Let’s find the easiest way to create a restart VM helpdesk operator Azure RBAC custom role for Azure Virtual Desktop (AVD). There are many other ways to create a custom role in Azure using PowerShell and JSON file.
The easiest method I found to create a custom Azure RBAC role is using the Azure portal itself. If you want to recreate this custom role in different Azure Subscriptions, you can use the JSON file that I shared in the below section of the post.
There is no default Azure RBAC role to permit to restart of a VM for level 1 support. I think this is critical for initial or first-level troubleshooting for all Azure Virtual Desktop (a.k.a WVD). Also, the end-users can’t restart the VMs from the RD client or RD web portal. I know this is irrelevant for multi-session scenarios, but this restart button for end-users can be useful for a single session.
I think for both single and multi-session scenarios, you will need to create the Restart VM Helpdesk operator Azure RBAC custom role to avoid a lot of tickets coming to Level 2 teams.
- How to Add Azure Virtual Desktop Session Host to Azure AD Join Guide WVD AVD
- Download Azure Virtual Desktop eBooks
- FIX: AVD Azure AD Joined VM Login Issue with Error Code 0x9735
AVD Helpdesk Operator Roles
The following are the roles that I recommend to provide for Level 1 helpdesk resources. Are you using some different built-in roles to delegate permissions to helpdesk support? If so, let me know in the comments. These two roles didn’t come with restart VM permissions.
The Desktop Virtualization Reader role assigned for helpdesk support admin helps to view everything permissions in the deployment but doesn’t let them make any changes.
- Desktop virtualization reader
- Desktop Virtualization Session Host Operator
The Desktop Virtualization Session Host Operator role helps the helpdesk admins view and remove session hosts and change drain mode. They can’t add session hosts using the Azure portal because they don’t have “write permission” for host pool objects.
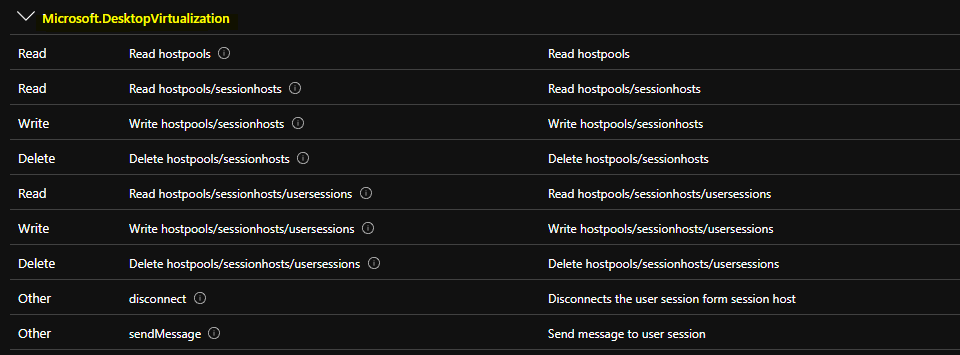
You will need to analyze/test the delete and write permissions assigned to the AVD Helpdesk admin role. These permissions need further assessment for each organization because it mainly depends on the existing support system.
| Type | Permissions | Details – Description |
|---|---|---|
| Read | Read hostpools | Read hostpools |
| Read | Read hostpools/sessionhosts | Read hostpools/sessionhosts |
| Write | Write hostpools/sessionhosts | Write hostpools/sessionhosts |
| Delete | Delete hostpools/sessionhosts | Delete hostpools/sessionhosts |
| Read | Read hostpools/sessionhosts/usersessions | Read hostpools/sessionhosts/usersessions |
| Write | Write hostpools/sessionhosts/usersessions | Write hostpools/sessionhosts/usersessions |
| Delete | Delete hostpools/sessionhosts/usersessions | Delete hostpools/sessionhosts/usersessions |
| Other | disconnect | Disconnects the user session form session host |
| Other | sendMessage | Send message to user session |
Custom Azure RBAC Role – Restart VM Helpdesk Operator
As mentioned above, there are many ways to create custom Azure RBAC roles. I have selected the easiest method in this post. For AVD Helpdesk admin, it’s very helpful to provide restart virtual machine (VM) permissions.
In my experience, 99.99% of AVD session host connectivity issues from RD Client and RD portal can be resolved by a restart. But, as you know, we don’t have a restart option for end-users from RD clients or RD web clients. Hence, it’s worth giving restart VM permission to the level 1 support team.
Let’s check how to build a custom Azure RBAC role for the AVD Helpdesk support team.
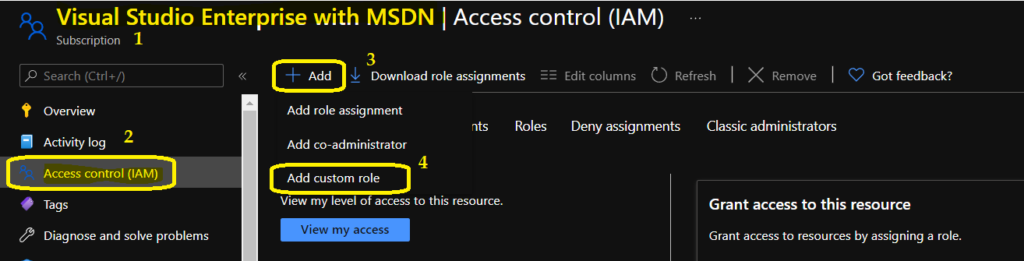
- Login to Azure portal – portal.azure.com.
- Navigate to Subscription – Access Control (IAM).
- Click on +add button and select Add Custom Role.
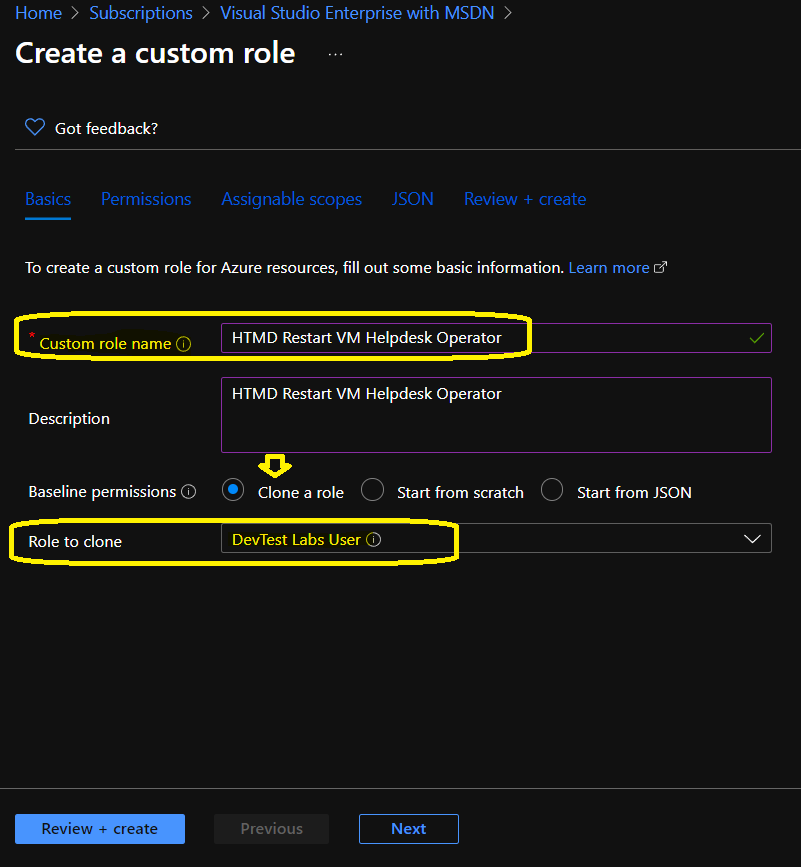
Enter the name of the Azure RBAC custom role. I choose the following name of the custom role HTMD Restart VM Helpdesk Operator. I recommend writing a detailed description of the Azure ARBAC custom role so that fellow admin can understand it quickly.
I normally use Clone a role to provide baseline permissions for the custom role. I have already checked the Microsoft documentation to understand the built-in Azure RBAC role that provides permission to restart the VM.
I selected the DevTest Labs User role as the role to clone. You will need to remove the additional permissions on this role to provide only the minimum required permissions for Restart VM Helpdesk Role.
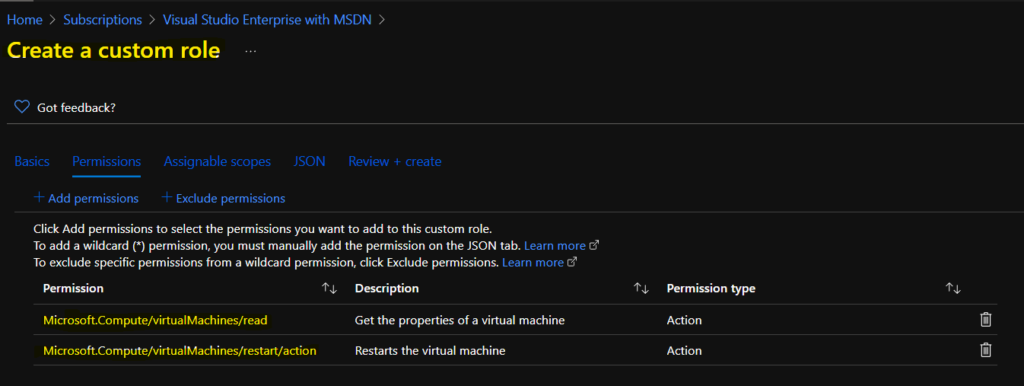
Add Permissions to Restart VM Helpdesk Operator
Let’s provide Add Permissions to Restart VM Helpdesk Operator role. You will need to keep only two permissions listed below and remove all the other permissions from the custom role. These two permissions help AVD admins to delegate restart Virtual Machine permission to Level 1 or the Helpdesk support team.
- Microsoft.Compute/virtualMachines/read – Get the properties of a virtual machine
- Microsoft.Compute/virtualMachines/restart/action – Restarts the virtual machine
Click Add permissions to select the permissions you want to add to this custom role. To add a wildcard (*) permission, you must manually add the permission on the JSON tab. To exclude specific permissions from wildcard permission, click Exclude permissions.
You will need to remove all the other permissions from the custom permission role for HTMD Restart VM Helpdesk Operator. This role should give only the restart permissions to helpdesk users.
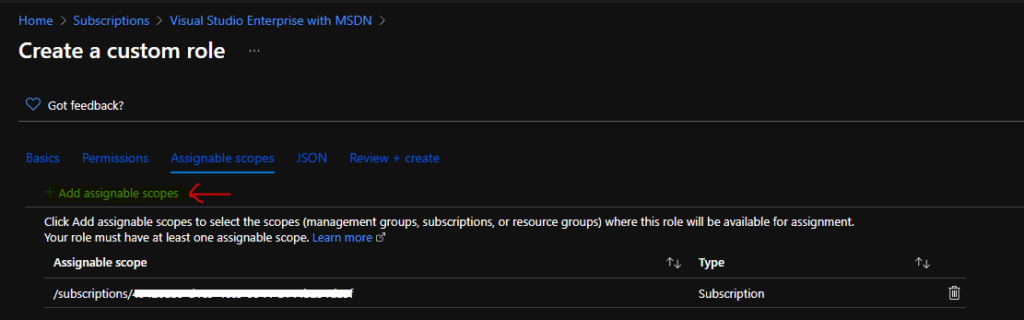
Assign a Scope for Custom Azure RBAC Role
In this section, you will have to add or assign a scope to the custom Azure RBAC role so that this role will be visible inside that particular scope.
You can click on Add assignable scopes to select the scopes (management groups, subscriptions, or resource groups) where this role will be available for assignment.
I’m going to leave this at the subscription level. So this custom role can be used within this particular subscription. You can change the scope only to a resource group if you want the custom role available only in that resource group.
Wait for Some Minutes
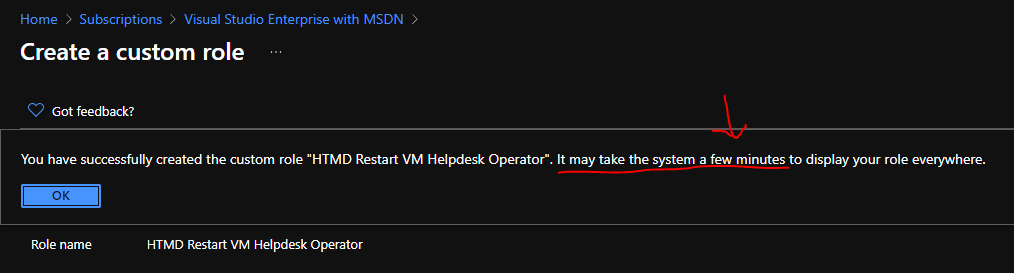
You will need to complete the creation of a custom role by clicking on the Next, Next, and Create buttons. The JASON file details for this custom role are given in the below section of the post.
NOTE! – It’s very important to understand that you will need to wait at least 5 minutes or so after successfully creating the Custom Azure RBAC role. Wait for some time before you start searching for the newly created custom role. Don’t create it again!
Assign Custom Azure RBAC Role
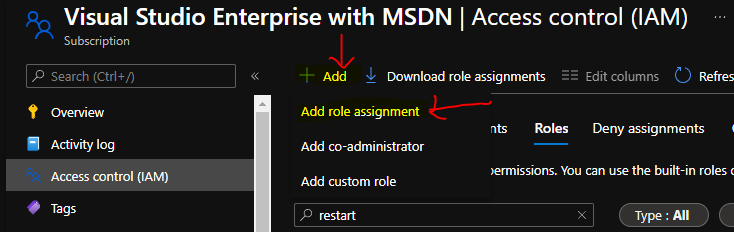
Now, it’s time to assign the newly created custom role to a user for testing or to an Azure AD user group. You will need to follow the steps mentioned below to complete the assignment process of the custom role.
You will need to click on +Add and select Add Role Assignment option to assign the custom role to a user or a group.
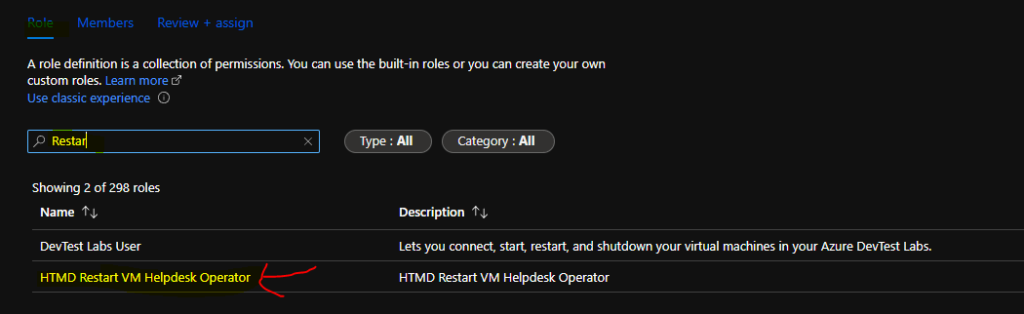
You will need to select the custom role that is created in the above section. You can search with the name that you choose in the above section. Click on the custom role and click on the Next button to continue.
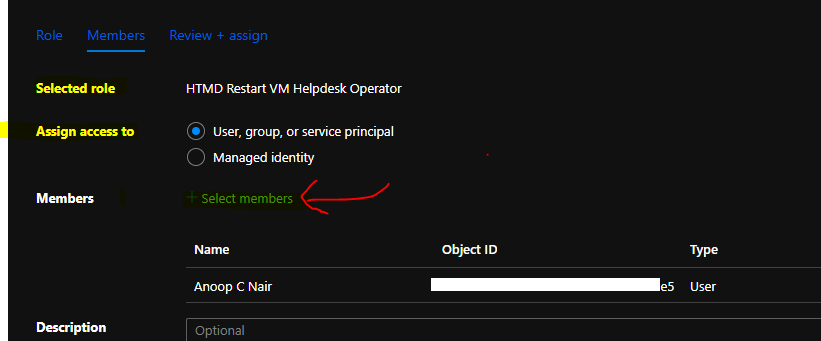
You will need to select the Helpdesk user or group that you want to assign this role. You can click on the + Select Members hyperlink option to add a user or an Azure AD user Group.
- Selected Role – HTMD Restart VM Helpdesk Operator
- Assign Access to – User, Group, or Service Principle
- Members – Anoop C nair
- Clcik on Review + Assign button to complete the role assignment.
JSON file to Create the Restart VM Helpdesk Role for AVD
You can create the custom Azure RBAC role with the following JSON file. You can try to download it from the Github repository. You will need to select the “Start from JSON” option from baseline permissions for the custom role creation using a JSON file.
{ "properties": { "roleName": "HTMD Restart VM Helpdesk Operator", "description": "HTMD Restart VM Helpdesk Operator", "assignableScopes": [ "/subscriptions/replace-with-d1c9-xxx-xxxx-subscription-ID" ], "permissions": [ { "actions": [ "Microsoft.Compute/virtualMachines/read", "Microsoft.Compute/virtualMachines/restart/action" ], "notActions": [], "dataActions": [], "notDataActions": [] } ] }}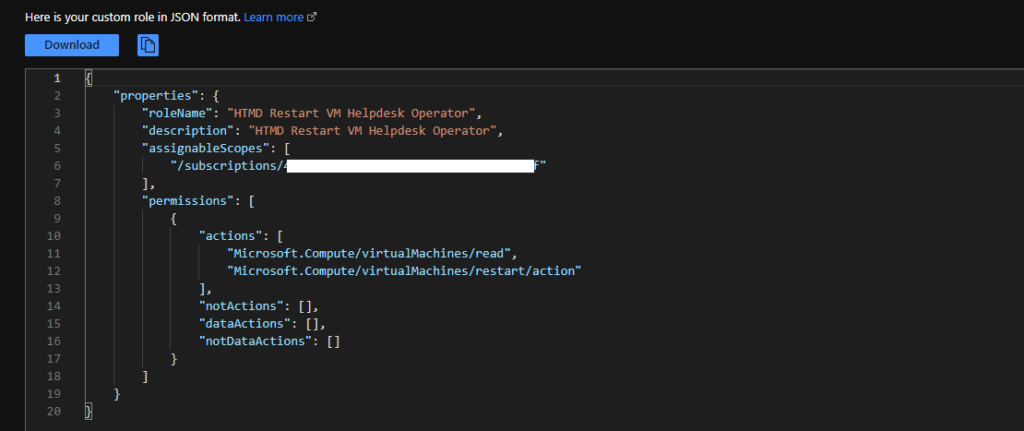
Result – Azure RBAC Custom Role to Restart VM
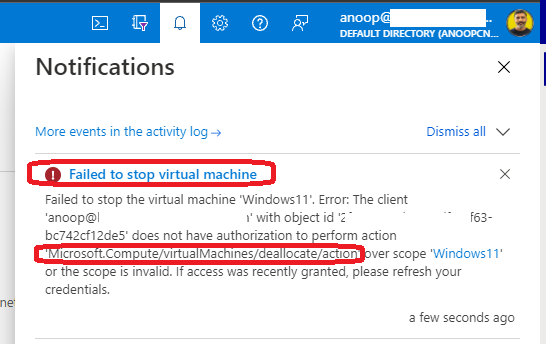
You will need to log in with the helpdesk user assigned to the HTMD Restart VM Helpdesk Operator role. Once logged in to the Azure portal, the restart option will be available for the user. The Stop VM action will also be available, but it won’t work because of permission issues.
The stop VM action won’t work as expected – Failed to Stop Virtual Machine.
Author
Anoop is Microsoft MVP! He is a Solution Architect in enterprise client management with over 17 years of experience (calculation done in 2018). He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc…..…
