Let’s check how to add an Azure virtual desktop session host to Azure AD. Microsoft released a public preview for the Azure AD join scenario on July 14, 2021. I already mentioned Azure Virtual Desktop Azure AD Join Support with Intune Management in the previous post. In the following posts, we will learn how to RDP Azure AD Joined VMs in Azure.
Check out the requirements for taking the RDP of an AAD Joined Windows 11 or 11 devices: 1. RDP Of Azure AD Joined Device MS-Organization-P2P-Access Certificate and 2. How To Take RDP Of Azure AD Joined Device. This does not apply to AVD Azure AD Joined scenarios.
In the previous post, I shared my AVD End-User Experience Journey with Intune Management. With MEM management and pure Azure AD join, you can manage and secure Azure Virtual Desktop session hosts. You don’t need to use the MDM group policy to enrol devices into Intune for the AAD join scenario.
If you are joining AVD session hosts to Azure AD, you don’t need connectivity to on-prem AD. Also, the AD DS requirement is not there if you use pure Azure AD Join for the AVD session hosts.
Microsoft released Windows 365 Cloud PC on July 14, 2021. The Cloud PC solution is also exciting for Windows personal desktops in the cloud.
Update: Microsoft announced the General Availability of Azure AD-joined VMs on September 15, 2021.
Table of Contents
Prerequisite to Add Azure Virtual Desktop Session Host to Azure AD Join Guide AVD
The following are the prerequisites to join AVD session hosts to Azure AD. Make sure you have covered the license and other AVD prerequisites.
Host pools should only contain VMs of the same domain join type. AD-joined VMs should only be with other AD VMs and vice versa. The minimum supported versions of Windows 10 are 2004 or later.
Default Users/Non-Admin Users on the virtual machine should be part of Virtual Machine User Login: Users with this role can log in to an Azure virtual machine with regular user privileges.
Admin User on virtual desktop should be part of Virtual Machine Administrator Login: Users with this role assigned can log in to an Azure virtual machine with administrator privileges.
Custom RDP setting in the host pool “targetisaadjoined:i:1” to connect Remote Desktops from non-Widnows end-user devices.
- Azure Virtual Desktop (classic) doesn’t support Azure AD-joined VMs.
- Azure AD-joined VMs don’t currently support external identities, such as Azure AD Business-to-Business (B2B) and Azure AD Business-to-Consumer (B2C).
- Azure AD-joined VMs can only access Azure Files file shares for synced users using Azure AD Kerberos.
- The Windows Store client doesn’t currently support Azure AD-joined VMs.
- New Azure Virtual Desktop App in the Microsoft Store Winget and Intune
- New Azure Virtual Desktop Client Microsoft Store App
- Download Azure Virtual Desktop eBooks
- Azure Virtual Desktop End-User Experience Journey with Intune Management
Add Azure Virtual Desktop Session Host to Azure AD
Azure AD join allows you to automatically enrol the VM with Intune to easily manage Windows 10 and Windows 10 multi-session VMs. You can use the option to add Azure Virtual Desktop Session Host to Azure AD.
NOTE: The Azure AD join is the modern method of managing devices with Intune auto-enrollment. The Azure AD join scenario doesn’t require direct connectivity to the on-prem Active Directory.
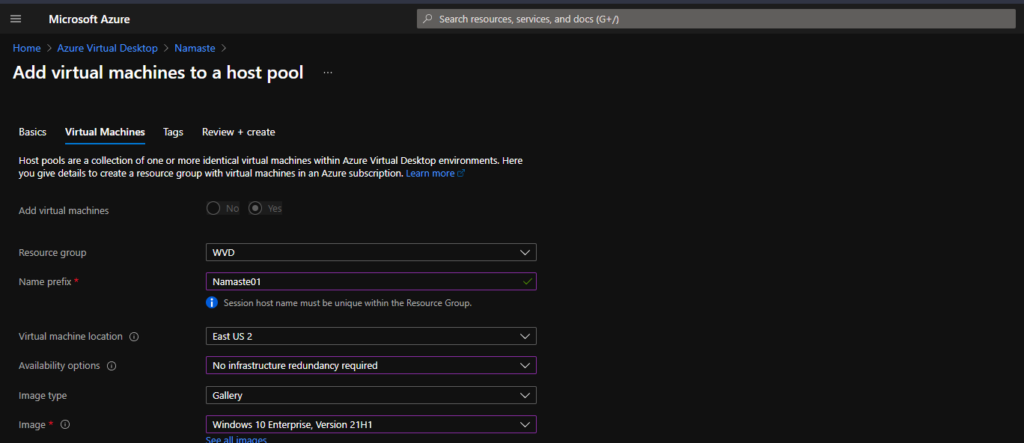
You can add VMs to Azure AD by selecting the add virtual machines to an existing host pool wizard option from the drop-down menu.
- Domain Join – Select which directory you want to join – Azure Active Directory.
- Enroll VM with Intune -> Yes.
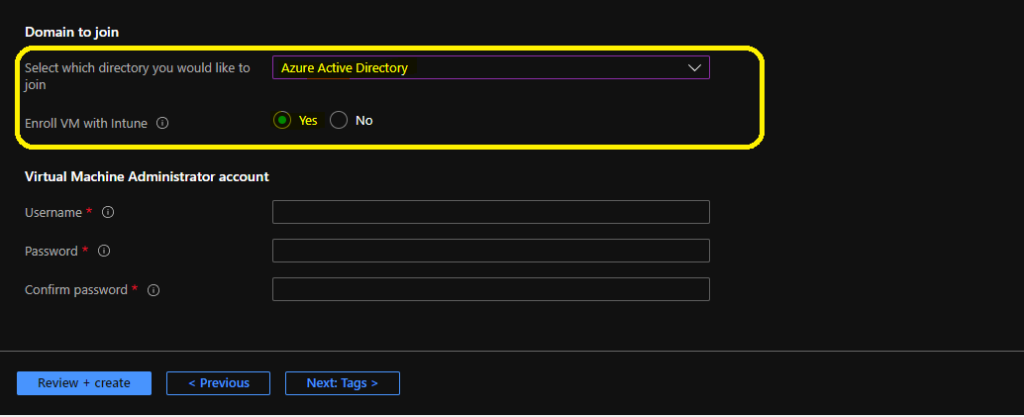
Enter the Virtual machine administrator account – Enter the local user name and password for Azure AD joined session hosts.
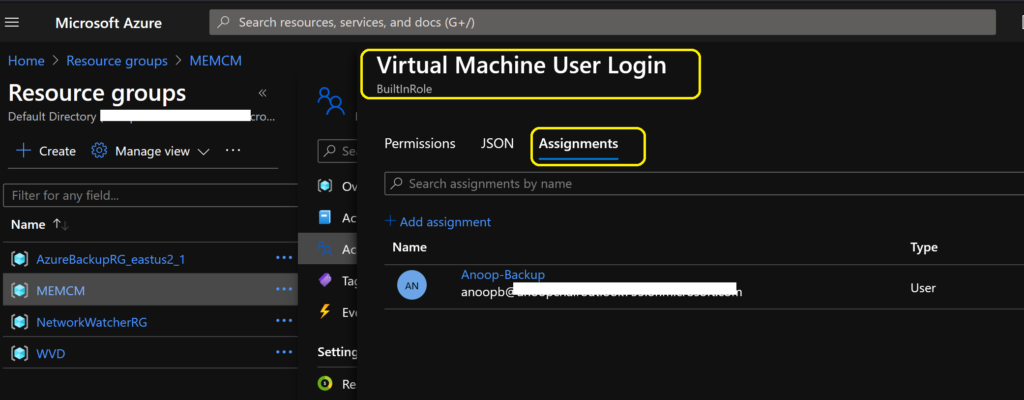
RBAC Roles Required for AVD Azure AD Join
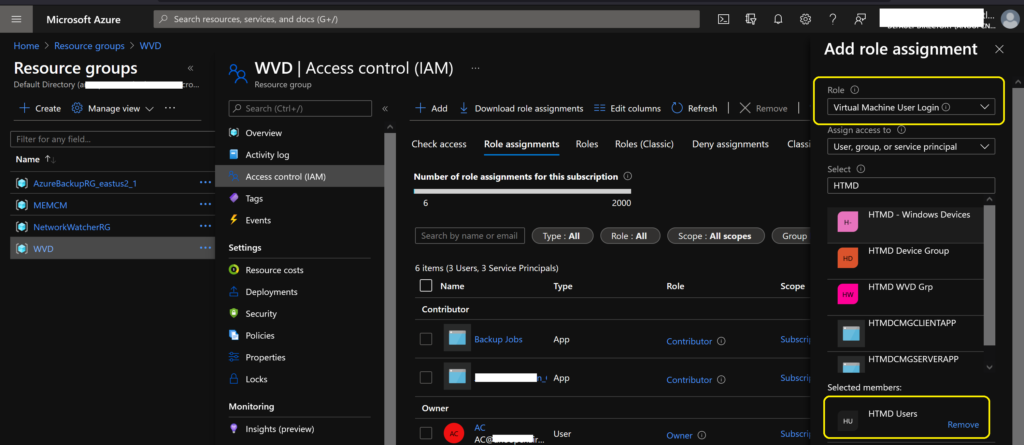
As I mentioned in the prerequisites section, you must add an Azure AD user group to give them login access to Azure AD joined VMs.
- Navigate to Resource Groups and select the resource group you used to build Azure AD joined session hosts.
- Click on Access Control (IAM).
- Click the +Add button to add role assignment.
- Select the Role “Virtual Machine User Login“.
- Select the Azure AD group where the login (AVD end-users) users are members of.
NOTE! – Repeat the above tasks to add Admin users access to AVD session host VMs using the built-in role called Virtual Machine Administrator Login.
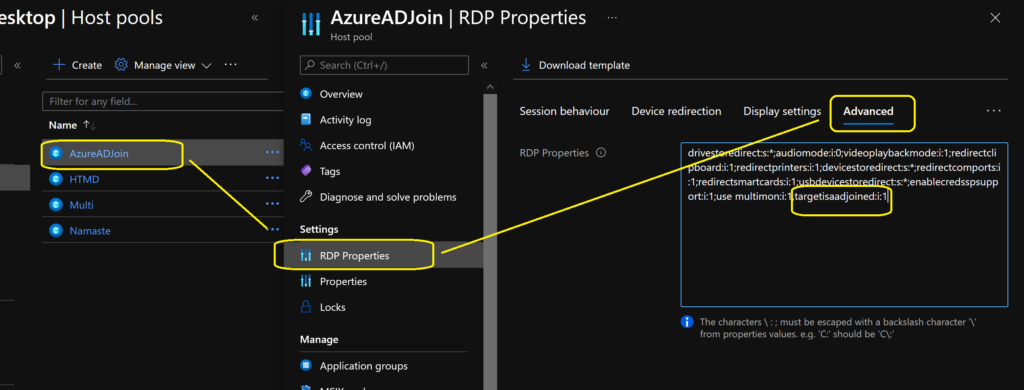
Special RD Settings for AVD Azure AD Joined
To access Azure AD-joined VMs using the web, Android, macOS, iOS, and Microsoft Store, you will need an advanced RD setting for Azure AD-joined AVD session hosts.
You can read the details about WVD New RDP Settings Options. Also, using the How to Download WVD Session Desktop RDP File post, you can check whether RDP settings are flowing down to the base clients.
- Navigate to Host Pool -> Select the Hostpool where Azure AD joined VMs are located.
- Click on RDP properties.
- Click on the… button and select the Advanced button.
- Enter targetisaadjoined:i:1 as the last custom property and click Save.
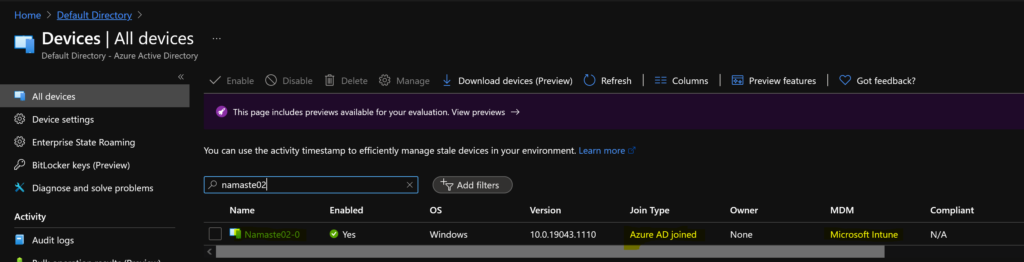
Results – AVD Azure AD Joined
You can check the results of AVD Azure AD joined session hosts from various places.
- Azure AD Devices node.
- Intune MEM Portal.
- Windows 10 or Windows 11 client.
What is the issue with Azure AD Joined VMs?
I can’t log in to Azure AD to join session hosts. I got the following error whenever I tried to connect to the VM from the RD client.
- The following error 0x9735 translates to SSL_ERR_INVALID_UPN_NAME, which originates from SEC_E_INVALID_UPN_NAME.
- This means “You can’t sign in with a user ID in this format. Try using your email address instead.”
- I’m logging in as a session host with anoop@abc.onmicrosoft.com ID. I don’t know whether this is supported or not,
NOTE! – Further troubleshooting in a later blog post. In the comments section, you can comment on your experience with Azure AD-joined VMs.
As promised, here is the blog post FIX: AVD Azure AD Joined VM Login Issue with Error Code 0x9735.
Error code: 0x9735
Extended error code: 0x0
Activity ID: {7432516d-23a3-483f-b99e-c3c321520000}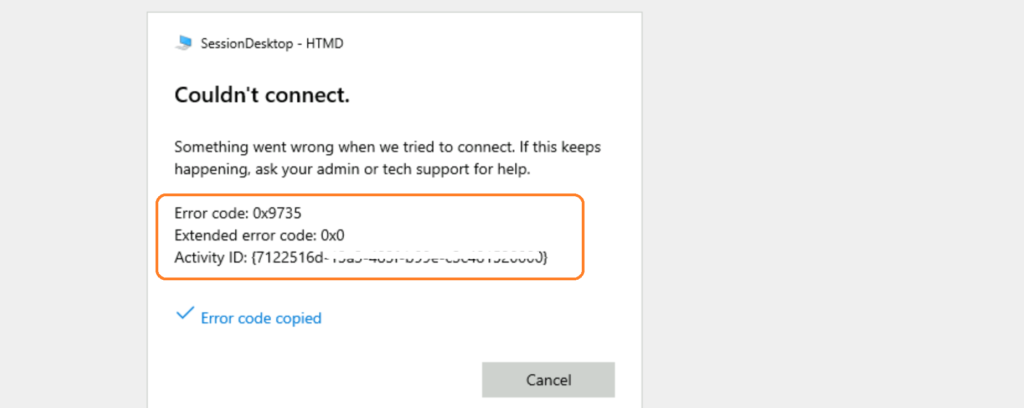
Resources
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.

hi
your guide is great.
i reeached to a point where im getting this 0x9735 error every time when trying to connect using Remote Desktop app on client device.
All prereqs are met. Device is AADJ to the same tenant, managed by intune and this error still occours.
The only way im able to login to my AADJ AVD hostpool is via RD web client. Theres no issues there.
Any clues ???
Are you using a cloud account that ends with .onmicrosoft.com or a standard account like anoop@htmd.com to login?
You need to have your host pool in the validation environment as well: https://docs.microsoft.com/en-us/azure/virtual-desktop/deploy-azure-ad-joined-vm
During public preview, you must configure your host pool to be in the validation environment.
Thank you for the tip!
Hi Anoop,
Is there a way to automate to assignment a user to AVD pool and to add Virtual Machine User Login?
how to mange that in a big company ?
Hi David – You can use Azure AD groups for automatic assignment as shown in the post. A VM from that hostpool will automatically get assigned whenever the user logs in.
Hi Anoop
The automatic assignment i setup for the App group, but how to add user to Virtual Machine User Login?
sorry i dont see in in the article
my goal is to automate all so i dont have add user to the Host pool and Virtual Machine User Login
Here you go https://www.anoopcnair.com/avd-admin-experience-create-new-host-pool/
Check for this sentence “Search for Azure AD Users or Groups to assign Desktop Application Group created through the Hostpool.” in the post
but there i can add a user to the Application group but still i need to add the user to the VM so can can login
sorrr or i dont understate something
The application group is assigned to Host Pool, and the host pool has VMs. Hence the users in the application group will automatically get VM assignment if there is enough capacity for VMs in the hostpool.
How can I route specific user to login to specific session hosts from host pool.
I already have existing VM which aren’t Azure AD joined, how do I add them to the Azure Active Directory and enrolll in Intune.
Lastly I see two VDI with AD joined under devices, how can I enroll them to Intune? Who do I give the license to?
Hi Anoop, I also have the same question, I have 2 hosts (Win11 mutisession) VMs that I want to join to MS Entra/AAD. How can I achieve that as I did not select Intune enrollment when onboarding them?.
Thanks