Today, we discuss a new topic: Allow Basic Authentication for HTTP using Setting Catalog Via Intune. We have discussed many setting catalog policies with you all. Now, let’s talk about Authentication for HTTP. You all know that security is very important for us nowadays.
In this case, setting catalog plays a vital role in the Microsoft Intune admin center. It provides security enhancements to the organization. You know that HTTP is how web browsers talk to web servers. When you enter a web address, your browser sends a request to the server hosting the site.
Basic Authentication for HTTP is when you use a username and password to access a website. Your browser sends this information to the server. This policy can be enabled through Intune by using the setting catalog, and it is the secure way for admins.
When this method is enabled, it does not require extensive configuration or additional software components. In this post, we can discuss enabling this policy through setting catalog.
Table of Contents
What is the Importance of Authentication for HTTP?
HTTP authentication is crucial for web security. It ensures that only authorized users can access sensitive data, tracks user activity for accountability, and personalizes user experiences.
Allow Basic Authentication for HTTP By using Setting Catalog Via Intune.
Above, I shared general things about authentication HTTP using the setting Catalog via Intune. This is the finest method to enable the policy. In this case, you can also turn off this policy for your organizations. Compared to another modern method, it’s not that secure.
- Enable Disable Secure DNS over HTTPS in Microsoft Edge
- Create Intune Policy using Graph Explorer API POST HTTP Method
- Total Number of Setting Catalog Policies for Windows, Apple and Linux
Create Profile
So, let’s look at how to create a profile of four people who deploy a policy. So first, we have to see that device option in Microsoft Intune and click on it. In the device section, you will get configuration option in the configuration option.
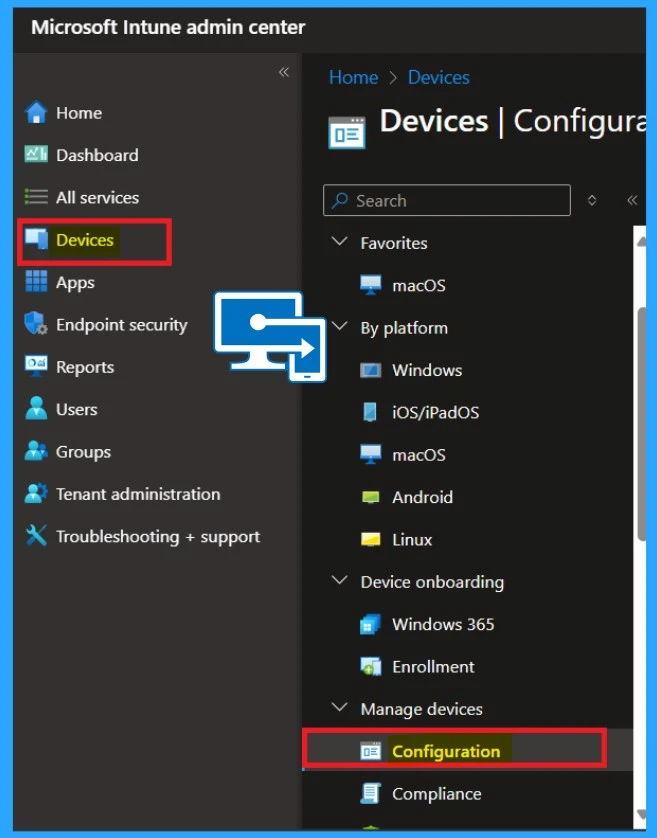
To get started, look for options like +Create and click on that. When you select the “Create” option, you will see two choices: “New” and “Import Policy.” Click on “New Policy.” In the new policy section, you will need to fill in some information, such as the platform profile type in the platform section.
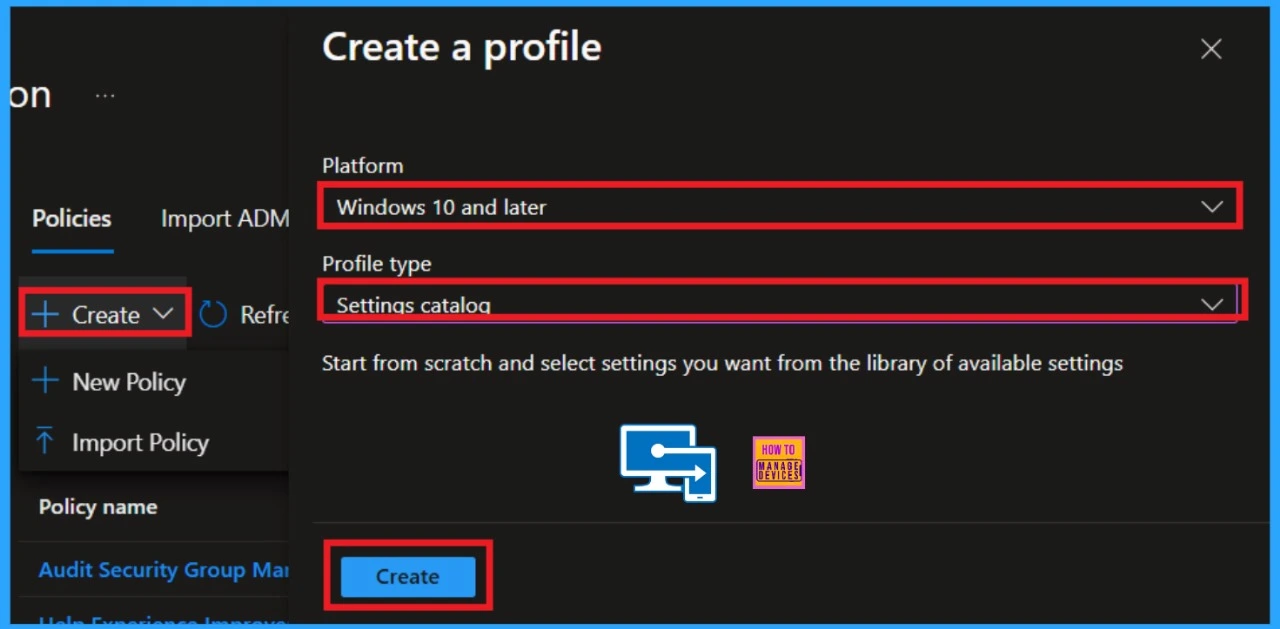
- Here, you should specify the platform; for example, I added “Windows 10 and later.
- Enter the setting catalog in the profile type. You can choose from the available options by clicking on the drop-down arrow.
- Once you have made your selections, click on the “Create” button.
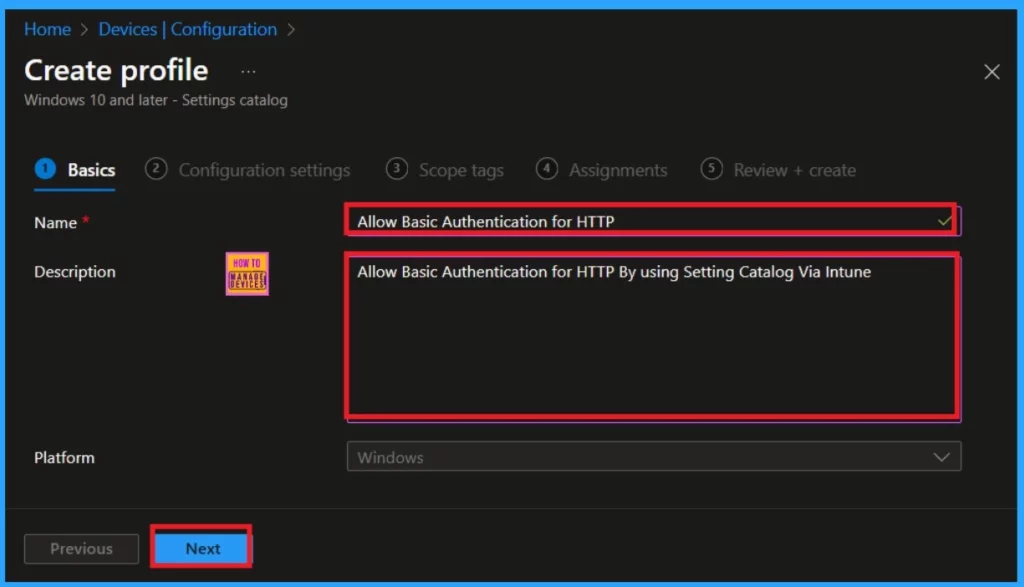
Basics
Microsoft offers several tabs for deploying a policy. The first step is to fill in the basic details. In this section, you need to provide the policy’s name, description, and platform options. I named the policy “Allowed Basic Authentication for HTTP” and added a brief description.
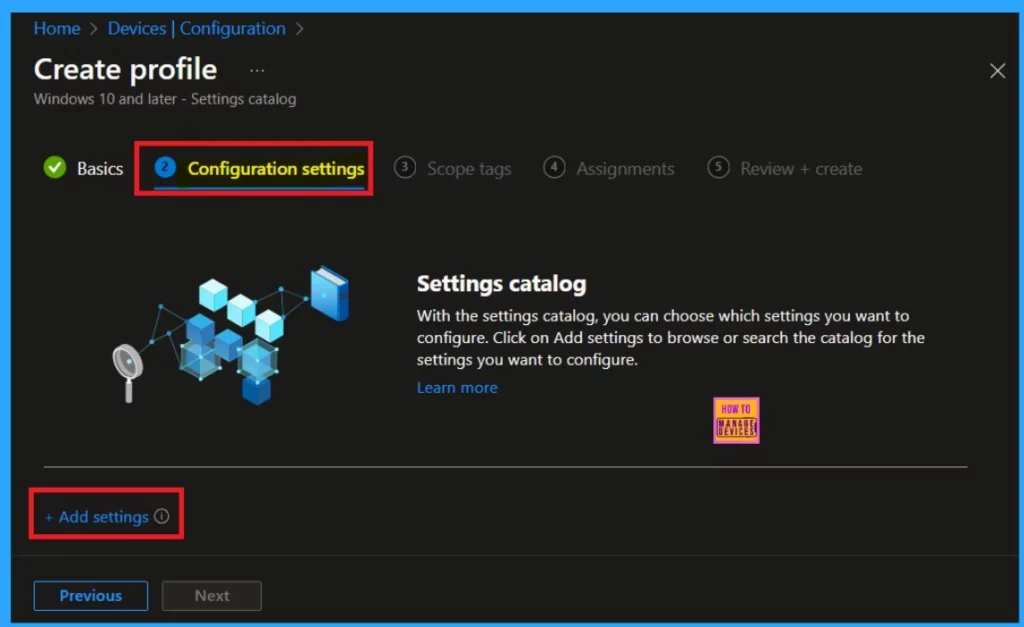
Configuration Settings
The configuration setting is the next section after the basic tab configuration setting. It is an important factor in Intune with this you can add settings to the organization. With the settings catalog, you can choose which settings you want to configure. Click on Add settings to browse or search the catalog for the settings you want to configure.
- Click on Add settings.
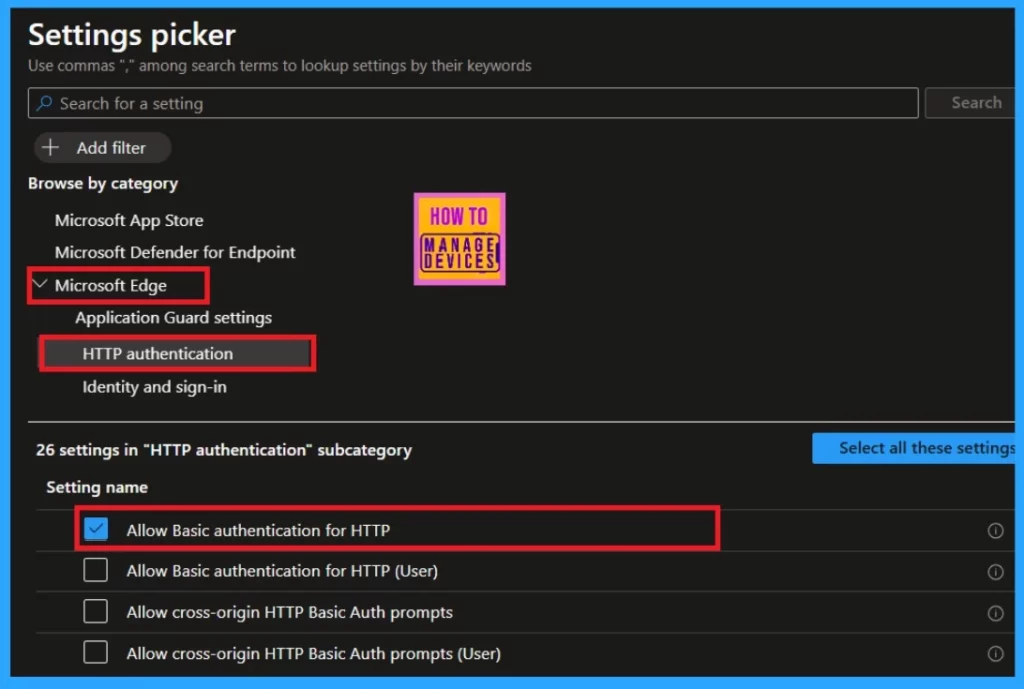
When you click on the added setting, you are on the Settings picker’s Settings page. Here, you can select the policy that you want to deploy. In the screenshot, you will see an option to add a filter in this category. You can select “Microsoft Edge” Click on the drop down arrow to reveal several settings.
One of these settings is for HTTP authentication. When you click on the HTTP authentication option, various setting names will be displayed. You can choose to allow basic authentication for HTTP by checking the corresponding checkbox, which will then be marked with a tick.
- After the selection you can close the Window of setting picker.
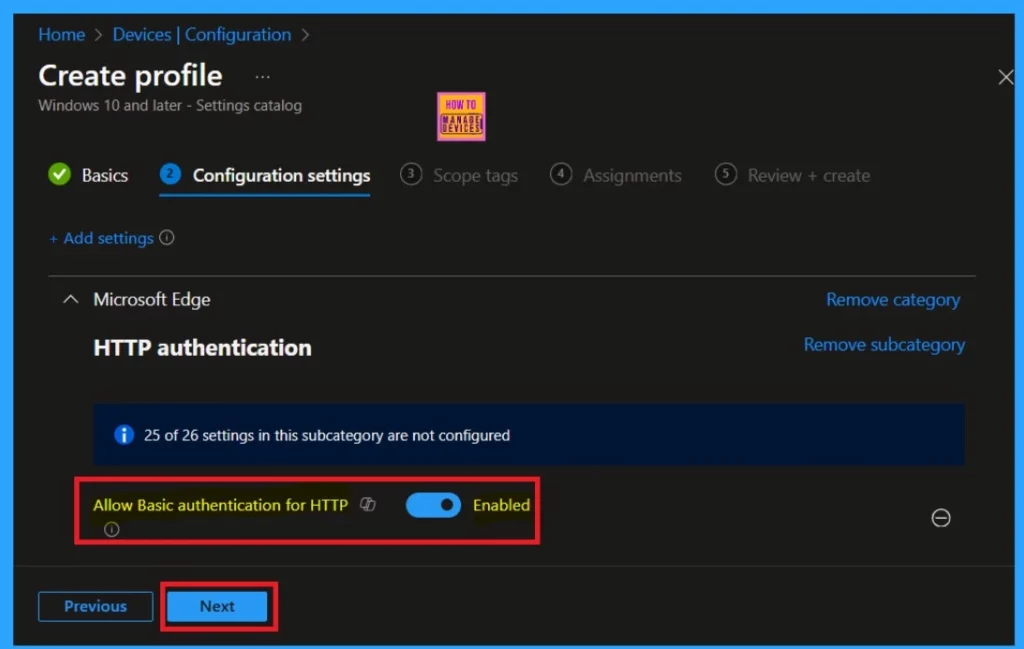
In the configuration settings, you will find an option for basic HTTP authentication that allows you to enable or disable the policy. To enable the policy, simply toggle the switch to the right. Once you’ve done that, you can proceed by clicking on the next option for further actions.
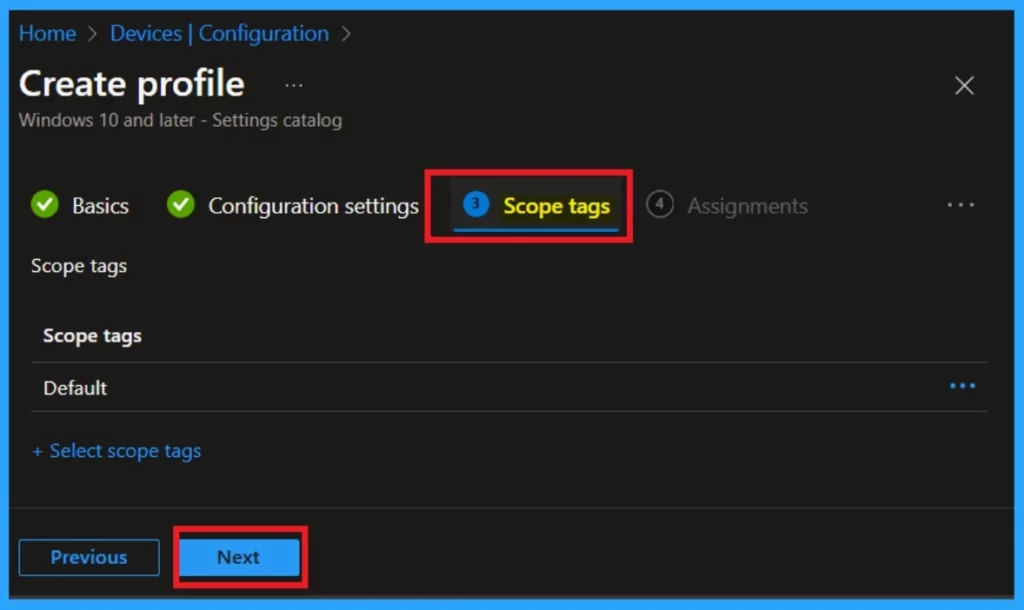
Scope Tags
The scope tag section follows the configuration settings in the policy. It is important to note that the scope tag is always mandatory at the time of policy deployment. I decided to skip this policy, which is specifically designed to add scope tags. Now that I’ve skipped it, you can proceed by clicking on the next option.
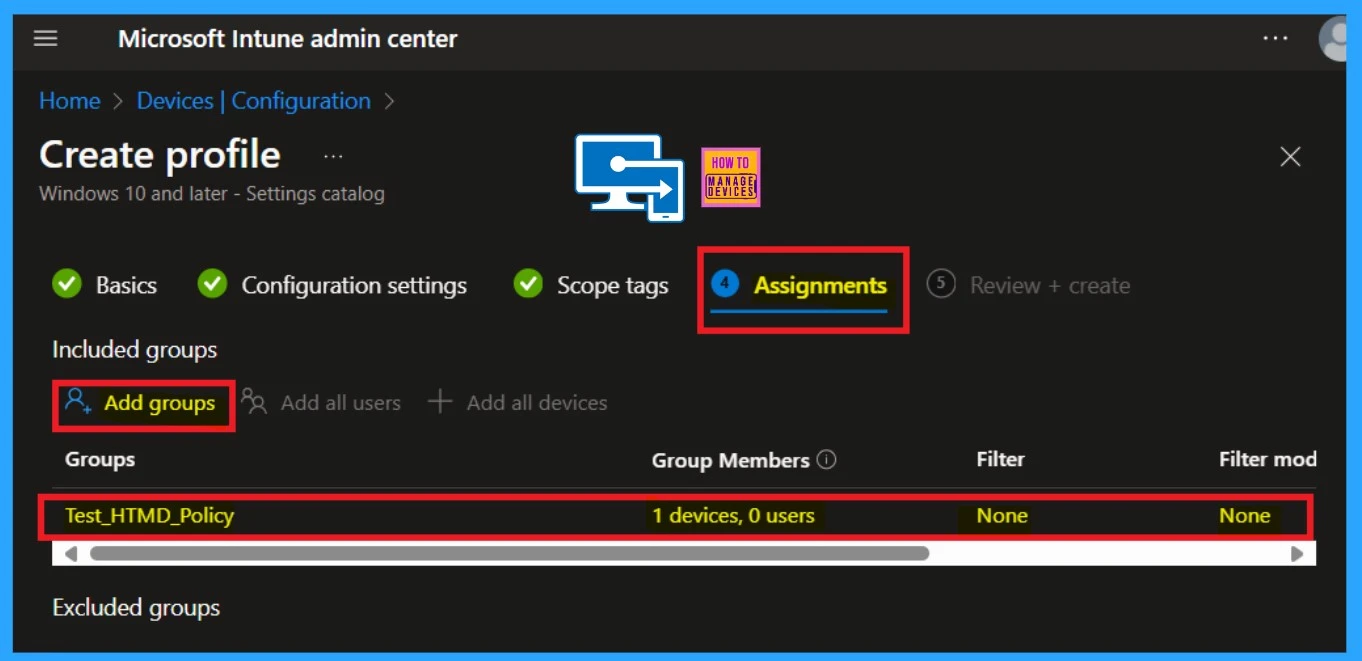
Assignments
The Assignment section is a crucial step when deploying a policy. What is our aim for a deployment? We have to deploy a policy to the specified group. In this section, assigning a policy to a specified group is possible. Here, click on Add Groups under Include Groups.
- Then select the Group that you want to assign the policy.
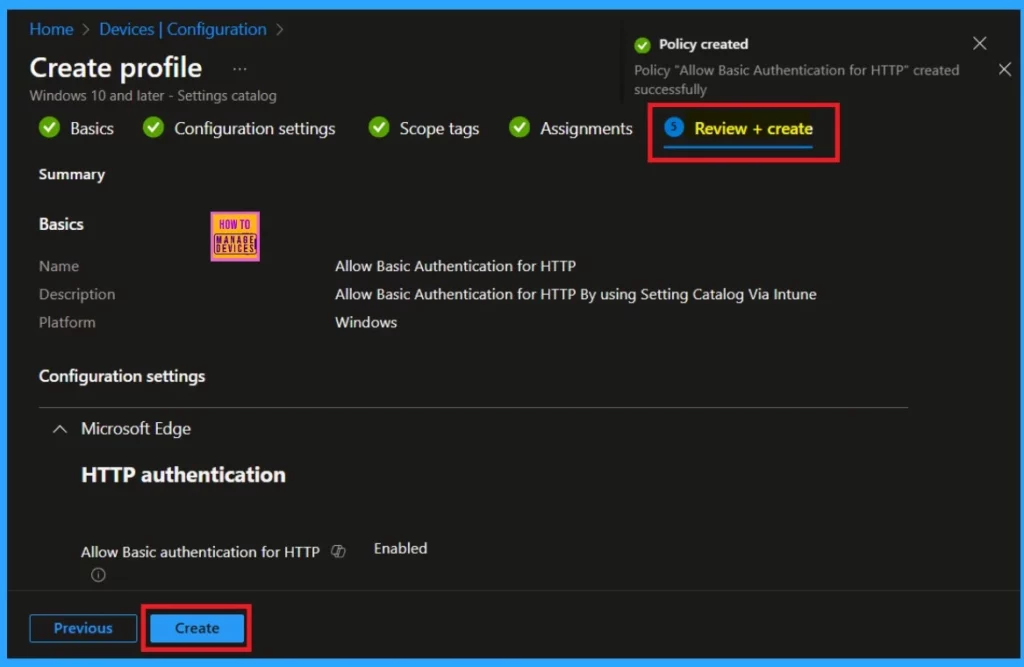
Review+Create
The Reviw+ Create option is the last stage of policy creation. You can check all the details that you are given to the policy for creating if everything is perfectly Ok, you can click on create option. Now you will get notified that the policy is created.
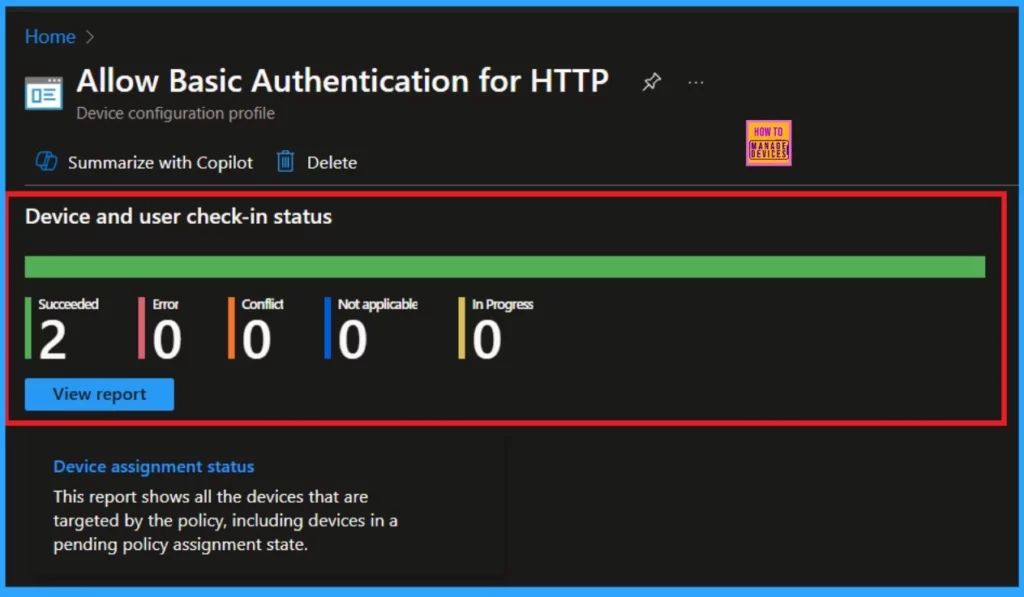
Monitoring Status
To check the monitoring status, navigate to Device > All Devices and search for the specific device you created (HTTP authentication). Typically, a policy takes about 8 hours to deploy. To expedite this process, you can sync the policy through the company portal. Once you do that, you can check the monitoring status.
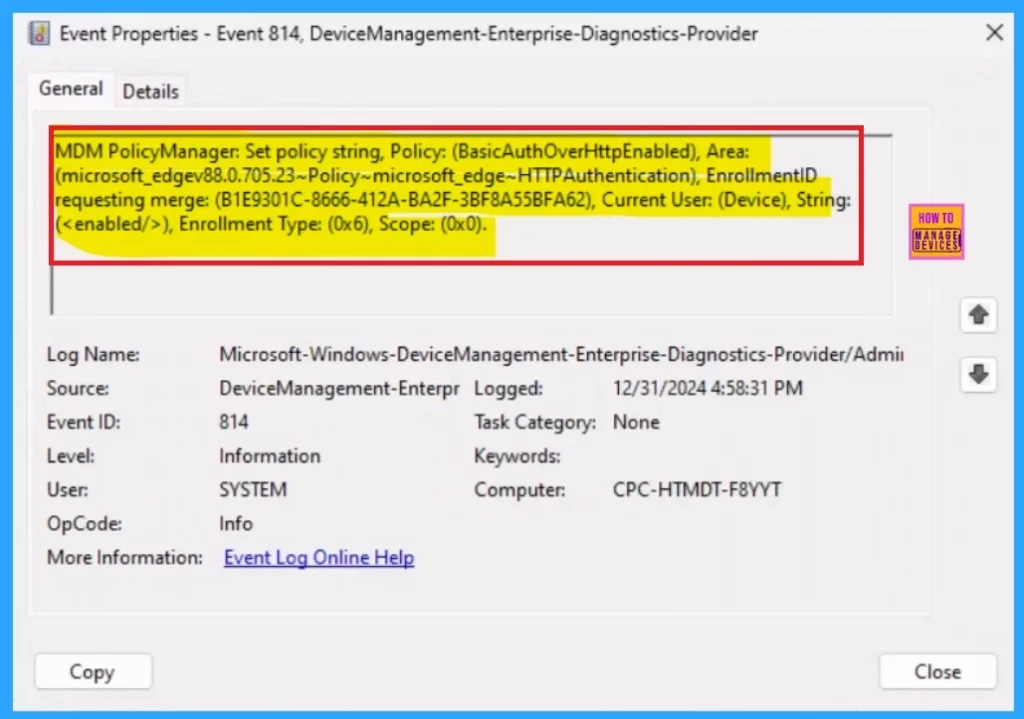
Client-Side Verification
To check the status of the Allow basic authentication for HTTP in Intune, for that open Event Viewer for that go to the Start and type “Event Viewer.” Then, navigate to Application and Services Logs > Microsoft > Windows > DeviceManagement–Enterprise–Diagnostics–Provider > Admin.
In the right pane, click Filter Current Log, enter 813 in the Event IDs field, and click OK.
This will filter logs related to the policy’s status, allowing you to quickly check its deployment and application without needing to access the Intune portal directly.
| Policy Status |
|---|
| MDM PolicyManager: Set policy string, Policy: (BasicAuthOverHttpEnabled), Area: (microsoft_edgev88.0.705.23~Policy~microsoft_edge~HTTPAuthentication), EnrollmentID requesting merge: (B1E9301C-8666-412A-BA2F-3BF8A55BFA62), Current User: (Device), String: (), Enrollment Type: (0x6), Scope: (0x0). |
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.

What’s the use case ? Enabling basic auth over http is not secure!