Let’s see the easiest method to enable MFA for Admins using Azure Active Directory Conditional Access policies. I have seen building an entire server infrastructure to enable multi-factor authentication. The Azure AD Conditional Access is the service offered by Microsoft to bring all the security signals together, make decisions, and enforce organizational policies.
Enabling MFA for admins becomes easy with Azure AD Conditional Access (CA) policy templates; it’s pretty straightforward. Let’s learn how to create, configure, and test Azure AD Conditional Access policies using CA policy templates. You can enable MFA for normal users using the following guide – Quick Guide to Enforce Multifactor Authentication MFA for Users.
The Azure AD conditional access policies are the first layer of defence, in my opinion. You should enable the MFA using Azure AD conditional access for all the portals such as Azure, MEM Admin Center, Microsoft 365, Teams, etc.
Microsoft is also pushing for password-less authentication scenarios and adding new capabilities, such as autofill passwords with the Microsoft Authenticator app. I use the Microsoft Authenticator app for all Multi-Factor Authentication scenarios.
Enable MFA for Admins using Azure AD Conditional Access
Let’s see how to configure MFA for admins using Azure AD Conditional Access policies. You can configure the conditional access policies from different portals such as Azure, MEM Admin center, etc. In this post, I will use the Azure portal to configure the Conditional Access policies.
- Login to Azure Portal.
- Search for the “Azure Active Directory Conditional Access” workflow.
Conditional Access Policy Template
Now, it’s time to create the CA policy using the policy template. The Azure AD Conditional Access policy creation and design are very complex processes, and you have many configuration options. I feel the Conditional Access policy templates are very useful for people like me.
Let’s create the MFA enforcement policy for admins using Conditional Access (CA) policy templates. You will need to follow the steps mentioned below to start the policy creation process.
- Login to Azure Portal.
- Search for the “Azure Active Directory Conditional Access” workflow.
- Go to Policies node.
- Click on + Create Policy drop-down option.
- Select Create new policy from templates option.
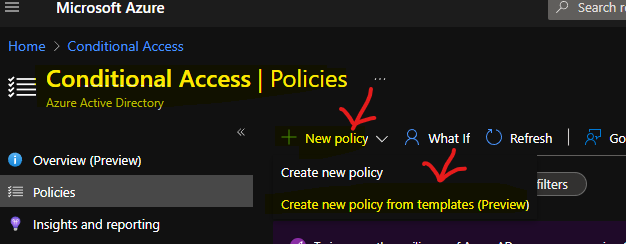
The Azure AD Conditional Access policy predefined templates are customized based on the type of policy you’re looking to create. You will need to select a template category from the following list. In this scenario, to enable MFA for Azure administrators, you will need to choose Identities.
- Identities
- Devices
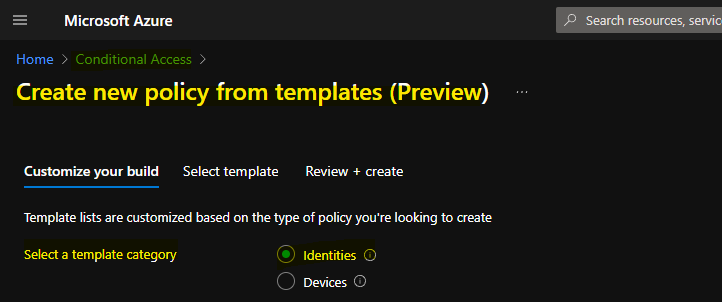
You will have options to select many CA policy templates, but the most suitable one to enforce or enable MFA for admins is Require Multi-Factor authentication. You will need to choose the same template and click on the NEXT button to continue.
Require multi-factor authentication for admins – Require multi-factor authentication for privileged administrative accounts to reduce the risk of compromise. This policy will target the same roles as Security Default.
Conditional Access Policy Report-Only Mode
Let’s deploy this CA policy using the Conditional Access Policy Report-Only Mode. This will help you to assess how this policy is performing in different scenarios. This is a very important setting, and I always recommend using Conditional Access Policy Report-Only Mode for the initial testing of CA policies.
You have the option to change the default Conditional Access policy name as per your organization’s standard. Also, you will need to make sure that apply this policy only in Report-Only mode for the initial deployment.
Name of the Policy – HTMD CA001: Require multi-factor authentication for admins
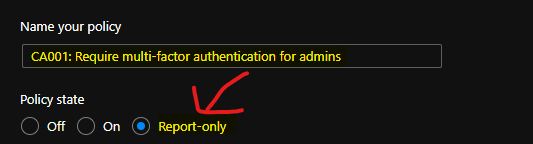
I like one thing about this Require multi-factor authentication for admins template, which excludes, users. This template helps to avoid any lockout situation because of the new CA policy implementation. The current user who is creating this CA policy is, by default, excluded from the policy.
The Conditional Access policy to enable MFA for admins is deployed based on the directory roles of an admin. So, if you have any custom roles created for AVD or any other cloud deployments, you will also need to include those roles in this CA policy.
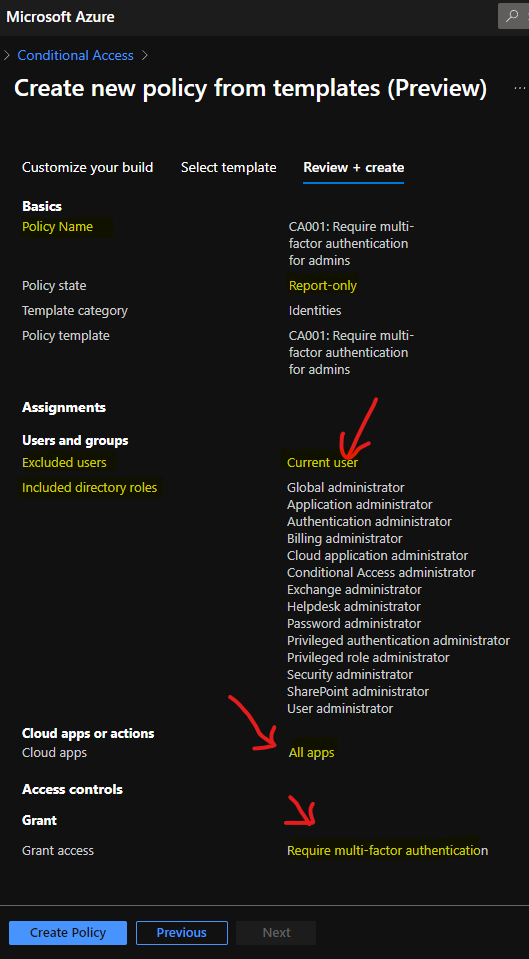
The Conditional Access policy creation is completed for enabling the MFA for admins now. You can get this confirmation from the following notification in Azure Portal.
Successfully created ‘CA001: Require multi-factor authentication for admins. The policy will be enabled in a few minutes if you have “Enable policy” set to “On.”
Confirm Conditional Access Report-Only Policy Verification
You will need to verify whether the Azure AD Conditional Access policy is working as expected using the Report-only mode. You can check this from the Sign-in Logs option from Azure Portal – Azure AD Conditional Access – Policies node.
In the Sign-in logs, you would be able to see many login details for the user that you are testing. Click on that login attempt to the Azure portal. This will open up another blade called Activity Details: Sign-ins. Go over to the Report-only tab mentioned in the screenshot below.
- Login to Azure Portal.
- Search for the “Azure Active Directory Conditional Access” workflow.
- Navigate to Policies – Sign-in logs.
- Click on any of the activity log for specific Azure portal login.
- Go over to Report-only tab to get more details.
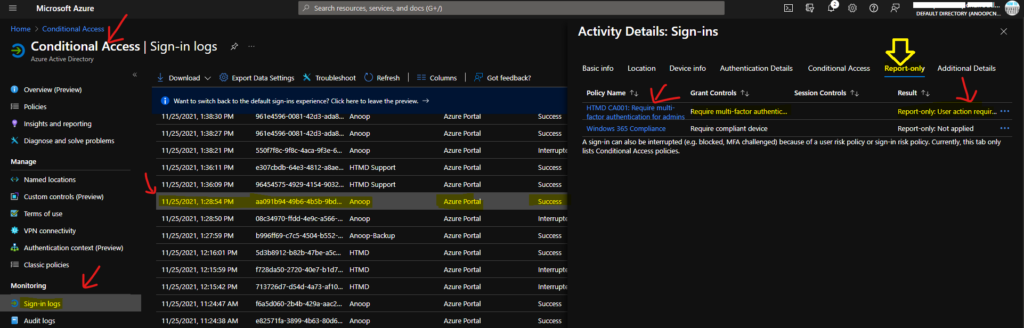
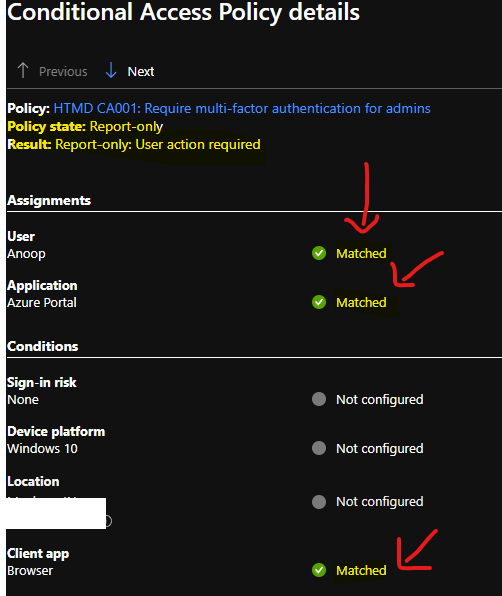
It seems the Azure AD Conditional Access policy read-only option testing is completed here. As you can see, the conditional access engine assessed the conditional for reporting purposes. The result you can see in the below list is Report-only: User Action Required.
- Policy: HTMD CA001: Require multi-factor authentication for admins Policy
- State: Report-only
- Result: Report-only: User action required
Also, you can see the assignment details for the same AAD Conditional Access policy deployed in read-only mode.
- Assignment Details
- User – Anoop – Matched
- Application – Azure Portal – Matched
- Client App – Browser – Matched
How to Change Azure AD Conditional Access Policy Read-Only to ON Mode
You can confirm that the Conditional Access policy to enable Multi-Factor Authentication for the admins is working fine as per the above report-only deployments.
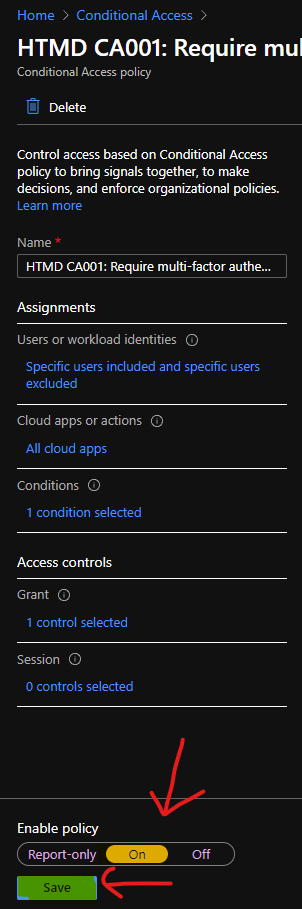
Now, it’s time to move the Azure AD CA policy from Read-Only to ON mode. This is the phase where all the admins will get the new MFA prompt when logging in to Azure or MEM admin center or Microsoft 365 portals.
NOTE! – If the admin is already login to the portal before enabling this policy, then after 10-15 minutes, the Conditional Access engine will enforce the policy. The admins will be forced to sign in again with Multi-Factor Authentication (MFA).
- Login to Azure Portal.
- Search for the “Azure Active Directory Conditional Access” workflow.
- Click on the Policies node.
- Click on the Conditional Access policy that you created to enable MFA for Admins.
- Scroll down and move the slide bar to ON button.
- Click on the SAVE button to continue.
NOTE! – Once you enable the Azure AD Conditional Access policy, the internal process is going to take a few minutes to get this policy enabled for your tenant and all the admins. So, there will be a few minutes of delay after you enable the policy and get the user experience or admin experience explained below.
Enable MFA for Admins Experience
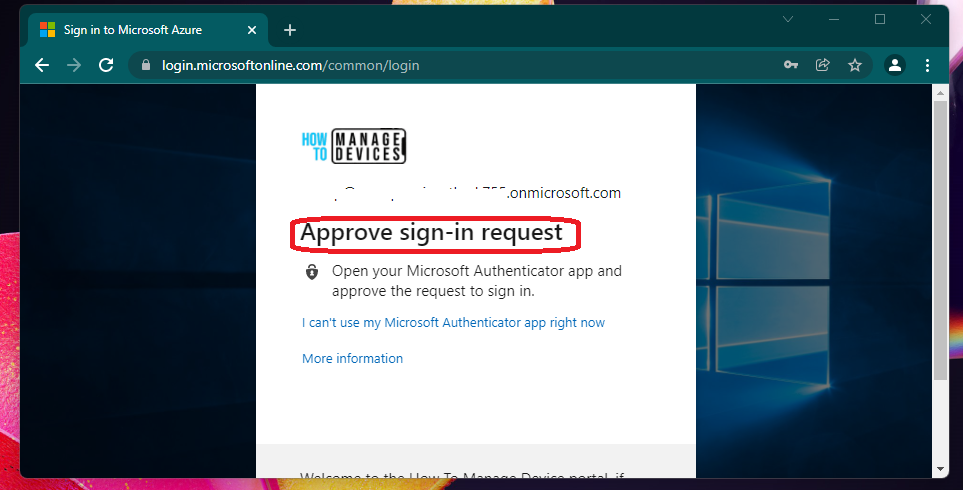
You have already enabled the MFA. The following would be the experience that admins will get when they log in after implementing the above-discussed Azure AD conditional access policy. The admins will get a slightly different experience when they are already login to browsers before implementing the AAD CA policy.
More details are given in the following paragraph of this post. The MFA authentication preference can be set from the admin user profile. You can go into https://myaccount.microsoft.com/?ref=MeControl site and change the configurations.
I have a post that explains the account configurations, such as receiving a text message, call, or using the Microsoft Authenticator App to complete the MFA for admins.
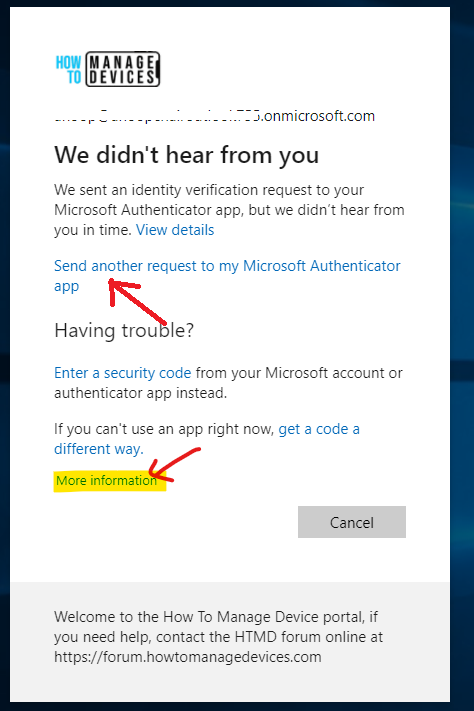
If you don’t respond to the Azure AD Conditional Access MFA prompt, you might get the following error or message.
We didn’t hear from you – We sent an identity verification request to your Microsoft Authenticator app, but we didn’t hear from you in time.
The option that you have then is to Send another request to my Microsoft Authenticator app.
Suppose you can’t use the Microsoft Authenticator app for some reason to complete the multi-factor authentication requests. In that case,t case, you will get the following options to complete the MFA process.
- Enter a security code from your Microsoft account or authenticator app instead.
- If you can’t use an app right now, get a code a different way.
- More information
Already Logged Admins Experience After MFA Implementation
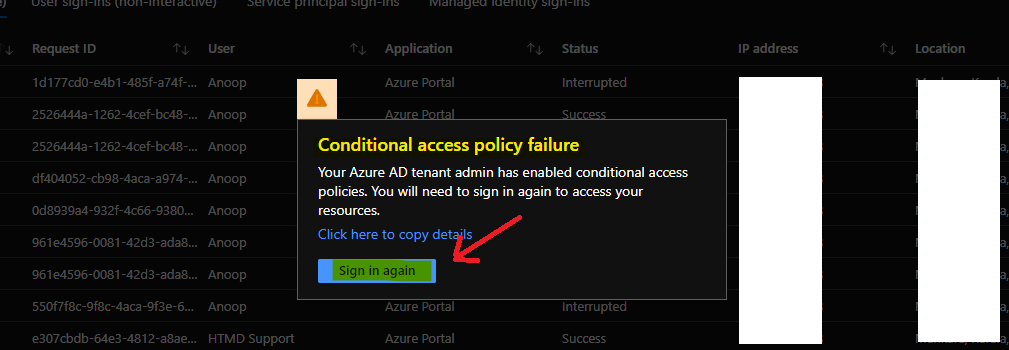
Now, let’s check what the experience is for Already Logged Admins after the MFA Implementation. The admins will get a popup prompt such as Conditional Access Policy Failure. Your Azure AD tenant admin has enabled conditional access policies. You will need to sign in again to access your resources.
Click on the Sign in Again button to log back into all the cloud apps clouding browsers such as Azure or MEM Admin center, or Microsoft 365 portal.
“AADSTS50076: Due to a configuration change made by your administrator, or because you moved to a new location, you must use multi-factor authentication to access“
Author
Anoop is Microsoft MVP! He is a Solution Architect in enterprise client management with more than 20 years of experience (calculation done in 2021) in IT. He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc……………
