 21H2 for x64-based Systems (KB5017316) | Windows Server version 21H2 | 244.1 MB | Download |
| 2022-09 Cumulative Update for Windows 11 for x64-based Systems (KB5017328) | Windows 11 | 274.4 MB | Download |
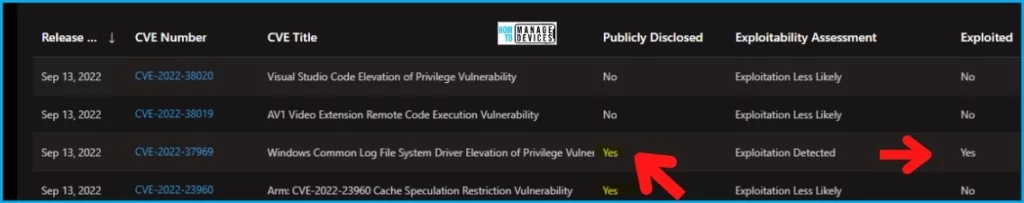
List of September 2022 CVE Vulnerability Details with Exploitation More Likely
Let’s find out the details of the List of CVE Vulnerability Details with the “Exploitation More Likely” Exploitability Assessment with September 2022 patch Tuesday.
| CVE Number | CVE Title | Publicly Disclosed | Exploitability Assessment | Exploited | Tags |
|---|---|---|---|---|---|
| CVE-2022-38020 | Visual Studio Code Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Visual Studio Code |
| CVE-2022-38020 | Visual Studio Code Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Visual Studio Code |
| CVE-2022-38019 | AV1 Video Extension Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Windows Codecs Library |
| CVE-2022-38019 | AV1 Video Extension Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Windows Codecs Library |
| CVE-2022-37969 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | Yes | Exploitation Detected | Yes | Windows Common Log File System Driver |
| CVE-2022-37969 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | Yes | Exploitation Detected | Yes | Windows Common Log File System Driver |
| CVE-2022-23960 | Arm: CVE-2022-23960 Cache Speculation Restriction Vulnerability | Yes | Exploitation Less Likely | No | Cache Speculation |
| CVE-2022-37963 | Microsoft Office Visio Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Office Visio |
| CVE-2022-38011 | Raw Image Extension Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Windows Codecs Library |
| CVE-2022-38011 | Raw Image Extension Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Windows Codecs Library |
| CVE-2022-38011 | Raw Image Extension Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Windows Codecs Library |
| CVE-2022-37962 | Microsoft PowerPoint Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Office |
| CVE-2022-38010 | Microsoft Office Visio Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Office Visio |
| CVE-2022-38007 | Azure Guest Configuration and Azure Arc-enabled servers Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Azure Arc |
| CVE-2022-38007 | Azure Guest Configuration and Azure Arc-enabled servers Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Azure Arc |
| CVE-2022-37959 | Network Device Enrollment Service (NDES) Security Feature Bypass Vulnerability | No | Exploitation Less Likely | No | Network Device Enrollment Service (NDES) |
| CVE-2022-38006 | Windows Graphics Component Information Disclosure Vulnerability | No | Exploitation Less Likely | No | Microsoft Graphics Component |
| CVE-2022-38006 | Windows Graphics Component Information Disclosure Vulnerability | No | Exploitation Less Likely | No | Microsoft Graphics Component |
| CVE-2022-37958 | SPNEGO Extended Negotiation (NEGOEX) Security Mechanism Information Disclosure Vulnerability | No | Exploitation Less Likely | No | SPNEGO Extended Negotiation |
| CVE-2022-37958 | SPNEGO Extended Negotiation (NEGOEX) Security Mechanism Information Disclosure Vulnerability | No | Exploitation Less Likely | No | SPNEGO Extended Negotiation |
| CVE-2022-38005 | Windows Print Spooler Elevation of Privilege Vulnerability | No | Exploitation Unlikely | No | Windows Print Spooler Components |
| CVE-2022-37957 | Windows Kernel Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Windows Kernel |
| CVE-2022-38004 | Windows Fax Service Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Role: Windows Fax Service |
| CVE-2022-38004 | Windows Fax Service Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Role: Windows Fax Service |
| CVE-2022-38004 | Windows Fax Service Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Role: Windows Fax Service |
| CVE-2022-37956 | Windows Kernel Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kernel |
| CVE-2022-37955 | Windows Group Policy Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Group Policy |
| CVE-2022-37954 | DirectX Graphics Kernel Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Microsoft Graphics Component |
| CVE-2022-34734 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows ODBC Driver |
| CVE-2022-34733 | Microsoft OLE DB Provider for SQL Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows OLE |
| CVE-2022-34732 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Windows ODBC Driver |
| CVE-2022-34731 | Microsoft OLE DB Provider for SQL Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows OLE |
| CVE-2022-34730 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows ODBC Driver |
| CVE-2022-34729 | Windows GDI Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Microsoft Graphics Component |
| CVE-2022-34728 | Windows Graphics Component Information Disclosure Vulnerability | No | Exploitation Less Likely | No | Microsoft Graphics Component |
| CVE-2022-34727 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows ODBC Driver |
| CVE-2022-34726 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows ODBC Driver |
| CVE-2022-34725 | Windows ALPC Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Microsoft Windows ALPC |
| CVE-2022-34725 | Windows ALPC Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Microsoft Windows ALPC |
| CVE-2022-34724 | Windows DNS Server Denial of Service Vulnerability | No | Exploitation Less Likely | No | Role: DNS Server |
| CVE-2022-34723 | Windows DPAPI (Data Protection Application Programming Interface) Information Disclosure Vulnerability | No | Exploitation Less Likely | No | Windows DPAPI (Data Protection Application Programming Interface) |
| CVE-2022-34722 | Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows IKE Extension |
| CVE-2022-34722 | Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows IKE Extension |
| CVE-2022-34721 | Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows IKE Extension |
| CVE-2022-34721 | Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows IKE Extension |
| CVE-2022-34720 | Windows Internet Key Exchange (IKE) Extension Denial of Service Vulnerability | No | Exploitation Less Likely | No | Windows IKE Extension |
| CVE-2022-34719 | Windows Distributed File System (DFS) Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Distributed File System (DFS) |
| CVE-2022-34718 | Windows TCP/IP Remote Code Execution Vulnerability | No | Exploitation More Likely | No | Windows TCP/IP |
| CVE-2022-34718 | Windows TCP/IP Remote Code Execution Vulnerability | No | Exploitation More Likely | No | Windows TCP/IP |
| CVE-2022-35841 | Windows Enterprise App Management Service Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows Enterprise App Management |
| CVE-2022-35840 | Microsoft OLE DB Provider for SQL Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows OLE |
| CVE-2022-35838 | HTTP V3 Denial of Service Vulnerability | No | Exploitation Less Likely | No | HTTP.sys |
| CVE-2022-35837 | Windows Graphics Component Information Disclosure Vulnerability | No | Exploitation Less Likely | No | Microsoft Graphics Component |
| CVE-2022-35837 | Windows Graphics Component Information Disclosure Vulnerability | No | Exploitation Less Likely | No | Microsoft Graphics Component |
| CVE-2022-35836 | Microsoft OLE DB Provider for SQL Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows OLE |
| CVE-2022-35835 | Microsoft OLE DB Provider for SQL Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows OLE |
| CVE-2022-35834 | Microsoft OLE DB Provider for SQL Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows OLE |
| CVE-2022-35833 | Windows Secure Channel Denial of Service Vulnerability | No | Exploitation Less Likely | No | Windows Transport Security Layer (TLS) |
| CVE-2022-35832 | Windows Event Tracing Denial of Service Vulnerability | No | Exploitation Less Likely | No | Windows Event Tracing |
| CVE-2022-35831 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | No | Exploitation Less Likely | No | Windows Remote Access Connection Manager |
| CVE-2022-35830 | Remote Procedure Call Runtime Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows Remote Procedure Call |
| CVE-2022-35830 | Remote Procedure Call Runtime Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows Remote Procedure Call |
| CVE-2022-34700 | Microsoft Dynamics CRM (on-premises) Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Dynamics |
| CVE-2022-34700 | Microsoft Dynamics CRM (on-premises) Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Dynamics |
| CVE-2022-33647 | Windows Kerberos Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kerberos |
| CVE-2022-33647 | Windows Kerberos Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kerberos |
| CVE-2022-33647 | Windows Kerberos Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kerberos |
| CVE-2022-33647 | Windows Kerberos Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kerberos |
| CVE-2022-30200 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Windows LDAP – Lightweight Directory Access Protocol |
| CVE-2022-38013 | .NET Core and Visual Studio Denial of Service Vulnerability | No | Exploitation Less Likely | No | .NET and Visual Studio |
| CVE-2022-37964 | Windows Kernel Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kernel |
| CVE-2022-37961 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Microsoft Office SharePoint |
| CVE-2022-37961 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Microsoft Office SharePoint |
| CVE-2022-37961 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Microsoft Office SharePoint |
| CVE-2022-38009 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Office SharePoint |
| CVE-2022-38009 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Office SharePoint |
| CVE-2022-38009 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Office SharePoint |
| CVE-2022-38008 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Office SharePoint |
| CVE-2022-38008 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Office SharePoint |
| CVE-2022-38008 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Office SharePoint |
| CVE-2022-38008 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Office SharePoint |
| CVE-2022-35828 | Microsoft Defender for Endpoint for Mac Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Defender |
| CVE-2022-35823 | Microsoft SharePoint Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Microsoft Office SharePoint |
| CVE-2022-35823 | Microsoft SharePoint Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Microsoft Office SharePoint |
| CVE-2022-35823 | Microsoft SharePoint Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Microsoft Office SharePoint |
| CVE-2022-35805 | Microsoft Dynamics CRM (on-premises) Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Dynamics |
| CVE-2022-35805 | Microsoft Dynamics CRM (on-premises) Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Microsoft Dynamics |
| CVE-2022-35803 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Windows Common Log File System Driver |
| CVE-2022-33679 | Windows Kerberos Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kerberos |
| CVE-2022-33679 | Windows Kerberos Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kerberos |
| CVE-2022-33679 | Windows Kerberos Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kerberos |
| CVE-2022-33679 | Windows Kerberos Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kerberos |
| CVE-2022-33679 | Windows Kerberos Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Kerberos |
| CVE-2022-30196 | Windows Secure Channel Denial of Service Vulnerability | No | Exploitation Less Likely | No | Windows Transport Security Layer (TLS) |
| CVE-2022-30196 | Windows Secure Channel Denial of Service Vulnerability | No | Exploitation Less Likely | No | Windows Transport Security Layer (TLS) |
| CVE-2022-30170 | Windows Credential Roaming Service Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Credential Roaming Service |
| CVE-2022-30170 | Windows Credential Roaming Service Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Credential Roaming Service |
| CVE-2022-26929 | .NET Framework Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | .NET Framework |
| CVE-2022-26928 | Windows Photo Import API Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Photo Import API |
| CVE-2022-26928 | Windows Photo Import API Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Windows Photo Import API |
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.
