Let’s see how you can filter application Using Azure AD Conditional Access Policy. Filters for apps provide a new way to manage Conditional Access assignments for apps and workload identities at scale.
Filter for applications is currently in public preview. Filters for apps are a nice addition to Conditional Access policies to only target specific applications. This conditional Access policy can be applied to all apps or to individual apps.
Application filters are a new feature for Conditional Access that allows organizations to tag service principals with custom attributes. These custom attributes are then added to their Conditional Access policies.
With filters for apps, admins can tag applications with custom security attributes and apply Conditional Access policies based on those tags, rather than individually selecting apps.
There is no limit on the number of apps covered, and new apps you add with the attributes are automatically included in the policies. Attribute assignment builds on top of custom security attributes, delivering attribute customization and a rich delegation model.
- Easiest Method To Enable MFA For Admins Using Azure AD Conditional Access
- Intune Filters For Assigning Apps Policies And Profiles In Intune Portal
Custom security attributes are security sensitive and can only be managed by delegated users. Even global administrators don’t have default permissions for custom security attributes. By default, Global Administrator and other administrator roles do not have permission to read, define, or assign custom security attributes.
One or more of the following roles should be assigned to the users who manage or report on these attributes. Assign the appropriate role to the users who will manage or report on these attributes at the directory scope
| Role name | Description |
|---|---|
| Attribute assignment administrator | Assign custom security attribute keys and values to supported Azure AD objects. |
| Attribute assignment reader | Read custom security attribute keys and values for supported Azure AD objects. |
| Attribute definition administrator | Define and manage the definition of custom security attributes. |
| Attribute definition reader | Read the definition of custom security attributes. |
Filter Application Using Azure AD Conditional Access Policy
Here’s how, you create a custom attribute set, assign a custom security attribute to your application, and create a Conditional Access policy to secure, and filter application.
You can configure the conditional access policies from different portals such as Azure, MEM Admin center, and AzureAD Portal. Here, I will use the Azure portal to configure the Conditional Access policies for filter application.
- Sign in to the Azure portal http://portal.azure.com/ as a Conditional Access Administrator, Security Administrator, or Global Administrator.
- Navigate to the Azure Active Directory > Security > Conditional Access. Select New policy.
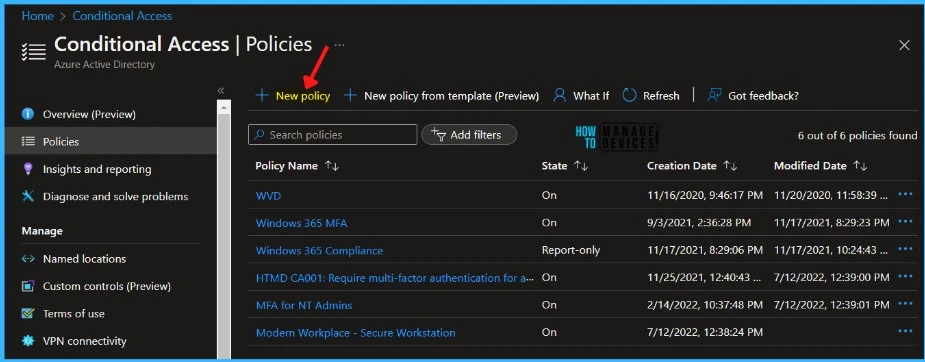
Provide the appropriate name for your policy. It is recommended to use standard names for policies.
- Under Assignments, select Users or workload identities.
- Under Include, select All users.
- Under Exclude, select Users and groups and choose your organization’s emergency access or break-glass accounts and Select Done.
- Under Cloud apps or actions, select the following options:
- Select what this policy applies to Cloud apps.
- Include Select apps.
- Select Edit filter and Set Configure to Yes.
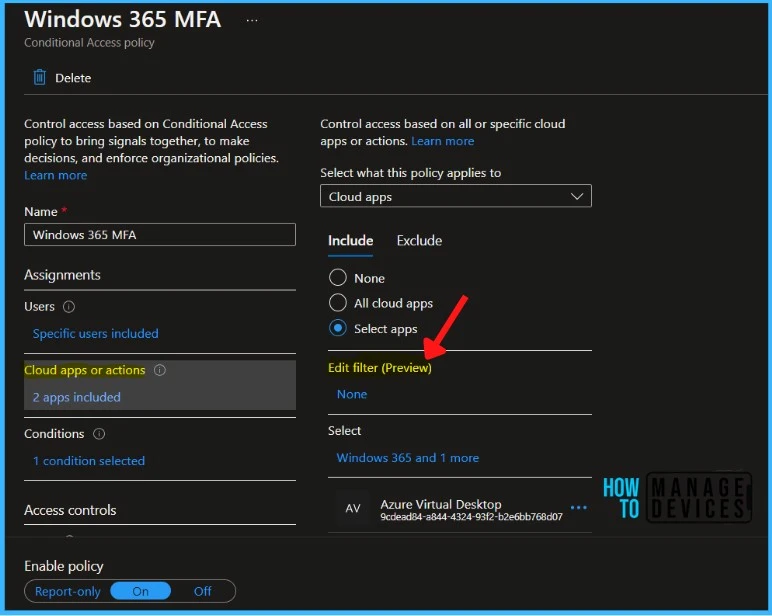
In the Filter, you can select the Attribute, Set Operator and set the Value, and click Done.
Cloud app assignment supports filters for apps. You can configure filter expression rules that get evaluated when an app is accessed. When a new app is onboarded, you only need to tag it with an attribute to bring it into the scope of the desired policy.
For example, you can create a custom security attribute to tag apps with an app category, like HR or Finance. Apps with one of these tags will then immediately have policy enforced.
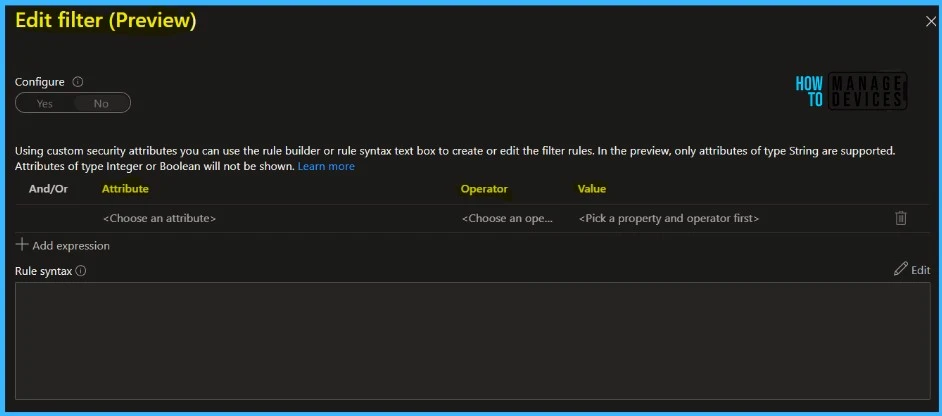
Confirm the specified settings and select Create to enable your policy. You can check out the Microsoft documentation for more details about how to create Conditional Access filters for apps.
