Let us learn about the Infographic for Meltdown Spectre and Latest News. Infographics for Meltdown Spectre and Latest NewsMeltdown & Spectre vulnerabilities are taken the tech world by storm.
Specter vulnerability impacts Intel & other processors. The Tech world is confused by the number of patches released to fix these issues. Meltdown affects only Intel processors, and this can be fixed mostly by Operating System Updates.
In my opinion, Intel mishandled the entire situation. I have a post that explains a way to “Monitor Meltdown Spectre Vulnerabilities with SCCM.”
In this post you will get all the details of the Infographic for Meltdown Spectre and Latest News. Infographic for Meltdown Spectre and Latest News topic is explained in detail below.
Table of Contents
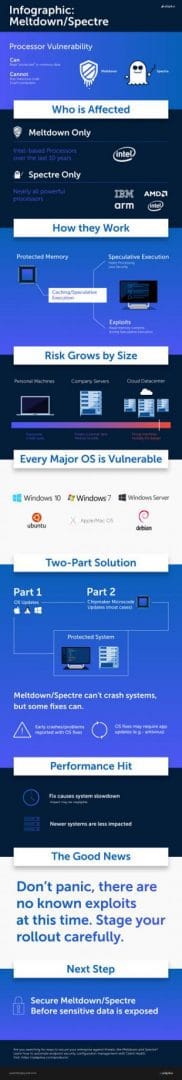
Bit More Details about Spectra/Meltdown Vulnerabilities – Infographic for Meltdown Spectre and Latest News
Meltdown and Spectre Variant 1 patches look fine as per the reports from various sources. But Intel is confusing the tech world with Spectre Variant 2 patches.
| Bit More Details about Spectra/Meltdown Vulnerabilities |
|---|
| Spectre variant 2 – CVE-2017-5715 (branch target injection) – Intel is going crazy |
| Spectre variant 1 – CVE-2017-5753 (bounds check bypass) |
| Meltdown – CVE-2017-5754 (rogue data cache load) |
They have hidden the issues with the patch released for “Spectre variant 2“. “DATA loss or corruption” issues were reported because of Intel’s patch for Spectre variant 2. This data loss or corruption issue is apart from unexpected reboot issues.
The hardware vendors like Dell, HP, and Lenovo started to recall their firmware update patches for Spectre variant two because of buggy patches from Intel. Microsoft released another out-of-band patch to Disable (their earlier patch) Mitigation against Spectre, Variant 2.
The latest update about meltdown and spectra is available in the following article. Keep an eye on the above link to keep updated with this news.
- Monitor Meltdown Spectre Vulnerabilities with SCCM Configuration Manager ConfigMgr
- July 2024 Windows 11 KB5040442 KB5040431 Patches and 4 Zero-Day Vulnerabilities
- Updated Windows 11 End-of-Life Dates
- Windows 11 Version Numbers Build Numbers Major Minor Build Rev
Steps to Bring Spectra and Meltdown Issues under Control for the organizations
Secure Windows systems from Meltdown and Spectre vulnerabilities carefully. OS patches are a no-brainer (not really for LOB apps), and you should apply those right away.
Deploy the patches after thorough testing in staging and pilot machines. Pilot testing of patching is essential as you know the removal or un-installation of the patches is not a very easy task.
Ideally, you should already be applying OS updates regularly as part of a comprehensive security configuration management policy. To keep your company secure, you must periodically validate the integrity of every endpoint’s compliance with corporate policy and vendor security fixes.
Download Infographic for Meltdown Spectre PDF
Adaptiva Client Health makes it easy to verify that every Windows endpoint in your enterprise meets security standards. It can automatically remediate non-compliant systems. To learn more about how to automate endpoint security at scale, request a free demo.
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP from 2015 onwards for consecutive 10 years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is Blogger, Speaker, and Local User Group Community leader. His main focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career etc…


Thanks for info Anoop.
The new out of band patch from Microsoft applicable only if some already deployed firmware updates and seeing some issues ??
Applicability of this patch in Microsoft update catalog website mention that , it’s applicable to AMD CPUs .
In which scenario this new out of band patch applicable ?
Thank you Ram for the comment. I didn’t notice that before and now, I’m confused 🙁
Considering the major implications these vulnerabilities present with Windows Credential Guard for Windows 10, this is just another reason why users would do well to stick with Windows 7 or those whom have Win10, to revert back to the Win 7 platform, since it is by it’s very nature, much core controllable, in terms of overall system security.
In Windows 10, as is now confirmed, there are far greater attack vectors and even greater exploitation possible as opposed to a properly hardened Windows 7 system.
It’s time for Windows users to face the music with regard to these security vulnerabilities of critical concern. Stay with Windows 7 for now. If you have Windows 10, the smart thing to do is down-grade to Windows 7 instead.
These recently discovered gaping holes in system security with Windows 10, are just a few of the many security risks you will encounter if you choose to swallow Microsoft’s Horse-Sh** by upgrading to or keeping Windows 10.
Microsoft is no different than any other money-hungry, fascist, corporate thug of an entity out there, hell bent upon taking advantage of us any way they can.
At least with Windows 7, you still have a fighting chance to not only lock down system security very tightly, but also to keep most, if not all of the corporate meddling via telemetry and other various methods, at bay, so long as you know what you are doing.
Don’t listen to Microsoft’s trolls and their corporate goons. With regard to Win10, they, like all the other fascist corporate creeps (including Google) only care about one thing———Exploitation for profit!
I agree with your sentiments. Most privacy-conscious Windows end-users definitely understand the serious implications of using a SAAS-model type operating system, such as Win10. It has vulnerability built right into to the architecture of the kernel and no amount of playing around with the Registry is going to solve the major issues surrounding the privacy violations inherent to the Windows 10 Operating System modules and interface.
You are also right about Windows 7. So long as you understand which mechanisms you need from the Microsoft Update as well as which ones to avoid, you can pretty much shield yourself from far greater risk than if you were a Win10 user.
However, equally important to accomplishing this, is that of having a complete understanding of system hardening. You must understand not only how to configure security applications properly, but you must also understand how to mitigate any risks to the attack surface. These concepts are a fundamentally important aspect of overall system security.