Hello everyone, this week, let’s learn something new about how to “Block access to M365 Apps Outside Android Work Profile using Intune”. In our previous blogs, we explained and discussed how to set up and enable settings for your organization, but this week, we will discuss how to meet a specific requirement of your organization.
Recently, one of my friends asked how we can block Office app access outside the Work profile on Android devices. Then I realized many admins might be looking for this, so this article will discuss various ways to block Microsoft 365 Apps outside the Work profile.
We will use conditional access policies, which are the best way to block Access. Conditional access policies can be defined as if-then statements. Users must complete a specific action if they want to access a resource. These policies are powerful tools for helping organizations set up rules to manage data and application access.
By using conditional access policies, you can allow or block access to resources based on certain conditions, such as device compliance, location, or user identity. This is a simple and effective way to ensure that your organization’s data is secure and that only authorized users can access it.
- Prepare Android Virtual Device for Intune Deployment Testing
- Enforce Users to Enroll Devices with Intune Conditional Access Policies
Create Enrolment Restrictions
To block access to Microsoft 365 apps on personal profiles, we need to restrict users from enrolling their devices in the Android Device Admin. Moreover, Google is deprecating Android device admin as it limits the MDM capability APIs. Let’s see how we can restrict it in the steps below.
- Login to Microsoft Intune Admin Center
- Click on Devices > Device Enrolment
- Click on Enrollment device platform restrictions
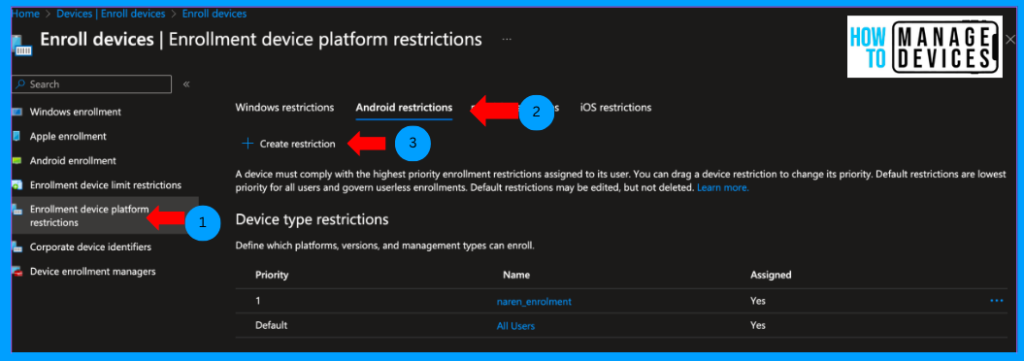
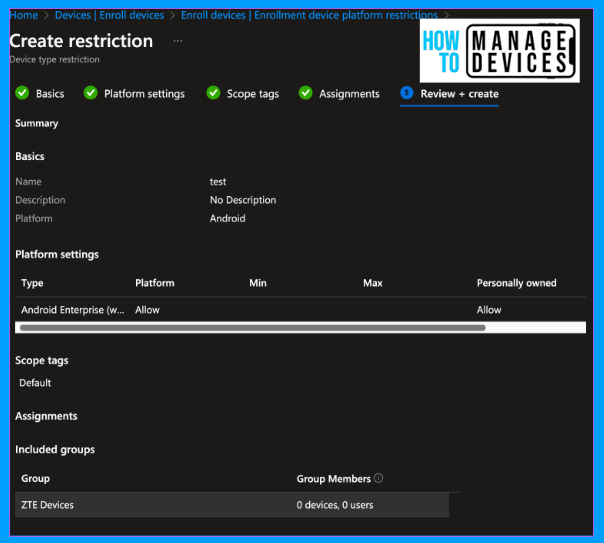
Now click on the Android tab and click on Create New Restriction. On the basics page, provide the Name and Description for restrictions and click Next.
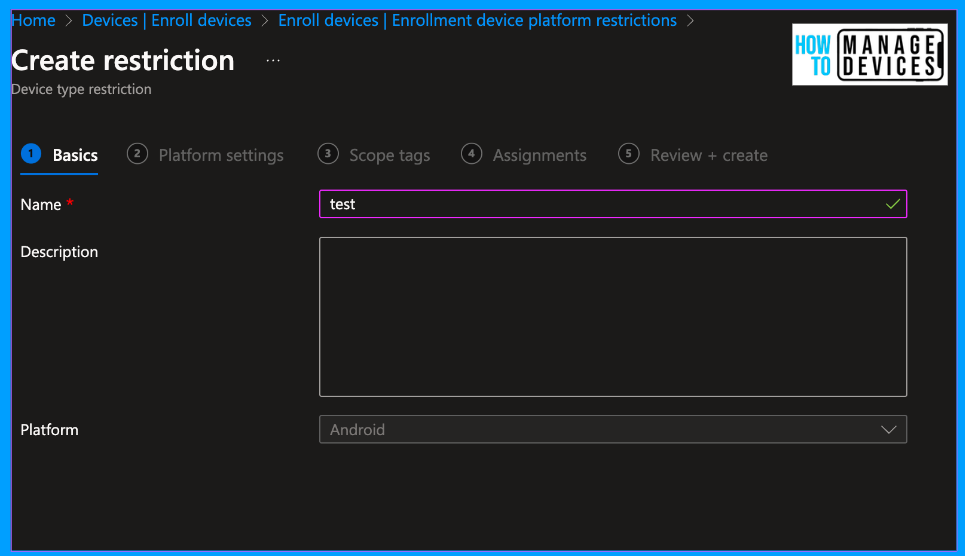
On the platform settings page, we see two options, Android Enterprise (work profile) and Android device administrator. Click on Block next to Android Device Administrator. We can define the minimum and maximum OS version required to enrol the devices in Intune. For now, I left it blank.
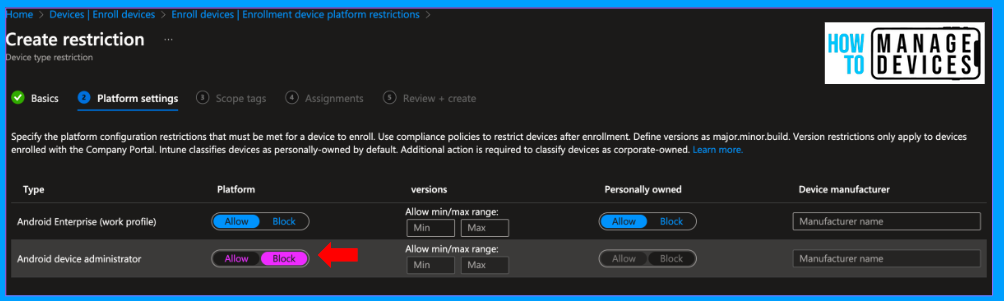
Click Next to Scope tags, add scope tags if you have any, and click Next to the Assignment page. Here, add the groups to which the policy should be assigned.
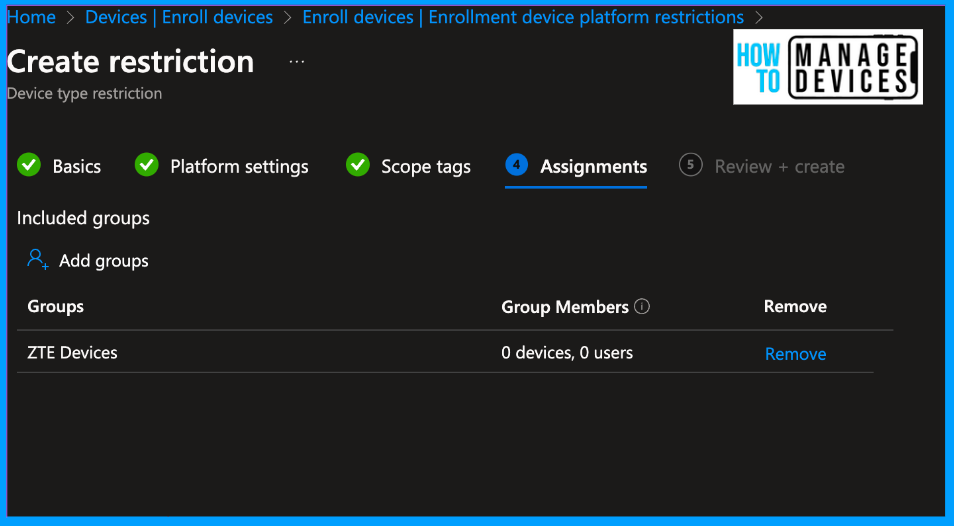
Click Next, review the restriction on the Review and Create page, and click Create. This will create a restriction, and users in the group will be forced to enrol their devices in Android for Work.
NOTE: If you want to allow only a few sets of users to enrol their devices to Intune, click on Default enrolment restriction > Properties > Edit block on all kinds of enrolments before creating the new enrolment restriction. If we keep it as is, users not part of the new enrollment restriction will get the default enrollment restriction and can enrol their devices to the Android device administrator.
Create a Conditional Access Policy to Block Access to Microsoft 365 Apps
As mentioned above, we can block Access to company resources or apps using device compliance, and we will use the same here to block Access. To create a Conditional access policy, you must have any one of the below Access
- Security Administrator
- Conditional Access Administrator
- Global Administrator
If you have the required Access, follow the steps below to create a conditional access policy.
- Login to Microsoft Entra Admin Center
- Click on Protection on the right side menu, and Click on Conditional Access.
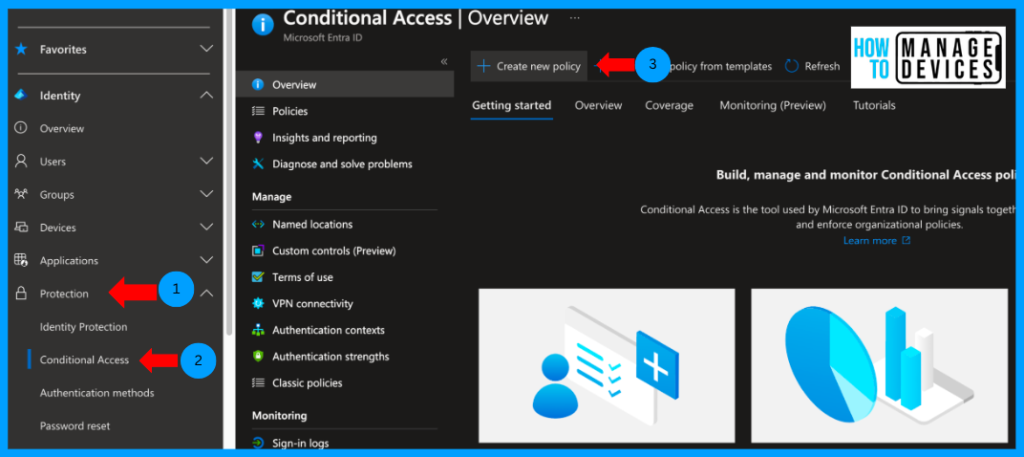
On the Overview page, click Create New Policy. Provide a name for the conditional access policy and click on the users and groups to which it should be assigned. We can assign the policy to all users or specific users and groups.
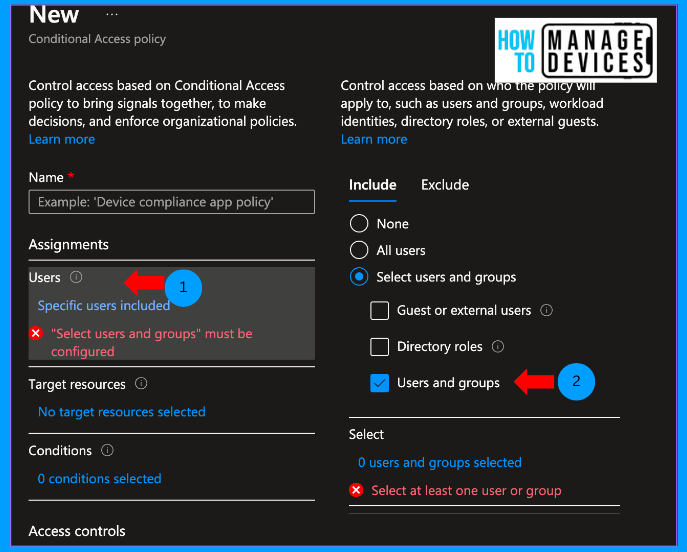
Now click on Target resources. This is where we define the corporate resources to which we need to configure the condition for access or limit access. We can select Cloud apps (those registered in Entra under Enterprise apps), user access, global secure access, or authentication access. I have chosen Cloud apps as we need to restrict access to Microsoft 365 apps.
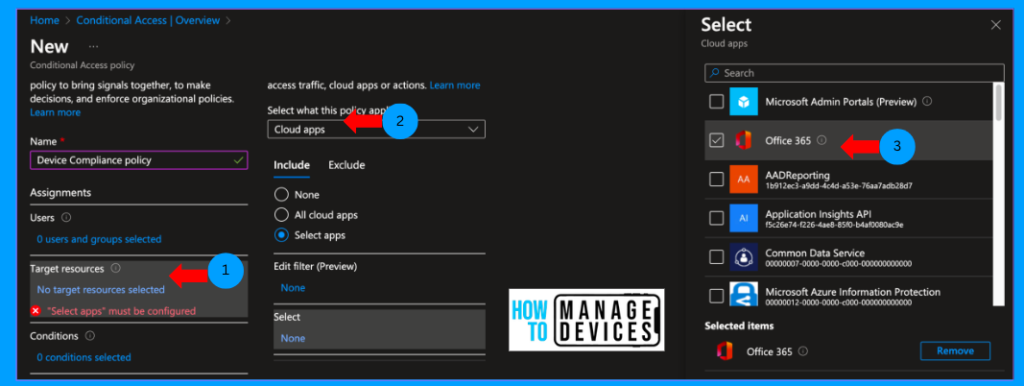
Click on Conditions. We need to decide the conditions, including Device Platform, sign-in risks, User risk, Location, etc. As we want to restrict access only to Android devices, select Device Platform, choose Android and click ok.
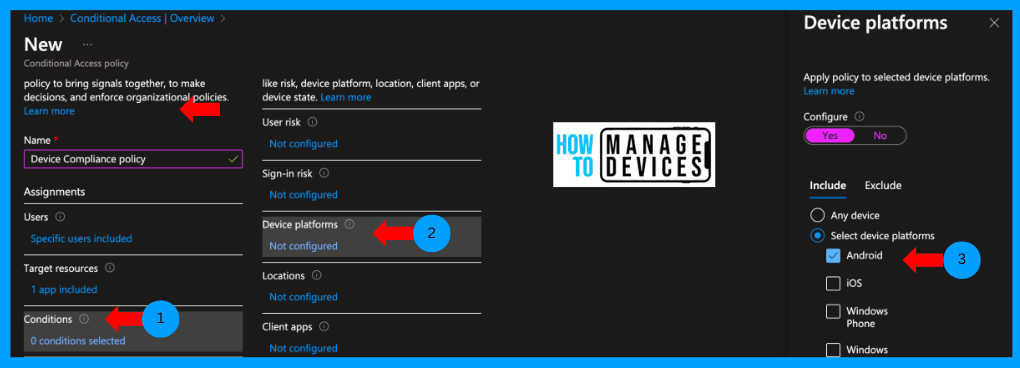
Now, let’s configure the grant control for the apps. We must decide whether to grant or block app access if the conditions are satisfied. Click on Grant, select Grant Access, and choose “Require device to be marked as compliant,” as we want to allow Access only to compliant devices.

Under Enable Policy, the policy will be selected as Report-only, change that to ON to deploy and block the users if the conditions are unmet. Click on Save to create and apply the Conditional access policy to the targeted users and application.
User Experience
Let’s see how it behaves when a user tries to access Microsoft 365 apps outside the work profile. For our discussion, we will download the Outlook app. Open the app and sign in with a user account. The user will be prompted with the message below.
So, the device will be marked as compliant if it is enrolled and satisfies the compliance settings we configured in Intune. We will not be able to access emails outside of the work profile. Let’s see how we can confirm this using sign-in logs.
- Login to Microsoft Entra Admin Center
- Click on Users > All users.
- Search for the user, Click on user.
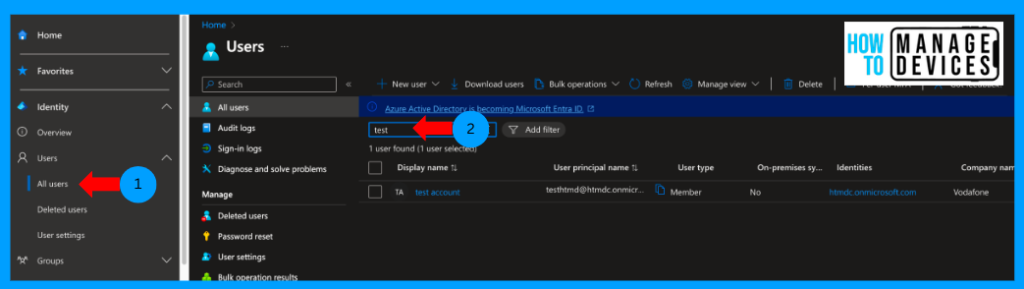
To get more insights, click on signing logs and then on the Conditional Access policy tab. Here, we can view the CA policies applied to the user, whether a failure or success.
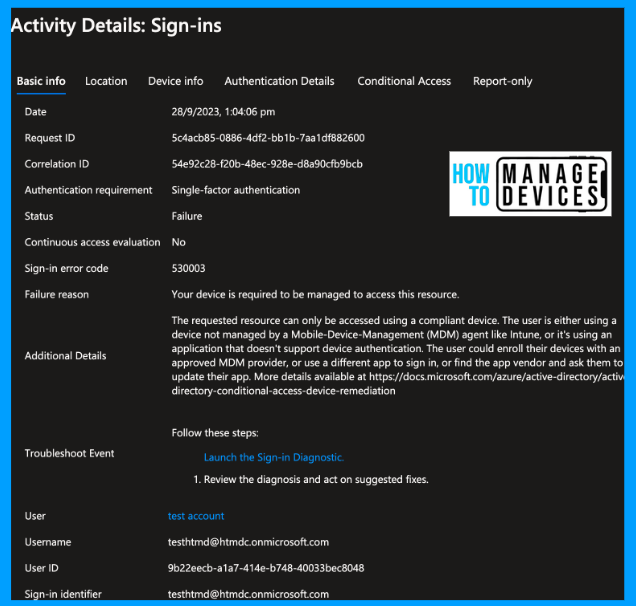
The sign-in error code is 530003, and the failure reason is that “your device is required to be managed to access this resource”. Users can enrol on the device and get Access to M365 applications. This configuration works great if you block the Android Device Administrator in enrollment restrictions.
What if your organization is required to enrol devices in Android device administrator to access emails on personal profiles? How can we achieve this? Think and let me know in the comments before reading the article.
Create Conditional Access with Filters
So, why do we need to create another CA policy with Filters, even though the CA policy with Compliance check will achieve your requirement? There will be many reasons like you not having device admin enrolment restrictions or your compliance policy not immediately marking the user’s device as non-compliant. This will allow users to access apps till the grace period.
So, let’s create another conditional access policy allowing Access only to Android Enterprise devices. This can be achieved with OS filters. Follow the below steps to create
- Login to Microsoft Entra Admin Center
- Click on Protection on the right side menu
- Click on Conditional Access.

Add Target resource as Office 365 and users to specific users and groups and assign it to a group similarly as above. Under Conditions, select the Device platform as Android, the same as the above policy. Click on Filter for devices, click Yes to configure the policy, select Exclude filtered devices from the policy, and configure the query below.
“device.operatingSystem -eq “AndroidForWork” -or device.operatingSystem -eq “AndroidEnterprise”
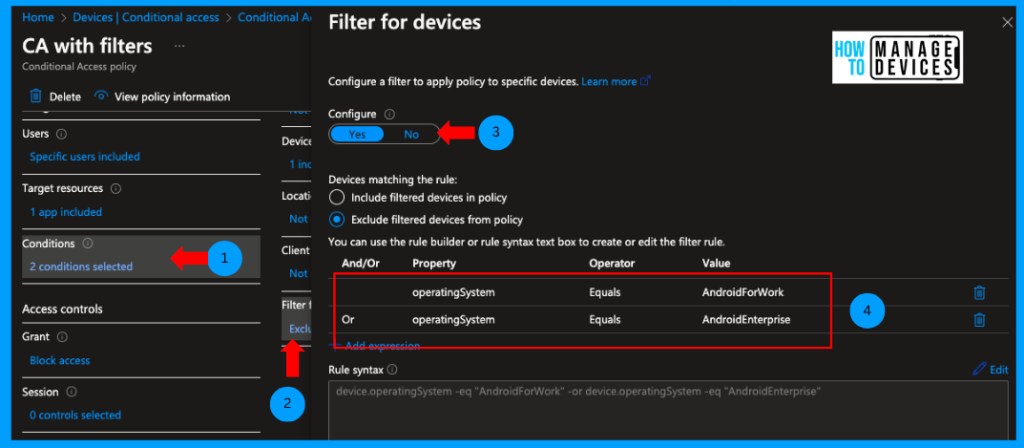
Now click OK, select Grant Access, select Block Access, and click Yes to Enable this policy and create the policy. Confused what we have done here? Let me explain: with this policy, we block Access to Microsoft 365 apps on all Android devices except for those whose operating system is equal to Android for Work and Android Enterprise.
User Experience
Let’s download any Microsoft 365 apps. This time, I have downloaded the OneDrive app. Please open it and sign it with your credentials in my personal space. You can see similar behaviour as we have seen. In the case of Outlook, I was forced to enrol in the device.
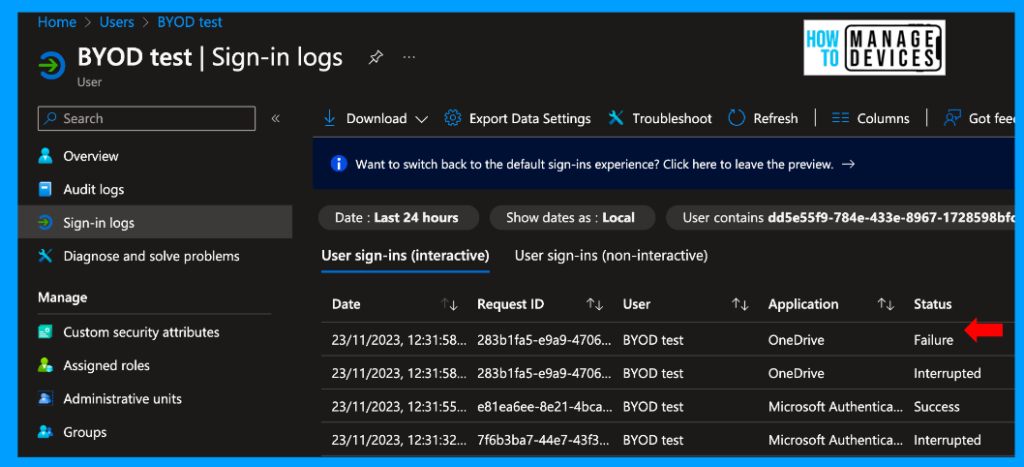
Let’s see the user sign-in logs. Login to AZURE ENTRA, search for the user and select the user. Now click on Sign-in logs to see a reason for Failure.
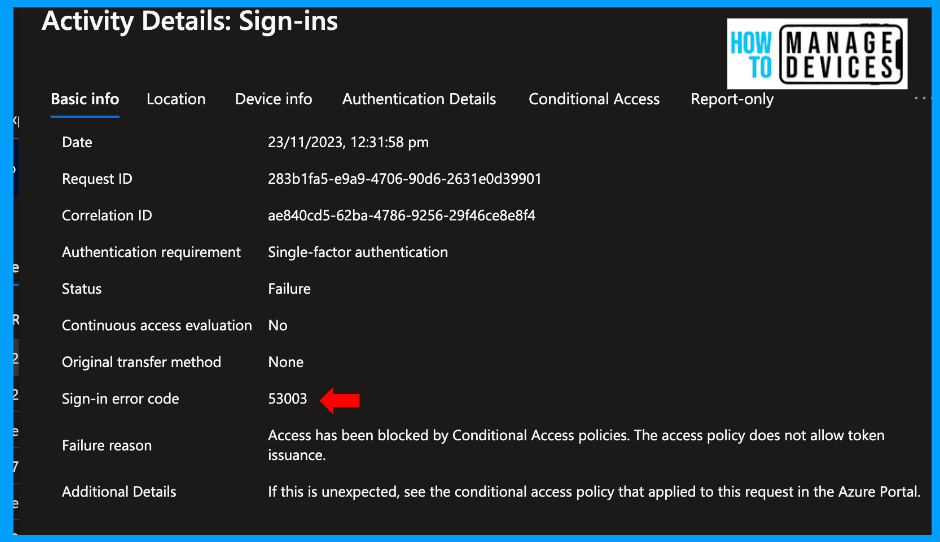
Click on the log to view a detailed view of the log. We can see the sign-in error code as 53003 and the failure reason as “Access has been blocked by Conditional Access policies. The access policy does not allow token issuance.” This reason is different from what we have seen earlier.
Click on the Conditional Access tab to see all the Conditional Access applied to the user and policies that are not assigned to the user.
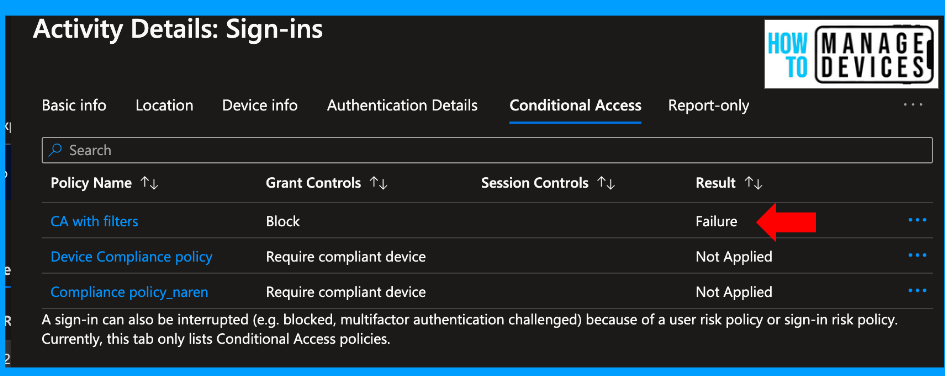
Click on the Conditional Access policy, which has Failure. In our case, we select CA with Filters. Scroll down to Devices, which says Not Matched the filters.
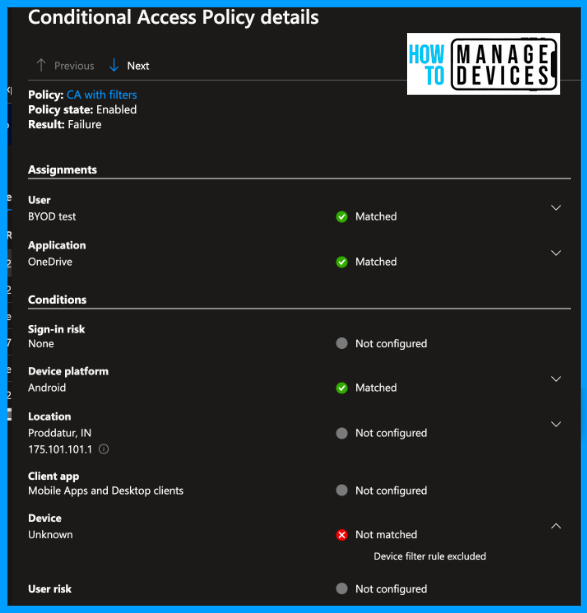
So, suppose we try to access Android for Work or Android Enterprise devices (enrolled as corporate devices). In that case, we can access the Microsoft 365 apps without issues. You can also view the sign-in logs for another user who has the corporate-owned fully managed device.
Under the Conditional Access tab, you can check that conditional access is not applied to the user, as shown in the screenshot below, and the user can access the Microsoft 365 apps.
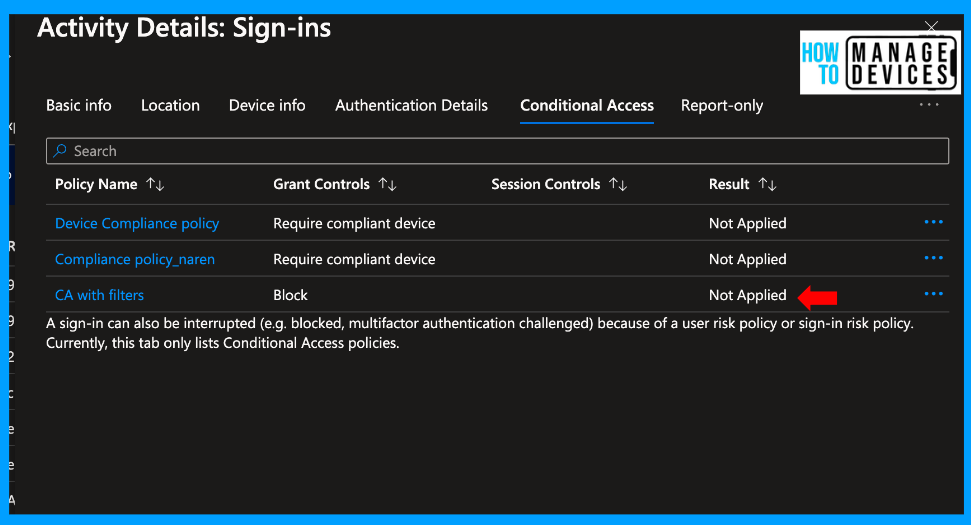
Therefore, we can use conditional access policies to restrict access to Microsoft 365 apps on personal profiles and allow access to the Work Profile.
Conclusion
So, we have discussed two ways to block access to Microsoft 365 apps outside the Android work profile. You can choose the best way that suits your organization’s requirements. Let me know if you like the article and need more like it. I will meet you guys on another exciting topic. Happy learning!
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here – HTMD WhatsApp.
Author
About Author – Narendra Kumar Malepati (Naren) has 11+ years of experience in IT, working on different MDM tools. Over the last seven years, Naren has been working on various features of Intune, including migration from different MDMs to Intune. Naren mainly focuses on Android, iOS, and MacOS.

Thanks for your testing and sharing. this is an very good option for BYOD scenario.
With the device restrictions you’ve set… the user won’t be able to use the Office applications on his personal device, nor install the Company Portal to access the data? Is that what I need to understand?
If I want users to be able to access data via the Enterprise Portal, I simply have to avoid the first step of enrolment restrictions? is that correct?
Thank you for all these useful documentations.
Thank you
Can we make an exception via a browser?