Let’s discuss Enable Windows Apps Get Diagnostic Info to Maintaining Security and Integrity using Intune. Let Apps Get Diagnostic Info” policy helps to controls whether Windows apps can access diagnostic information about other installed Windows apps, including the user name associated with those apps.
Windows Apps Get Diagnostic Info policy is designed by Microsoft Intune to allows administrators to manage app-to-app communication regarding diagnostic data, offering granular control over privacy and security in organization.
Organizations can enforce this policy for several reasons. Allowing access is essential for diagnostic tools or monitoring agents used by the organization’s IT department. These tools rely on this data to effectively troubleshoot issues, monitor performance, and detect conflicts between applications.
This policy is helpful for admins, users and organization. The policy is a fundamental tool for maintaining control, stability, and service quality across the device fleet. Admins can prove that they are enforcing a data minimization policy, which helps meet regulatory requirements.
Table of Contents
Enable Windows Apps Get Diagnostic Info to Maintaining Security and Integrity using Intune
This policy setting specifies whether Windows apps can get diagnostic information about other Windows apps, including user name. You can specify either a default setting for all apps or a per-app setting by specifying a Package Family Name. You can get the Package Family Name for an app by using the Get-AppPackage Windows PowerShell cmdlet. A per-app setting overrides the default setting.
- How to Enable or Disable Device Delete Setting for Diagnostic Data in Windows using Intune Policy
- Best Method to Allow Telemetry or Diagnostic Data with Intune
- Turn On Diagnostic Data Viewer in Windows 11
How to Configure Policy From Intune Portal
This policy allows administrators to enforce a consistent and secure behavior across all devices. For start policy creation sign in to Microsoft Intune admin center. Then go to Devices > Configuration > +Create >+ New Policy.
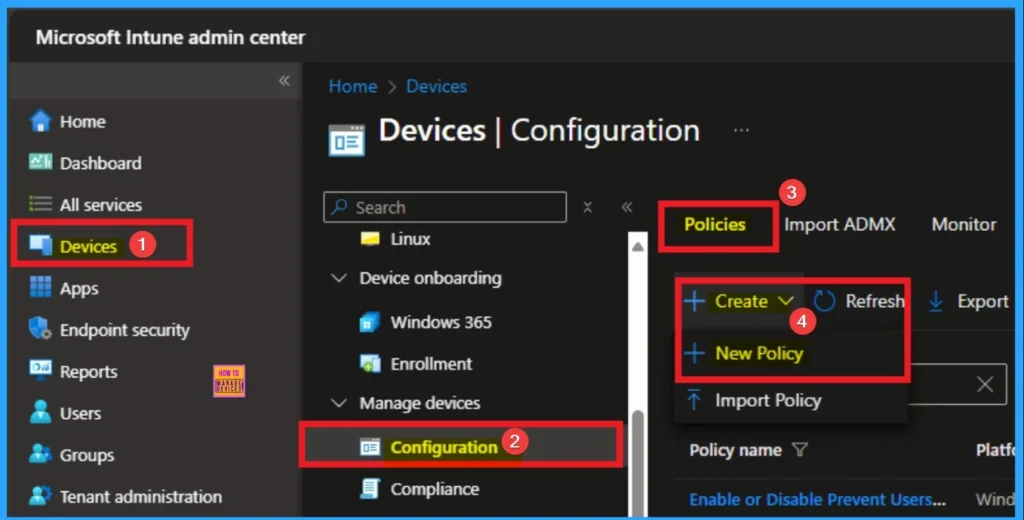
Selecting Platform and Profile Type
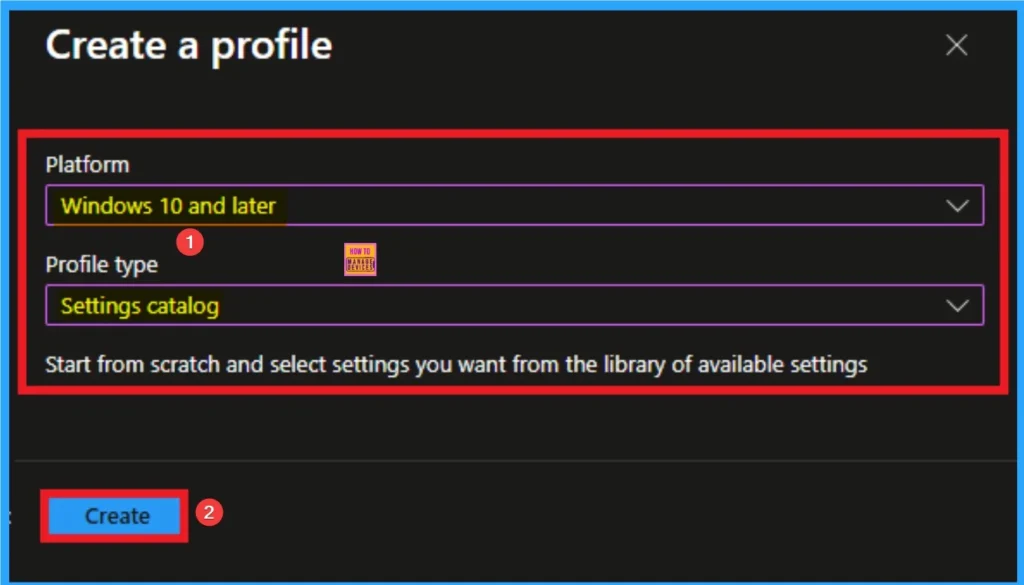
Selecting Platform and Profile Type is the next step we have to do. This is very essential to apply the policy to appropriate Platform and Profile Type. Here I would like to configure the policy to Windows 10 and later platform and settings catalog profile. Then click on the Create button.
Basics of Policy
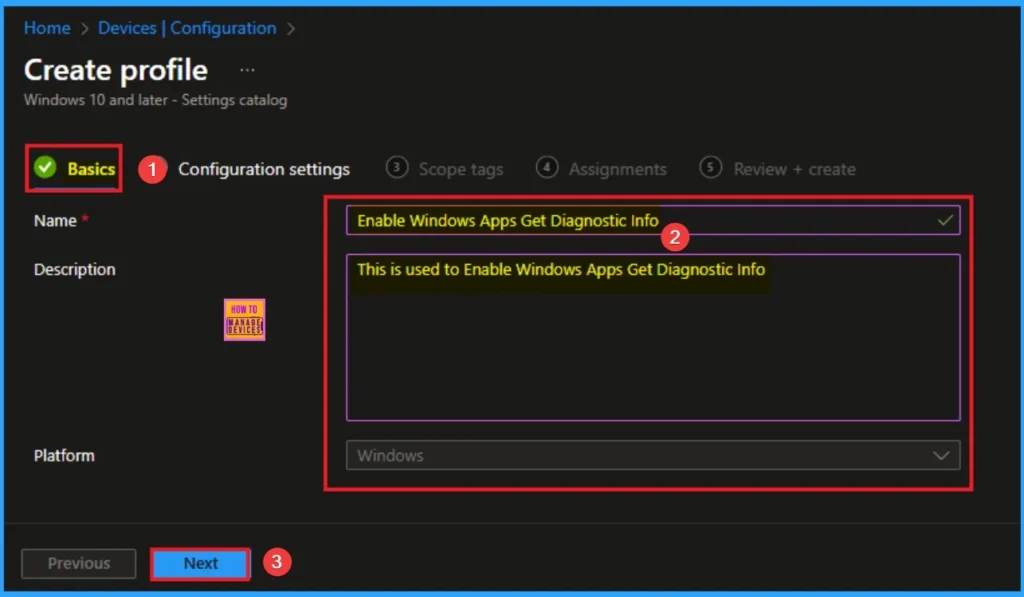
As per the heading, basic tab is the begging stage that helps you to add basic details like name and description for the policy. Here is Name is mandatory and description is optional. After adding this click on the Next button.
Configuration Settings for Selecting Settings
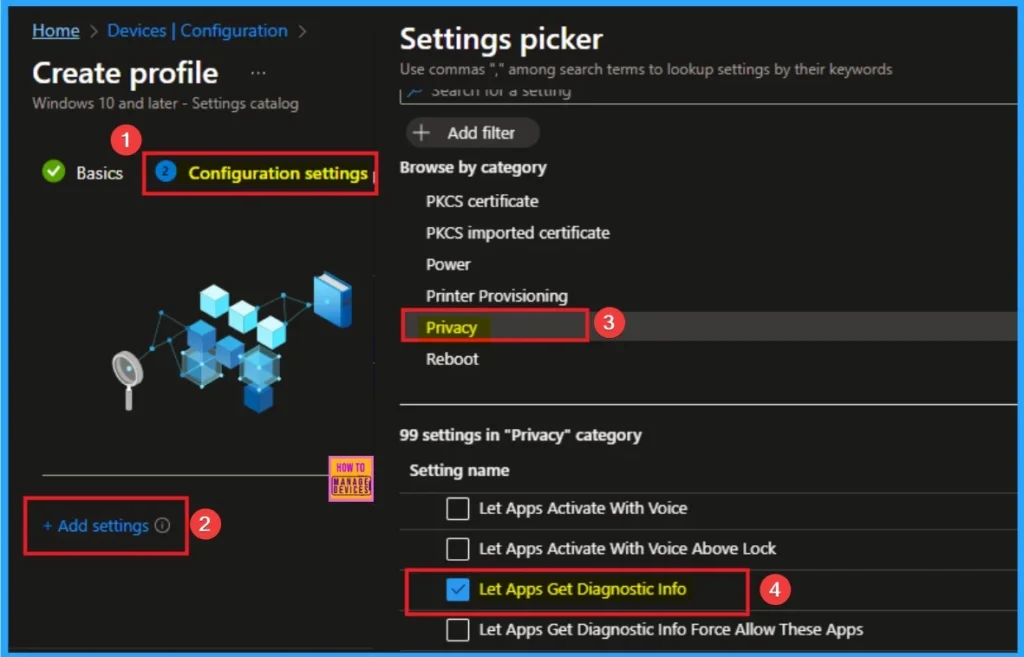
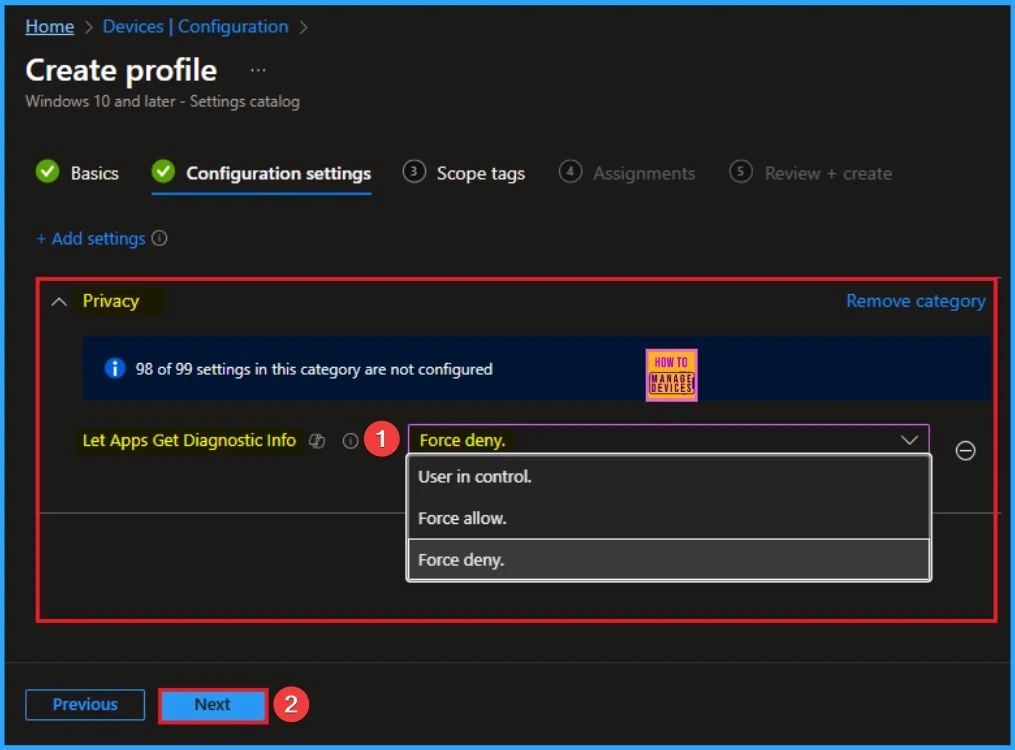
From the configuration settings tab you can access settings picker to select specific settings for policy creation. To get the Settings Picker, click on the +Add settings hyperlink. Here, I would like to select the settings by browsing by Category. I choose Privacy. Then, I choose Let Apps Get Diagnostic Info Policy settings.
Available Values
There are 3 values are available for this policy. You can choose any of these value according to the organization preferences. The below table shows the values and its details.
| Values | Details |
|---|---|
| Fore Allow | If you choose the “Force Allow” option, Windows apps are allowed to get diagnostic information about other apps and employees in your organization can’t change it. |
| Fore Deny | If you choose the “Force Deny” option, Windows apps aren’t allowed to get diagnostic information about other apps and employees in your organization can’t change it. |
| Disable or don’t configure | If you disable or don’t configure this policy setting, employees in your organization can decide whether Windows apps can get diagnostic information about other apps by using Settings > Privacy on the device. |
Adding Scope Tags
Scope Tags sections help you add restrictions to the visibility of the Policy. But it is not a mandatory step, so you can skip this step. Here, I don’t add scope tags for Windows Advertising Id Policy. Click on the Next button.
Selecting Group from the Assignment Tab
To assign the policy to specific groups, you can use the Assignment Tab. Here I click, +Add groups option under Included groups. I choose a group from the list of groups and click on the Select button. Again, I click on the Select button to continue.
Review + Create Tab
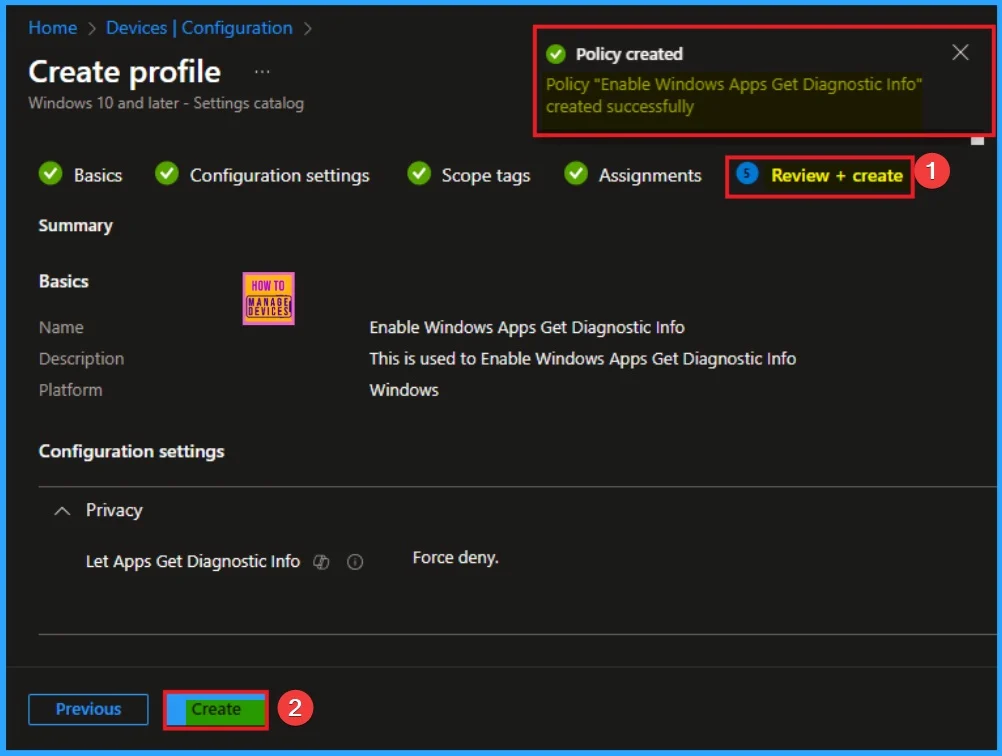
Before completing the policy creation, you can review each tab to avoid misconfiguration or policy failure. After verifying all the details, click on the Create Button. After creating the policy, you will get a success message.
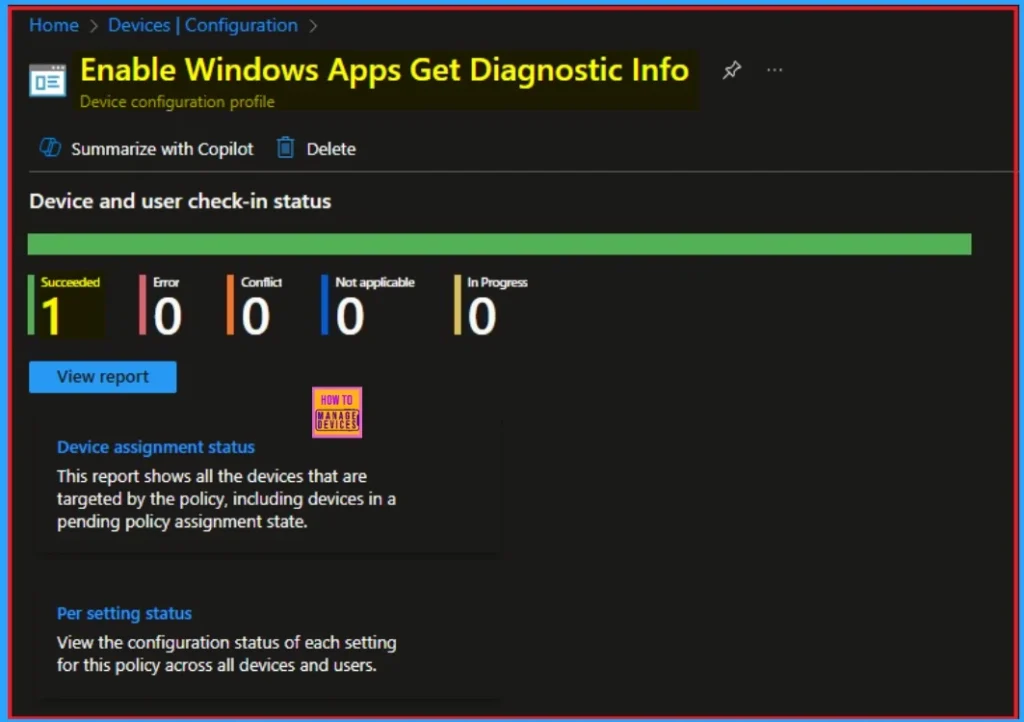
Monitoring Status
The Monitoring Status page shows whether the policy has succeeded or not. To quickly configure the policy and take advantage of the policy sync, the device on the Company Portal, Open the Intune Portal. Go to Devices > Configuration > Search for the Policy. Here, the policy shows as successful.
Event Viewer
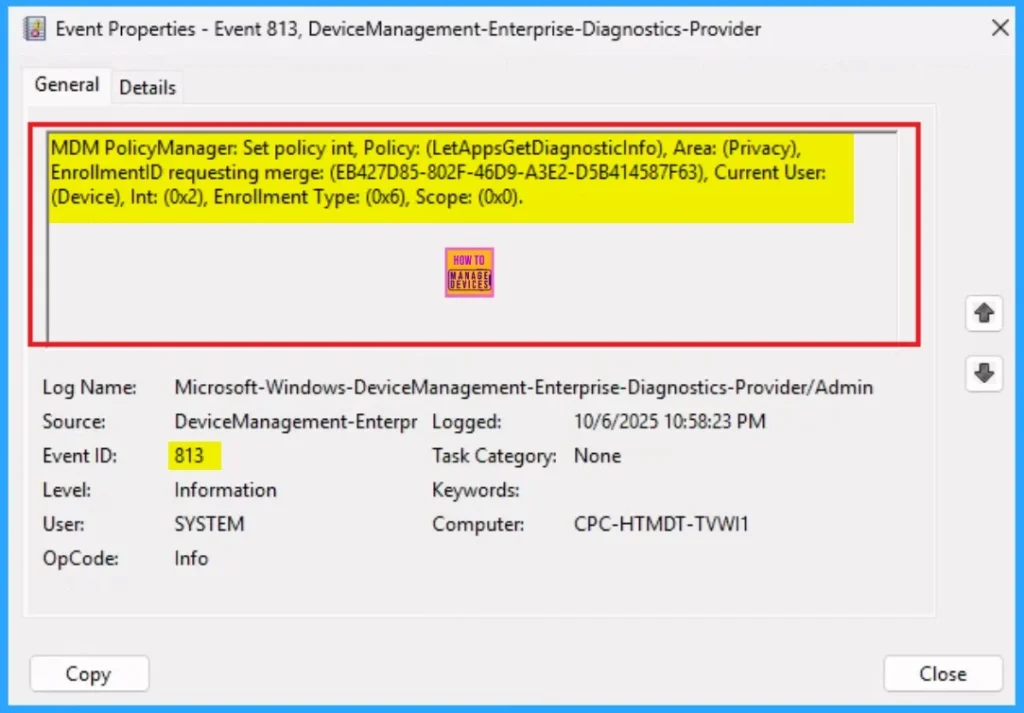
It helps you check the client side and verify the policy status. Open the Client device and open the Event Viewer. Go to Start > Event Viewer. Navigate to Logs: In the left pane, go to Application and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider > Admin.
- You will get the success result on Event ID 813
MDM PolicyManager: Set policy int, Policy: (LetAppsGetDiagnosticlnfo), Area: (Privacy),
EnrollmentID requesting merge: (EB427D85-802F-46D9-A3E2-D5B414587F63), Current User:
(Device), Int: (0x2), Enrollment Type: (0x6), Scope: (0x0).
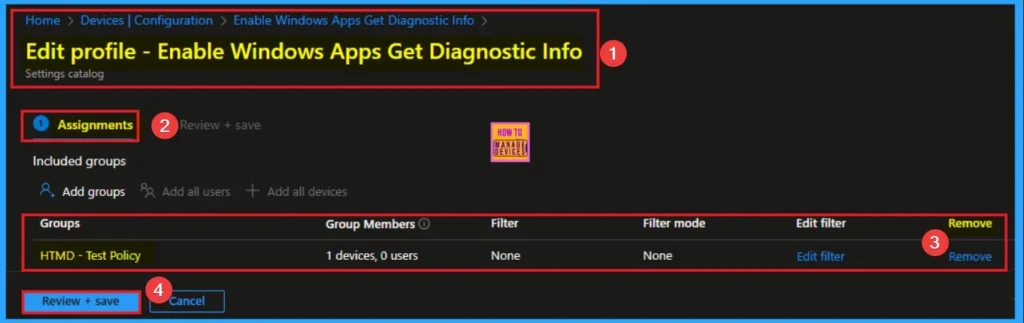
Removing the Assigned Group from Let Apps Get Diagnostic Info Policy Settings
If you want to remove the Assigned group from the policy, it is possible from the Intune Portal. To do this, open the Policy on Intune Portal and edit the Assignments tab and the Remove Policy.
To get more detailed information, you can refer to our previous post – Learn How to Delete or Remove App Assignment from Intune using by Step-by-Step Guide.
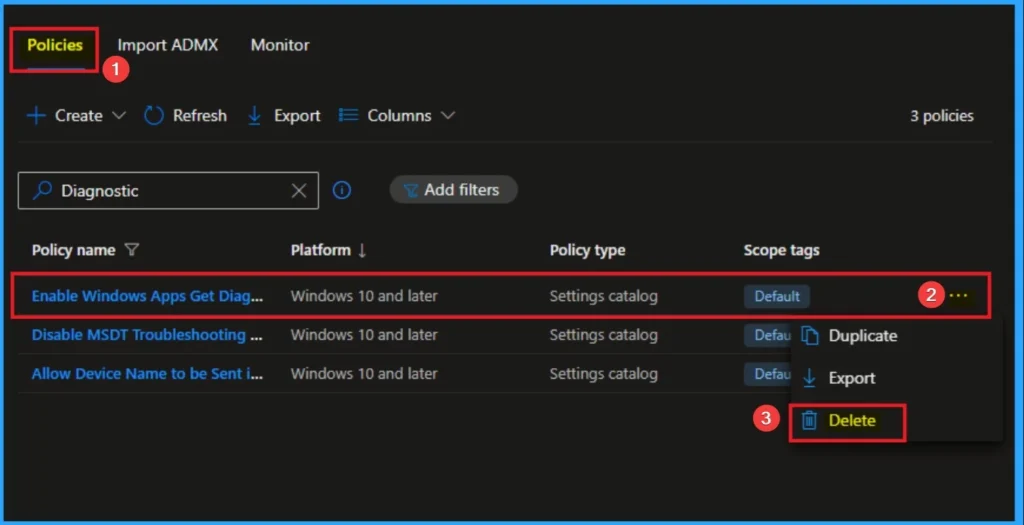
How to Delete Windows Apps Get Diagnostic Info Policy
You can easily delete the Policy from the Intune Portal. From the Configuration section, you can delete the policy. It will completely remove it from the client devices.
For detailed information, you can refer to our previous post – How to Delete Allow Clipboard History Policy in Intune Step by Step Guide.
CSP Details
If an app is open when this Group Policy object is applied on a device, employees must restart the app or device for the policy changes to be applied to the app. The most restrictive value is 2 to deny apps access to diagnostic data.

Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc


