Let’s have a look at the Cloud PC monthly patching process using Intune WUfB policies in this post. I’m going to cover the troubleshooting tips for Cloud PC patching as well. I recommend using MEM Intune to configure Windows Update for Business (WUfB) policies to deploy monthly patches to Cloud PCs.
The Cloud PC provisioning process is tightly integrated with the Microsoft Endpoint Manager (MEM) admin center portal. You can configure Intune Windows Update ring policies for Windows 10 and Windows 11 PCs. You can also configure Windows 10 and 11 Feature Update using Intune policies. The troubleshooting on Cloud PC and physical PC is also the same for monthly patching and feature update scenario.
You can either use Intune assignment filters or Azure AD dynamic device groups for deploying these policies to Cloud PCs. I have used filter rules to deploy Windows 21H2 preview release version to Cloud PCs. This segregation can help you to test Cloud PCs from physical PCs.
Video – Intune Patch Management Options
What is Intune Patching? Intune patching is the process that helps IT admins to keep Windows, iOS/iPad, and macOS devices updated with the latest patches released by Operating Systems, Core Components, Drivers, etc… Intune uses Windows Update for Business (WUfB) Deployment service to deploy patches onto Windows Devices.
Intune doesn’t store the content of the patches. The devices manage the patch installation file directly from Windows Update/Apple Update services. macOS and iOS/iPad devices must be in a supervised mode to enable patching via Intune.
Configure Monthly Patching Policy for Cloud PCs
Let’s learn how to configure monthly patching policies for Cloud PCs in this section. As I mentioned about the best option is to use Intune Windows update ring policies to configure WUfB policies in this context.
You will need to have appropriate permissions on the MEM admin center portal to carry out the following activities. Let’s go through the steps mentioned below to complete the monthly patching policy creation process.
- Launch endpoint.microsoft.com portal.
- Navigate to Devices -> Windows 10 Update Rings tab. Well, this tab name is going to change for Windows 11 monthly patching policies.
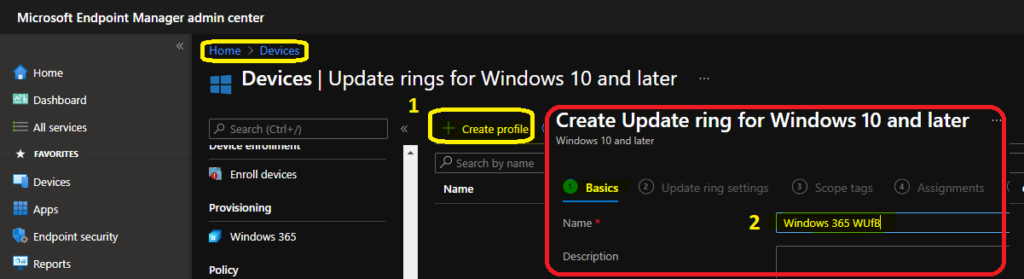
- Click on + Create Profile button from the top bar.
- Enter the name of the Profile -> I used “Windows 365 WUfB Policies.”
- Click on Next button to continue.
Let’s see how to configure the Intune Windows update ring policies in this section. You can change it as per your organization’s requirements. However, I will keep the default Microsoft configuration wherever possible.
I have segregated this policy configuration into two sections 1. Update Settings 2. User experience settings for easy understanding.
- Update settings
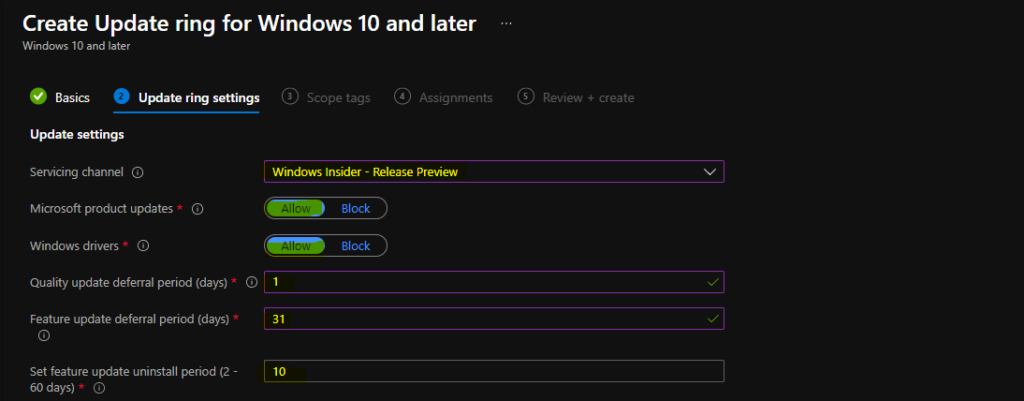
- Service Channel – Windows Insider – Release Preview.
- You have different update channels available here. For most of the scenarios, you will need to select Semi-Anual Channel for production PCs.
- Microsoft product updates – Allow.
- Windows drivers – Allow.
- Quality update deferral period (days) – 1 – Defer quality updates for the specified number of days. The allowed value is between 0-30 days.
- Feature update deferral period (days) – 31 – Defer feature updates for the specified number of day. The allowed value is between 0-365 days.
- Set feature update uninstall period (2 – 60 days) – 10 – This is to set feature update uninstall period. The allowed value is between 2-60 days.
- Service Channel – Windows Insider – Release Preview.
NOTE! – Don’t use Windows Insider – Release Preview for Cloud PCs deployments. It can use only for a small number of test Physical PCs. For Cloud PCs, use a Semi-Anual Channel. This excise is just for documentation purposes.
You can check the User Experience settings for monthly patching policy configuration for Cloud PCs and other Windows PCs. These Intune policies are configured in the Admin center portal.
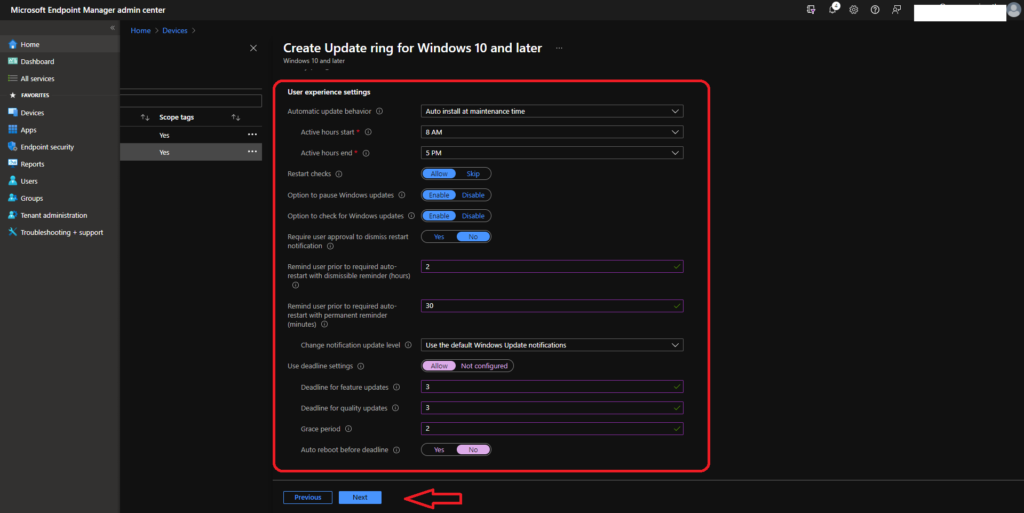
- Automatic Update behavior -> AutoInstall at maintenance time.
- Active hours start -> 8 AM
- Active hours end -> 5 PM
- Restart checks – Allow – This policy is set to skip all check before restart: Battery level = 40%, User presence, Display Needed, Presentation mode, Full screen mode, phone call state, game mode etc.
- Option to pause Windows updates -Enable
- Option to check for Windows updates – Enable
- Require user approval to dismiss restart notification – No
- Remind user prior to required auto-restart with a dismissible reminder (hours) – The allowed number of hours, 2, 4, 8, 12, or 24 – 2 Hours.
- Remind user prior to required auto-restart with a permanent reminder (minutes) – The allowed number of minutes, 15, 30, or 60 – 30 Minutes.
- Change notification update level – Use default Windows Update notifications.
Now, it’s time to set user deadline settings experience for Cloud PC devices in monthly patching context using WUfB. You will need to be careful about all these configurations because this is all about the end-user experience.
- Use deadline settings -> Allow
- Deadline for feature updates -> 3
- Deadline for quality updates -> 3
- Grace period – > 2
- Auto reboot before the deadline – No
- Click on Next to continue.
You will need to define the Intune scope tags if you have a requirement to control the visibility of these policies to a particular team. I have skipped this step for the lab environment. You will also need to assign the Intune monthly patching policy to All devices or any Azure AD device group.
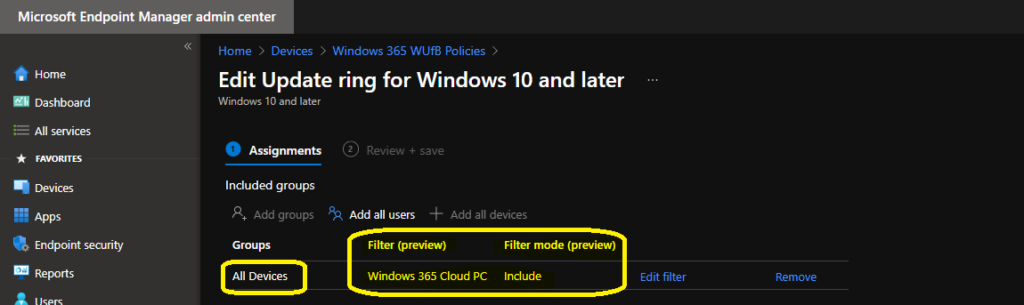
If you are using all devices, add the filter rule to Include this assignment or policy applies only to Cloud PCs. This is what I showed in the below screenshot as well. I have explained filter rules and must create filter rules for Cloud PCs before assigning this policy.
- Click on All Devices.
- Click on Filter to add Windows 365 Cloud PC filter and you need to include only Cloud PC devices.
- Click on Review + Save to complete Intune monthly policy creattion process.
Troubleshooting Tips Cloud PC Monthly Patching Process
You have now deployed the Intune policy to relevant Cloud PCs, as explained in the above section. It’s time to check whether the policies are deployed to Cloud PCs or any other Windows PCs. I think it’s better to Initiate a Manual Intune Policy Sync for troubleshooting purposes.
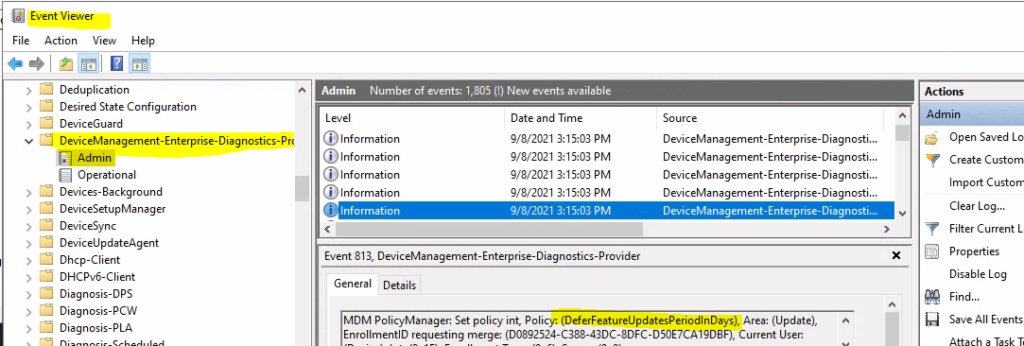
- The first thing you need to check after the manual sync of Intune policy is event logs.
- Cloud PC Event Logs -> Microsoft->Windows->DeviceManagement-> Enterprise-Diagnostics-Provider/Admin.
MDM PolicyManager: Set policy int, Policy: (DeferQualityUpdatesPeriodInDays), Area: (Update), EnrollmentID requesting merge: (D0892524-C388-43DC-8DFC-D50E7CA19DBF), Current User: (Device), Int: (0x1), Enrollment Type: (0x6), Scope: (0x0). MDM PolicyManager: Set policy int, Policy: (ConfigureFeatureUpdateUninstallPeriod), Area: (Update), EnrollmentID requesting merge: (D0892524-C388-43DC-8DFC-D50E7CA19DBF), Current User: (Device), Int: (0x5), Enrollment Type: (0x6), Scope: (0x0). MDM PolicyManager: Set policy int, Policy: (UpdateNotificationLevel), Area: (Update), EnrollmentID requesting merge: (D0892524-C388-43DC-8DFC-D50E7CA19DBF), Current User: (Device), Int: (0x2), Enrollment Type: (0x6), Scope: (0x0).
You can now see the policy that you have configured above is coming down to Cloud PCs from the event log entries. This is important for troubleshooting Intune policies.
It’s time to check the registry entries to confirm whether Intune Windows update policy is correctly configured on the Windows 10 and Windows 11 PCs. Each type of Intune policy has different locations in the registry to check.
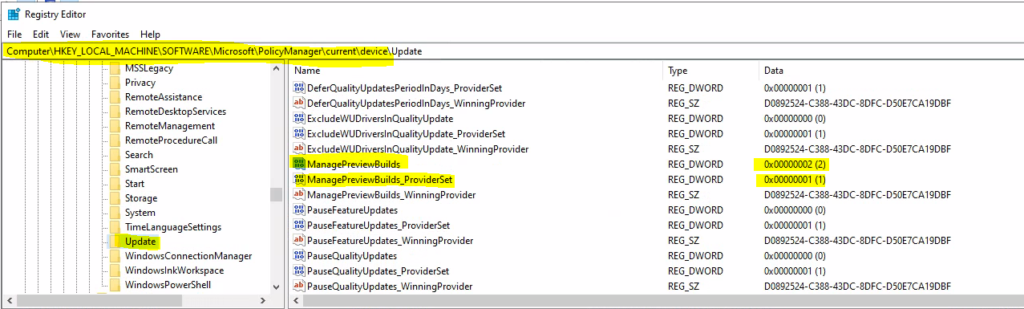
The registry entry path changes depending on the Windows CSP policy that you deal with. In this scenario, you deal with Intune or Windows Update for Business monthly patching and feature update policies. Let’s see the registry entry path details for WUfB.
- Path -> Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\Update
Intune WUfB Registry Path (This is correct Registry key that should be looked into)- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\Providers\D1E11663-BF69-4DD8-974A-BAD47E6EF433\default\Device\Update
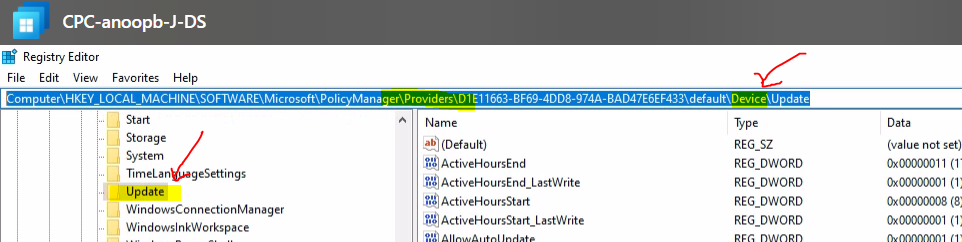
NOTE! – I have removed the “_WinningProvider” policy value for each of the policies listed in the below table. I don’t know what the exact use of those entries is. I assume this “_WinningProvider” is there to avoid policy conflicts.
| Intune WUfB – Windows CSP Policy | Value |
|---|---|
| AllowAutoUpdate | dword:00000001 |
| AllowAutoUpdate_ProviderSet | dword:00000001 |
| AllowMUUpdateService | dword:00000001 |
| AllowMUUpdateService_ProviderSet | dword:00000001 |
| ExcludeWUDriversInQualityUpdate | dword:00000000 |
| ExcludeWUDriversInQualityUpdate_ProviderSet | dword:00000001 |
| DeferQualityUpdatesPeriodInDays | dword:00000001 |
| DeferQualityUpdatesPeriodInDays_ProviderSet | dword:00000001 |
| PauseQualityUpdates | dword:00000000 |
| PauseQualityUpdates_ProviderSet | dword:00000001 |
| PauseFeatureUpdates | dword:00000000 |
| PauseFeatureUpdates_ProviderSet | dword:00000001 |
| SetEDURestart | dword:00000000 |
| SetEDURestart_ProviderSet | dword:00000001 |
| ActiveHoursStart | dword:00000008 |
| ActiveHoursStart_ProviderSet | dword:00000001 |
| ActiveHoursEnd | dword:00000011 |
| ActiveHoursEnd_ProviderSet | dword:00000001 |
| ConfigureFeatureUpdateUninstallPeriod | dword:00000005 |
| ConfigureFeatureUpdateUninstallPeriod_ProviderSet | dword:00000001 |
| UpdateNotificationLevel | dword:00000002 |
| UpdateNotificationLevel_ProviderSet | dword:00000001 |
| DeferFeatureUpdatesPeriodInDays | dword:0000001e |
| DeferFeatureUpdatesPeriodInDays_ProviderSet | dword:00000001 |
| SetDisablePauseUXAccess | dword:00000000 |
| SetDisablePauseUXAccess_ProviderSet | dword:00000001 |
| SetDisableUXWUAccess | dword:00000000 |
| SetDisableUXWUAccess_ProviderSet | dword:00000001 |
| BranchReadinessLevel | dword:00000008 |
| BranchReadinessLevel_ProviderSet | dword:00000001 |
| ManagePreviewBuilds | dword:00000002 |
| ManagePreviewBuilds_ProviderSet | dword:00000001 |
| ConfigureDeadlineForFeatureUpdates | dword:00000003 |
| ConfigureDeadlineForFeatureUpdates_ProviderSet | dword:00000001 |
| ConfigureDeadlineForQualityUpdates | dword:00000003 |
| ConfigureDeadlineForQualityUpdates_ProviderSet | dword:00000001 |
| ConfigureDeadlineGracePeriod | dword:00000001 |
| ConfigureDeadlineGracePeriod_ProviderSet | dword:00000001 |
| ConfigureDeadlineNoAutoReboot | dword:00000000 |
| ConfigureDeadlineNoAutoReboot_ProviderSet | dword:00000001 |
Results
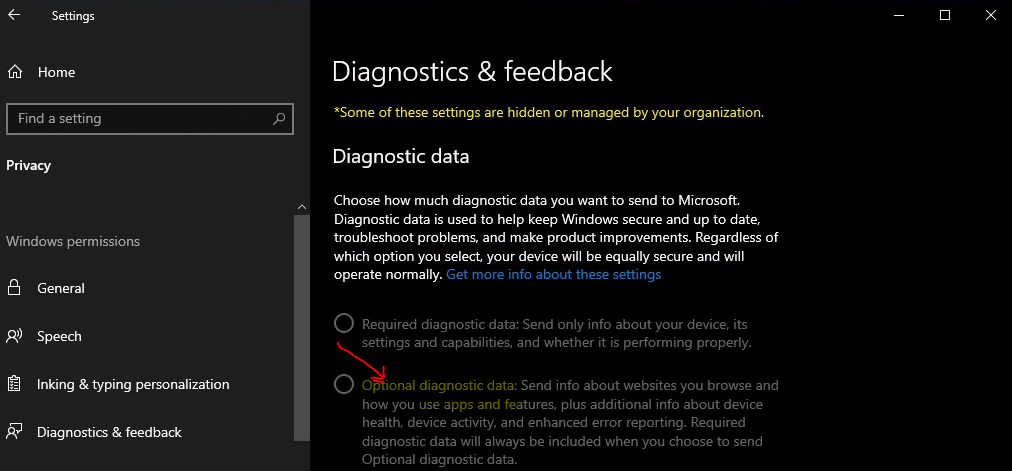
As I mentioned above, the Cloud PC doesn’t support preview builds because you can’t turn on Optional diagnostic data settings from the cloud PC. There are registry entries to change this forcefully, but I don’t want to try this for Cloud PC now.