Let’s learn SCCM Third-Party Software Updates Setup Step-by-Step (Guide Post1). I will guide you through the process of configuring third-party software updates in SCCM. This guide is comprehensive and will help you set up patching with ease.
For many years, SCUP helped many of us deploy third-party software updates. Now, SCCM doesn’t require SCUP to deploy Third-party updates. Let’s dive into the SCCM third-party software update setup. Microsoft applications are patched as part of the Microsoft Software Update patching process. However, the third-party applications (non-Microsoft) are NOT patched using Microsoft updates.
There is no option to customize the end-user experience using a third-party patching solution from Microsoft. For example, Adobe Acrobat and Reader when the applications are open, and the SCCM / WSUS patching is applied. It might force the termination of the applications without notice.
You should have a different process for 3rd party updates. This post will teach you how to enable 3rd party patching using SCCM and WSUS without using SCUP. The patching of applications like Chrome, Java, etc… is not easy.
- SCCM Third-Party Software Updates Setup Step-by-Step Guide Post Video Guide
- Free SCCM Catalog List – SCCM Third-Party Updates Post 2
- Background Process flow with Logs – SCCM Third-Party Software Updates – Post 3
- Fix SCCM 3rd Party Patching Sync Failed Issue
This post is a step-by-step SCCM third-party software update setup guide for all SCCM admins.
First of all, you need to analyze and understand the business requirements of third-party updates. From my perspective, third-party patching is critical for the overall IT security landscape.
The following are some of the questions that will help you get ready for a third-party software update setup.
- What is the current process for patching third-party applications?
- Are you using the standard packaging process to perform third-party updates?
- How many application vendors are providing SCCM-friendly “Update Catalogs” for free?
- Do you need to spec up the SCCM server hardware before enabling third-party updates?
Video Guide – SCCM Third-Party Software Updates Setup Step-by-Step Guide Post Video Guide
In this video, we will learn how to configure SCCM third-party Software Updates Setup in step-by-step.
Prerequisites
You can enable third-party updates from SCCM (without SCUP integration) when you have 1806 or a later version.
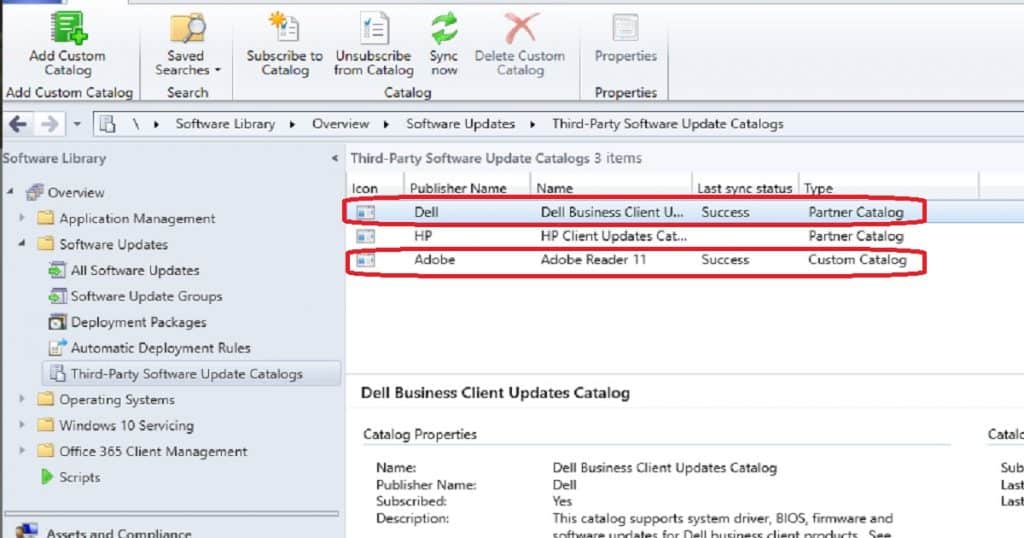
- Partner catalogs are software vendor catalogs partnered with Microsoft. The following are the two partner catalogs (DELL & HP) available with SCCM 1902 release.
- Custom Catalogs are third-party software catalogs you can manually add to the SCCM console. The section below provides more details.
The SCCM third-party software updates feature allows you to subscribe to partner and custom catalogs from the SCCM console and publish the updates to WSUS.
NOTE! – There are only a few vendors that provide FREE custom catalogs. You can find more details in the blog post free List of Catalogs SCCM Third-Party Software Updates.
The following is the quick list of prerequisites that you want to ensure before enabling the update feature.
- WSUS and SUP should be configured and working fine.
- Updates Classification should be enabled from Software Update Point Component Properties.
- Valid Business requirements and find sponsorship from management.
- License cost – SCCM support is free, but if you want to use other third-party products to get more vendor application support (via Custom Catalog), you need to pay the extra licensing cost.
- SCCM Server Specs & Disk Space – Consider Upgrading Disk Space per your requirement.
- Adjust your proxy and Firewall configurations – port 443, and you might need to white list all the third-party vendor URLs to download metadata, CAB files, and source files of updates.
- Check out Certificate requirements on the Server and client sides. You might also need to adjust the Group Policy setting on the client side.
- SCCM Client Settings – Enable third-party software updates policies to YES.
- Additional requirements when the SUP is remote from the top-level site server
NOTE! – Some Certificate Details – 1. WSUS (Publishers Self Signed) – Code Signing – Only WSUS Server 2. Trusted Publishers – WSUS Server & Client 3. Trusted Root Certificate – WSUS Server & Client
Enable SCCM Third-Party Software Updates
As I mentioned in the prerequisites, ensure that you have a working WSUS and SUP environment before enabling the third-party updates.
The following steps should be completed from the top site, either SCCM CAS or the Standalone primary server. The below steps will help you to enable SCCM third-party update feature.
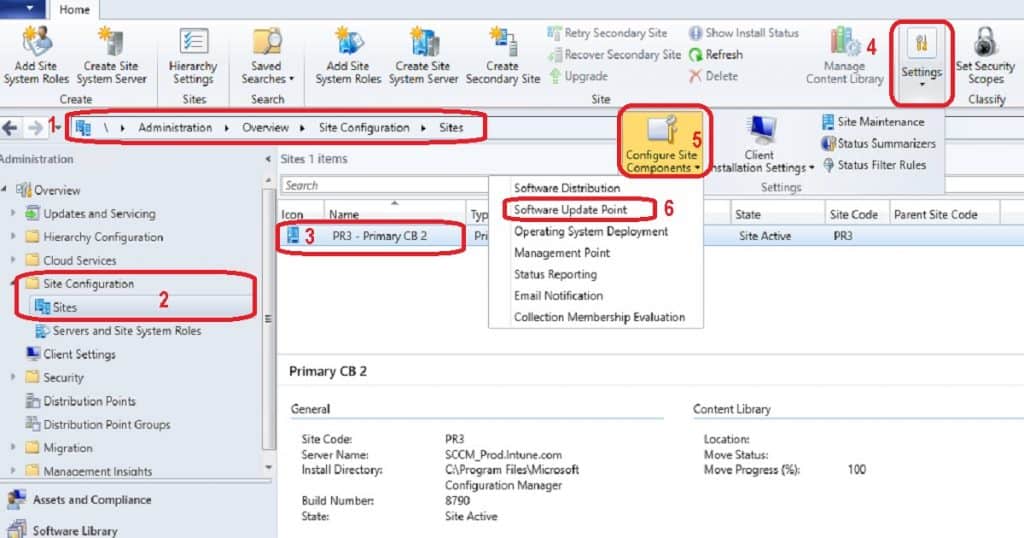
- Go to the Administration workspace in the SCCM console. Expand Site Configuration and select the Sites node.
- Select the top-level site in the hierarchy. From the Ribbon menu, click Configure Site Components and select Software Update Point.
- Click on the Third-Party Updates tab and select the option Enable third-party software updates from Software Update Point Component Properties.
- Select Configuration Manager to manage the certificate (I selected this default option).
- I have not chosen this option—manually managing the certificates. This option should be used when you need to use PKI certificates.
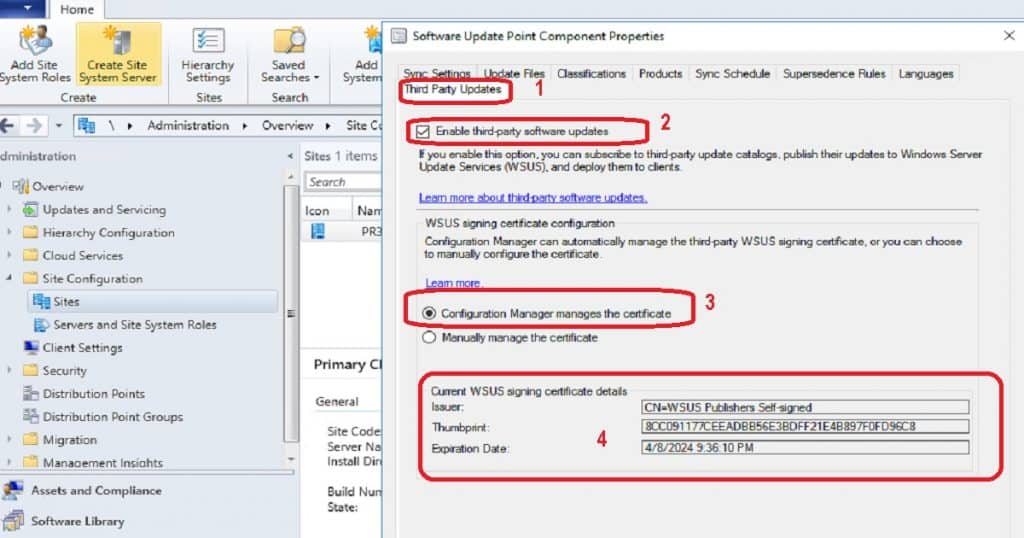
NOTE! – I would recommend using the default options of the SCCM configuration wizard unless you have a specific reason to select another option. I have chosen the configuration manager-managed certificate option.
If you don’t have any PKI certificate requirements for SCCM third-party updates, you can use the default option, as I mentioned above.
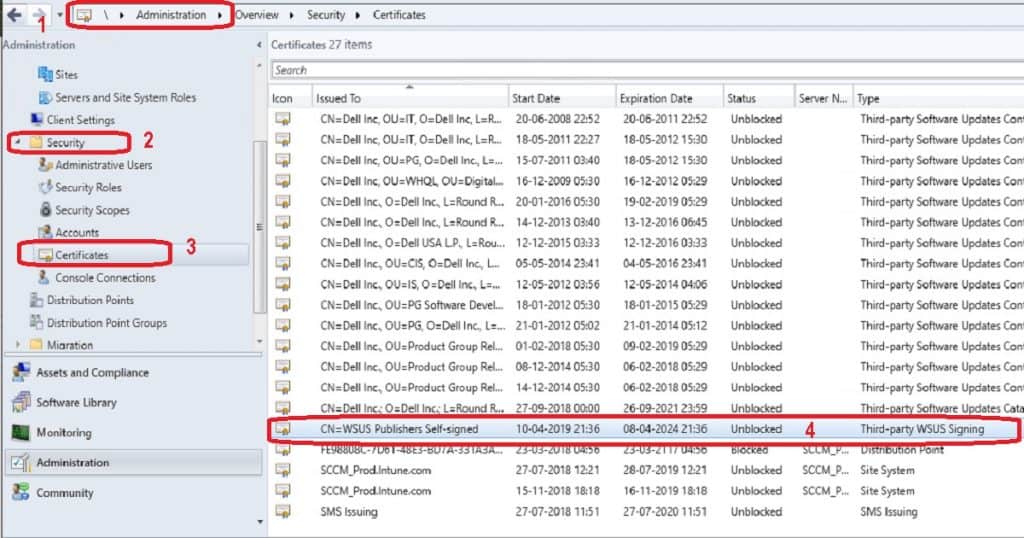
You might be able to see a new certificate type, “third-party WSUS Signing” (as I showed in the picture below), when you use Configuration Manager to manage the certificate option from the above wizard.
Navigate to – \Administration\Overview\Security\Certificates
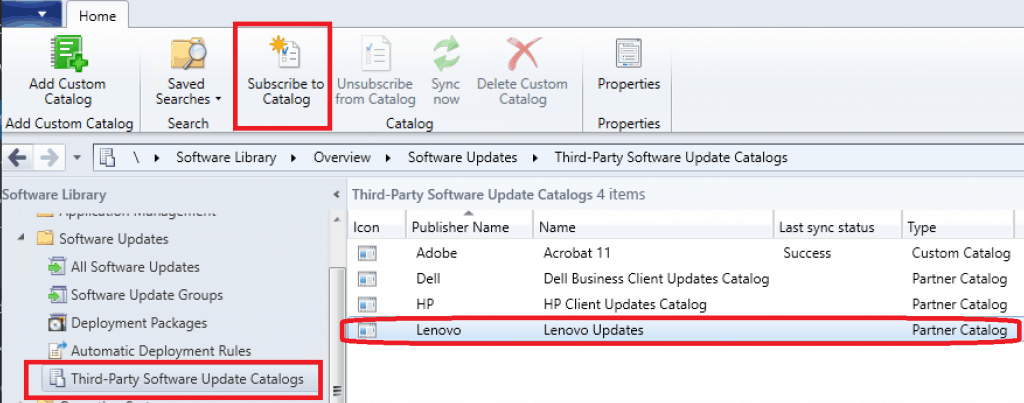
Subscribe to Partner Catalog
In this section, you can subscribe to partner catalogs (out-of-box settings, as I mentioned above).
- Launch SCCM Console
- Navigate \Software Library\Overview\Software Updates\Third-Party Software Update Catalogs node
- Click on the “Lenovo” partner catalog from the list on the right side
- Click on Subscribe
Add a Custom Catalog
The next step in setting up SCCM third-party software updates is to add custom catalogs. In the console, you can add the custom catalogs from \Software Library\Overview\Software Updates\Third-Party Software Update Catalogs.
You might already see the partner catalogs in the SCCM console. HP and Dell are the only two(2) partner catalogs available for SCCM 1902 version.
You can follow the below steps to add a custom catalog to SCCM.
- Navigate to \Software Library\Overview\Software Updates\Third-Party Software Update Catalogs.
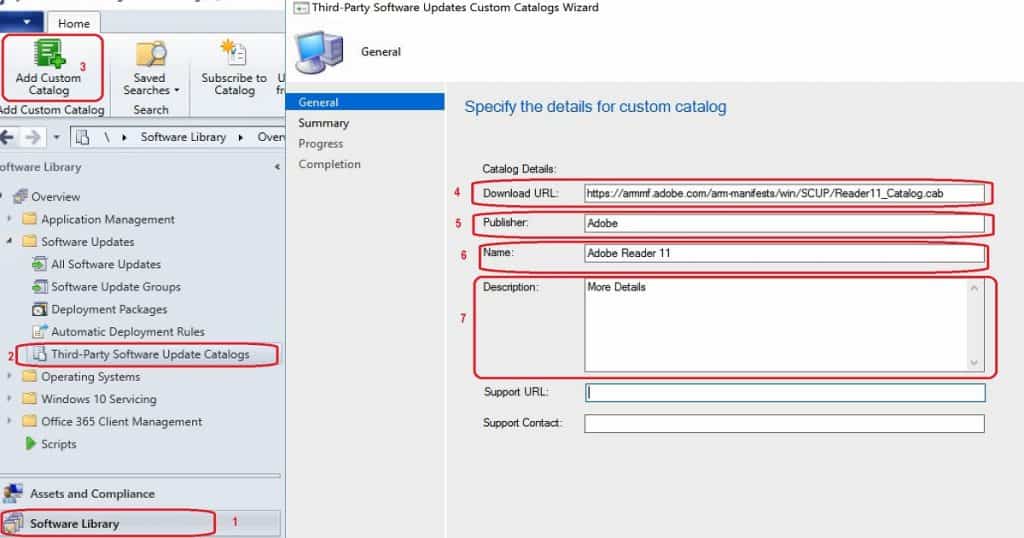
- Click on Add Custom Catalog from the ribbon menu.
In the Third-Party Software Updates Custom Catalogs Wizard, you must provide the following details: The next four(4) values are mandatory.
- Download URL – https://armmf.adobe.com/arm-manifests/win/SCUP/Reader11_Catalog.cab
- Publisher – Adobe
- Name – Adobe Reader 11
- Description – You can provide any text description.
NOTE! You will wonder how I got the DOWNLOAD URL Details for Adobe Reader 11 Third-Party Updates. I will explain this to you in a different blog post.
Subscribe to Custom Catalogs
The Subscribe to Catalog step is the following configuration for enabling the SCCM Third-Party Software Updates setup. The Third-Party Software Update Catalogs node allows you to subscribe to third-party custom and partner catalogs.
The subscription of partner and custom third-party catalogs helps SCCM environments to get regular updates (or patches) from third-party application vendors.
The following steps ensure that the SCCM environment is subscribed to the vendor’s product updates, similar to Microsoft Software updates.
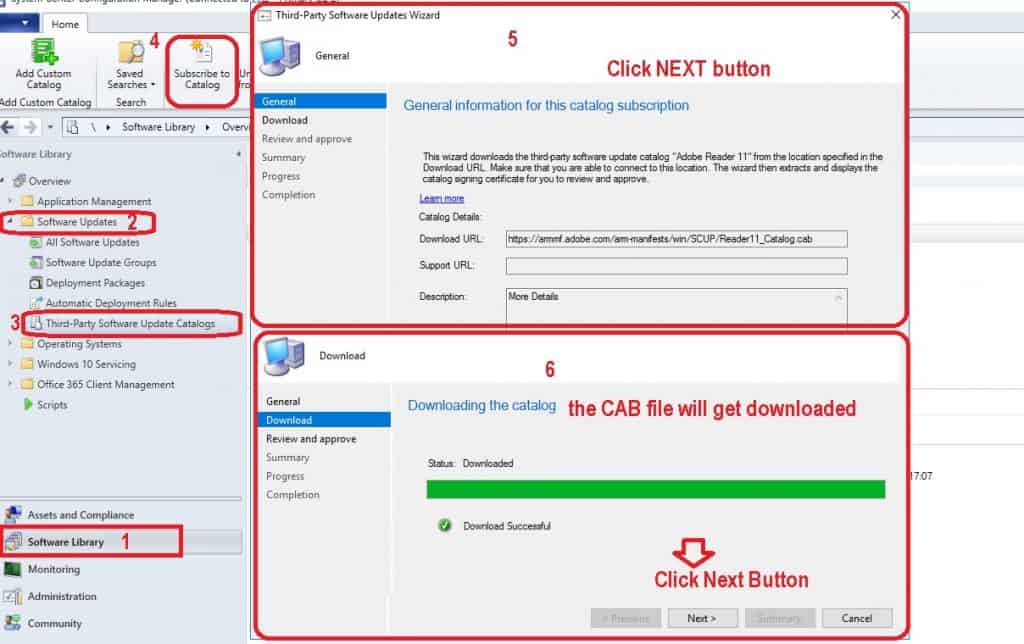
- Navigate to the Software Updates Library workspace from the SCCM console.
- Expand Software updates, and select the Third-Party Software Update Catalogs node.
- Select the Custom Catalogs to which you want to Subscribe to:
- I selected Adobe Reader 11
- Click the NEXT button from Third-Party Software Updates Wizard
- On the Download page of the third-party software update wizard, SCCM will download the CAB file using the URL you provided while adding a custom catalog.
NOTE! As I mentioned in the prerequisites section above, you need to have appropriate internet connections. If not, the download will fail, and you won’t be able to proceed with the third-party software update wizard. This wizard uses the same proxy connection you set up in the SUP configuration.
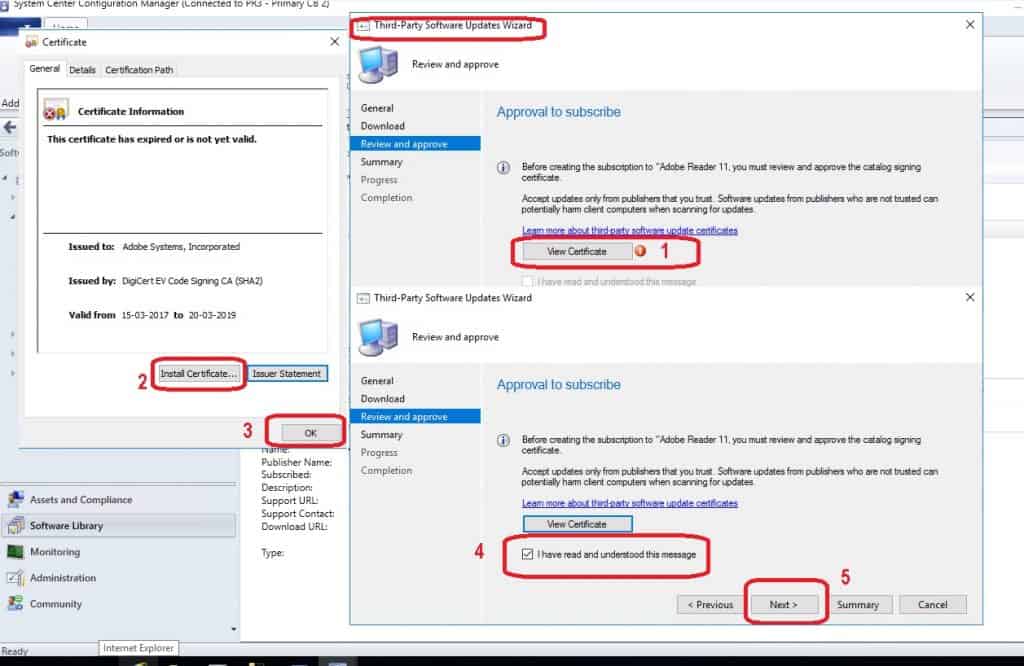
- Review and Approve the catalog certificate from the review and approve page of the Third-party updates wizard
- Click on the View Certificates box to view and review the certificate properties.
NOTE! I recommend reviewing and installing the Certificate on the Local Machine (Default location). If you don’t do this, Publishing third-party update content will fail in the later stage of this process. As I mentioned in the above section, you can check the certificate details in the Certificates node of the SCCM console.
- Click the OK button on certificate properties windows.
- Click on the Checkbox near “I have read and understood” to agree and proceed further.
- Click on the Next button to continue and finish the subscription process of the third-party catalog.
- Click on NEXT on the Confirm Settings page.
- FINISH the wizard to start the metadata updates synchronization onto WSUS.
- Click on Adobe Custom Catalog and initiate a Sync (Sync Now button from the ribbon) from the Third-Party Software Update Catalogs node.
- Make sure the Last Sync Status is SUCCESS.
The above sync will import all the Adobe Reader 11 updates into the WSUS database. For more information, refer to the log file SMS_ISVUPDATES_SYNCAGENT.log.
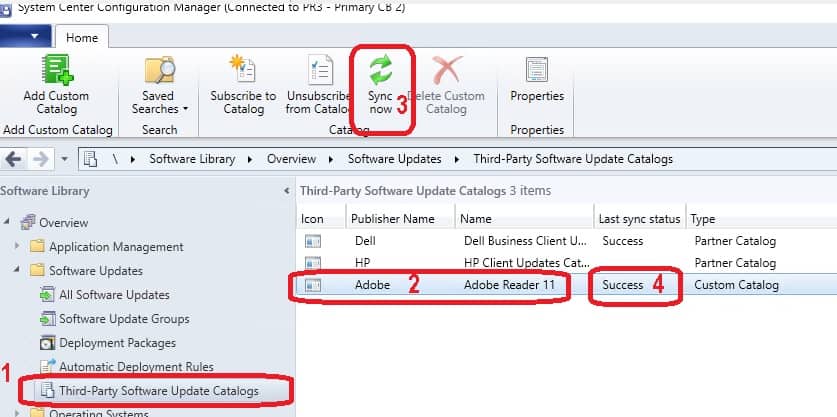
NOTE! – The above Sync (use Sync Now button from the ribbon) from \Software Library\Overview\Software Updates\Third-Party Software Update Catalogs won’t make the metadata of Adobe Reader 11 updates available in the SCCM console.
Products Selection
Now, you can see the Adobe Reader underneath “All Products—Adobe Systems. Inc.” in the Software Update Point Component Properties window.
Select the product “Abode Reader” as I showed in the below picture and click OK.
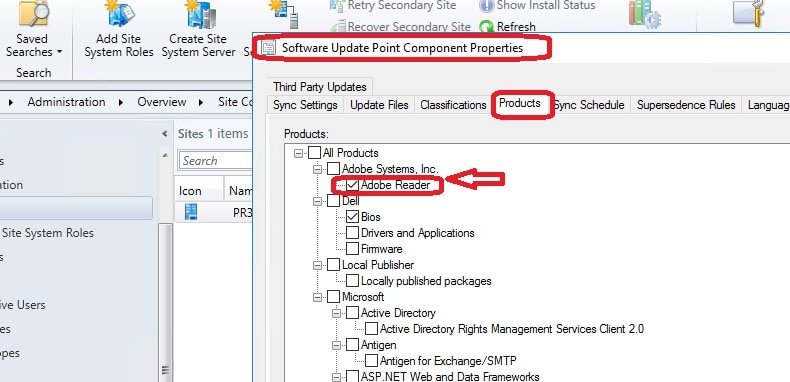
NOTE! – I have seen people complaining that some of the Abode patches are missing from the SCCM console. It could be possible that Adobe changed the product name. So, it’s recommended to check whether any new products got added or not. You might need to enable those new products from software update point component properties.
Another Sync
It’s time for another Sync, but this time, it’s not from the same place. Follow the below steps to make all Adobe Reader 11 updates (metadata) available in the SCCM console’s “All Software Updates” node.
- Navigate to \Software Library\Overview\Software Updates\All Software Updates.
- Click on the Synchronize Software Updates button from the ribbon menu.
- After successfully finishing this sync (WSYNCMGR.log to verify), you can see all the Adobe Reader 11-related updates, as shown in the following picture.
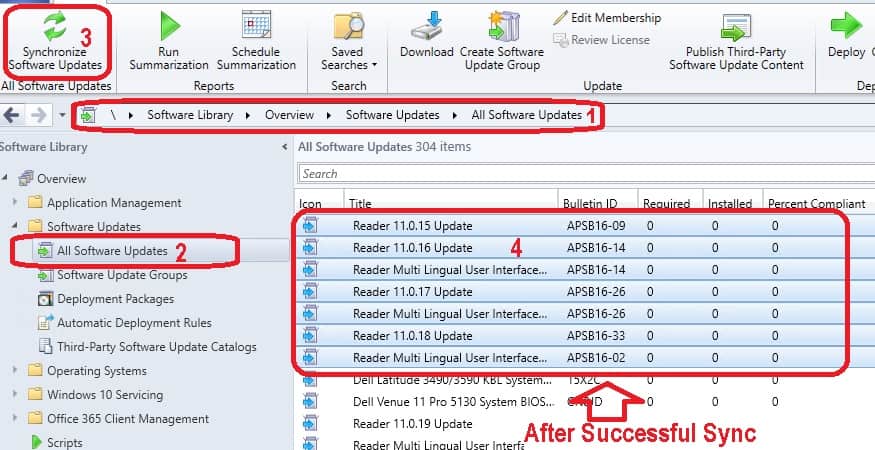
NOTE! – Check out the BLUE color icons for Adobe Reader 11 updates metadata (metadata-only updates = BLUE). More details about the change of Third-Party Software Updates icons are below.
Publish Third-Party Software Update Content
Once the third-party software updates are available in the console, you can publish those Adobe Updates to WSUS.
The following steps will help you publish Adobe Reader Third-Party Software Update content to WSUS.
- Navigate to \Software Library\Overview\Software Updates\All Software Updates node
- Select the Abode Reader Updates you want to publish.
- Click on Publish Third-Party Software Update Content button from the ribbon menu.
- Check out SMS_ISVUPDATES_SYNCAGENT.log to monitor the progress.
- The update files (for Adobe, it was . MSP files) will get downloaded to a temporary folder called C:\Program Files\Microsoft Configuration Manager\ISVTemp. (the folder name ends with .mrm or .mgm or some random name – that is nice)
NOTE! – When you publish third-party software update content, any certificates used to sign the content are added to the site. If you don’t install the certificates used to sign the third-party update content, publishing the content might fail.
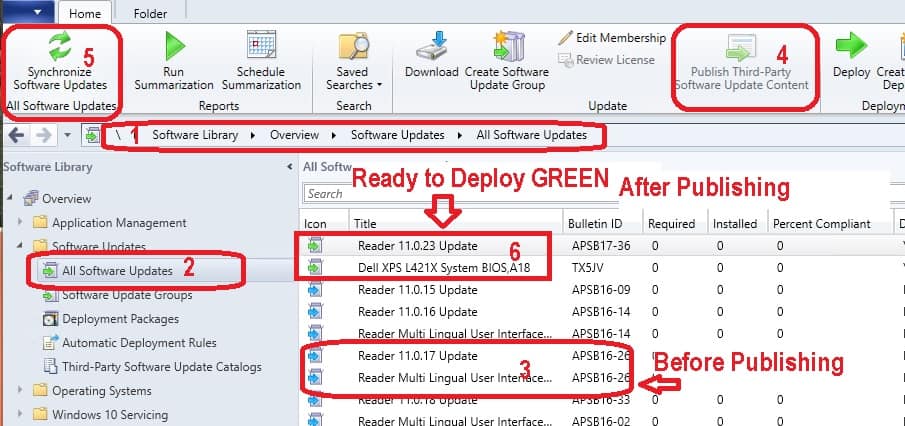
You can also check whether the certificate status is BLOCKED or UNBLOCKED from the SCCM console (\Administration\Overview \Security\Certificates). If the certificate is blocked, there is a chance of failure in the publishing process.
- Once the publishing process is finished, you might need to perform another Sync (WSyncMGR.log) to make the software update available for SUP to deploy and change the icon from BLUE to GREEN.
Download and Deploy SCCM Third-Party Software Updates
Now, it’s time to download and deploy the SCCM third-party software updates to Windows devices.
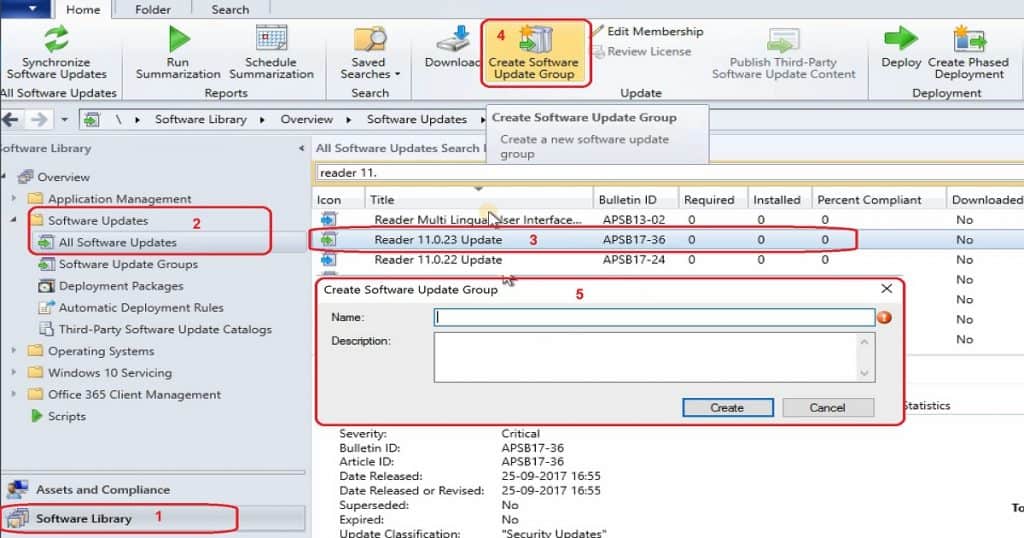
Create Software Update Group
The following steps will help you create a Software Update Group, Download and Deploy the third-party updates.
- Navigate to \Software Library\Overview\Software Updates\All Software Updates node.
- Select the third-party software updates that you want to download and deploy.
- Click on Create Software Update Group.
- Enter the name of the software update group = Reader 11 0 23 (“.” is not allowed)
- Enter the description of the group.
- Click OK to finish the creation of the Software Update Group.
Start Deploy Software Update Wizard
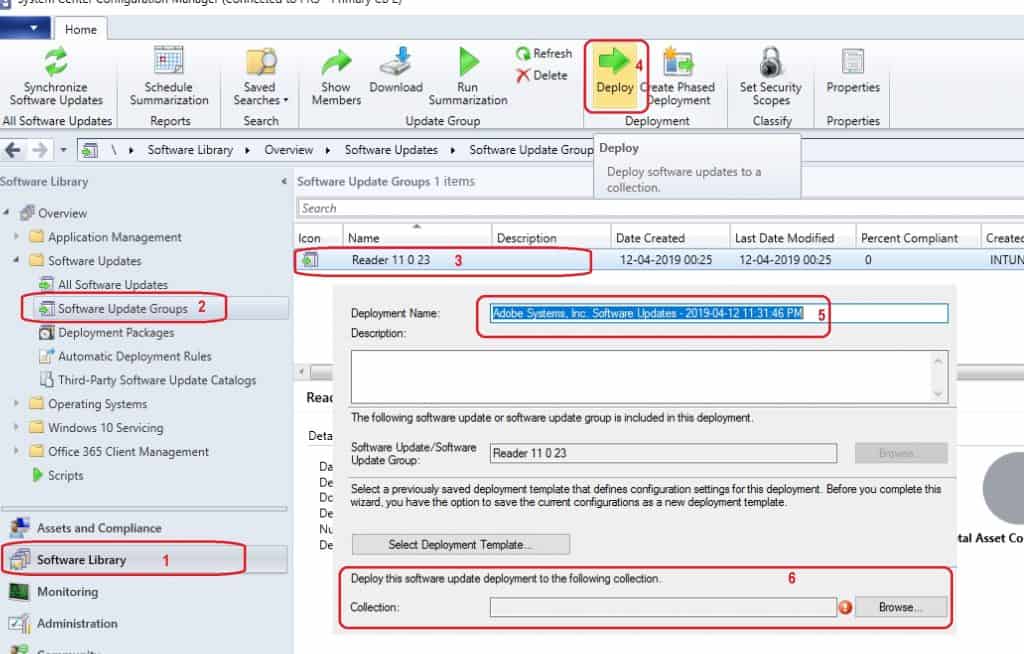
You have already created Software Update groups in the above section. Now, you can start the deployment wizard for third-party updates.
You can select the third-party update deployment and device collection names in this section.
- Navigate to \Software Library\Overview\Software Updates\Software Update Groups.
- Select the Reader 11 0 23 groups created above and click on the Deploy button on the ribbon.
- Follow through with the deployment wizard.
- Deployment Name = Adobe Systems, Inc. Third-Party Software Updates
- Select the Collection of devices you want to deploy Third-Party Software update and Click Next.
Scheduling & Deployment Settings
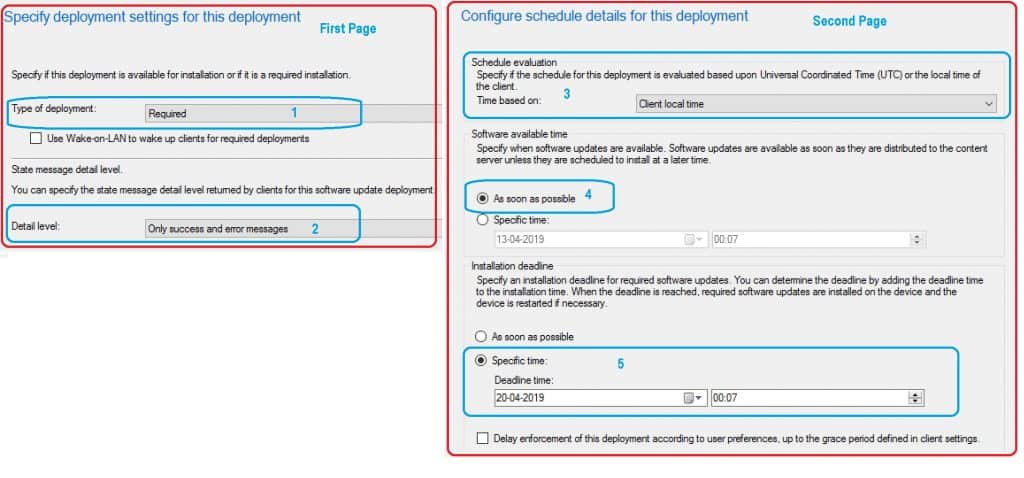
This section helps to schedule the third-party software updates.
- Specify Deployment Settings for this deployment.
- Type of deployment = Required.
- Details level = Only Success and error messages.
- Click on the Next button.
- Configure Schedule Details for this Deployment.
- Schedule Evaluation – Time Based on: Client Local Time.
- Software Available Time – As soon as possible.
- Installation Deadline – Specific Time.
- Click on the Next button to continue…
User Experiences & Alerts
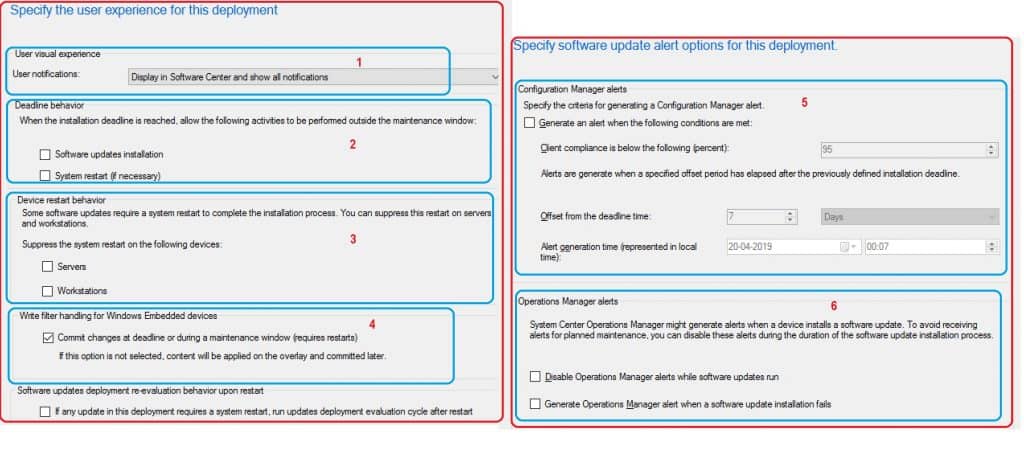
I selected all the default settings in the following two pages of User Experiences & Alters.
- Specify the User Experience for this Deployment – User Visual Experience.
- User Notifications – Display in Software Center and show all notifications – Default option.
- Deadline Behavior – When the installation deadline is reached, allow the following activities to be performed outside maintenance windows:
- Software update installation
- System Restart (if necessary)
- Device Restart Behavior – Some software updates require a system restart to complete the installation process. You can suppress this restart on servers and workstations.
- Suppress the system restart on the following Devices:
- Servers
- Workstations
- Write filter handling for Windows Embedded devices
- Commit changes at the deadline or during a maintenance Windows (requires restarts) – Default option
- Suppress the system restart on the following Devices:
- Specify Software Update Alert Options for this deployment
- Configuration Manager Alerts
- Operation Manager Alerts
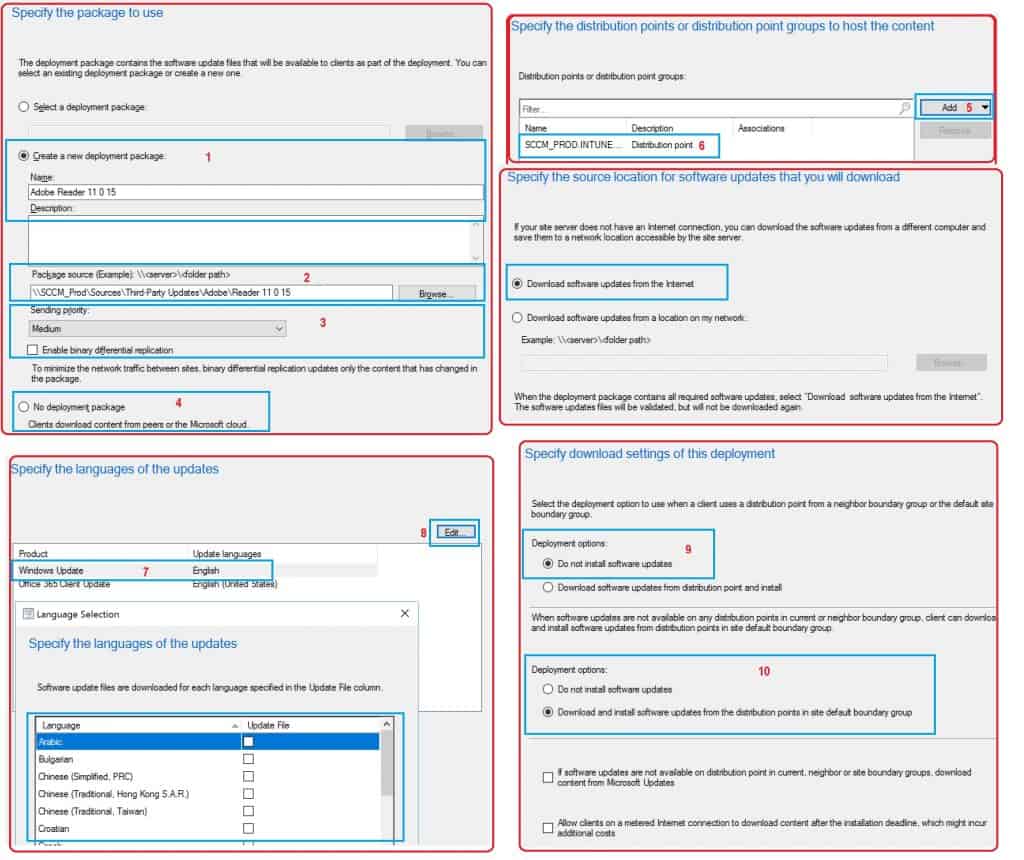
Create Deployment Package – Third-Party Software Updates
The section will help you understand how to create a third-party software update package.
- Specify the Package to Use page
- Create a new deployment package:
- Name – Adobe Reader 11 0 15
- Package Source – UNC Path – \SCCM_Prod\Sources\Third-Party Updates\Adobe\Reader 11 0 15
- Sending Priority – Medium
- Enable Binary Differential Replication (Not Mandatory – But Recommended settings)
- No Deployment package (NOT Mandatory Option)
- Clients download content from peers or Microsoft Cloud (NOT a Suitable option for Third-Party Updates).
- Click Next to go next page.
- Create a new deployment package:
- Specify the Distribution point groups to host the content
- Specify the Languages of the updates
- Product – There are two products-Windows Update and Office 365 Client Update – The language selected is English
- There is an Edit option to add another language if available from third-party software updates.
- Click NEXT
- Specify the Languages of the updates
- Add Distribution Point and click Next.
- Specify the source location for the Software Update that you will download
- Download software updates from the Internet
- Specify Download Settings of this Deployment
- Deployment Options
- Do not install software updates
- Deployment Options
- Download and Install Software Updates from the Distribution points in the site default boundary group
- Deployment Options
Conclusion
Now, you have deployed the third-party software updates. You can check out the content distribution status from the SCCM console. The deployment success with third-party software updates compliance report from SSRS.
Resources
- SCCM Third-Party Software Updates Setup Step-by-Step Guide Post Video Guide
- Free SCCM Catalog List – SCCM Third-Party Updates Post 2
- How to Install, Configure and Integrate with SCUP 2017 with SCCM
- How to Publish 3rd Party Abode Acrobat Patches via SCCM SCUP 2017
Bonus Details
Subscribe to a custom catalog Wizard template:
Subscribe To Catalog
• Catalog Name: Adobe Reader 11
• Publisher: Adobe
• Description: More Details
• Support URL :
• Support Contact :
• Download URL: https://armmf.adobe.com/arm-manifests/win/SCUP/Reader11_Catalog.cab
Create, Download, and Deploy Third-Party Software Updates Package Template:
Updates Targeted:
• Reader 11.0.11 Update APSB15-10(Article ID)
General:
• Deployment Name: Adobe Systems, Inc. Software Updates
• Collection: Test Static Collection
Deployment Settings:
• Send wake-up packets: No
• Verbosity Level: Only success and error messages
Scheduling:
• Deployment schedules will be based on: Client’s local time
• Available to target computers: 13-04-2019 02:41:00
• Deadline for software update installation: 20-04-2019 00:07:00
• Delayed enforcement on deployment: No
User Experience:
• User Notifications: Display in Software Center and show all notifications
• Install software updates outside the maintenance window when the deadline is reached: No
• Restart system outside the maintenance window when the deadline is reached: Suppressed
• If a restart is required, it will be: Allowed
• Commit changes at the deadline or during a maintenance window (requires restarts): Yes
• If any update in this deployment requires a system restart, run updates deployment evaluation cycle after restart: No
Alerts:
• On software update installation error generate a Window Event: No
• Disable Window Event while software updates install: No
Package:
The software updates will be placed in a new package:
• Adobe Reader 11 0 15
Content (1):
• SCCM_PROD.INTUNE.COM
Software updates that will be downloaded from the internet
Reader 11.0.11 Update
Windows Update Language Selection:
English
Office 365 Client Update Language Selection:
English (United States)
Download Settings:
• Computers can retrieve content from remote distribution points: No
• Download and install software updates from the fallback content source location: Yes
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc

Hello,
I’ve followed your step by step but I’ve a strange behavoir.
I’ve tried with the “Adobe Flash Player Plugin” Update (version 32.0.0.171).
I have deployed it to a test computer with an older version installer (32.0.0.141).
The update isn’t seen from the computer and from the report it says: ALREADY COMPLIANT.
Also the required column is 0, and also the column already installed is 0.
It could be because of the issue at the client side. Are you sure you have Adobe Flash Player installed on the client machine and that requires this particular updates? Did you check the log files and event logs to confirm the same? Also, worth checking the certificates installed on the client machine.
Hello,
Yes I’m sure it’s installed.
Version actually installed is: 32.0.0.142 NPAPI
Version deployed is: 32.0.0.171 NPAPI
What I have to check exactly?
Also it’s strange that the “Required” and the “Installed” column for the update are = 0 (since the deployment says: COMPLIANT … which means…installed)
I have mentioned about Group Policy and Cert requirements in the guide and linked to https://docs.microsoft.com/en-us/sccm/sum/deploy-use/third-party-software-updates#configure-the-wsus-signing-certificate. Have you checked this requirements?
So I wanted you to check the general Software Update troubleshooting flow at the client side as explained in the below guide
https://sudheesh.azurewebsites.net/?p=34 (Check out CLIENT SIDE troubleshooting section)
Hello Anoop,
Cert is installed (although if there was a problem with the certificate, I would have problem with the installation, not the detection).
Policy is set to allow third party (also via CM Client Policy; and checked regkey it’s present and configured).
I’ve checked the client side troubleshooting section and unfortunately no clue in the logs.
Unfortunately, I don’t have any other suggestion because I don’t have any clue what is happening. I might need to test and re-pro the issue later whenever I get time.
I would still think there would some hints like whether the policy is received by client or is it evaluated by client etc … that would help you further troubleshooting
Solved 😆
my bad … this Adobe Flash update nomenclature is getting me crazy. On SCCM you have PPAPI & Plugin … I needed the Plugin one and not the PPAPI…
I will test out also Reader & Pro just to make sure it works.
Thank you in advice and sorry 😆
SCCM 3rd party patching works 🙂
Thank you for sharing your experience here
Thanks for the guide Anoop! It was helpful.
I am trying to deploy an Adobe Reader 2015 Classic Track update using your instructions.
The SMS_ISVUPDATES_SYNCAGENT log gives me this error when I try to publish third-party software update content:
Failed to publish update “07c4ec0f-71cd-49f7-94f3-aa3da81fb72b” due to missing update metadata.
Possible cause: The update may have been synchronized to WSUS outside of Configuration Manager.
Solution: Synchronize the update with Configuration Manager before attempting to publish it’s content. If an external tool was used to publish the update metadata then use the same tool to publish the update content.
I followed your instructions exactly. I did not use an external tool like the message indicates. Do you know where I might look to solve the problem?
Thanks for any insight you may have.
This could be because you have not selected the updates category from software update point component configuration
How does this work with machine updates? I installed the Lenovo.cab and it downloaded a bunch of drivers, which was my intention. I’m learning how to use SCCM to image our machines. Can I use this method for Driver Packages? If so, how would I go about doing that?
In your case the Lenovo cab should provide the driver updates via custom catalog, then only you can use this feature to update drivers on Lenovo devices. I have not tested the Lenovo catalog to confirm this behavior. I hope you have tried to add custom catalog – https://www.anoopcnair.com/list-of-free-sccm-catalogs-third-party-updates/#List_of_Free_SCCM_Catalogs_Download_URLs
Yes. I did use a custom catalog and followed the steps up to publishing the software. But I’m not sure if I need to do the steps after that since these aren’t actually software updates, they’re drivers. Would I need to do something under Operating Systems > Driver Packages for the drivers to push correctly?
Yes you need to follow the steps mentioned in the post to update the drivers which are already installed. You don’t have to perform Driver package stuff IMHO…
Sounds good. Thank you for your help and really great guide.
Thank you much. Happy to hear it helped 🙂
Hello,
Again great article.
I still have a problem with the 3rd party updates.
For Adobe Reader DC & Adobe Acrobat DC – I can sync updates but under “REQUIRED” I have 0 for every available update.
Have you tried the scan the clients and check again ?
Hello,
Again Great article.
I can get the adobe reader & adobe acrobat updates to work.
The updates are synced successfully but show that aren’t required on any machine (which obviously isn’t true).
I then checked the Report: Compliance 2 – Specific software update and break it down to my computer to see what it was showing.
I then selected “Update Class” and … I can see only Adobe Flash player as a result of “indexed” updates – no trace of a Adobe Reader or Adobe Acrobat update.
So my guess is now, is it possible that the hw inventory in some way doesn’t report back to the update point the whole software list?
I think this is to do something with scanning as you mentioned in the above comment.
Yeah but what could be possibly wrong?
I mean Flash player is seen as required.
So what could I check?
Scan agent .log might provide some details. The client side troubleshooting of 3rd party software updates is similar to normal sccm software updates troubleshooting
Hi,
Thanks for your great post.
I’ve suscribed to Dell catalog, and I notice that I’ve no Dell drivers which are required by my clients (1500 Dell machines).
Which is quite strange..
Do you think I need to enable additional hardware inventory classes in Client Settings? Or is there any reasons?
Thanks in advance
Hi, I never a heard about updating hardware inventory to cater the requirement of driver updates.
Have you checked the Dell machines and checked the requirement of driver update ?
What I’m trying to say is “are those machines require a driver update” ? Or the drivers installed on those machines are not there in the dell catalog
You need to install the dell open manage inventory agent first
Hi Anoop
This is very helpfull post to configure the third party updates, Please help to share how we can cleanup the older updates metadata and contents from SCCM site server and systems as well as content from source location. So that we can maintain our SCCM environment.
You might be able to workout something with the following blog post from Kannan https://www.anoopcnair.com/sccm-wsus-maintenance-cleanup-tasks/
Hello!
Great article! As far as the update package creation is concerned, what is the source of the files? I don’t have \SCCM_Prod\Sources\Third-Party Updates and checking the content tab of one of the Adobe updates shows another UNC path that I can’t seem to locate on my server.
Any help is appreciated!
Hello You need to create a source folder. SCCM will automatically create content for you
Hello Anoop,
The pre requisites which you have mentioned are not complete. please refer https://docs.microsoft.com/en-us/sccm/sum/deploy-use/third-party-software-updates
Thank you
Sorry can you kindly remove the server name, forgot to remove it.
I’ll remove it later before approving the comment. It’s won’t be visible or you can repost the log without that server name
thanks , Re-posted with server name.
Hi Anoop
After Turning on the SSL on update point, all the clients were stopped getting any updates. WuHandler showed error:
OnSearchComplete – Failed to end search job. Error = 0x80240440. WUAHandler 8/10/2019 2:32:10 PM 4552 (0x11C8)
Scan failed with error = 0x80240440. WUAHandler 8/10/2019 2:32:10 PM 4552 (0x11C8)
Its a WSUS Update Source type ({D3FC19DE-264D-4295-A309-0C42523AAF3E}), adding it. WUAHandler 8/10/2019 2:32:21 PM 4552 (0x11C8)
This device is not enrolled into Intune. WUAHandler 8/10/2019 2:32:21 PM 6748 (0x1A5C)
Device is not MDM enrolled yet. All workloads are managed by SCCM. WUAHandler 8/10/2019 2:32:21 PM 6748 (0x1A5C)
SourceManager::GetIsWUfBEnabled – There is no Windows Update for Business settings assignment. Windows Update for Business is not enabled through ConfigMgr WUAHandler 8/10/2019 2:32:21 PM 6748 (0x1A5C)
Existing WUA Managed server was already set (https:SERVERNAME:8531), skipping Group Policy registration. WUAHandler 8/10/2019 2:32:21 PM 4552 (0x11C8)
Added Update Source ({D3FC19DE-264D-4295-A309-0C42523AAF3E}) of content type: 2 WUAHandler 8/10/2019 2:32:21 PM 4552 (0x11C8)
Scan results will include superseded updates only when they are superseded by service packs and definition updates. WUAHandler 8/10/2019 2:32:21 PM 4552 (0x11C8)
Search Criteria is (DeploymentAction=* AND Type=’Software’) OR (DeploymentAction=* AND Type=’Driver’) WUAHandler 8/10/2019 2:32:21 PM 4552 (0x11C8)
Async searching of updates using WUAgent started. WUAHandler 8/10/2019 2:32:21 PM 4552 (0x11C8)
Async searching completed. WUAHandler 8/10/2019 2:32:25 PM 2824 (0x0B08)
OnSearchComplete – Failed to end search job. Error = 0x80240440. WUAHandler 8/10/2019 2:32:25 PM 4552 (0x11C8)
Scan failed with error = 0x80240440. WUAHandler 8/10/2019 2:32:25 PM 4552 (0x11C8)
Restarted the Server and client machines and still same issue. And as soon as I turned off the SSL , all start working again? Is there am misisng?
Hello,
I have the same Issue, Any update Please ?
Regards,
Hadjer YH
Hi Anoop,
thanks for the very good help for all of us.
How is it possible to remove third party products in: Administration – Site Configuration – Sites – Software Update Point Component Properties?
Thanks for your help
I found the solution with this wonderfull script:
https://gallery.technet.microsoft.com/Delete-3rd-Party-Updates-e5bf19fe
Hi Anoop,
Any idea how can we avoid the third party software updates [mainly the driver updates] to get install during the OSD process?
The updates are increasing the OSD time huge to complete.
Thanks you in advance!
Use windows 10 servicing instead of using In-place task sequence… it’s better in 1903 to 1909 updates … one example https://www.anoopcnair.com/windows-10-1909-deployment-enhancement/
I’ve gotten to step 8 (Another Sync)
I’m also looking at this documentation – https://thinkdeploy.blogspot.com/2019/07/lenovo-updates-catalog-v2-for-sccm.html
where it says I need to distribute LUC Agent v1005 but so far all the Lenovo updates that have synced are only showing as blue and I can’t download them. I get “All Software Updates in this selection are expired or meta-data only, and cannot be downloaded”
What am I missing here?
Hello,
How to cleanup the third party patches coming from SCUP or from Software Library > Overview > Software Updates > Third Party Software Update Catalogs?
All these patches remain under Software Library > Overview > Software Updates > All Software Updates …
Thanks,
Dom
Hello,
wouldn’t it be possible to just create an automatic deployment rule for all required updates?
I tryed this as I did for normal windows updates but it won’t download anything (and yes in All Updates it is shown as “required”).
Would be nice to see a guide for this.
Thank you in advance.
Manu
Hi Anoop,
many thanks for the great post! . It would be really good if you can guide , about updating drivers for existing clients with help of this ( such as if any special manufacturer related agent needs to be instlled first) specially Dell and HP
Thanks
Hello – Thank you. Can you give some specific examples from Dell or HP so that I can be sure about what you are looking for? If I understand correctly this is something to do with the Dell experience application for touchpad gestures (3 taps).
Dear Anoop C Nair,
I have an issue with 3rd party updates. our environment is running adobe DC 2017 and upgrade was downloaded in SCCM and deployed on some machines as well smoothly but, WSUS server certificate “3rd party WSUS signing certificate” expired and we regenerated a new signing certificate from our CA Server which is working with all the products updates except the adobe reader DC 2020 update. the .cab file which is available on WSUS is showing the old certificate in its properties. I have tried all the possible solutions but clients are still getting that old .cab file. i have removed that file from WSUS also from CM_sources and CM_packages but clients are still getting that old .cab file and giving error “Failed to download updates to the WUAgent datastore. Error = 0x800b0101.” I will be very grateful if you guide me how can I redownload the .cab file with updated certificate so client didn’t receive this error.
Thanks
Hi Anoop,
Excellent site…really informative and useful. I wondered if you’ve ever come across the following scenario. I’ve followed the steps, published a third party update (doesn’t matter which one, this happens to them all), downloaded the update to a content folder on the network, created a SUG and a deployment package and deployed to a test collection containing 1 machine. Deployment works fine…but the update also installs on all other devices running the application. I haven’t enabled any ADRs. This obviously makes it impossible for me to test any patch before deployment.
Thanks in advance.
Hi, we have a old 2008R2 server with SCCM 2002. I want to put in a new 2019 Server with SCCM 2107 and retire the old SCCM server. We are also using Endpoint and co-managed. What is the best method to get there?
Regards
Phil
SCCM 2002 Distribution points are running on the 2008 server? I think it’s better to create a new server and DP?