Let’s learn more details of the SCCM ADR Automatic Deployment Rule creation process in this post. I will cover the Windows 11 and Windows 10 ADR creation process in this post. Microsoft released Windows 11 production version, and you will have to follow the steps mentioned below to carry out the patching of Windows 11 OS.
ConfigMgr ADRs are Automatic Deployment Rules created for automatic deployment of Software Updates (monthly patches). Let’s learn to create SCCM Automatic Deployment Rule (ADR) to make monthly patching easy for Configuration Manager Admins.
The assumption here is that you already have a manual patching process in place for your organization. Now the requirement is to take the monthly patching process to the next level by using ADR.
- Fix: Windows Update Issues For Windows 11 Errors Troubleshooting Tips
- Fixed – SCCM WSUS Sync Failed With UssInternalError SoapException Error 0x80131500
- SCCM WSUS Office Updates Sync Failed with Error 400
- Monthly Patching process using Intune
The end-to-end SCCM patching or software update deployment process is covered in the two video tutorials and blog posts below. SCCM ADR is going to work if you have all these prerequisites in place.
- Free SCCM Training Part 1 | 17 Hours of Latest Technical Content
- Free ConfigMgr Training Part 2 | 20 Hours of Technical | SCCM
- Install WSUS for ConfigMgr Software Update Point Role
- Install ConfigMgr Software Update Point Role (SUP) Setup Guide
Create SCCM ADR Automatic Deployment Rule
Let’s start creating automatic deployment rules for monthly patching scenarios. You should have appropriate access to create SCCM ADR rules for Windows 10, Windows 11, or Windows Server 2022 patches.
- Launch ConfigMgr Console.
- Navigate to \Software Library\Overview\Software Updates\Automatic Deployment Rules
- Right-click on Automatic Deployment Rules node and Select Create Automatic Deployment Rule.
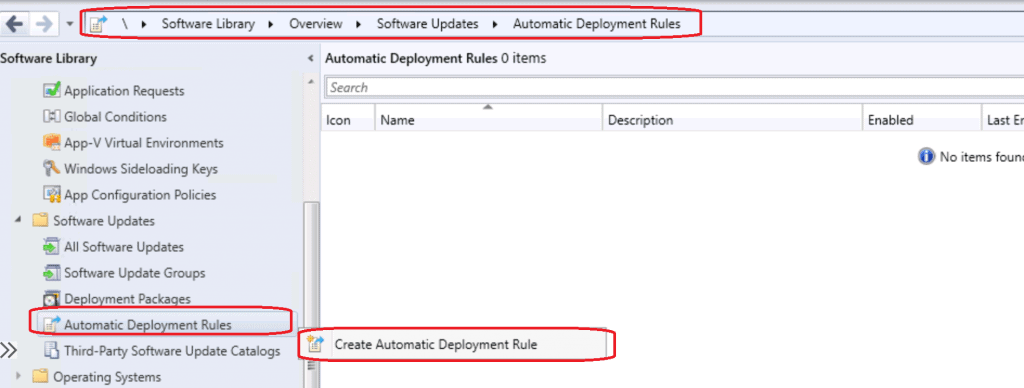
General Settings Page
Let’s understand the general settings of the Automatic Deployment Rule. The following settings are the best options for some scenarios. I would recommend you try testing different combinations for several months before deciding on one particular option.
One example is Create a New Software Update Group. Creating a new SUG is the best option in my experience for many scenarios. But some of you might have a different opinion & experience. Please feel to share in the comments if you like.
- Enter the Name for ConfigMgr ADR rule
- HTMD ADR for Windows 10 Monthly Security Patches.
- Enter the Description – So that your colleagues can understand what is this ADR
- “Sample Text – Pilot – Monthly security Patches for HTMD Team. Please create another ADR for different departs. Don’t change the ADR without notifying the following teams.”
- Select the Device collection you want to deploy the monthly security patches.
- I normally select pilot collection with fewer devices and then production deployment will be a different one.
Now, you need to tell the ADR that what it should do when?
Each Time the rule runs and finds new updates. I select Create a new Software Update Group. Make sure you select the checkmark to Enable the Deployment after this rule is run for a pilot deployment.
For production, if you want you can uncheck this option to be safer. Click on the Next button to continue.
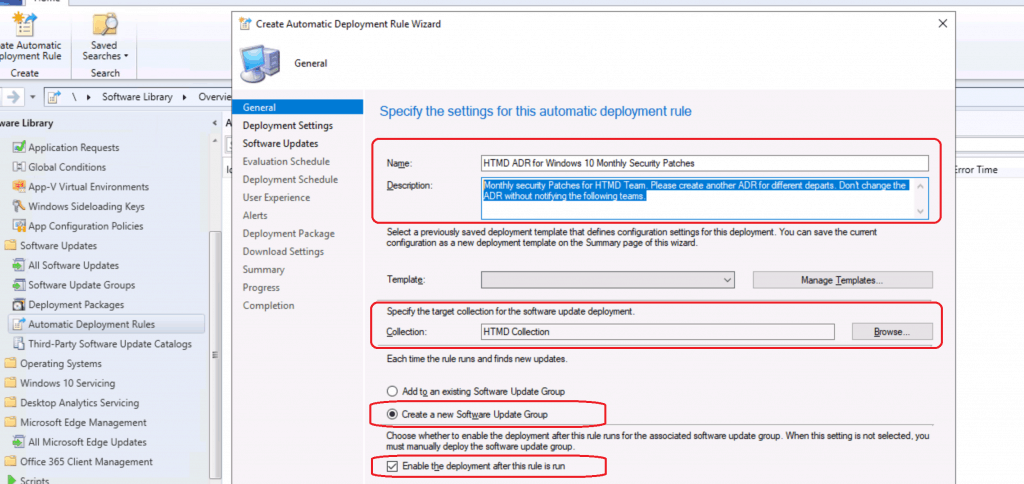
Deployment Settings
The patch deployment process is explained for all the operating systems, including Windows 10 and Windows 11.
Choose How many state details do you want the client to report back for deployment created by this ADR? Details Level – I selected the default one.
Only Error Messages – Some Software updates include license agreements. This option is to approve any license agreements automatically.
I select the default option – Automatically deploy all software updates found by this ADR and approve any license agreement.
Click on the Next button to continue.
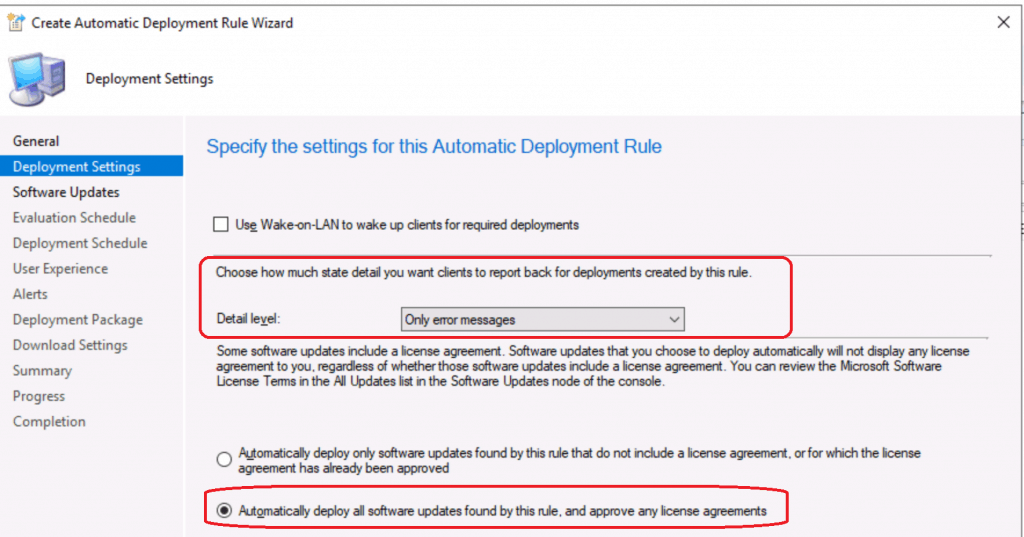
Select Software Updates using ADR Criteria
This is the brain of SCCM ADR for Windows 11 and Windows 10 operating systems. You have to select according to your requirements. The filter criteria for me are not probably suitable for your organization.
I have given a couple of options here as examples. You will have to select the best-suited one for you as SCCM ADR filter criteria.
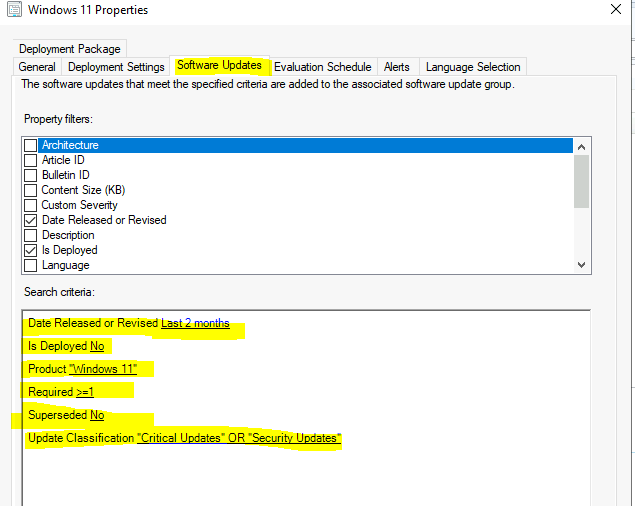
The brain of ADR – Let’s select the criteria you want to deploy using SCCM ADR.
- The software updates that meet the specified criteria are added to the associated software update group
- Properties filters – You can select from the following list:
- Article ID
- Bulletin ID
- Content Size (KB)
- Custom Severity
- Date Released or Reviewed
- Description
- Is Deployed
- Language
- Product
- Required
- Severity
- Superseded
- Title
- Update Classification
- UUP Preference
- Vendor
- Select the value for the filters you want for each filter
- (Refer to the screenshot to get more details about the filters which I used for pilot deployment SCCM ADR rule).
- Properties filters – You can select from the following list:
- Architecture: “x64”
- Date Released or Revised: Last 2 months
- Is Deployed: No
- Product: “Windows 10, version 1903 and later”
- Superseded: No
- Update Classification: “Security Updates”
- Required Greater than or equal to 1
Platform Details
You can also add additional settings like mentioned below to filter out Windows 11 updates. There are various options to select the Windows updates that you want to include in the ADR rules.
- Date Released or Revised: Last 2 Months
- Is Deployed: No (optional)
- Product: Windows 11 (only required if you are creating different Software Update Group for different OS products)
- Superseded: No
- Required: Greater than or equal to 1
- Update Classification: “Critical Updates” OR “Security Updates”
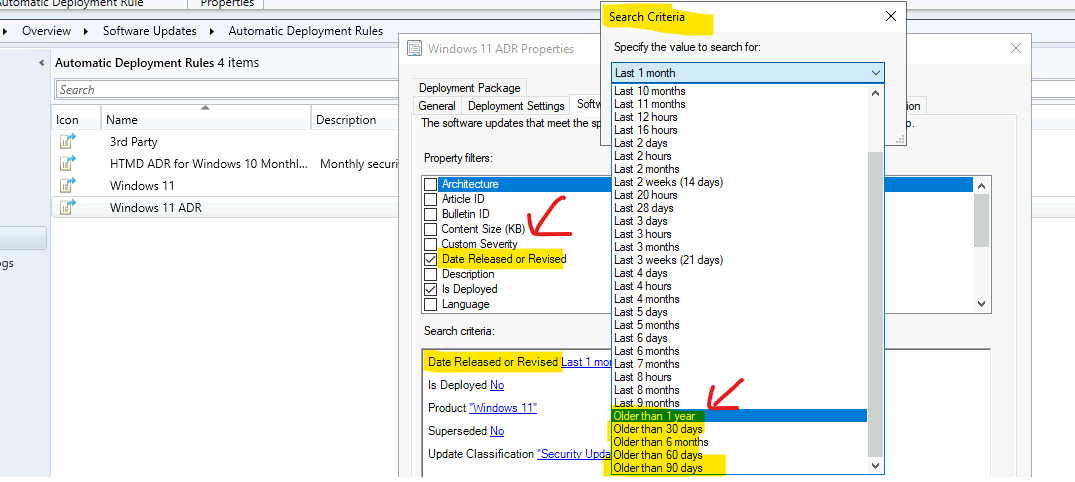
Date Released or Revised with Older than Options
Let’s check SCCM 2111 new features production release. The additional options (such as older than 30, 60, 90 days, or 6 months, or 1 year) for Date Released or Revised search criteria are added to Automatic Deployment Rules.
The Older than options in search Criteria – Specify the Value to Search for:
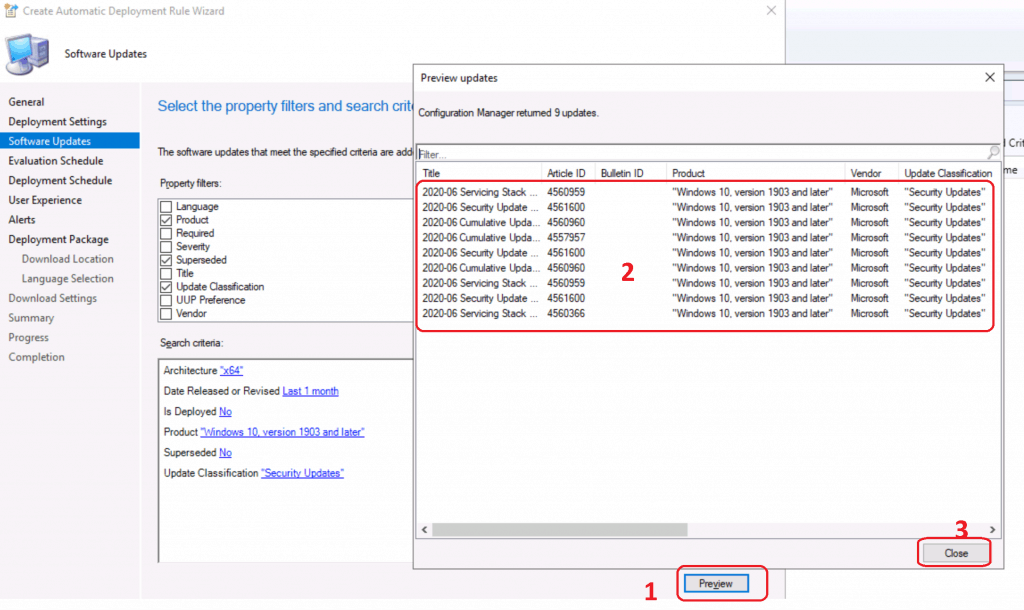
Preview Software Updates
The preview button is a very useful option while creating SCCM automatic deployment rules. You can check which KB articles are included in the filter criteria. You can also use similar ADR rules for Windows Server 2022 version.
- Click on the Preview button to check and confirm whether you are using the filters correctly and to avoid accidental deployment errors.
- Click on the CLOSE button.
- Click on the next button to continue.
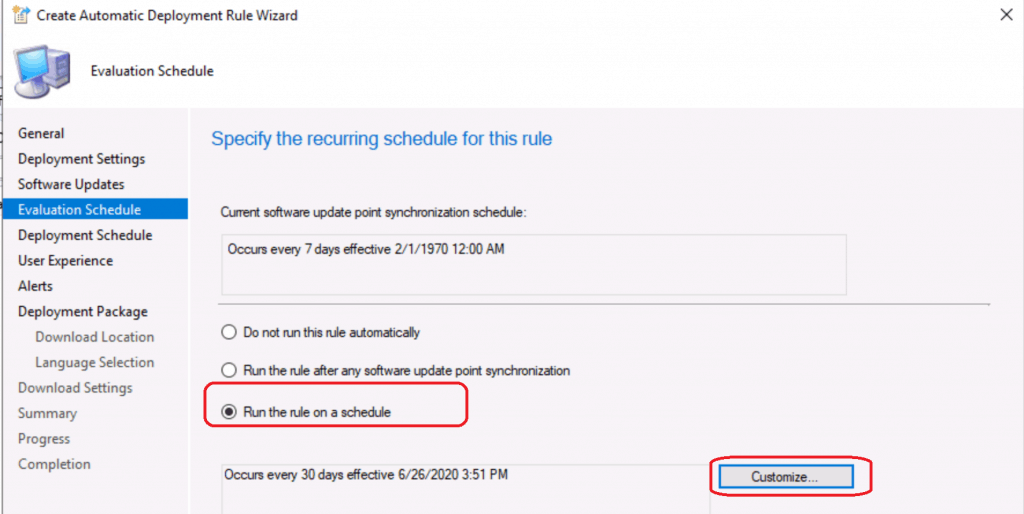
ADR Evaluation Schedule Settings
Now, let’s set up a monthly second Tuesday schedule for ConfigMgr Automatic Deployment Rule (ADR).
- Select Run the Rule on a Schedule.
- Click on the Customize button to schedule.
Custom Schedule Second Tuesday for ADR
- Select the Custom Schedule for the ADR evaluation schedule.
- Select Time – Select the time you want to start custom schedule
- Reoccurrence pattern
- Configure the recurrence schedule
- Monthly – The Second Tuesday
- Click OK
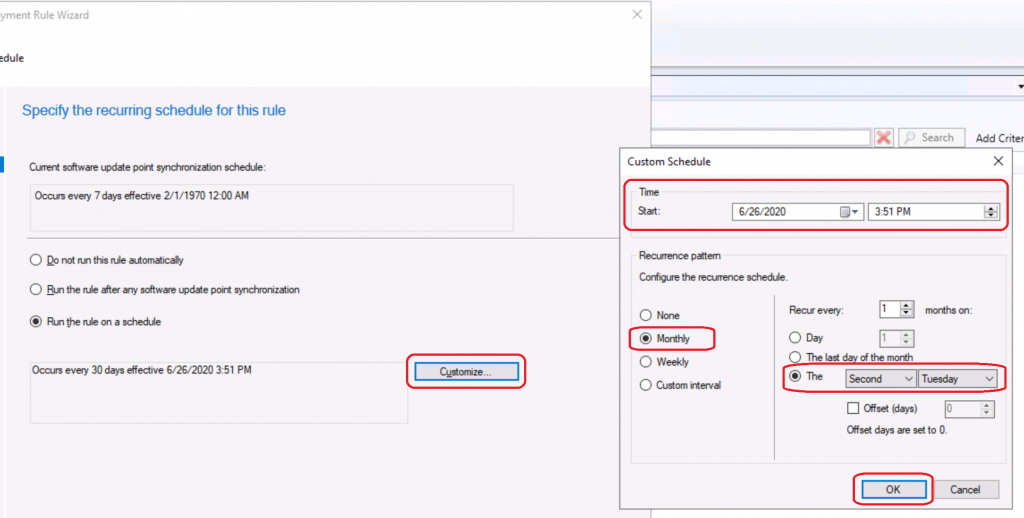
- Occurs the Second Tuesday of every 1 months effective 6/26/2020 3:51 PM
- Click the Next button to continue
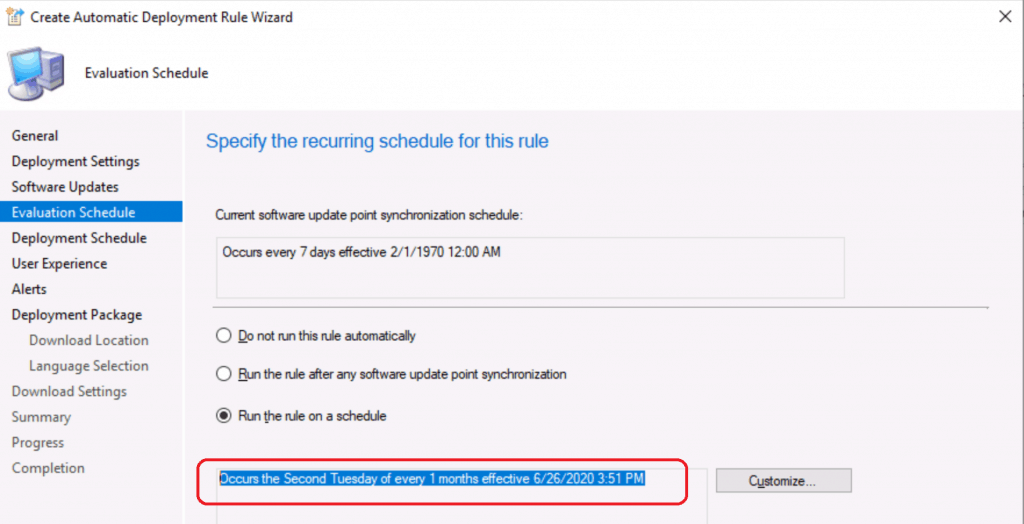
Deployment Schedule for SCCM ADR
Scheduling options are important for Windows 11 and Windows 10 operating systems patch deployment process.
- Specify if the schedule for this deployment is evaluated based upon UTC or local client time.
- I select default option Time Based on – Client Local Time
- Software available time.
- As Soon As Possible – or select the hours
- Installation Deadline.
- Specific Time – 7 Days – Better to use Hours (56 hours) instead of Days.
- Click the NEXT button.
NOTE! – You can enable the feature to Delay enforcement of this deployment according to user preferences up to the grace period defined in client settings.
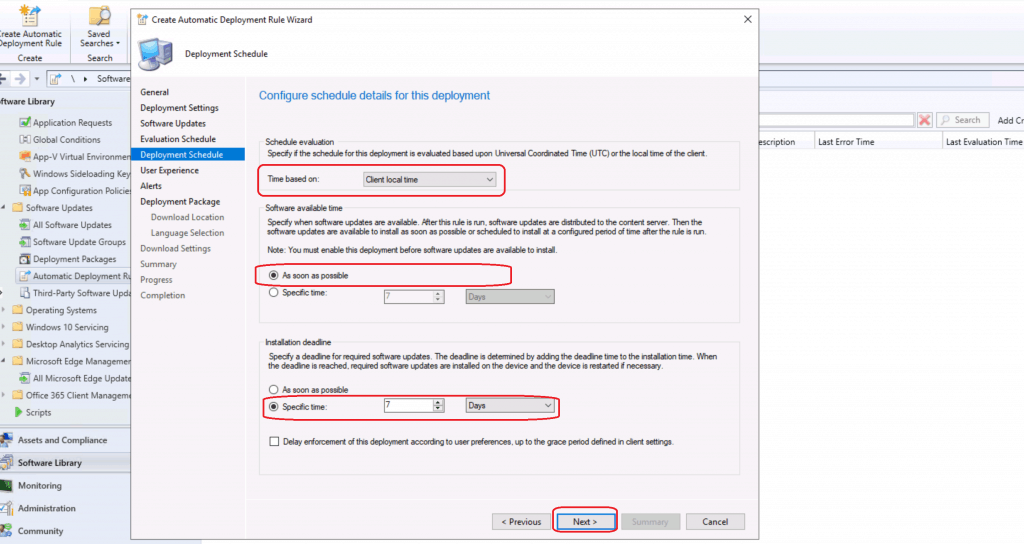
User Experience – ADR Template
I always keep the user experience as the default unless you have a specific business requirement.
Setup Alerts for Automatic Deployment Rule (ADR)
Set the alerts using the following option.
Generate an alert when this Rule fails
Click the Next button.
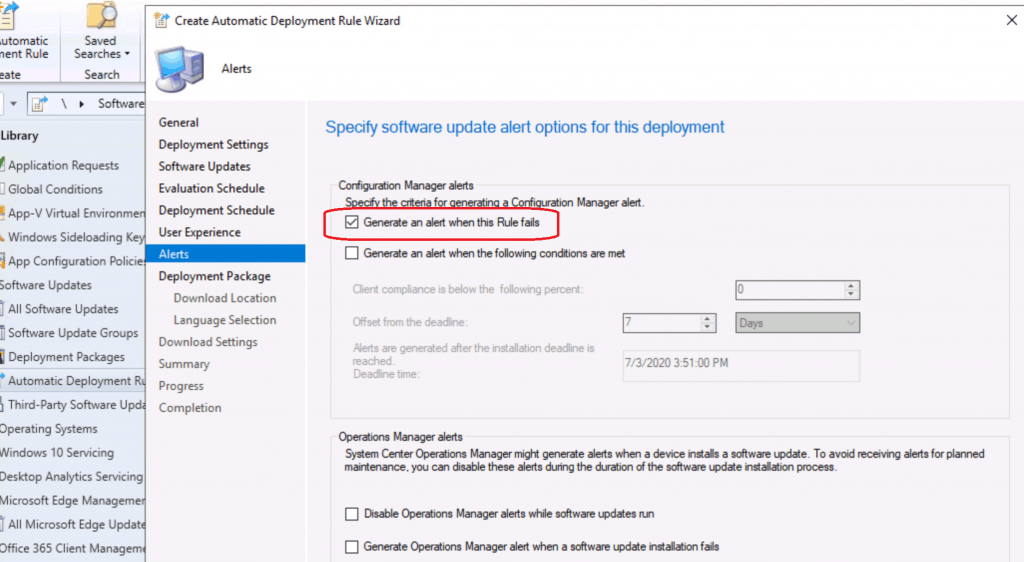
Package Creation Process
I prefer the NO deployment package option wherever possible in the Work from the Home scenario. But, if you are already working from an office scenario, on-prem DPs are a better option.
Select the option – Create a new Deployment Package
Enter the Package name – Windows 10 Security Patches
Enter the package source location – \\CMMEMCM\Sources\Patches\Security Patch
Make sure you enable the option called – Enable binary differential replication.
Click the next button.
NOTE! – Select the NO Deployment Option if you want to use Microsoft cloud instead of on-prem DPs for patching. Use Existing SCCM Config To Help To Reduce VPN Bandwidth | ConfigMgr
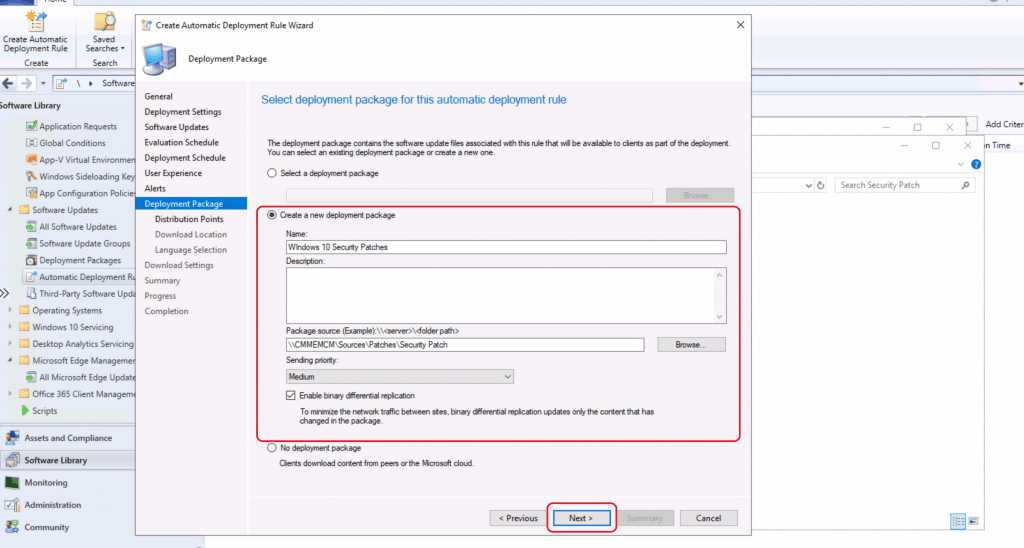
Distribute the Package
There is no need to create a package in no package scenario because the patches will get downloaded directly from Microsoft updates.
- Select the Distribution Point you want to distribute the package.
- Click Add and Select the available distribution point.
- Click ok.
- Click the Next button to continue.
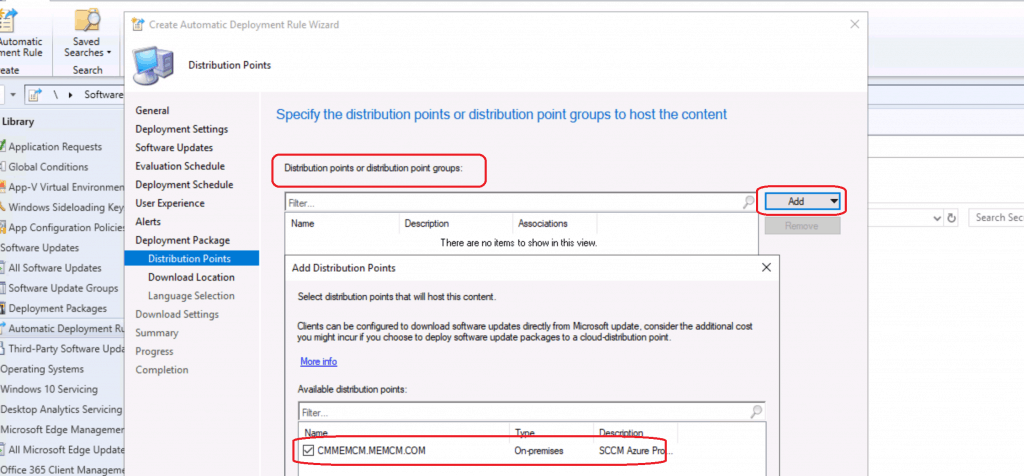
Download Options
Select the option to download the updates from Microsoft cloud. You will need to have all the proxy and firewall ports opened for this scenario to work.
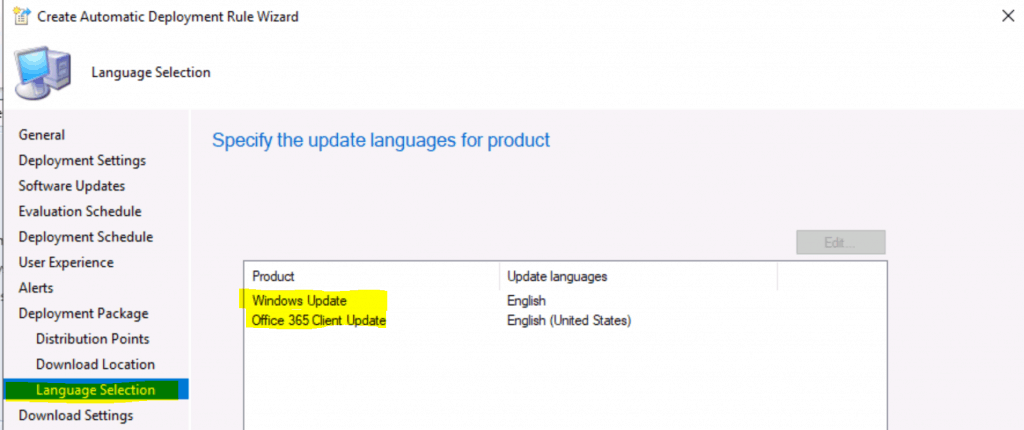
Language Selection
If you are a global organization, you will need to select different languages.
- This is the option to select Language Selection.
- Windows Update Language = English.
- Office 365 Client Update = English (United States).
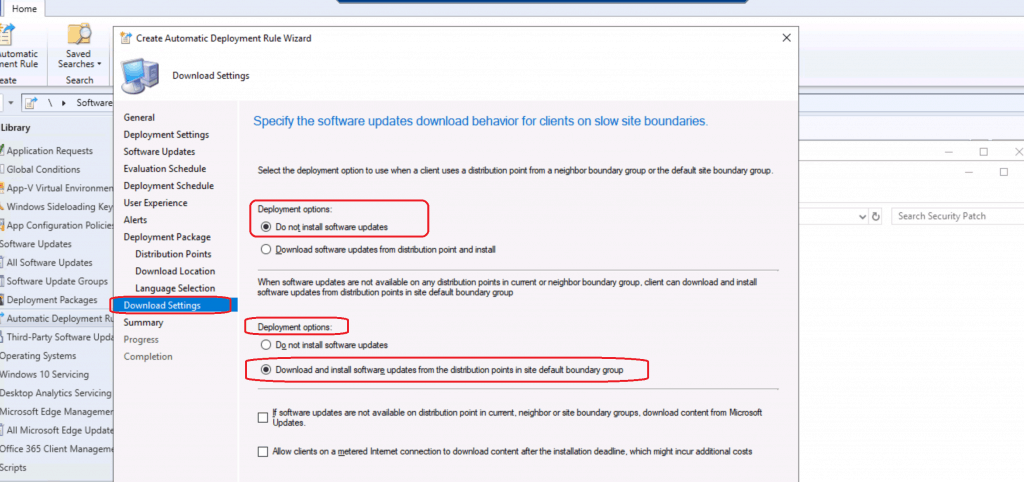
Client Download Settings
The client download settings are also important for the SCCM ADR creation scenario. You will need to follow the settings as per your best practices.
- Select Download settings for the client.
- Deployment Options
- Do not install software updates
- Deployment options
- Download and Install software updates from all distribution points in site default boundary group
- Click on the Next button
- Deployment Options
NOTE! – You should use the NO Package option.
Click Next, Next, and Close.
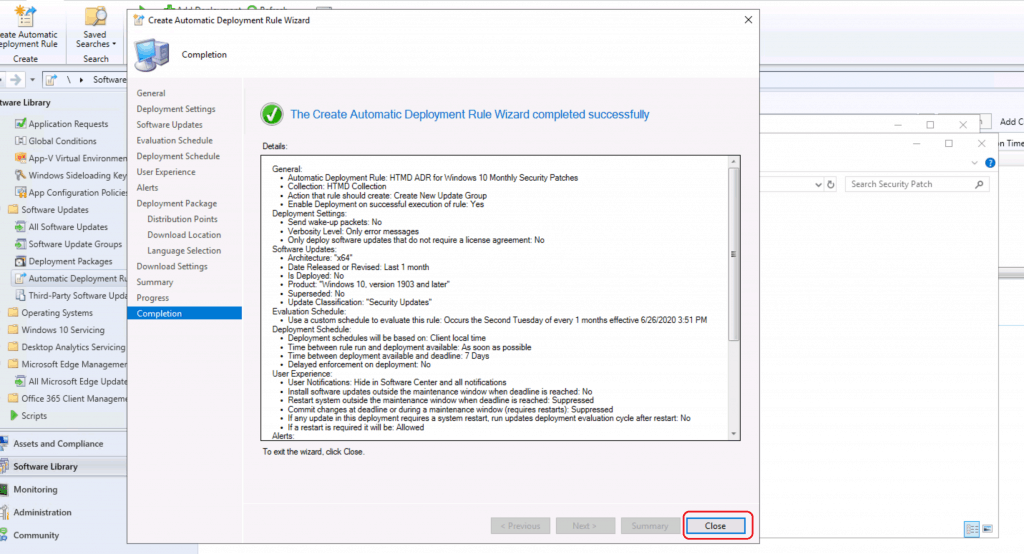
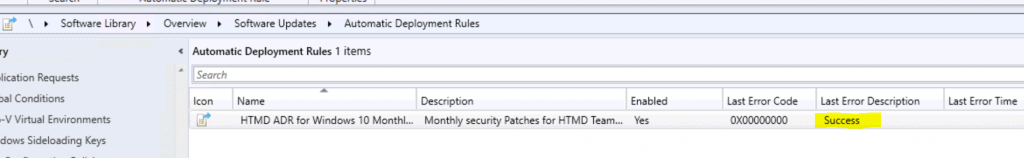
Results – SCCM ADR Rule
Let’s check the results ADR results here. You can check and monitor the SCCM ADR rule status from the Automatic Deployment Rule (SCCM ADR) itself.
The last Error Description column in the ADR node gives you the error details of the ADR rule.
SCCM ADR Log File
You can check the SCCM logs also to get confirmation on the successful creation of the Software Update Group and Patch package for Windows 11, Windows 10, or Windows Server 2022 operating systems. More details on SCCM Logs Files are available in this post.
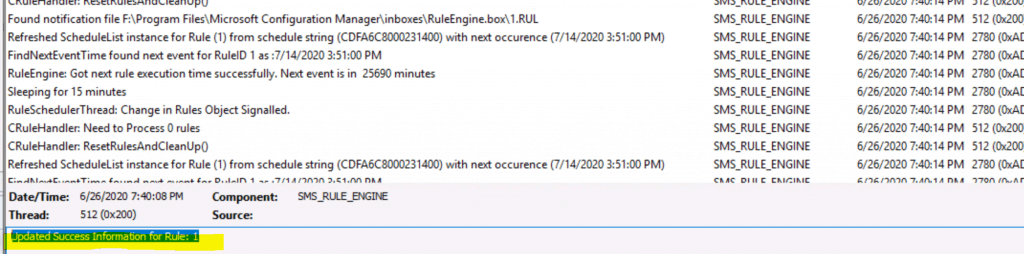
- Check the log file called ruleengine.log on site server.
Downloading contents (count = 1) for UpdateID 16783343 List of update content(s) which match the content rule criteria = {16780582} Successfully downloaded the update content with ID 16780611 from internet. Updated Success Information for Rule: 1
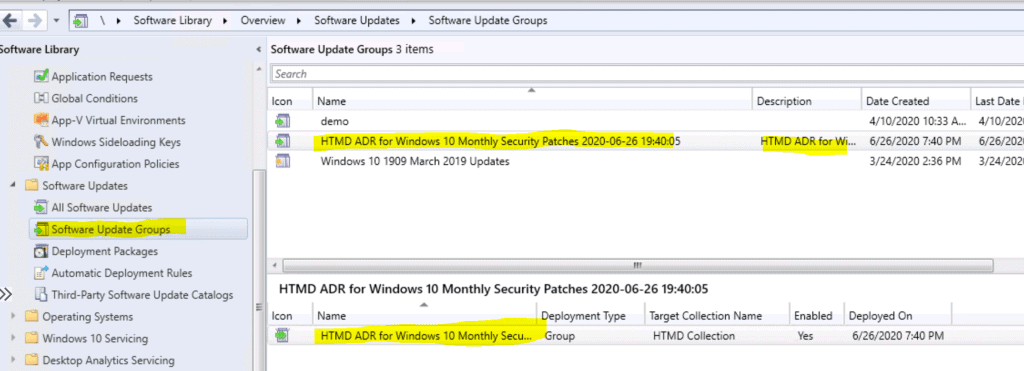
Software Update Group by ADR
Software Update Group got created using SCCM ADR.
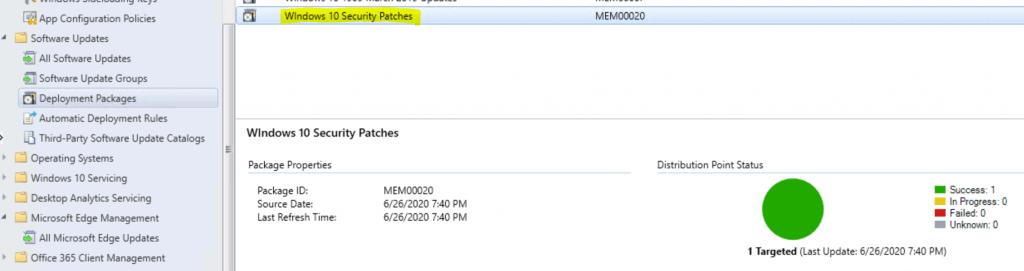
Deployment Package Created by ADR
The deployment package got created using the SCCM ADR!
Resources
- Install New ConfigMgr Software Update Role Setup Guide| SUP| SCCM
- SCCM Third-Party Software Updates Setup Step by Step Guide Post 1
Author
Anoop is Microsoft MVP! He is a Solution Architect in enterprise client management with over 17 years of experience (calculation done in 2018). He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc…..…

Hi Anoop,
I have followed the steps mentioned and created an ADR for updating windows updates. However, the software update group is not created. Can you suggest what could have gone wrong.
Have you checked the log file mentioned in the logs section of the post? Check the log file called ruleengine.log on site server
Hello Mr. Nair,
Great Blogs.. Been a fan of your blogs, very informative and supportive.
I have a question, can we make the ADR as to be “Available” not “Required”. I do not see any options as such here, in this workflow.
One of the content of the update is not getting download. How to identify which update failed ?
have combed the internet but could not find any reference. is there any other log that will list the failing update.
Let’s say you have an update for Intel Management Agent and you have 2 models that use different driver versions for this update. If you have one collection with both models will the appropriate driver install on the correct model? Or do you need to do multiple ADR’s?
Hi Anoop,
Have you done a setup where the SCCM site is offline? In our case, we have an offline site and the WSUS points to another upstream WSUS server with internet access.
What should we set at the “Download Options”? We have tried pointing it to the WSUSContent folder on the WSUS server but it didn’t work.
Thank you.
San
Need exact location of Ruleengine.log file with screenshot