Let’s check how to FIX KB5020276 Domain Join Hardening Changes CVE-2022-38042. You can use the SCCM task sequence to fix this Active Directory Domain Services Elevation of Privilege Vulnerability.
In this post, we will discuss the changes introduced by CVE-2022-38042 in the October 11, 2022, cumulative update packages across all supported operating systems. These changes are enabled and secure by default.
Updated on 8th Nov 2022: After installing the hardening explained in KB5020276, the Domain join processes may fail with the error “0xaac (2732).” Domain join operations might intentionally fail with error “0xaac (2732): NERR_AccountReuseBlockedByPolicy” and text “An account with the same name exists in Active Directory. Re-using the account was blocked by security policy.”
After October patches are applied to a client, you cannot join the domain to an existing computer object if you are either not a Domain Admin or the owner of the AD object. The scenario of re-images where a service account is doing the domain join and someone used a personal account to pre-stage the AD object completely breaks.
Microsoft made changes to fix KB5020276 Domain Join Hardening Changes vulnerability CVE-2022-38042 with October 11, 2022, cumulative update packages for all supported operating systems.
- Windows Server 2008 Datacenter ESU
- Windows Server 2008 Standard ESU
- Windows Server 2008 Enterprise ESU
- Windows 7 Enterprise ESU
- Windows 7 Professional ESU
- Windows 7 Ultimate ESU
- Windows Server 2008 R2 Enterprise ESU
- Windows Server 2008 R2 Standard ESU
- Windows Server 2008 R2 Datacenter ESU
- Windows Embedded Standard 7 ESU
- Windows Embedded POSReady 7 ESU
- Windows Server 2012
- Windows Embedded 8 Standard
- Windows 8.1 Windows RT 8.1
- Windows Server 2012 R2
- Windows Embedded 8.1 Industry Enterprise
- Windows Embedded 8.1 Industry Pro
- Windows 10, version 1607, all editions
- Windows Server 2016, all editions
- Windows 10 Enterprise 2019 LTSC
- Windows 10 IoT Enterprise 2019 LTSC
- Windows 10 IoT Core 2019 LTSC
- Windows Server 2019
- Windows 10 Enterprise Multi-Session, version 20H2
- Windows 10 Enterprise and Education, version 20H2
- Windows 10 IoT Enterprise, version 20H2
- Windows 10 on Surface Hub
- Windows 10, version 21H1, all editions
- Windows 10, version 21H2, all editions
- Windows 11 version 21H2, all editions
- Windows 11 version 22H2, all editions
- Windows Server 2022
- Install SCCM Client on Workgroup Non-Domain Joined Windows 11 PC
- FIX SCCM OSD Machine Domain Join Issue ldap_add_s failed: 0x35 0x216d
Legacy behavior before you install October 11, 2022 and later updates – KB5020276 Domain Join Hardening
The client queries Active Directory for an existing account that has the same name. This query occurs during domain join and computer account provisioning. If such an account exists, the client will automatically attempt to reuse it.
Note – The reuse attempt will fail if the user attempting the domain join operation does not have the appropriate write permissions. However, if the user has enough permissions the domain join will succeed.
There are two scenarios for domain joining with respective default behaviors and flags as follows:
- Domain Join (NetJoinDomain)
- Defaults to account reuse (unless NETSETUP_NO_ACCT_REUSE flag is specified)
- Account provisioning (NetProvisionComputerAccountNetCreateProvisioningPackage).
- Defaults to NO reuse (unless NETSETUP_PROVISION_REUSE_ACCOUNT is specified.)
New behavior after you install October 11, 2022 and later updates – KB5020276 Domain Join Hardening
During domain join, the client will perform additional security checks before attempting to reuse an existing computer account.
- Account reuse attempts will be permitted if the user attempting the operation is the creator of the existing account.
- Account reuse attempts will be permitted if the account was created by a member of domain administrators.
After installing the October 11, 2022 or later Windows cumulative updates, domain join might fail with the following error:
Error 0xaac (2732): NERR_AccountReuseBlockedByPolicy: “An account with the same name exists in Active Directory. Re-using the account was blocked by security policy.”
There is a new registry entry NetJoinLegacyAccountReuse, and the log C:\Windows\Debug\netsetup.log provides an indication that Active Directory join has been blocked on the account by the security policy.
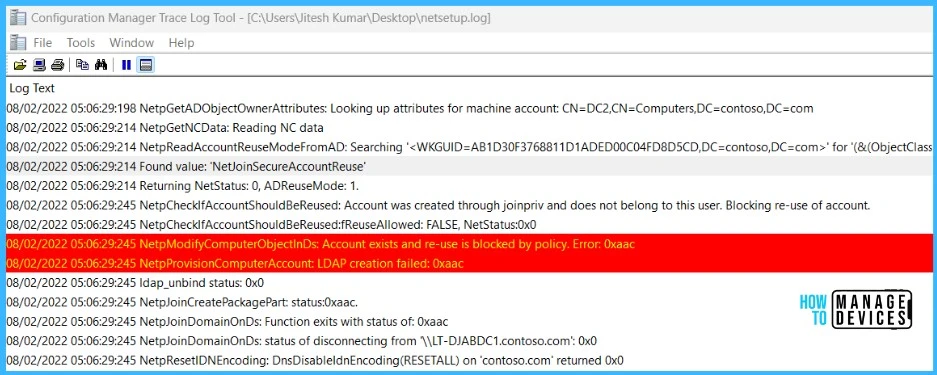
NetpGetComputerObjectDn: Crack results: (Account already exists) DN = CN=DC2,CN=Computers,DC=contoso,DC=com
NetpGetADObjectOwnerAttributes: Looking up attributes for machine account: CN=DC2,CN=Computers,DC=contoso,DC=com
NetpGetNCData: Reading NC data
NetpReadAccountReuseModeFromAD: Searching '<WKGUID=AB1D30F3768811D1ADED00C04FD8D5CD,DC=contoso,DC=com>' for '(&(ObjectClass=ServiceConnectionPoint)(KeyWords=NetJoin*))'.
Found value: 'NetJoinSecureAccountReuse'
Returning NetStatus: 0, ADReuseMode: 1.
NetpCheckIfAccountShouldBeReused: Account was created through joinpriv and does not belong to this user. Blocking re-use of account.
NetpCheckIfAccountShouldBeReused:fReuseAllowed: FALSE, NetStatus:0x0
NetpModifyComputerObjectInDs: Account exists and re-use is blocked by policy. Error: 0xaac
NetpProvisionComputerAccount: LDAP creation failed: 0xaac
ldap_unbind status: 0x0
NetpJoinCreatePackagePart: status:0xaac.
NetpJoinDomainOnDs: Function exits with status of: 0xaac
NetpJoinDomainOnDs: status of disconnecting from '\\LT-DJABDC1.contoso.com': 0x0
NetpResetIDNEncoding: DnsDisableIdnEncoding(RESETALL) on 'contoso.com' returned 0x0
NetpJoinDomainOnDs: NetpResetIDNEncoding on 'contoso.com': 0x0
NetpDoDomainJoin: status: 0xaac- Easily Find SCCM Task Sequences Reference Application
- How to Add Run Command Line Step to SCCM Task Sequence
Possible Solutions to FIX KB5020276 Domain Join Hardening Changes | CVE-2022-38042
You can use event logs and c:\windows\debug\netsetup.log to understand the failure and take the necessary steps to resolve the issue. Here are the possible steps you can follow to fix KB5020276 Domain Join Hardening Changes.
- Rename the machine and join using a different account name
- If the existing account is stale (unused), delete it before re-attempting to join the domain.
| Event log | Event ID | Event Type | Event Text |
|---|---|---|---|
| SYSTEM | 4100 | Informational | “During domain join, the domain controller contacted found an existing computer account in Active Directory with the same name.%nAn attempt to re-use this account was permitted. %n%nDomain controller searched: %1%nExisting computer account DN: %2%n%nSee https://go.microsoft.com/fwlink/?linkid=2202145 for more information. |
| SYSTEM | 4101 | Error | “During domain join, the domain controller contacted found an existing computer account in Active Directory with the same name.%nAn attempt to re-use this account was prevented for security reasons.%n%nDomain controller searched: %1%nExisting computer account DN: %2%nThe error code was %3.%n%nSee https://go.microsoft.com/fwlink/?linkid=2202145 for more information.” |
If you are using SCCM Task Sequence for imaging, you can apply the possible solutions in the task sequence step for automation in client machines. If you using the OS Image, that doesn’t include the latest 2022-10 CU or October Updated Image, You can skip this step.
Here you need to adjust the task sequence steps to apply registry changes to fix KB5020276 Domain Join hardening changes during the task sequence execution. The step to create registry value should be added before running the Domain Join step.
Create Registry value – FIX KB5020276 Domain Join Hardening Changes using SCCM Task Sequence
If you set the Dword value NetJoinLegacyAccountReuse to 1, The domain join with the old user accounts should work.
Important⚠️- The workaround for the registry is not officially supported by Microsoft. You can expect some fixes to come out.
New-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Control\Lsa\ -Name NetJoinLegacyAccountReuse -PropertyType DWORD -Value 1
Note – The computer needs to be restarted in order to complete the operation.
- Join Domain or Workgroup
- Remove Registry value
Remove-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Control\Lsa\ -Name NetJoinLegacyAccountReuse
Let’s check how to add Run PowerShell Script Step to SCCM Task Sequence. The PowerShell script added to the SCCM task sequence must be installed silently when you decide to add it during the OS deployment.
- In the Configuration Manager console, go to the Software Library workspace, expand Operating Systems, and then select the Task Sequences node.
- In the Task Sequence list, select the task sequence that you want to edit. Select Edit to modify.
- To add this step in the task sequence editor, select Add, select General and select Run PowerShell Script.
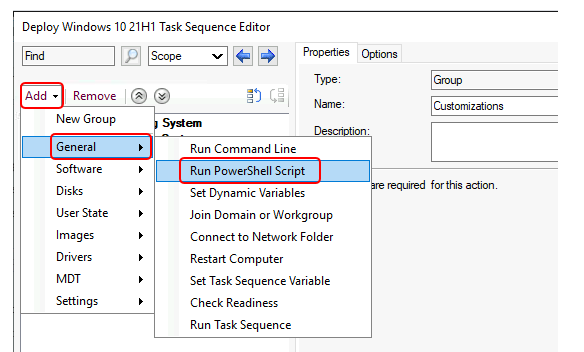
In this step, you can enter the PowerShell code directly. This feature lets you run PowerShell commands during a task sequence without distributing a package. If needed, you can directly do the changes and perform testing without looking into the package creation process and distribution to fix KB5020276 Domain Join Hardening Changes.
FIX Domain join processes may fail with error 0xaac (2732)
Microsoft has not provided any FIX for Domain join processes that may fail with the error 0xaac (2732) issue yet. This issue originates with the October 2022 security updates (KB5020276) as explained in the above section.
These hardening changes are enabled by default for domain join scenarios and caused error 0xaac (2732). You can fix the issue by disabling the hardening policies. The following are the affected scenarios:
- Domain join or re-imaging operations where a computer account was created or pre-staged by a different identity than the identity used to join or re-join the computer to the domain.
Resource – Windows 10, version 22H2 | Microsoft Learn
Thank you sir as always!
This is going to cause a lot of headaches.
will not work in winpe
After applying the OS wim the Task Sequence :
Run Command Line – Load System Hive:
Reg load HKLM\ImportedHive “C:\Windows\System32\config\SYSTEM”
Run Command Line – Adding NetJoinLegacyAccountReuse Registry:
Reg add HKLM\ImportedHive\ControlSet001\Control\Lsa /v NetJoinLegacyAccountReuse /t REG_DWORD /d 1 /f
Run Command Line – Unload System Hive:
Reg unload HKLM\ImportedHive
Add to Task Sequence where it boot into the OS:
Run Command Line – Removing NetJoinLegacyAccountReuse Registry:
Reg add HKLM\ImportedHive\ControlSet001\Control\Lsa /v NetJoinLegacyAccountReuse /t REG_DWORD /d 1 /f
[Corrected]
After applying the OS wim the Task Sequence :
Run Command Line – Load System Hive:
Reg load HKLM\ImportedHive “C:\Windows\System32\config\SYSTEM”
Run Command Line – Adding NetJoinLegacyAccountReuse Registry:
Reg add HKLM\ImportedHive\ControlSet001\Control\Lsa /v NetJoinLegacyAccountReuse /t REG_DWORD /d 1 /f
Run Command Line – Unload System Hive:
Reg unload HKLM\ImportedHive
Add to Task Sequence where it boot into the OS:
Run Command Line – Removing NetJoinLegacyAccountReuse Registry:
powershell.exe -executionpolicy bypass -noprofile -NonInteractive -command “Remove-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Control\Lsa\ -Name NetJoinLegacyAccountReuse”
Worked perfectly. Thanks!!
my task sequence fails at the first step loading the importedhives.
Tim, thanks for posting those details!!!
Dante, you may have the same situation as me. The OS is not installed to “C:” so the “Reg LOAD” command fails because it’s trying to load the SYSTEM hive from the C: drive.
My rollout is slightly different. While in WinPE my “Install OS” task could be installing the OS to a different drive letter than “C:”. Sometimes its E: or F:. The “Install OS” tasks uses the OSDISK variable to target which drive will receive the OS install. For the “Load System Hive” task, I can use the OSDISK variable in the “Reg LOAD” command so that the proper drive is targeted.
I put the next two tasks (“Adding registry” and “Unload System Hive”) immediately after the “Reg LOAD” task.
These 3 additional tasks are in the Install phase section of your TS.
I put the last additional task “Removing registry” in my State Restore phase right after the “Recover from Domain” task.
Thanks again Tim!!!
Hope this helps.
I put the “Load System Hive” task immediately after the “Install OS” task.
And changed the Reg command to use the OSDISK variable for the drive where the SYSTEM hive is located.
Run Command Line – Load System Hive:
Reg load HKLM\ImportedHive “%OSDISK%\Windows\System32\config\SYSTEM”
I will give this Run Command Line – Load System Hive:Reg load HKLM\ImportedHive “%OSDISK%\Windows\System32\config\SYSTEM” a try. I want forgot to mention was when i press F8 to open command prompt so that i can test manually I can run those commands in the c drive.
Same problem here… I can execute all of the commands from the F8 console. But I can’t load the registry hive from the task sequence. Tested with c:\ and %OSDISK%
Any ideas?
@Sven I bet you copy/pasted commands? If so pay attention to quotes in “C:\Windows\System32\config\SYSTEM”
Hi again,
@Pawel: you had the right idea. The workaround runs perfect now
But – once again Microsoft changed the game. They added new policies for a special group in AD to allow Domain Rejoin again. Regarding the change log and notes in KB50200276 MS said, that they will remove the possibility for the legacy mode later this year.
We added the new policies to our domain, we put the domjoin account into the new group, removed the workaround described here and now the domjoin fails again.
Has anyone tried the “new way” succesful?
Sven
Apparently adding the Domain Join account to DC GPO is not enough. The same account have to be the Computer object owner to be able to re-use it.
So far I have no working way to fix this!
@Seven
But – once again Microsoft changed the game. They added new policies for a special group in AD to allow Domain Rejoin again. Regarding the change log and notes in KB50200276 MS said, that they will remove the possibility for the legacy mode later this year.
We added the new policies to our domain, we put the domjoin account into the new group, removed the workaround described here and now the domjoin fails again.
Has anyone tried the “new way” succesful?
have you found any new way to fix this part. We are working on windows 10 22h2 and facing issue for domain join.
Hi!
We use step: ‘Apply network settings’ to join computer to domain – we have a special account to adding computer to domain and of course the step does not work now. I understand that account added to GPO “bypass” must be a owner/creator of computer account in domain? OK, but what about accounts created by IT Support – they have permission to creat and add computer to domain – we cannot rejoin these accounts using our special account during TS. Now everything works fine because we added ‘bypass’ in register but what about time when MS will remove this register bypass?
@Anmol Ratan
Have you fixed the domain join issue? Change back to use the workaround?
Hi,
NetJoinLegacyAccountReuse setting will be removed on August 13, 2024, and what else can we do that?
I tried this fix, and it worked for *Most* of my computers, but still failed on a handful. Turns out that some of my computers had the property ms-ds-creatorSID set. These computers were added by a regular user, and hence got this key added.
TLDR – domain join will FAIL if you have ms-ds-creatorSID set, and the SID doesn’t match your domain join account (almost definitely will NOT match).
Deleting the ms-ds-creatorSID value is not easy as it is owned by the System and protected from deletion. I ended up finding this blog post (https://windowstechno.com/name-attribute-cannot-be-modified-owned-by-the-system/) – scroll to the bottom and he gives you instructions on how to delete system keys. Everything works now!