Another day, Another Post, this time about the Always install with elevated privileges Policy !!! Here it is next in the Configuration Profiles segment. The Always Install with elevated privileges Policy using Intune will be covered today. Here also, we will make use of Configuration Profiles from Intune.
This policy setting allows Windows Installer to use elevated permissions during program installations on the system. By enabling this setting, programs are granted extended privileges that are typically reserved for user-assigned, computer-assigned, or Add/Remove Programs-listed programs.
This policy lets users install programs that require access to restricted directories, even on highly restricted computers. However, if you disable or don’t configure this policy, the system applies the current user’s permissions for programs not distributed or offered by the system administrator.
Note that this policy appears in both the Computer Configuration and User Configuration folders and must be enabled in both to take effect. Caution should be taken since skilled users can exploit this policy’s permissions to gain permanent access to restricted files and folders. It’s important to note that the User Configuration version of this policy is not guaranteed to be secure.
In summary, the policy setting described in the original text allows Windows Installer to use elevated permissions when installing programs on the system. It can be helpful in certain situations but may also be risky and should be used with caution. It is recommended to have this disabled.
- Password Protected Screen Saver Policy using Intune
- Best Method to Prevent Users from Modifying Settings Policy Using Intune
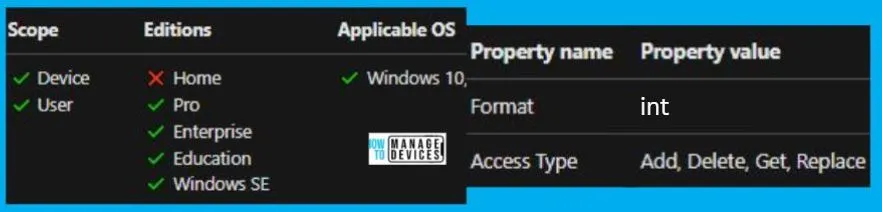
Windows CSP Details MSIAlwaysInstallWithElevatedPrivileges
Let’s go through Windows CSP Details for this Policy setting MSIAlwaysInstallWithElevatedPrivileges. The policy setting described in the original text allows Windows Installer to use elevated permissions when installing programs on the system. It can be helpful in certain situations but may also be risky and should be used with caution. Also, It’s important to note that the User Configuration version of this policy setting may not be completely secure and can also be exploited in this manner.
User-based CSP URI – ./User/Vendor/MSFT/Policy/Config/ApplicationManagement/MSIAlwaysInstallWithElevatedPrivileges
Device-based CSP URI – ./Device/Vendor/MSFT/Policy/Config/ApplicationManagement/MSIAlwaysInstallWithElevatedPrivileges
Always Install with Elevated Privileges Policy using Intune
To set the Always Install with elevated privileges Policy using Intune, follow the steps stated below:
- Sign in to the Intune Admin Center portal https://intune.microsoft.com/.
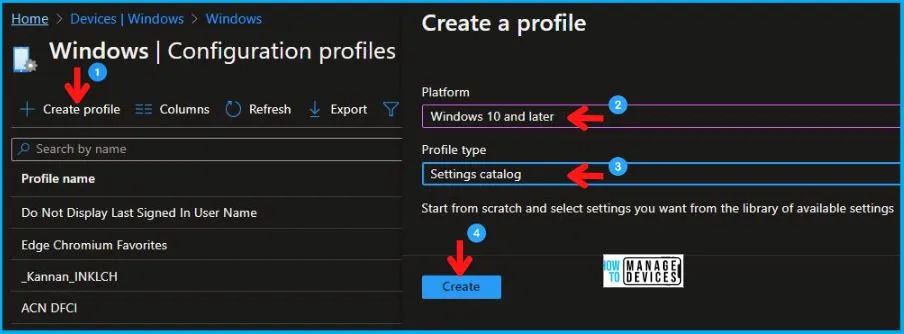
- Select Devices > Windows > Configuration profiles > Create a profile.
To create a new profile, choose “Windows 10 and later” as the platform and select “Settings Catalog” as the profile type in the Create Profile section. After making these selections, click the “Create” button to proceed.
| Platform | Profile Type |
|---|---|
| Windows 10 and later | Settings Catalog |
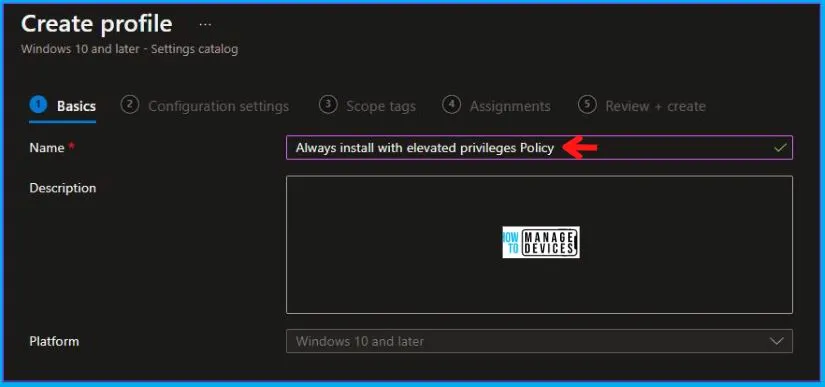
In the Basics tab pane, enter a name for the Policy as Always install with elevated privileges Policy. You can enter the Description for the Policy if you want, then select Next.
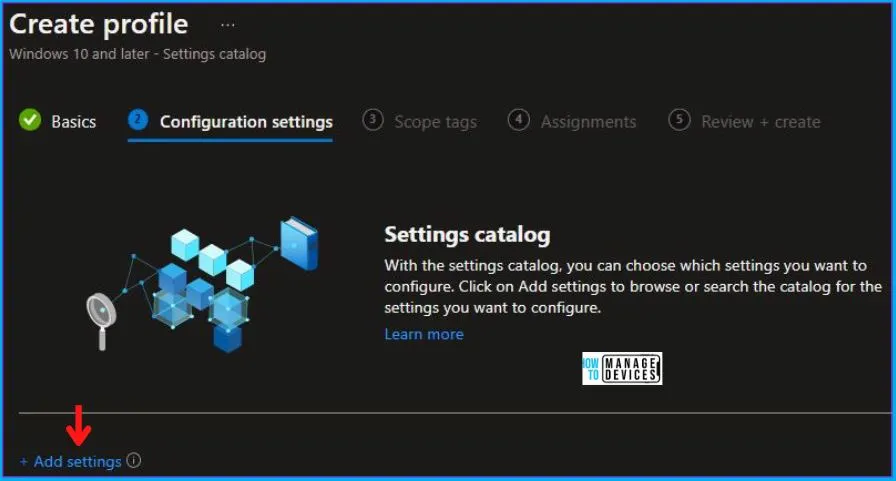
Now in Configuration settings, click Add Settings to browse or search the catalog for the settings you want to configure.
In the Settings Picker windows, search by the keyword Elevated, you will see Microsoft App Store, and select this.
When you select the option as stated above, you will see two settings: MSI Always Install With Elevated Privileges and MSI Always Install With Elevated Privileges (User). After selecting both settings, click the cross mark at the right-hand corner, as shown below.
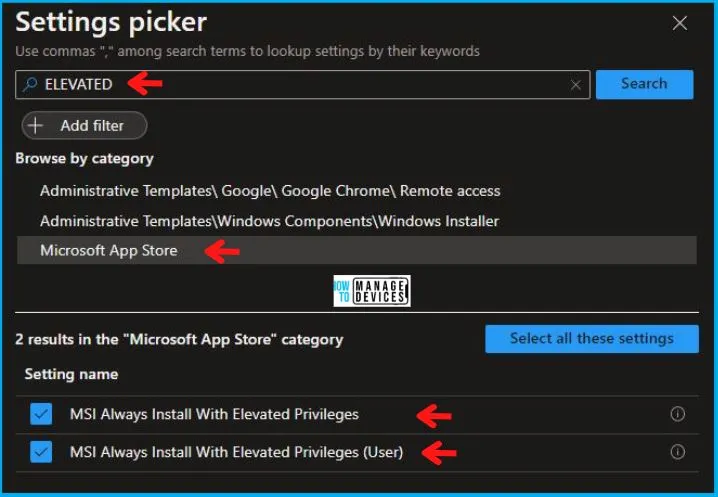
Now, in the Microsoft App Store, disabled both MSI Always Install With Elevated Privileges (User), and MSI Always Install With Elevated Privileges, as shown below in the image.
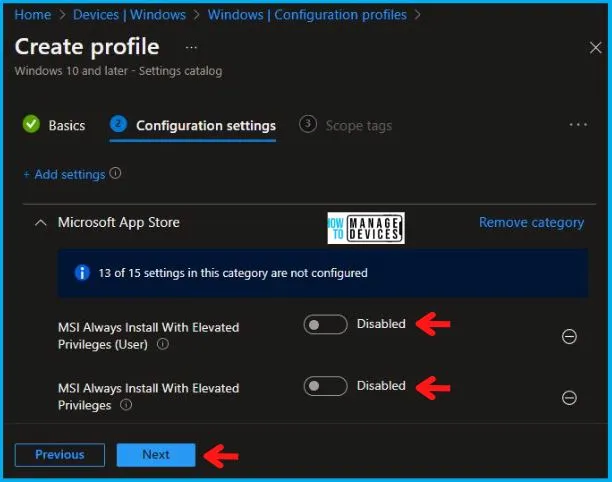
Using Scope tags, you can assign a tag to filter the profile to specific IT groups. One can add scope tags (if required) and click Next to continue. Now in Assignments, in Included Groups, you need to click on Add Groups, choose Select Groups to include one or more groups, and click Next to continue.
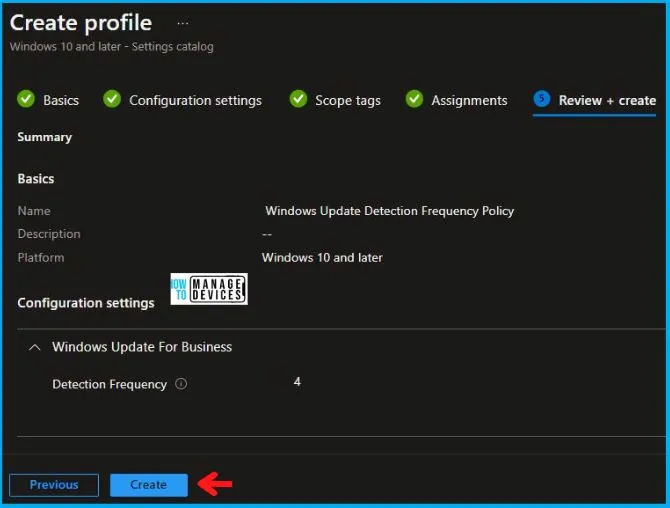
In the Review + Create tab, you need to review your settings. After clicking on Create, your changes are saved, and the profile is assigned.
A notification will appear automatically if you see it in the top right-hand corner. One can easily see that the “Always install with elevated privileges Policy” was created successfully. Also, if you check in the Configuration Profiles list, the Policy is visible there.
Your groups will receive your profile settings when the devices check in with the Intune service. The Policy applies to the device.
Intune Report for Always install with elevated privileges Policy
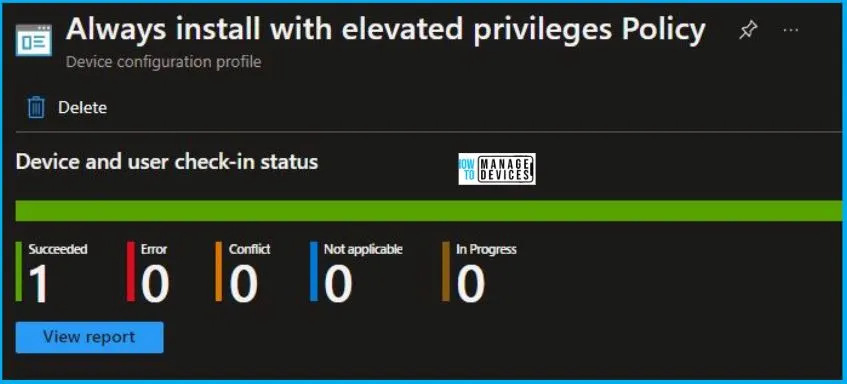
From Intune Portal, you can view the Intune settings catalog profile report, which provides an overview of device configuration policies and deployment status.
One needs to select the Policy from the list of Configuration Profiles, To monitor the policy assignment, and, here it’s been checked the device and user check-in status. If you click View Report, additional details are displayed. Let’s now check the results of the Always install with elevated privileges Policy settings.
Intune MDM Event Log
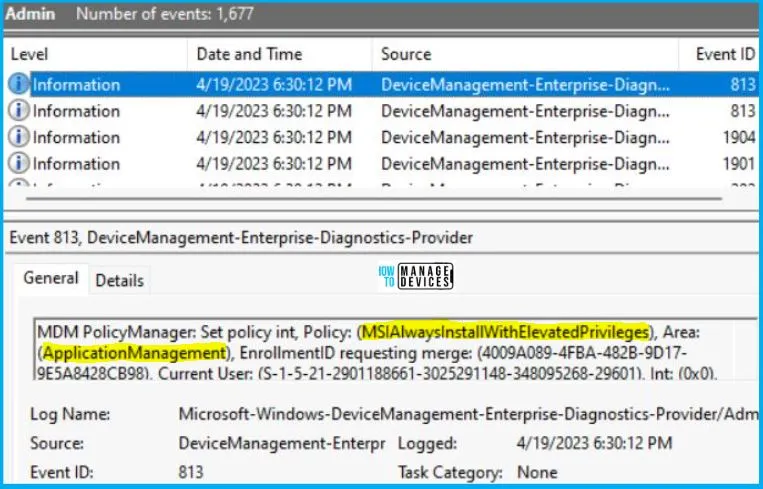
String policy has been applied to Windows 10 or 11 devices can be indicated by Intune event ID 813 or 814. In addition, you can view the exact value of the Policy that is being applied to those devices. For this policy, it’s an integer and event ID 813. But here, you will have two different logs i.e. user based and device based.
To confirm this, you can check the Event log path – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
The user-based log states the following – MDM PolicyManager: Set policy int, Policy: (MSIAlwaysInstallWithElevatedPrivileges), Area: (ApplicationManagement), EnrollmentID requesting merge: (4009A089-4FBA-482B-9D17-9E5A8428CB98), Current User: (S-1-5-21-2901188661-3025291148-348095268-29601), Int: (0x0), Enrollment Type: (0xD), Scope: (0x1).
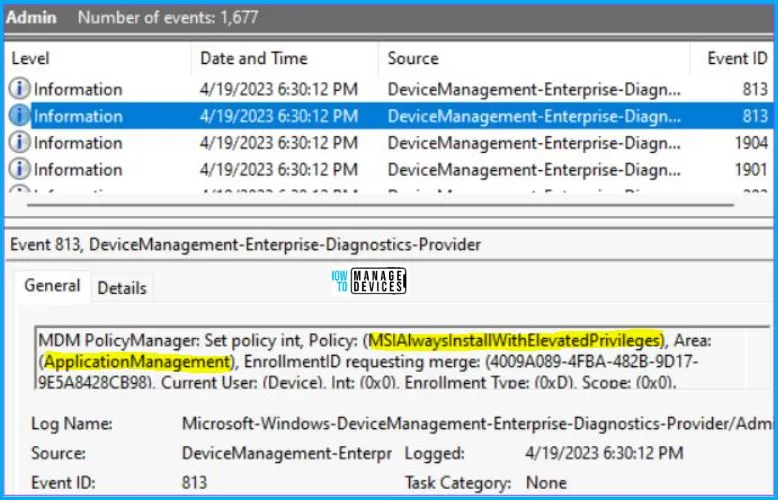
The Device-based log states that – MDM PolicyManager: Set policy int, Policy: (MSIAlwaysInstallWithElevatedPrivileges), Area: (ApplicationManagement), EnrollmentID requesting merge: (4009A089-4FBA-482B-9D17-9E5A8428CB98), Current User: (Device), Int: (0x0), Enrollment Type: (0xD), Scope: (0x0). Device
You will get some important information like Area and Enrollment ID that will help you detect the registry path after you look in the event viewer to log above. Please refer to the tables below for this information, as we have user-based and device-based profiles.
| Area | Policy | Int | Scoped | Event ID |
|---|---|---|---|---|
| ApplicationManagement | MSIAlwaysInstallWithElevatedPrivileges | 0 | User | 813 |
| Area | Policy | Int | Scoped | Event ID |
|---|---|---|---|---|
| ApplicationManagement | MSIAlwaysInstallWithElevatedPrivileges | 0 | Device | 813 |
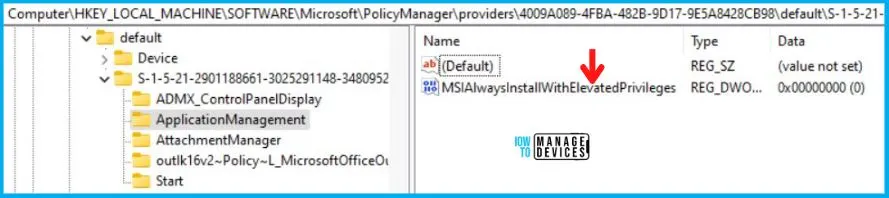
Information from the above table of Always install with elevated privileges Policy Using Intune can be used to REGEDIT.exe on a target computer to view the registry settings that store group policy settings. These settings are located in the registry path. But now, as you know, we have two profiles i.e. user-based and device-based, we also have two different registry keys for each of them.
- User-Based: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\4009A089-4FBA-482B-9D17-9E5A8428CB98\default\S-1-5-21-2901188661-3025291148-348095268-29601\ApplicationManagement
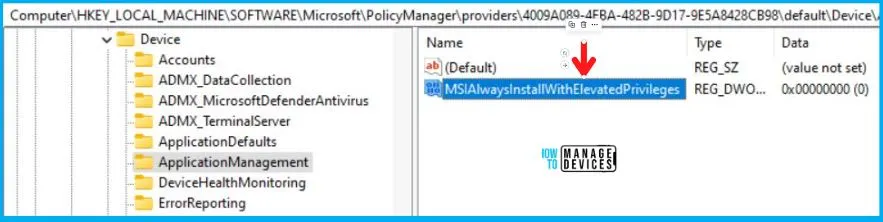
- Device-Based: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\4009A089-4FBA-482B-9D17-9E5A8428CB98\default\Device\ApplicationManagement
When you navigate the above paths in the Registry Editor, you will find the registry keys with the name MSIAlwaysInstallWithElevatedPrivileges for the user-based and device-based profiles. Refer to the table and images below.
| Registry Name | Value Data |
|---|---|
| MSIAlwaysInstallWithElevatedPrivileges | 0 |
Author
Abhinav Rana is working as an SCCM Admin. He loves to help the community by sharing his knowledge. He is a B.Tech graduate in Information Technology.
