In this article, I will explain the Best Method to Enable a Windows Passwordless Experience with Microsoft Intune. The near future is passwordless. Microsoft is expanding its passwordless experience for Windows, particularly for devices joined to Microsoft Entra ID.
This new feature, got introduced with the September 2023 update to Windows 11 (version 22H2), allows organizations to enable passwordless authentication methods like Windows Hello for Business and FIDO2 security keys. These methods are designed to be phish-resistant and more secure than traditional passwords.
Once the passwordless experience is enabled, users no longer need to enter a password to sign in, whether for in-session authentication, User Account Control (UAC), or the “Run as” administrator feature. Additionally, options to change passwords are removed from settings, though users can still manage their accounts using the “Ctrl + Alt + Del” method.
Once the policy is configured, passwords are eliminated from the user interface for both device sign-in and in-session auth scenarios, such as “Run as” admin scenarios, password managers in web browsers, and User Account Control (UAC). Instead of using a password for login, users will need to utilize Windows Hello.

Table of Contents
Enable Windows Passwordless Experience Microsoft Recommendations
Before enabling Windows passwordless experience, take into consideration the following list of Microsoft recommendations.
| Details |
|---|
| Configure the PIN reset feature so users can reset their PIN from the lock screen if Windows Hello for Business is enabled. With KB5030310, the PIN reset process is enhanced in Windows 11, version 22H2. |
| Don’t set up the security rules. Interactive sign-in: Don’t show the most recent sign-in as this interferes with the Windows passwordless experience. |
| Do not disable the password credential provider by using the Exclude credential providers policy. The following are the main distinctions between the two policies. |
| All accounts, including local accounts, have their passwords disabled by the Exclude credential providers policy. Only Microsoft Entra accounts that log in using Windows Hello or a FIDO2 security key are eligible for the Windows passwordless experience. Additionally, it removes Other User from the policy, giving users an additional way to log in. |
| The RDP and Run authentication scenarios are prohibited from using passwords due to the Exclude Credential Providers policy. |
| Consider enabling the local administrator account or creating a new one and using the Windows Local Administrator Password Solution (LAPS) to randomly generate its password in order to streamline helpdesk support operations. |
- Quick Fix to your Windows OS Issues with Detection and Remediation Scripts with Intune
- Easy Guide to Deploy Azure VPN Client Microsoft Store App using Intune
- How to Set App Defaults using Intune | Export the Default XML File & Encode it in Base64 format
Create Enable Windows Passwordless Experience Configuration Policy in Intune
Users can rely on PIN reset or web sign-in options if passwordless methods fail. This update is part of Microsoft’s ongoing effort to enhance security by reducing reliance on passwords and encouraging organizations to adopt more secure and modern authentication methods.
Users can use recovery tools like Web sign-in and PIN resets to retrieve their login credentials, avoiding contacting the IT help desk if they cannot sign in.
Follow the steps below to create an Enable Windows Passwordless Experience configuration policy with Microsoft Intune. Log in to the Microsoft Intune Admin Center using your Intune administrator credentials.
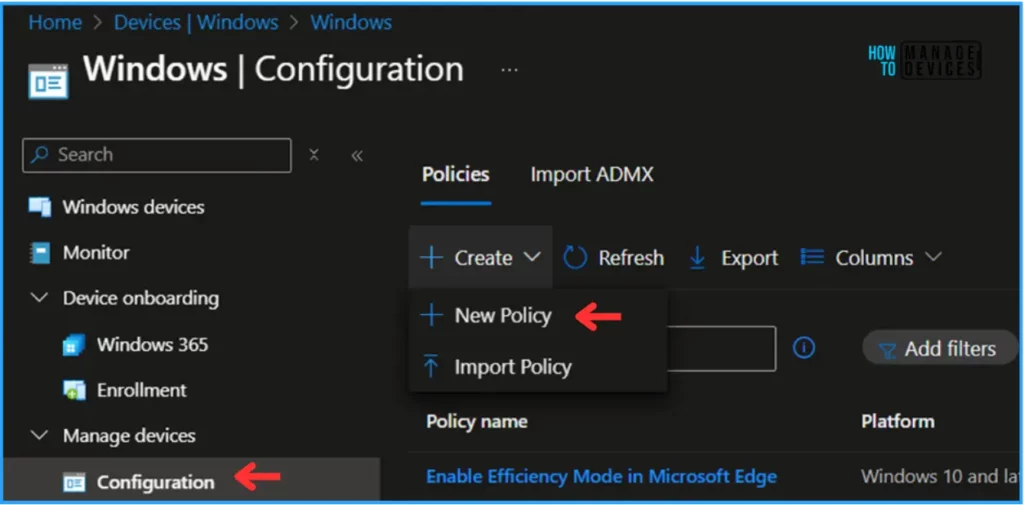
- Navigate to Devices > Windows > Configuration
- Click on +Create > +New Policy
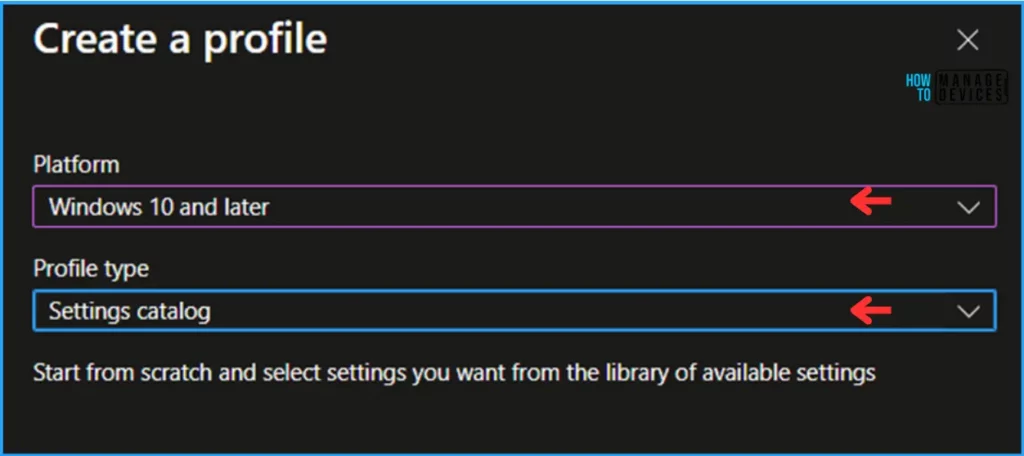
In the next step, we can create a new Configuration Profile from scratch. First, we need to provide the options mentioned below.
- Platform: Windows 10 and later
- Profile type: Settings catalog
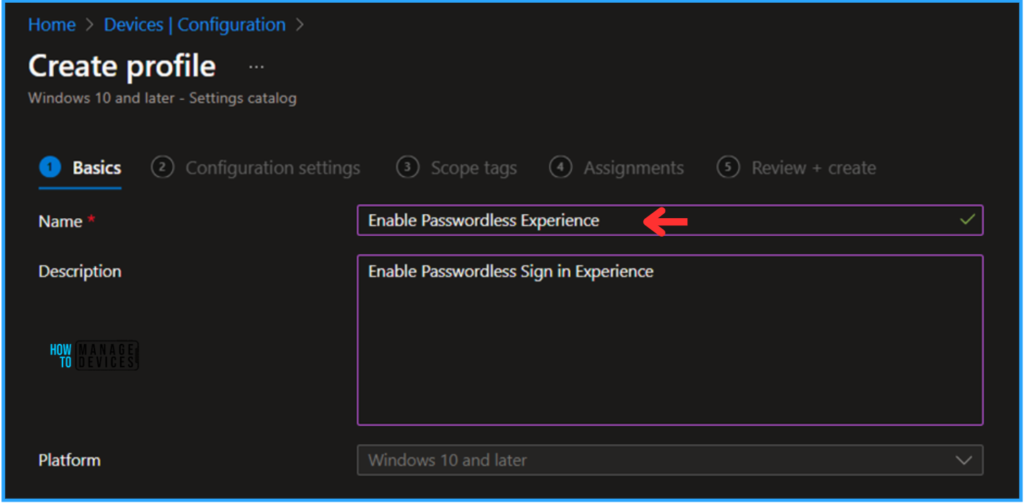
On the Basics details page, we can name the configuration profile “Enable Windows Passwordless Experience”, briefly describe the policy’s use and click Next.
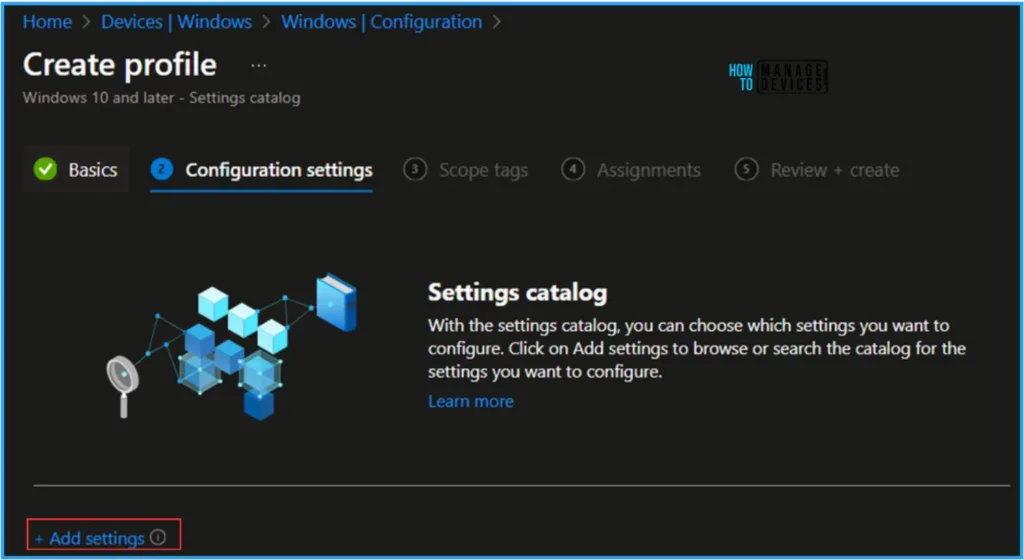
We can now add the required settings to the Configuration Settings pane. To do so, click +Add settings in the bottom left corner of the page.
Search for “Enable Passwordless Experience” as a keyword. This will help you find the correct policy based on our current needs. Now you can see the browse by category found as Authentication. Click that to find “Enable Passwordless Experience” Select the check option and close the Settings picker pane.
Note! Specifies whether connected users on AADJ devices receive a Passwordless experience on Windows. The feature defaults to the existing edition and device capabilities, Enabled. The Passwordless experience will be enabled on Windows and Disabled. The Passwordless experience will not be enabled on Windows.
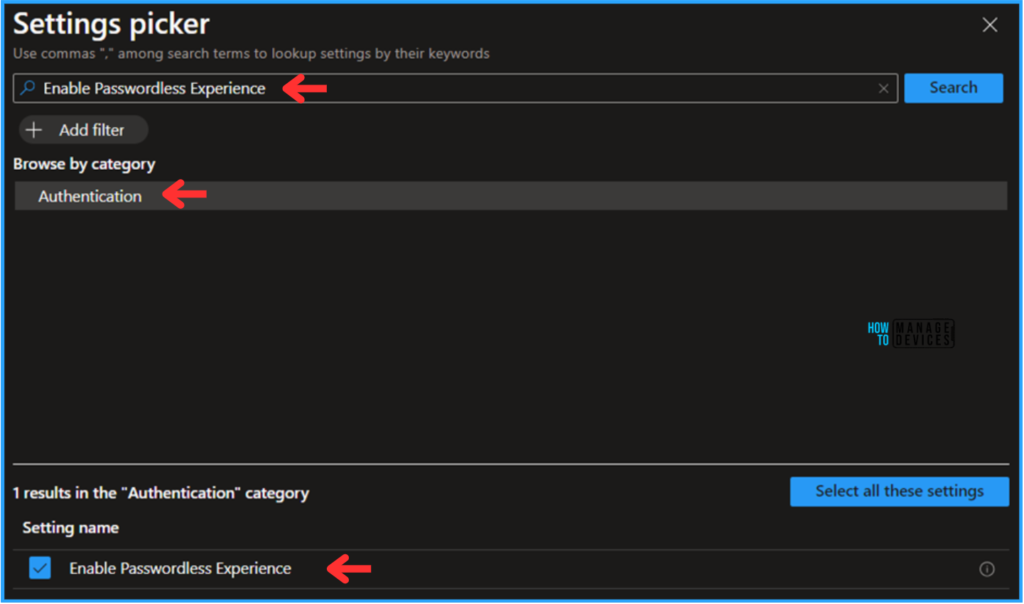
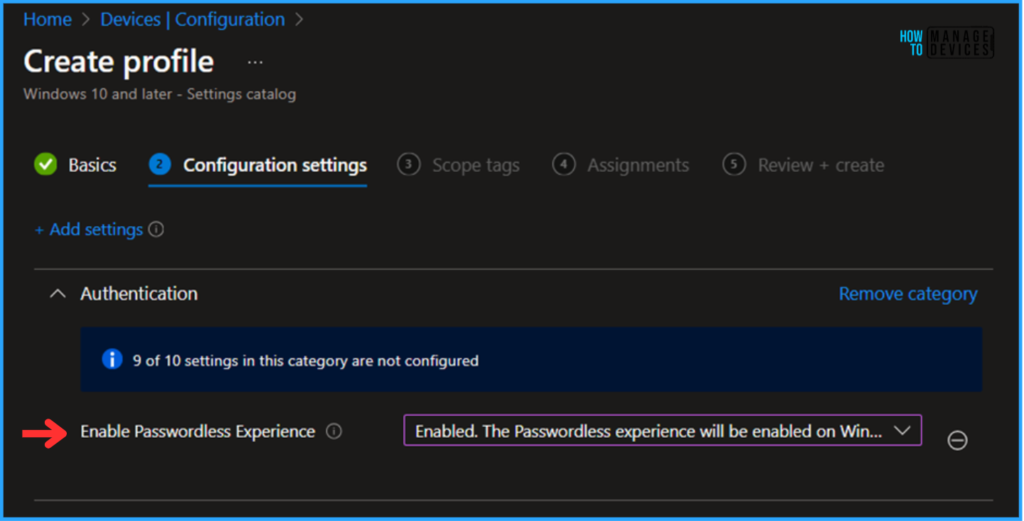
On the next page, in the Enable Passwordless Experience drop-down menu, select Enabled. The Passwordless experience will be enabled on the Windows option, and click Next.
On the next page, Leave the Scope tags as Default. If you have any custom scope tags available, you can also select them for this policy assignment.
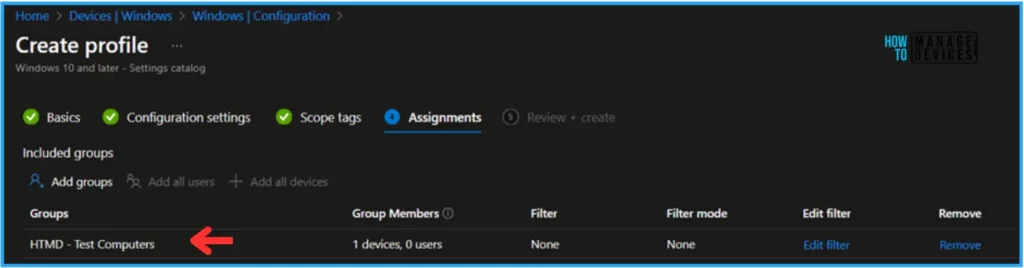
Click on Next and assign the configuration profile to HTMD – Test Computers. Then click Add Groups and select the required device group using the Included Groups option.
- New Windows Autopilot Device Preparation Experience using Intune
- Best Method to Add a Local User to Local Administrator Group with Intune Local User Membership Policy
- Intune Win32 App Supersedence and Auto App Update Explained
On the Review + Create page, carefully review all the settings you’ve defined for the “Enable Windows Passwordless Experience” configuration. Once you’ve confirmed everything is correct, select Create to deploy the Configuration Policy.
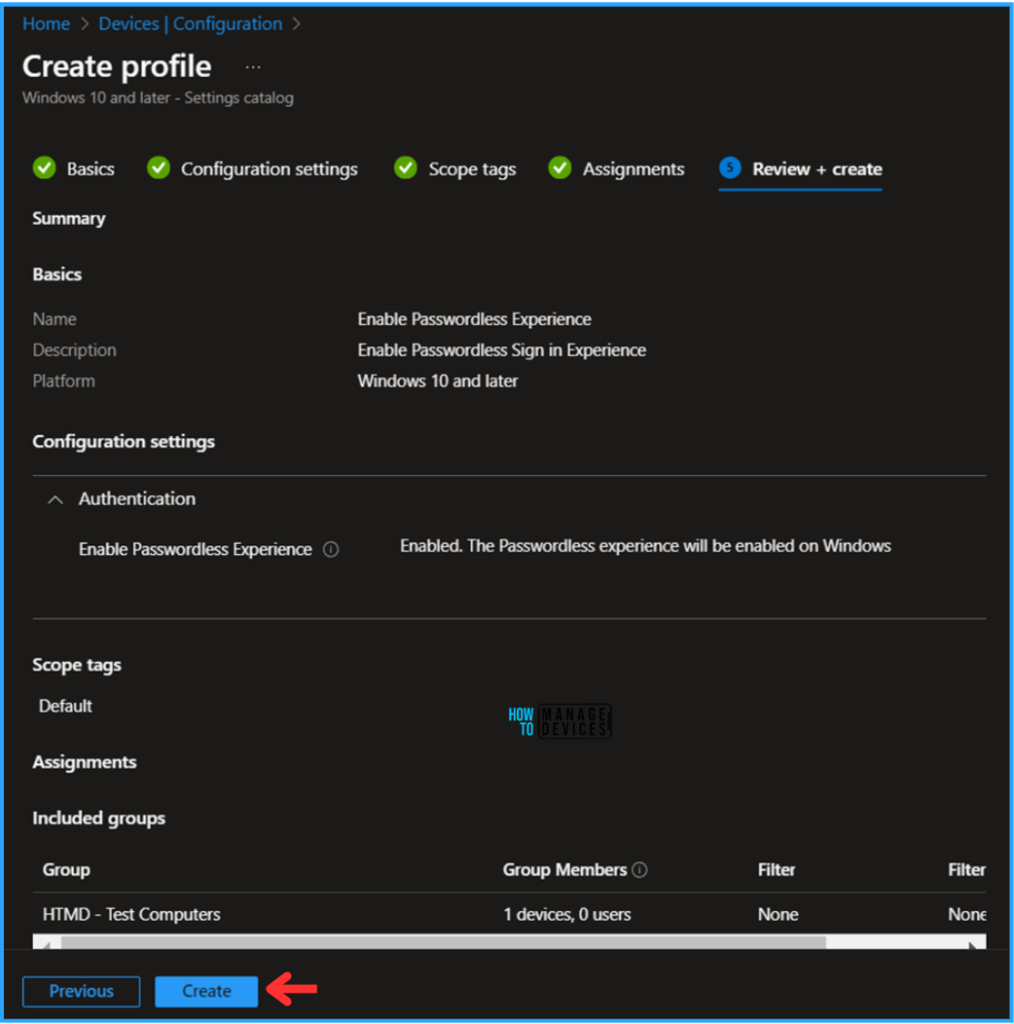
Monitor the Enable Windows Passwordless Experience Policy Deployment
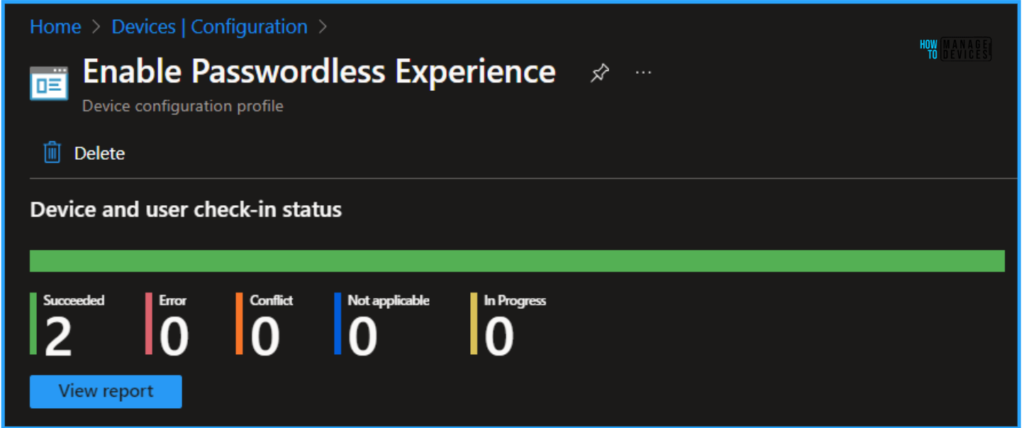
This configuration policy has been deployed to the Microsoft Entra ID group (HTMD – Test Computers). Once the device is synced, the profile will take effect immediately. To monitor the profile deployment status from the Intune Portal, follow the steps below.
- Navigate to Devices > Windows > Configuration > Search for the “Enable Passwordless Experience” configuration.
- Under the Device and user check-in status, you can see the policy’s deployment status.
End User Experience – Enable Windows Passwordless Experience Policy
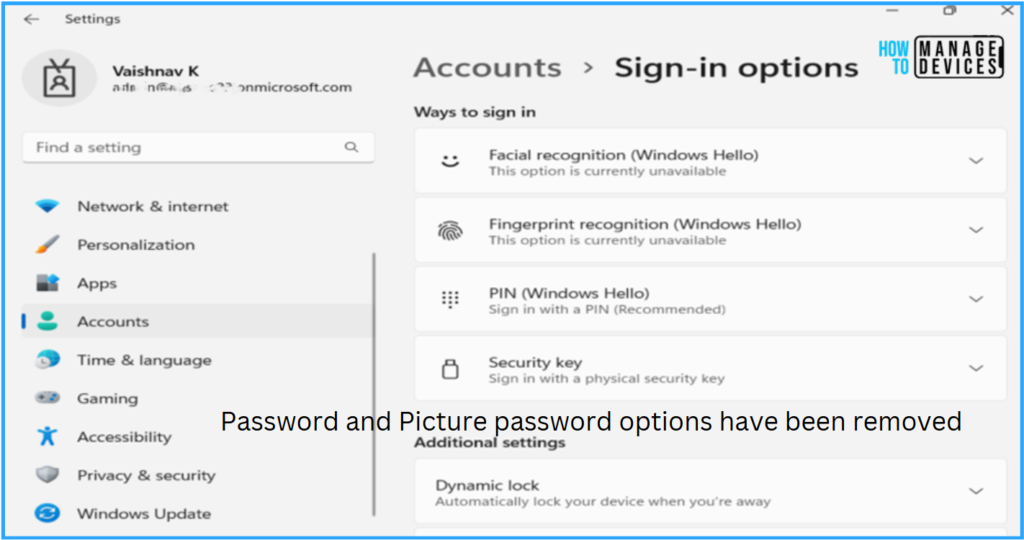
Now we have to check whether the Enable Windows Passwordless Experience worked. To check the same. Log in to one of the policy-targeted devices.
- Click on Start > Settings > Accounts > Sign-in options
All allowed Sign-in options except the Password and Picture password are available on the device. So we can conclude our policy is working perfectly fine!
Author
Vaishnav K has over 11 years of experience in SCCM, Device Management, and Automation Solutions. He writes and imparts knowledge about Microsoft Intune, Azure, PowerShell scripting, and automation. Check out his profile on LinkedIn.
