Let’s discuss the 4 Step Guidance Excel Template for Zero Trust Adoption and Business Scenarios. In this article, I explain the concept, starting with an excellent reason for using Zero Trust principles in your business.
This Zero Trust adoption guidance recommends forming a solid Zero Trust strategy and framework by concentrating on several key business scenarios. These scenarios include swiftly enhancing your security measures, ensuring the safety of remote and hybrid work setups, identifying and safeguarding critical business data, minimizing the impact of potential breaches, and adhering to regulatory and compliance standards.
By addressing these scenarios, organizations can effectively develop and implement a robust Zero Trust approach to their needs, enhancing overall security posture and resilience against cyber threats.
In one of our articles, we explain how to set up Microsoft Copilot while incorporating Zero Trust principles. We break down the process into manageable steps, guiding you through preparing Copilot to work securely within a zero-trust framework.
In this post, you will find everything you need about a simple 4-step Excel template for adopting Zero Trust principles and handling various business situations.

- Microsoft Defender Zero Day Vulnerability and FIX
- 2024 Cybersecurity Certifications for IT Professionals
4 Step Guidance Excel Template for Zero Trust Adoption and Business Scenarios
This Zero Trust adoption guidance focuses on constructing a robust Zero Trust strategy and architecture for specific business scenarios. The following scenarios are used.
| Business Scenarios | Details |
|---|---|
| Rapid Modernization of Security Posture | You can implement rapid upgrades to enhance the organisation’s overall security posture. |
| Securing Remote and Hybrid Work | You should ensure secure access and protection for employees working remotely or in hybrid environments. |
| Identification and Protection of Sensitive Business Data | Identify critical business data and implement measures to safeguard it from unauthorized access or exposure. |
| Prevention or Reduction of Business Damage from Breaches | Developing strategies and technologies to prevent or minimize the impact of security breaches on business operations. |
| Meeting Regulatory and Compliance Requirements | Ensuring alignment with regulatory standards and compliance requirements affects the industry and ensures adherence to legal obligations and standards. |
Structured Zero Trust Implementation Process
Let’s discuss the Structured Zero Trust Implementation Process. The above-mentioned business scenarios divide the Zero Trust implementation process into manageable components, facilitating progression across 4 implementation stages.
- The structured approach enables organizations to prioritize tasks and monitor progress
PowerPoint Slide Deck for Zero Trust Progress Tracking
This guidance includes a PowerPoint slide deck with progress slides explicitly used for presenting and monitoring work progress to business leaders and stakeholders. These slides have features aimed at facilitating the easy tracking and presentation of the advancement of your Zero Trust implementation efforts.
PowerPoint Slide Deck for Zero Trust Progress Tracking – PowerPoint slide deck
Excel Workbook for Business Scenario Progress Tracking
This guidance includes an Excel workbook featuring individual worksheets for each business scenario. These worksheets are designed to assist you in assigning owners and monitoring progress for each stage, objective, and task related to the respective scenario.
Excel Workbook for Business Scenario Progress Tracking – Excel workbook
Business Scenario Objectives
By systematically filling out the rows, assigning owners, tracking status, and accessing linked resources, you can effectively manage the implementation of Zero Trust principles across different business scenarios. To use this Excel workbook, follow these steps.
- Each worksheet in the workbook corresponds to a specific Zero Trust adoption framework business scenario.
- Each row within the worksheet represents an objective for each of the 4 stages of the Plan phase of the scenario.
- Assign owners for each objective by filling in the designated columns.
- Use the workbook to monitor the status of each objective. You can update the status as tasks are completed or in progress.
- Utilize the links provided within the workbook to access key documentation resources relevant to each objective.
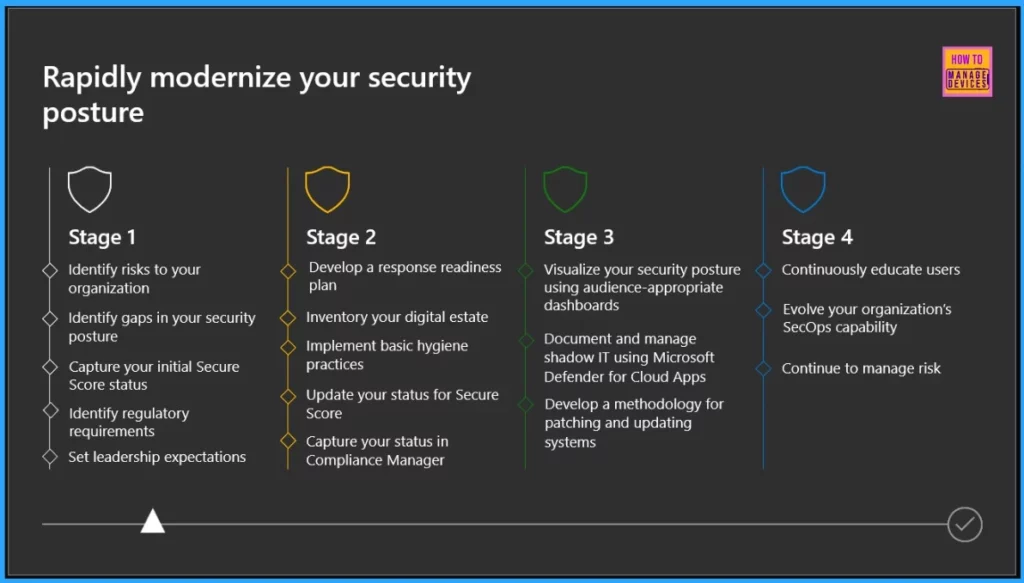
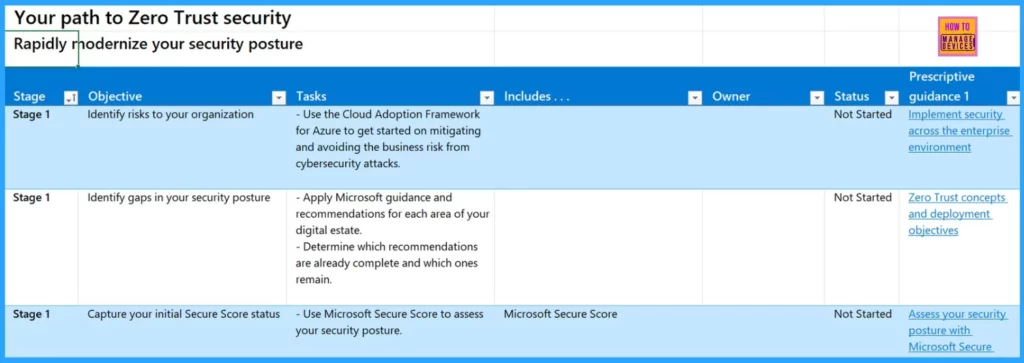
Rapidly Modernize your Security Posture
To implement Zero Trust security, you will start with Stage 1. In this stage, your objective is to identify risks to your organization and gaps in your security posture. One task involves capturing your initial Secure Score status.
| Rapidly Modernize your Security Posture |
|---|
| Use Cloud Adoption Framework for Azure |
| Apply Microsoft Guidance |
| Evaluate Recommendations |
| Assess with Microsoft Secure Score |
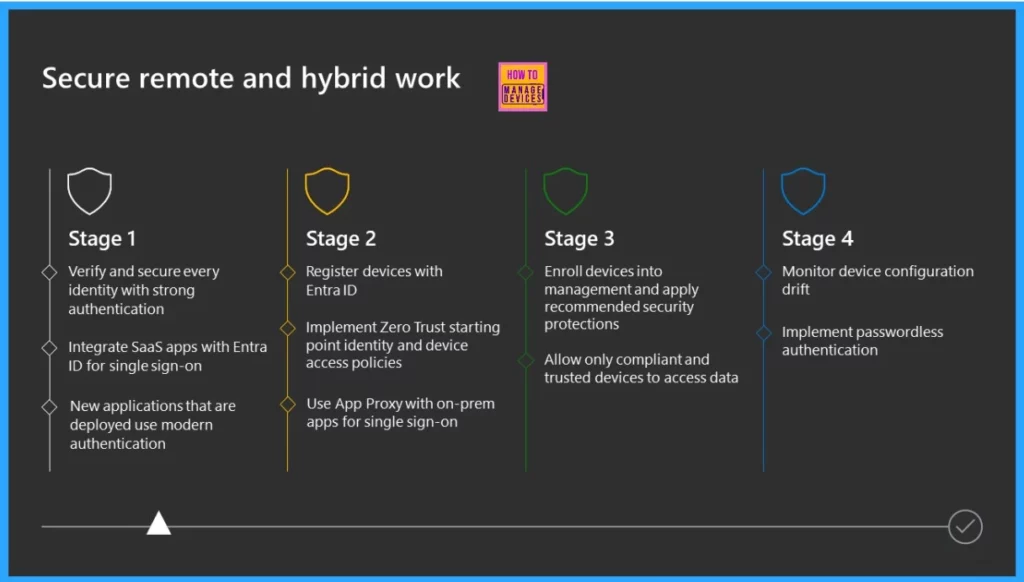
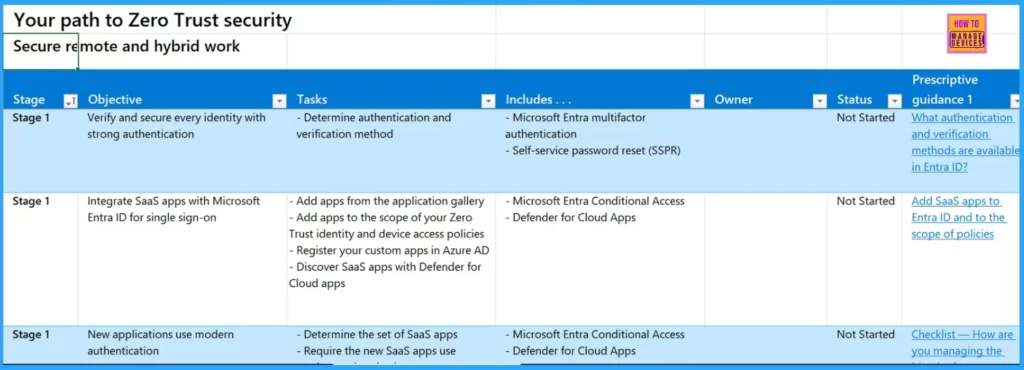
Secure Remote and Hybrid Work
To ensure secure remote and hybrid work, you will begin with Stage 1, focusing on verifying and securing every identity with strong authentication. Completing the below tasks will strengthen the security of remote and hybrid work setups, ensuring that every identity is verified and protected against potential threats.
- Determine Authentication Method
- Integrate SaaS Apps with Microsoft Entra ID
- Ensure New Applications Use Modern Authentication
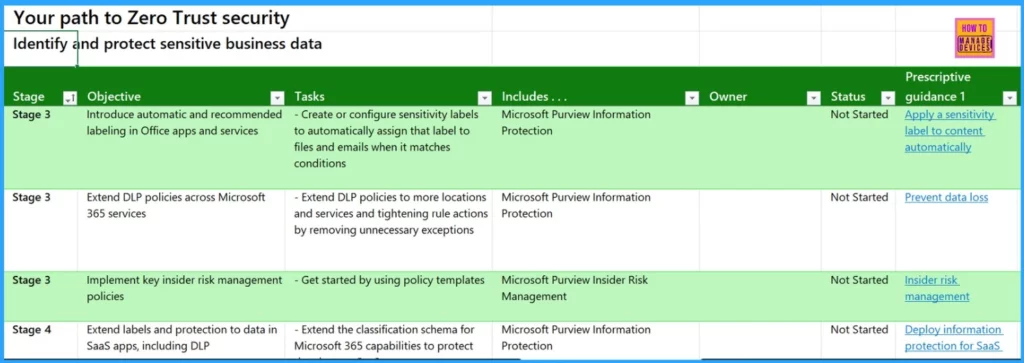
Identify and protect Sensitive Business Data
To protect sensitive business data effectively, you will focus on Stage 3 and Stage 4 tasks. By completing the below functions, you can quickly strengthen your organization’s ability to identify and protect sensitive business data, mitigating risks and ensuring compliance with data protection regulations.
- Extend DLP Policies Across Microsoft 365 Services
- Implement Key Insider Risk Management Policies
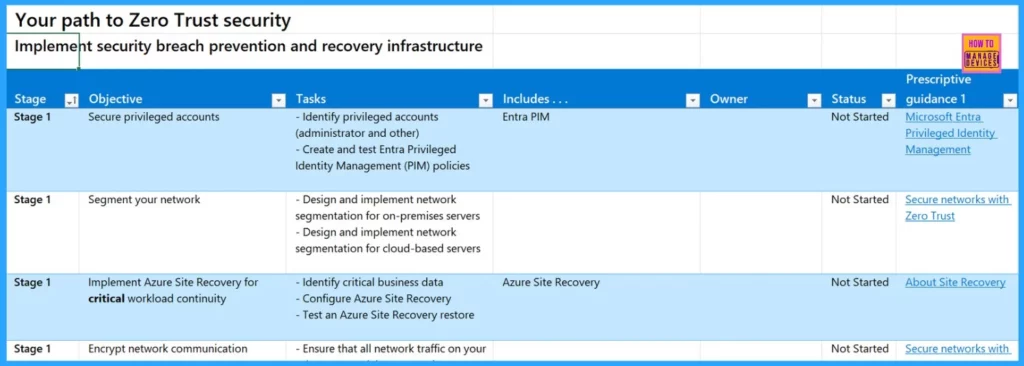
Implement Security Breach Prevention and Recovery Infrastructure
Stage 1 of implementing security breach prevention and recovery infrastructure focuses on several key objectives. The key objects are as follows.
- Secure Privileged Accounts
- Segment Your Network
- Implement Azure Site Recovery for Critical Workload Continuity
- Encrypt Network Communication
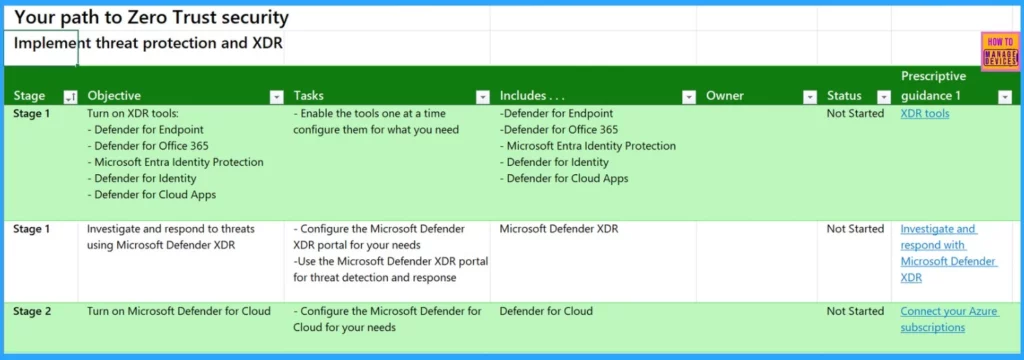
Implement Treat Protection and XDR
Stage 1 focuses on implementing threat protection and Extended Detection and Response (XDR) capabilities. In Stage 2, you will turn on Microsoft Defender for Cloud and configure it according to your requirements.
- Configuring Microsoft Defender XDR Portal
- Configuring Microsoft Defender for Cloud
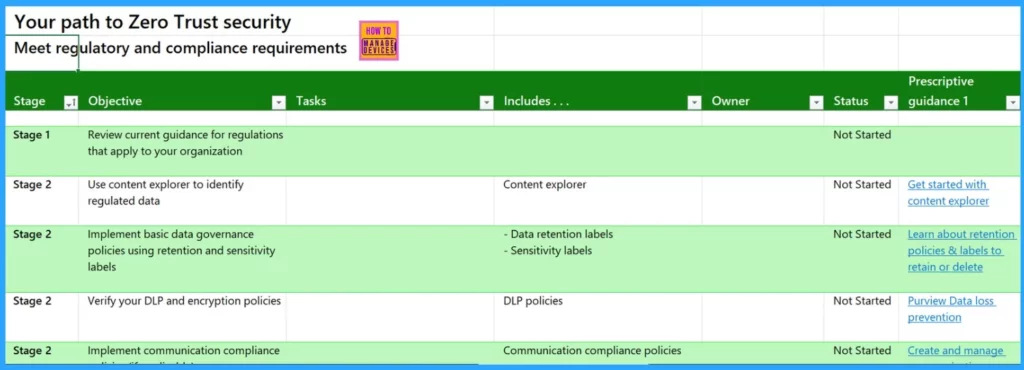
Meet Regulatory and Compliance Requirements
In Stage 2 of the process, the objective is to focus on regulatory compliance and data governance. Additionally, you should implement communication compliance measures. This involves setting up tools and processes to monitor and enforce organisational communication policies.
Resources
Zero Trust adoption framework overview | Microsoft Learn
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
About the Author: Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing about Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.
