Today, I would like to explore how to configure the Audit Policy for Registry Object Access in Windows using Intune. Utilizing Intune to audit access attempts to specific registry objects on devices can significantly improve security monitoring. Object Access auditing encompasses 14 subcategories, allowing for detailed tracking of these access attempts.
Audit Policy for Registry Object Access setting allows tracking who tries to access registry objects. An audit event is only generated when a system access control list (SACL) is defined for the object, and the requested access type (like Read, Write, or Modify) and the requesting account match the SACL’s settings.
When Audit Audit Policy for Registry Object Access policy is configured, every time an account tries to access a registry object that has a specific SACL, an audit event is created. Successful attempts are recorded as “success audits”, and failed attempts are recorded as “failure audits”.
If this policy is not configured, the user would not know when someone tries to get into specific registry settings. Audit policies significantly enhance the device’s security. By configuring these settings, can record attempts to verify account information on a domain controller or the local Security Accounts Manager (SAM).
Table of Contents
What are the Advantages of Configuring Audit Policy for Registry Object Access in Windows using Intune?
Intune’s Object Access Audit Registry policy boosts security by tracking who accesses your system’s registry. This helps to spot unauthorized changes, catch insider threats, and ensure your system stays healthy.
It also helps meet compliance rules by creating a detailed log of registry activity, and the audit data is useful for investigating any security incidents.
Audit Policy for Registry Object Access in Windows using Intune
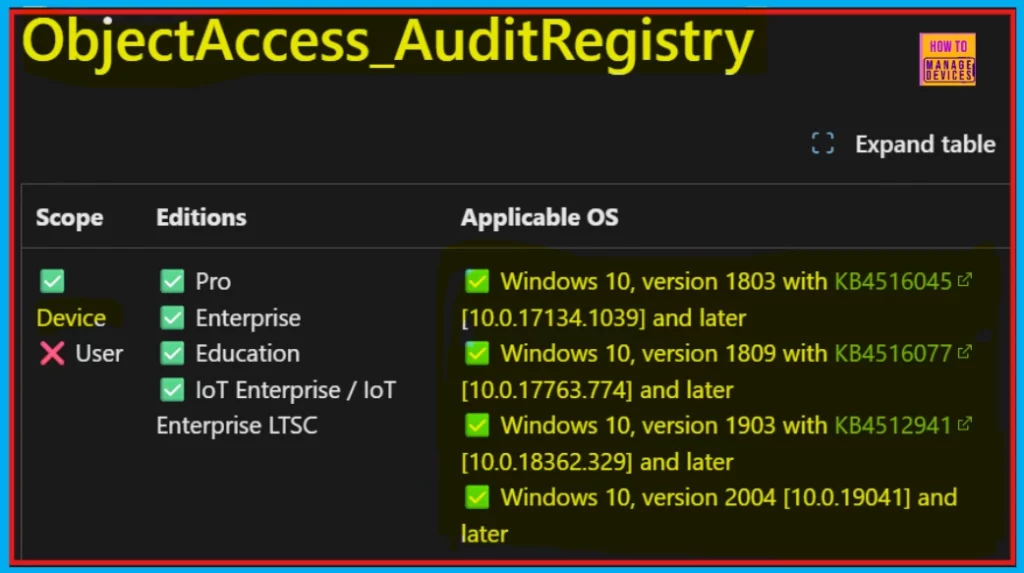
We can find the Audit Policy for Registry Object Access in the Auditing section of the Windows Configuration Service Provider (CSP), under the Object Access subcategories. The details of the Object Access_Audit Registry Policy within the Windows CSP will be shown next.
Description framework properties
| Property Name | Property Value |
|---|---|
| Format | int |
| Access Type | Add, Delete, Get, Replace |
| Default Value | 0 |
Allowed Values
In Intune’s Settings Catalog, the Allowed Values are the choices available for a particular setting. These selections directly dictate how that setting will behave on a device. The following table showcases the Allowed Values of the Object Access_Audit Registry policy.
| Value | Description | Features |
|---|---|---|
| 0 (Default) | Off/None. | No audit events are generated. |
| 1 | Success | Attempts that worked. |
| 2 | Failure | Attempts that didn’t work. |
| 3 | Success + Failure | Both successful and failed attempts are recorded. |
Group Policy Mapping
Group Policy Mapping or Group Policy Analytics in Microsoft Intune is a tool that helps to move the current Group Policy Objects (GPOs) to the cloud. The table below shows how the Audit Policy for Registry Object Access in Windows using Intune
| Name | Value |
|---|---|
| Name | Audit Registry |
| Path | Windows Settings > Security Settings > Advanced Audit Policy Configuration > System Audit Policies > Object Access |
./Device/Vendor/MSFT/Policy/Config/Audit/ObjectAccess_AuditRegistry
- How To Configure Files, Folders And Registry Keys Access Auditing Application Policy In Intune
- How To Allow Direct Memory Access For Data Protection Through Intune Settings Catalog
- Free Intune Training 2024 For Device Management Admins
OMA-URI Setting of Audit Policy for Registry Object Access in Windows
We can easily configure or not configure the Audit Policy for Registry Object Access using Intune on Windows devices using Microsoft Intune or configure a custom OMA-URI setting. Below is a step-by-step guide to help to set this up.
- Sign in to Microsoft Intune
- Go to Devices > Configuration
- Click Create and then New policy
- Choose the platform as Windows 10 and later
- For Profile type, select Templates and then choose Custom
- Provide a Name – e.g. Audit Registry Object Access Policy.
- Add a Description if needed
- Click on + Add under OMA-URI Settings to configure the specific setting.
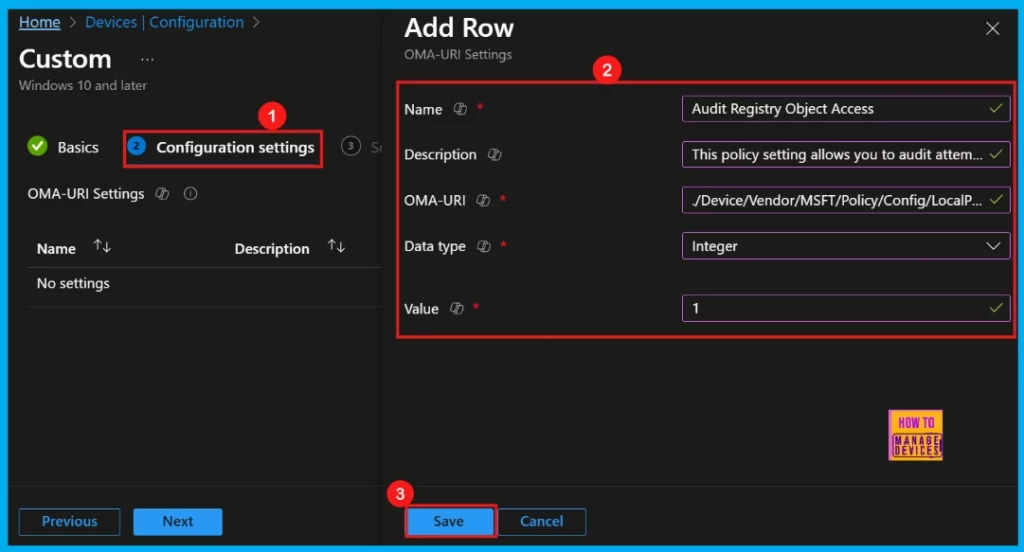
- To Configure the OMA-URI Setting, do the following
- Enter a name for this setting, such as Audit Registry Object Access Policy.
- Briefly describe the setting, e.g., “This policy setting allows you to audit attempts to access registry objects”.
- Enter the following OMA-URI path
- ./Device/Vendor/MSFT/Policy/Config/Audit/ObjectAccess_AuditRegistry
- Set the Data type to Integer.
- Enter the value
- 1 to Success the Audit Registry for Object Access Policy.
- 0 to Off/None in the Audit Registry for Object Access Policy.
- After entering the above details, click Save.
How to Configure Audit Policy for Registry Object Access in Windows using Intune
To start deploying a policy in Intune, simply sign in to the Microsoft Intune admin center. Once there, navigate to Devices > Configuration profiles, then click Create profile.
- In the Create a Profile window, set the Platform to Windows 10 and later
- Choose Settings catalog as the Profile type.
- Finish up by clicking Create.

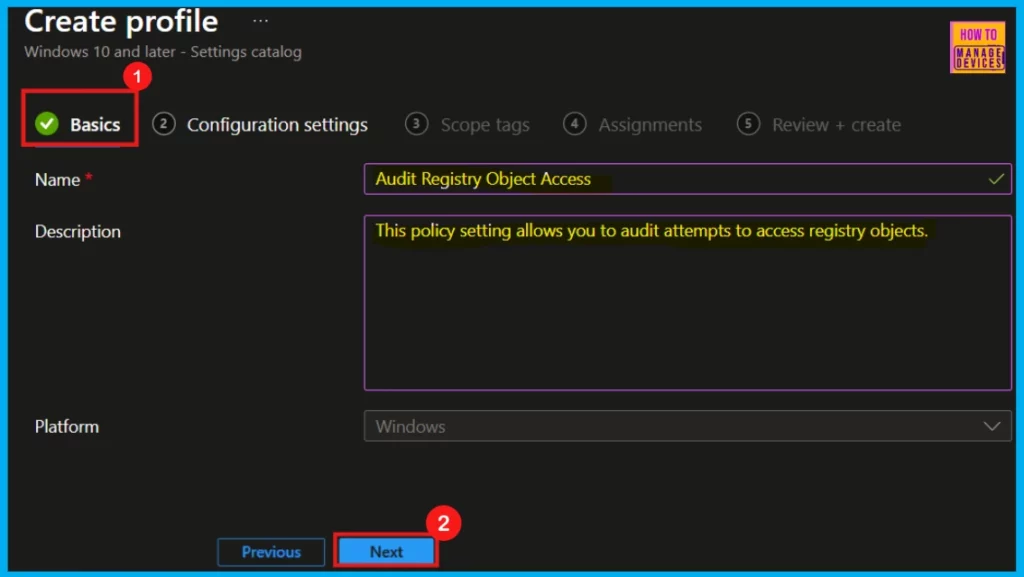
The Basics step is where we can give our policy its essential details. Start by providing a clear Name so we can easily identify it later. Then add a short Description explaining its purpose. The Platform is already configured, so no action is needed there.
- Click Next to proceed.
Configuration Settings
Now, let’s move to Configuration Settings. This is where we will define what this policy actually does. Click Add Settings to open the Settings Picker. In the search bar, type Auditing, and then select Object_Access Audit Registry from the results.
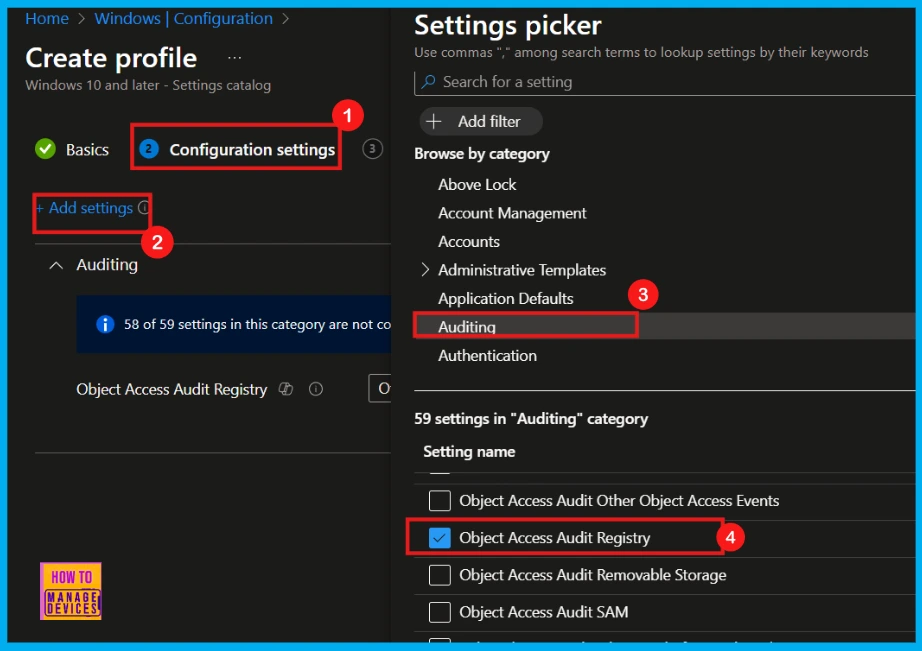
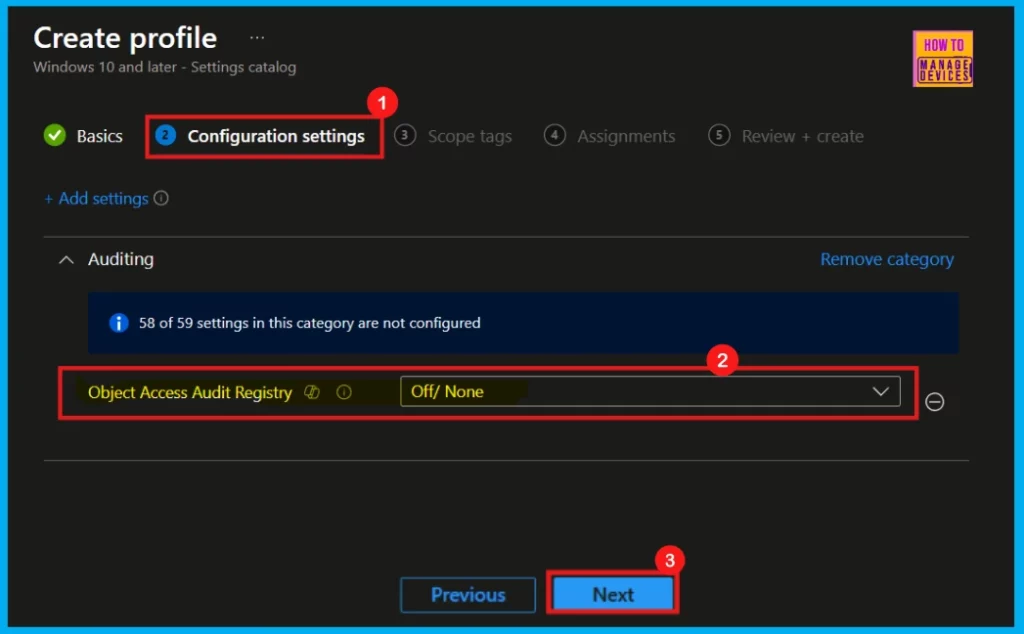
Once we have selected Object_Access Audit Registry and closed the Settings Picker, we will find it listed on the Configuration Settings page. By default, its status is showing as Off/None (Not configured).
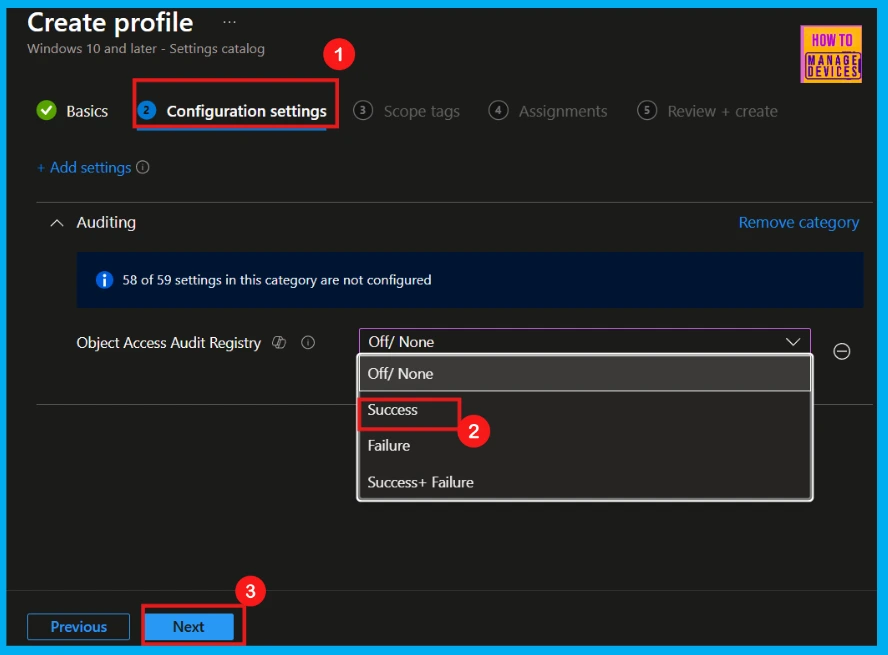
We can see that the Object_Access Audit Registry policy has three configurable options (more details are in Table 2). For this setting, I will choose Success (Value1), which means records successful attempts to access an object with an SACL.
Scope Tags
In Intune, Scope Tags help you control who can see and modify this policy, keeping things organized and managing access. They’re optional, so you can just click Next if you don’t need to assign them.
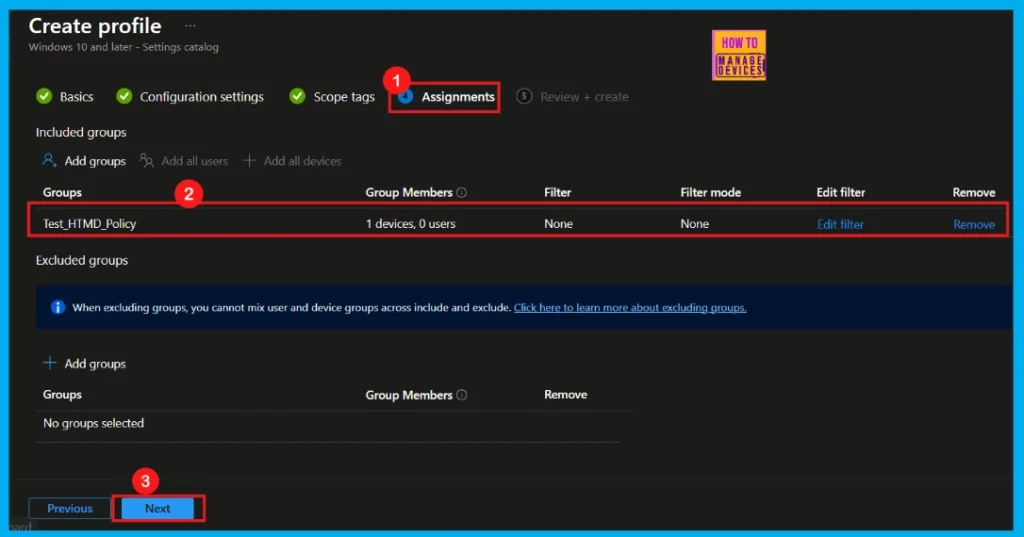
Assignments
The Assignments tab is where you decide which users or devices receive this policy. Under Include Groups, click Add Groups and choose the desired group from the list. The selected group will then appear in your assignments.
- For example, I have chosen Test_HTMD_Policy for this policy.
- After making the selection, click Next to continue.
Review + Create
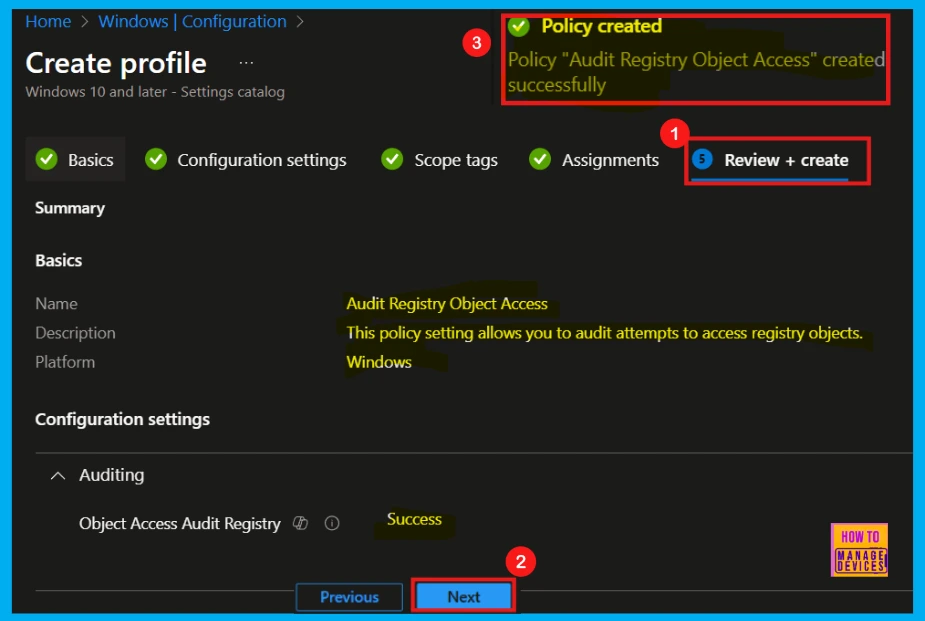
In the Review + Create we will see a full summary of the new policy. Check everything over, and if needed to change anything, hit Previous.
- When all are ready, click Create to finish.
- We will now get a notification confirming the policy, Audit Registry Object Access was created successfully.
Device and User Check-in Status
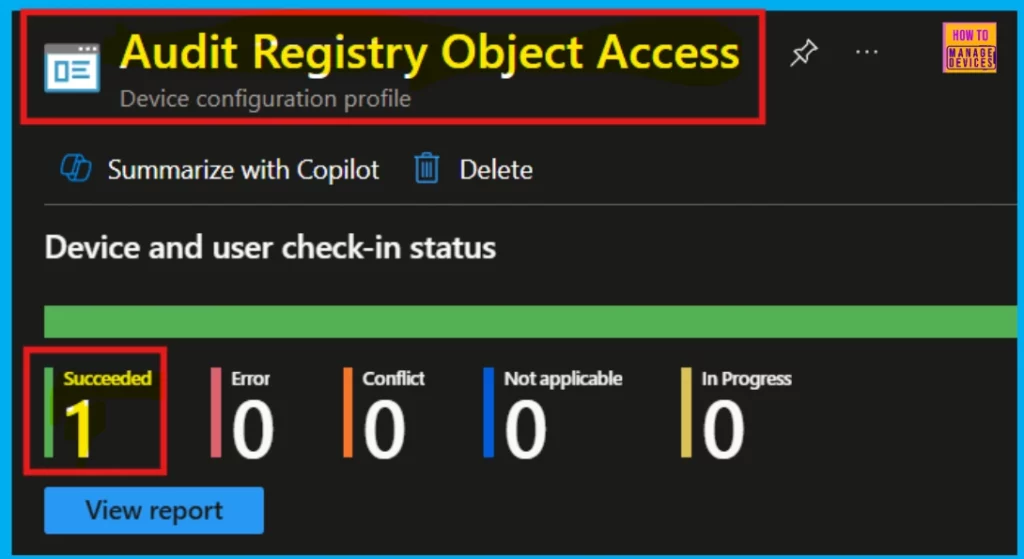
We can verify the policy in the Intune Portal. Policy creation typically takes around 8 hours. If it’s taking longer, use the manual sync option in the Company Portal app on the device, then check the status again.
- Go to Devices, then Configuration.
- Click on the policy Audit Registry Object Access.
- The Audit Registry Object Access policy status is succeeded (1).
Client Side Verification
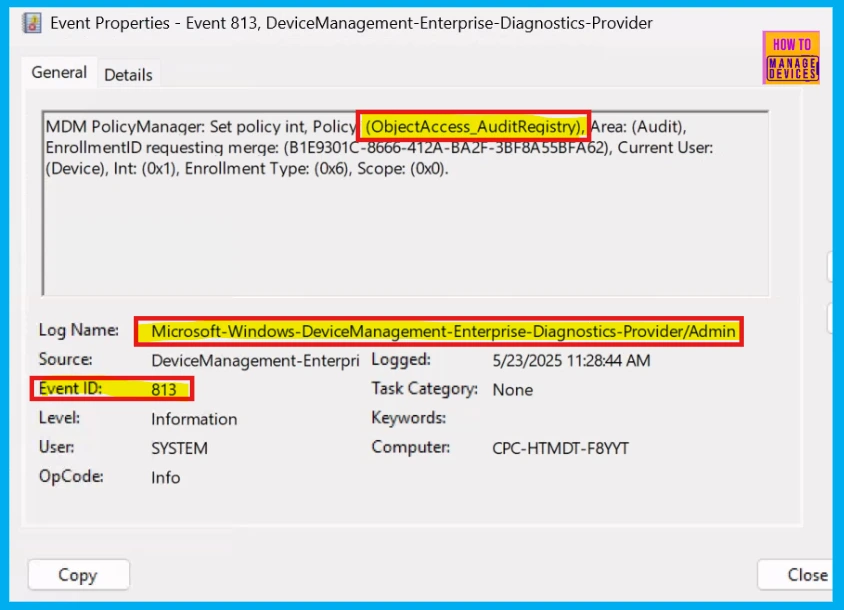
To check if the policy applied, use the Event Viewer on the client device. Navigate to Applications and Services Logs > Microsoft > Windows > Device Management > Enterprise Diagnostic Provider > Admin.
We can see a list of policies there. Use the Filter Current Log option on the right and search for Intune event 813. This event confirms that a text setting has been applied to a Windows 10 or 11 device and will display the specific setting.
MDM PolicyManager: Set policy int, Policy: (Object Access_Audit Registry), Area: (Audit), EnrollmentID requesting merge: (B1E9301C-8666-412A-BA2F-3BF8A55BFA62), Current User: (Device), Int: (0x1), Enrollment Type: (0x6), Scope: (0x0).
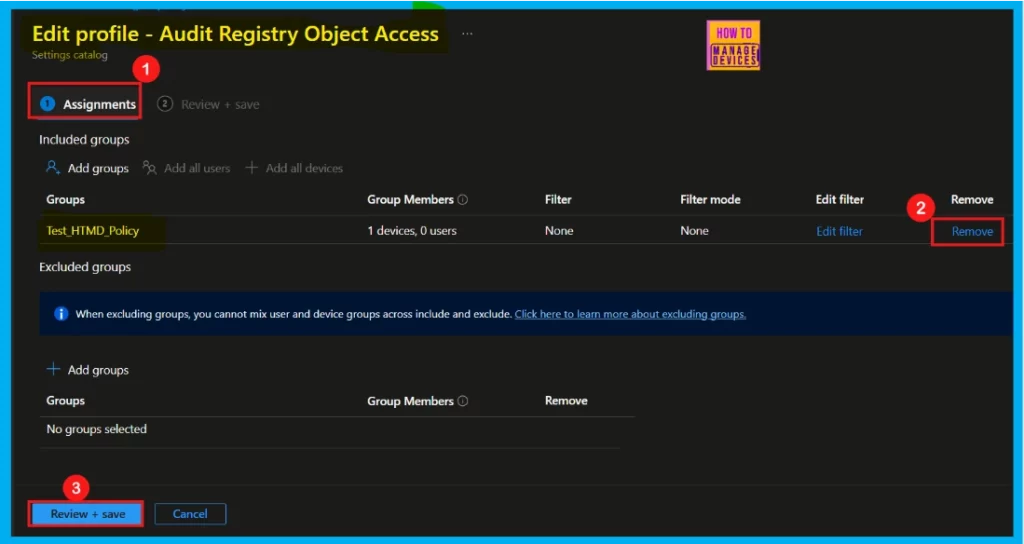
How to Remove Assigned Group from Audit Registry Object Access Policy
We might need to remove a group from a policy assignment for security updates or to improve workflow. The image shows how to unassign a group from a policy. After removing it, remember to click Review + Save.
For detailed information, you can refer to our previous post – Learn How to Delete or Remove App Assignment from Intune using by Step-by-Step Guide.
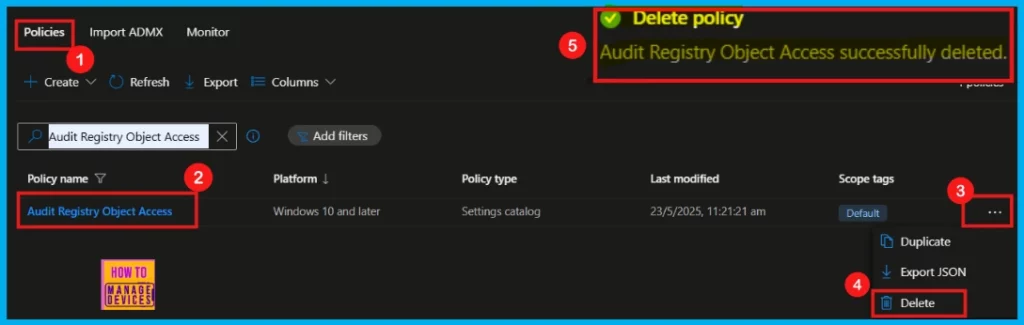
How to Deleting Audit Registry Object Access Policy from Intune
If we want to delete an Intune policy for security or operational reasons, here’s how to remove Audit Registry Object Access policy.
- Navigate to Devices > Configurations.
- Find the Audit Registry Object Access policy in the list.
- Click the three dots (…) next to it.
- Select Delete from the menu.
For detailed information, you can refer to our previous post – How to Delete Allow Clipboard History Policy in Intune Step by Step Guide.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


