Let’s analyze the options to fix SCCM SCEP related issues. In this post, I will try to cover the knowledge acquired from the field to fix different problems with Windows Defender or Endpoint Protection clients (a.k.a, SCEP?).
Don’t get confused between SCEP and Windows Defender or Endpoint Protection clients. All these are the same from an IT Professional perspective. Microsoft changed the name of SCEP to Windows Defender or Endpoint Protection client.
In this post, I’m sharing information for Endpoint protection (defender) clients managed through Configuration Manager (a.k.a. SCCM). Let me know in the comments section if you have any queries or concerns.
Endpoint Protection manages antimalware policies and Windows Firewall security for client computers in our Configuration Manager hierarchy. This statement has been correct until now, and SCEP does what it’s supposed to do. However, some offenders refuse to get regular definition updates from SCCM, which makes our entire infrastructure vulnerable.
Table of Contents
Issue
We started this SCEP (Windows Defender or Endpoint Protection client) Remediation project early in 2019, and the task was simple. We just had to ensure all the clients in the infrastructure were running the latest definitions if they were connected to the network.
- Fix SCCM SCEP Related Client Side Issues Part 2 | ConfigMgr | Defender | Endpoint Protection
- Intune SCEP Certificate Workflow Analysis – Intune PKI Made Easy With Joy – Part 4
- [Fix] List of SCCM 1806 Known Issues – Documented
It sounds simple, but when we got our hands dirty and started seeing different errors, we saw limited articles and fixes to help us achieve the goal.
There is not much information available on google too apart from the generic MS article https://docs.microsoft.com/en-us/mem/configmgr/protect/deploy-use/troubleshoot-endpoint-client and the one from Henrik Hoe https://blog.ctglobalservices.com/configuration-manager-sccm/heh/configuration-items-and-baselines-example-scep-client-compliance/
So finally, we reached home to HTMD: https://forum.howtomanagedevices.com/ and tried.
Important – Read more about the question here: https://forum.howtomanagedevices.com/endpointmanager/configuration-manager/scep-definitions-not-updating-mecm-2002-adr/
If you are done reading the question, you noticed the HOD – Anoop C Nair. It was suggested that a case with MS be opened because of the complexity of the question.
Note: Most of the points explained in this blog are from several Microsoft forums, and the data was collected from those including several other websites like CTGLOBAL (Link already given in the block above), MANAGE ENGINE, COMPARITECH, BERKELEY, SEARCH SECURITY TECH, TRUSTRADIUS, and REDDIT.
Objectives:
So, without further delay, let’s deep dive from page 1.
- The evolution of malware
- Overview of System Center Endpoint Protection
- Management + Security
- Overview of the Endpoint Protection client
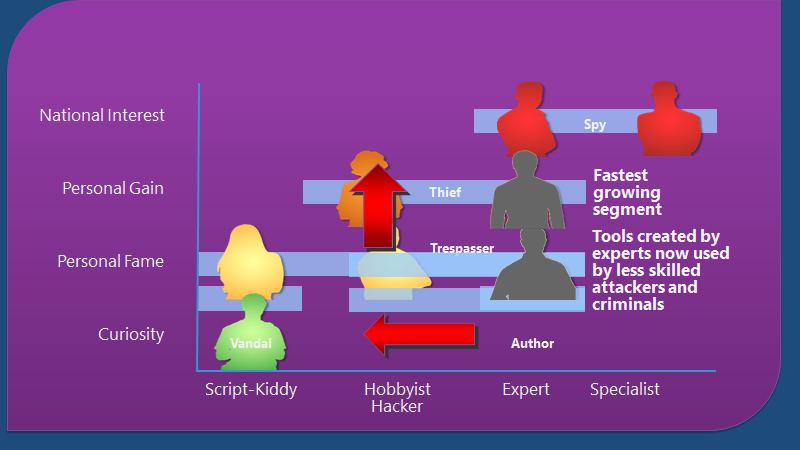
1. In 1991, 1000 known threats, in 2001 there were 60,000 2. Today there are millions, and it’s growing every day 3. Sophistication and production rates continue to evolve 4. Anybody can do it—full malware suites available online 5. Your stuff is worth money, and they want it!
The below figure shows the current reprehensible entities.
Fastest growing segment. Less-skilled attackers and criminals now use tools created by experts.
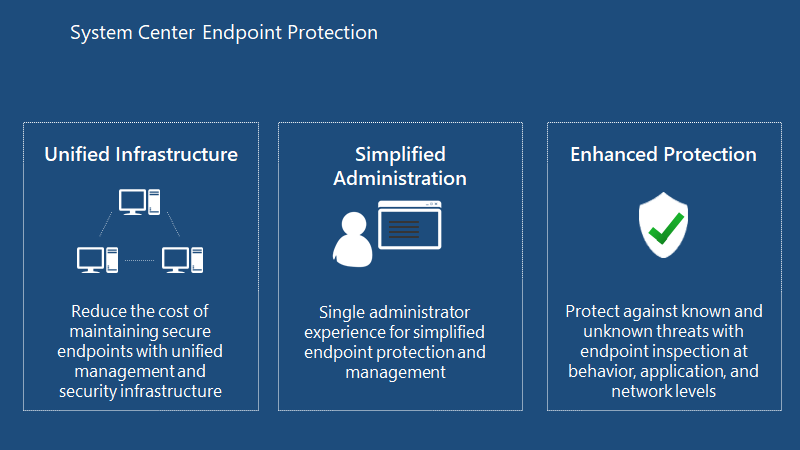
WHY SCEP?
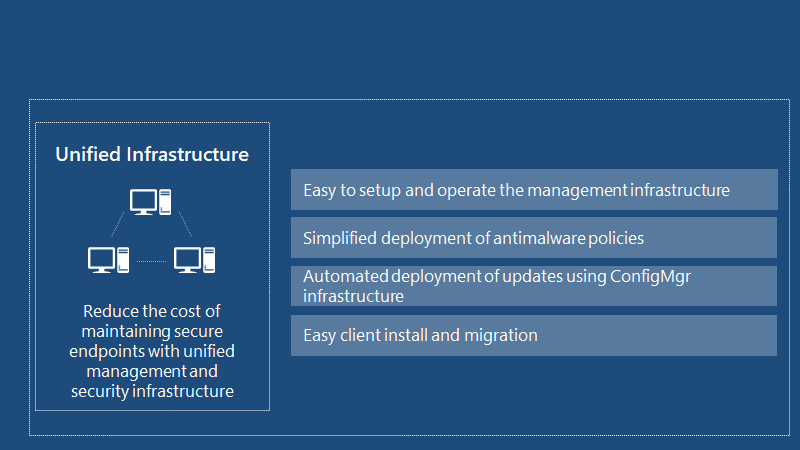
Reduce the cost of maintaining secure endpoints with unified management and security infrastructure. Single administrator experience for simplified endpoint protection and management. Protect against known and unknown threats with endpoint inspection at behaviour, application, and network levels.
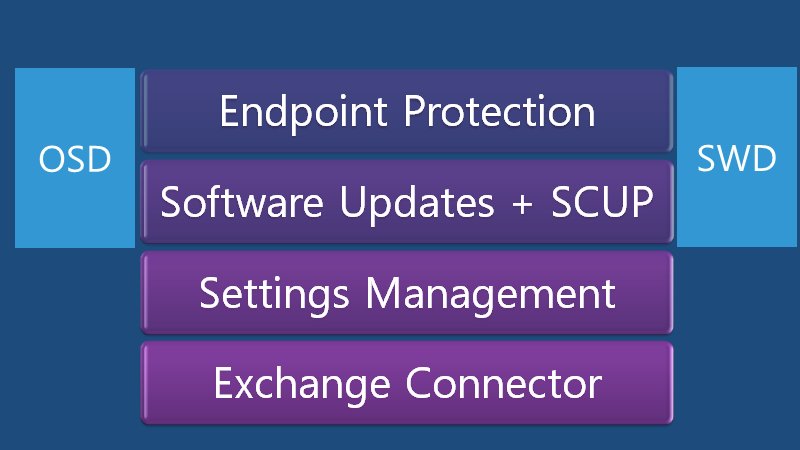
Mgmt + Security In Configuration Manager
Endpoint protection software updates +SCUP settings management exchange connector.
Infrastructure Changes from FEP 2010
Configuration manager site servers and management point.
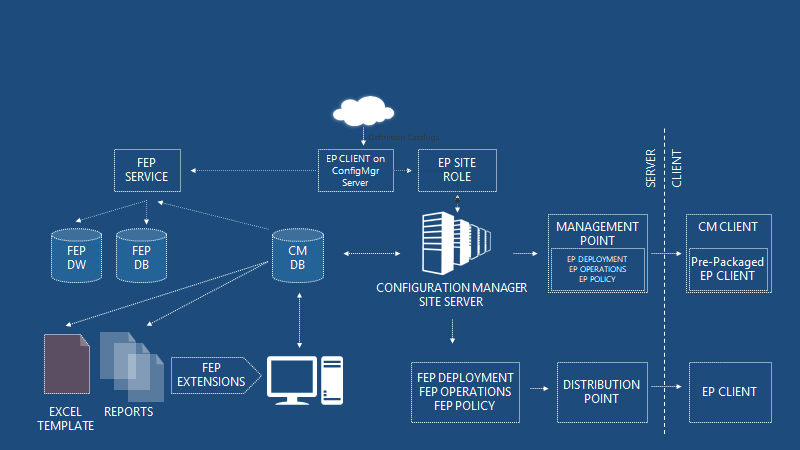
Simplified Deployment of AM Policies
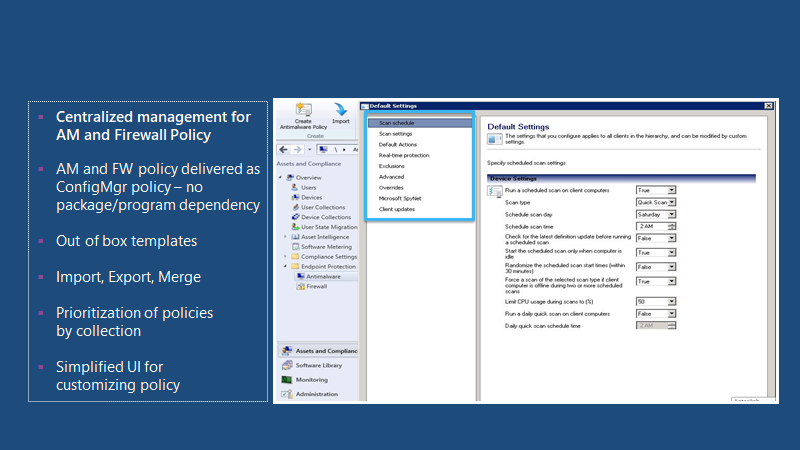
Centralized management for AM and firewall policy. AM and FW policy is delivered as ConfigMgr policy—no package/program dependency exists—out-of-the-box templates—import, export, Merge—prioritization of policies by collection, Simplified UI for customizing policy.
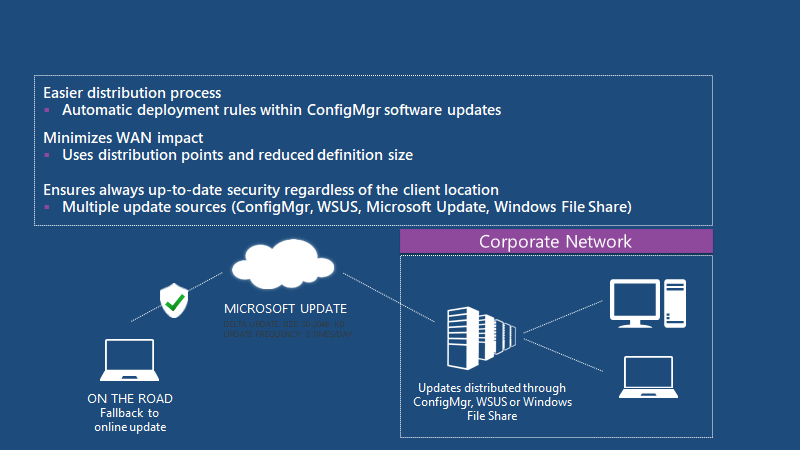
Signature Update Distribution
More straightforward distribution process and automatic deployment rules within ConfigMgr software updates. Minimizes WAN impact and user distribution points and reduces definition size. Ensures always up-to-date security regardless of the client’s location—multiple update sources (ConfigMgr, WSUS, Microsoft update, windows file share).
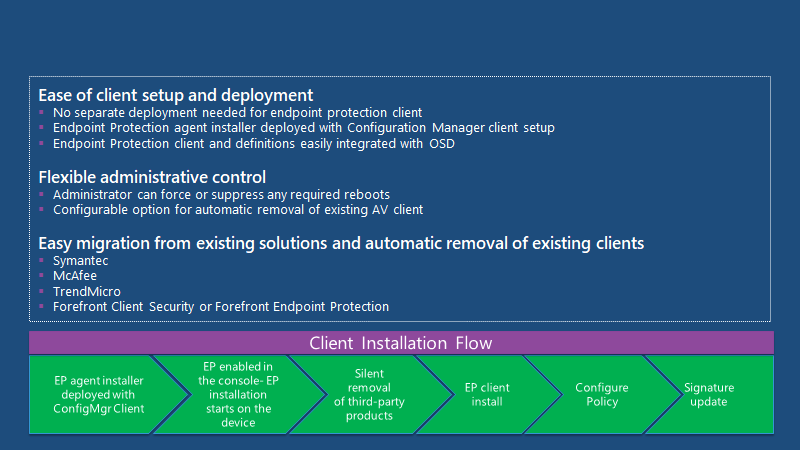
Simplified Client Setup
Ease of client setup and deployment.Flexible administrative control, easy migration from existing solutions and automatic removal of existing clients.
Client Deployment
System centre endpoint protection, single interface for client management and security. Improved alerting, clint to admin within 5 minutes, and reporting with real-time and user-centric data views.
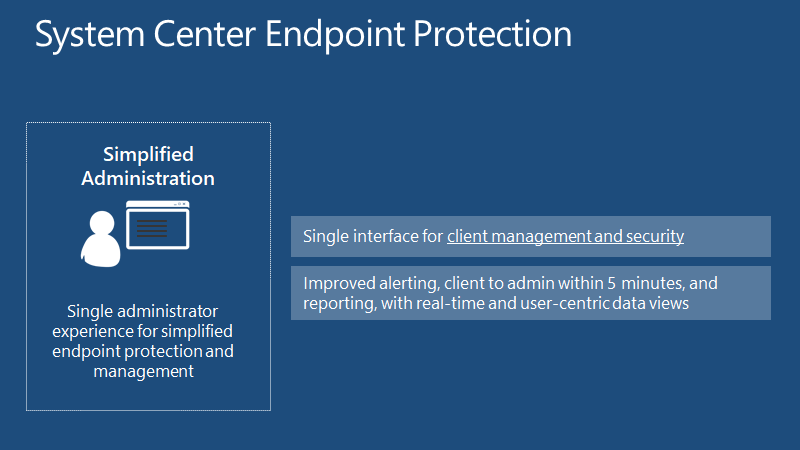
Single Interface For Management And Security
A single interface for client management and security. Quick identification and remediation of client security.Flexibility to separate security admin roles.
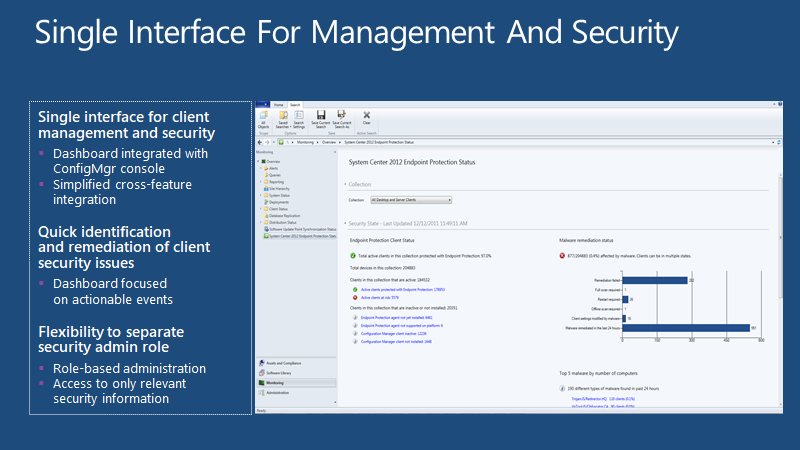
Monitoring Client Security
The console provides quick and event alerts, which can be notified in real-time using a high-speed data channel.
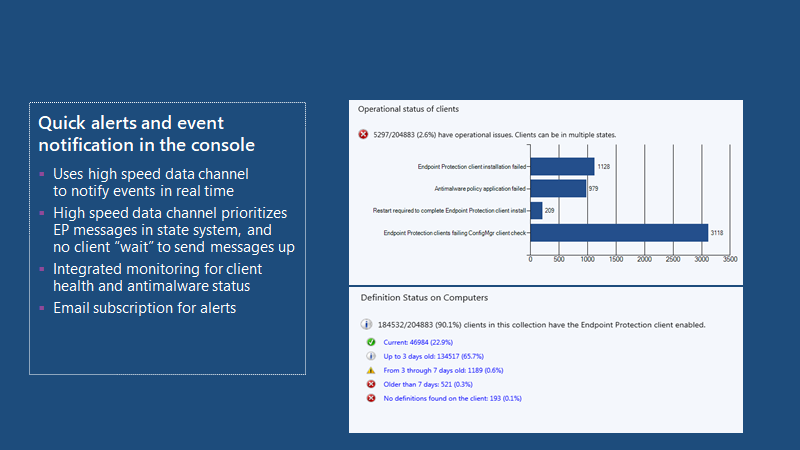
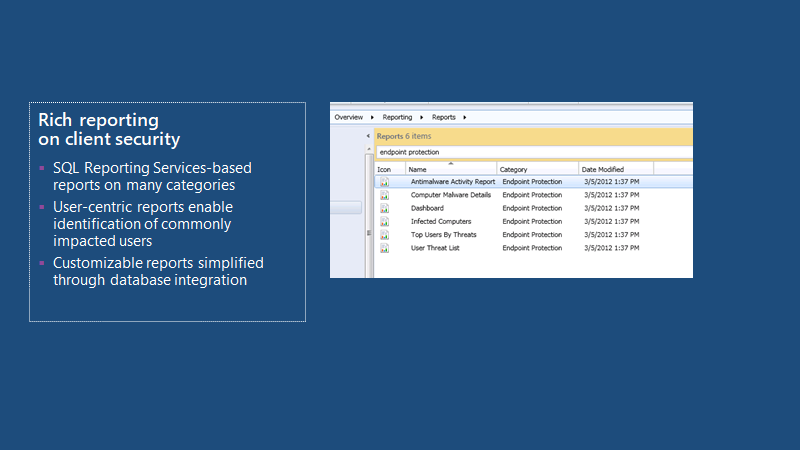
Rich Reporting And Analysis
Rich reporting on client security. SQL reporting services -based reports on many categories. Users-centric reports enable the identification of commonly impacted users. Customizable reports are simplified through database integration.
Management and Real-time Monitoring
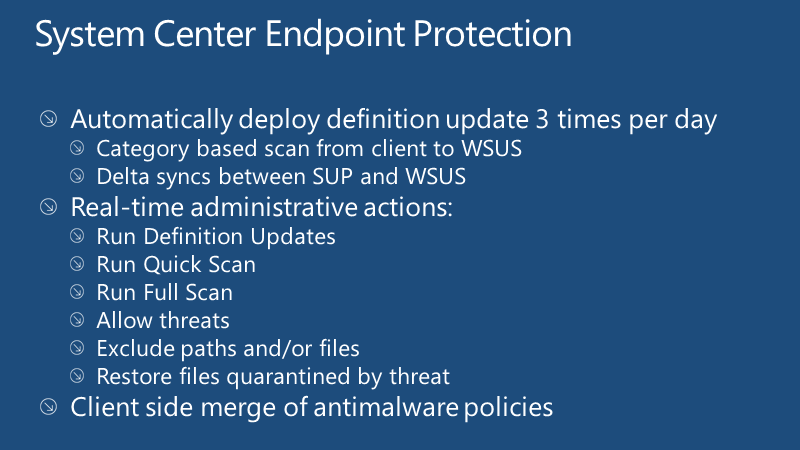
It automatically deploys definition updates three times per day. The category is based on the scan from the client to WSUS. Real-time administrative actions. Client-side merge of antimalware policies.
Real-time Administrative Actions
Select “Run Full Scan” on a collection in the administrative console. A task is created, and MP is told that a new urgent task has been requested.
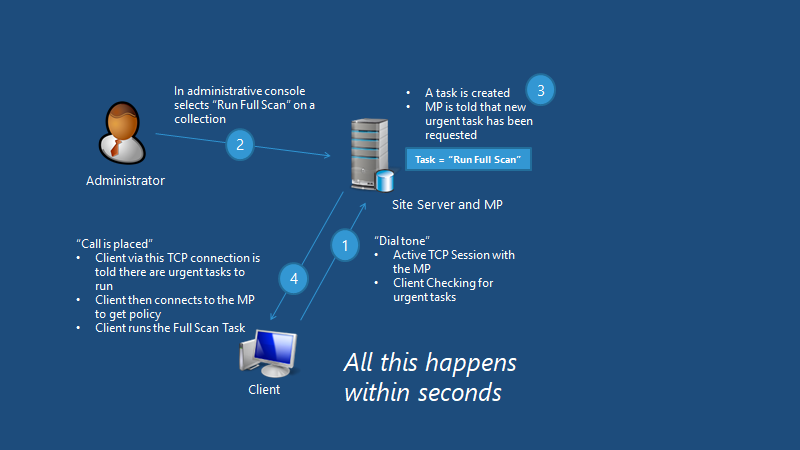
Real-time Administrative Actions in Endpoint Protection
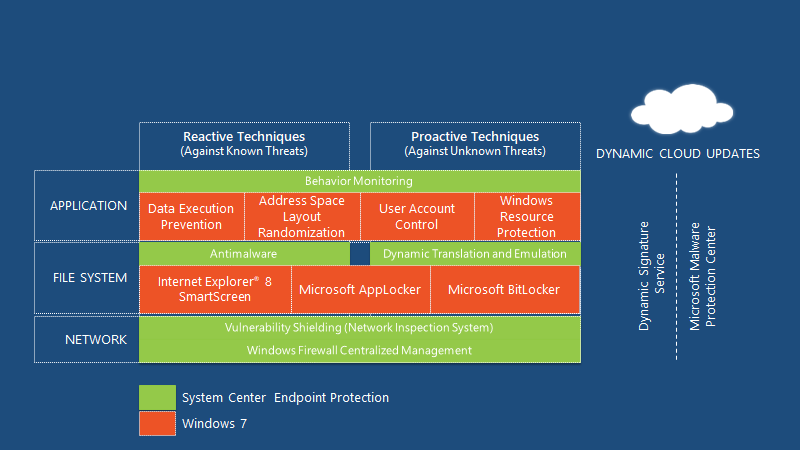
Protect against known and unknown threats with endpoint inspection of behaviour, application, and network levels. Comprehensive protection stack building on Windows security.

Comprehensive Protection Stack
Reactive techniques and protective techniques. Address space layout Randomization, user account control, and Windows resource protection.
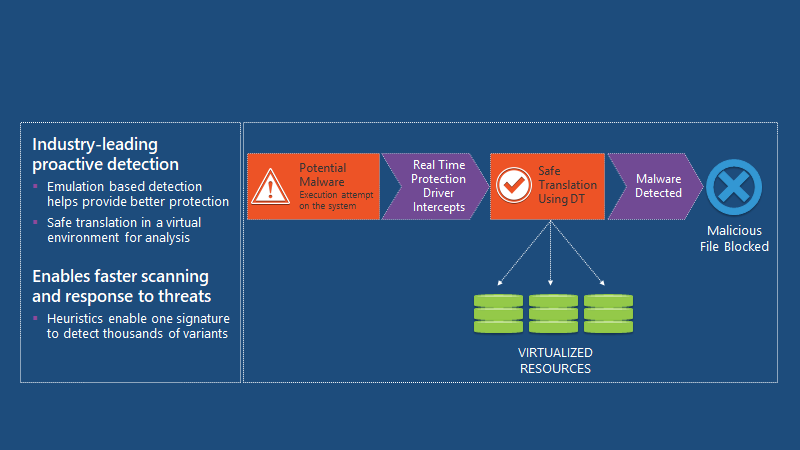
Dynamic Translation With Heuristics
Industry-leading proactive detection enables faster scanning and response to threats. Emulation-based detection helps provide better protection and safe translation into a virtual environment for analysis.
Behavior Monitoring And Dynamic Signatures
Live system monitoring identifies new threats and updates for new threats delivered through the cloud in real-time. Tracks behaviour of the unknown processes and known bad processes, multiple sensors to detect OS anomaly.
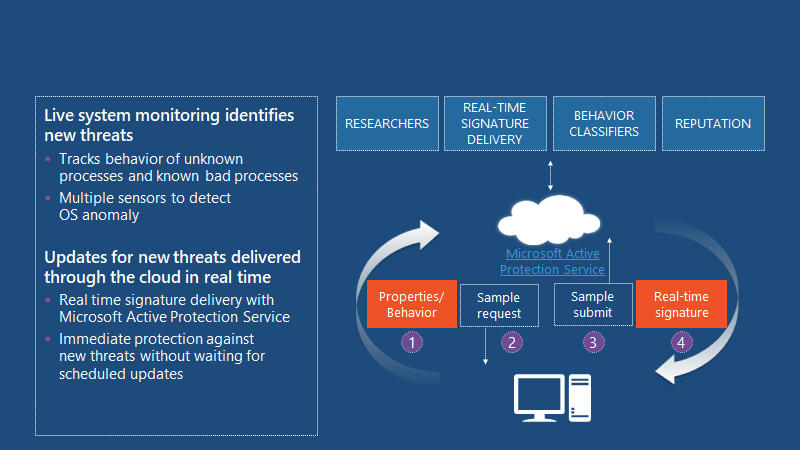
Protect Clients With Reduced Complexity
Simple interface, administrative control, maintains high productivity—minimal high-level user interactions.
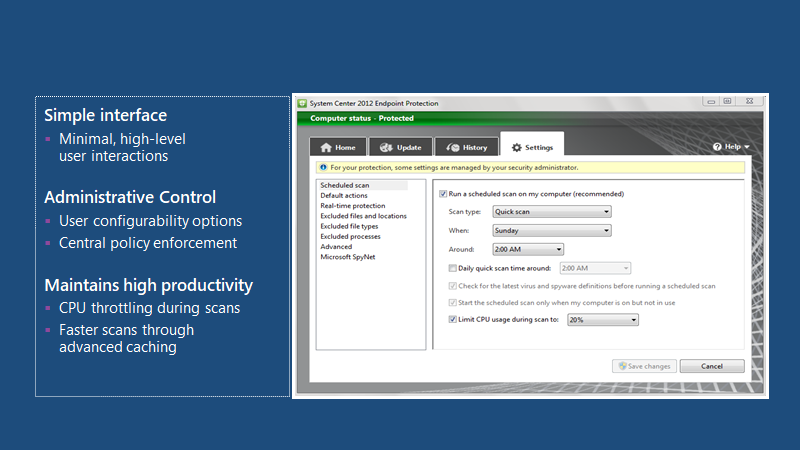
Summary
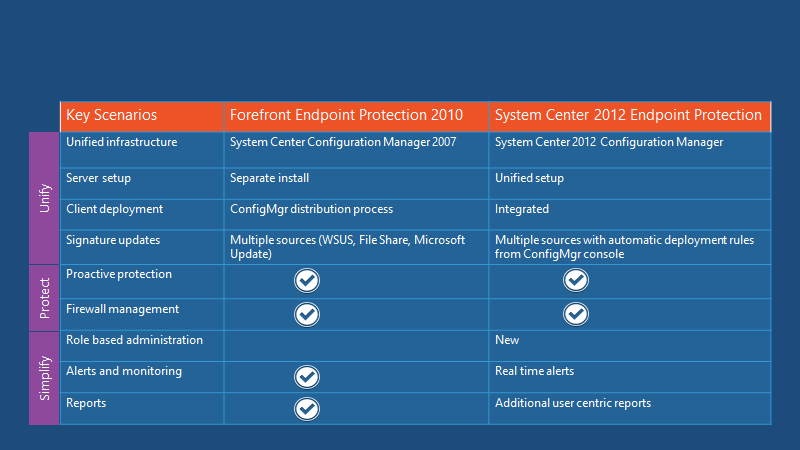
Key scenarios, forefront protection 2010, system centre 2012 endpoint protection.
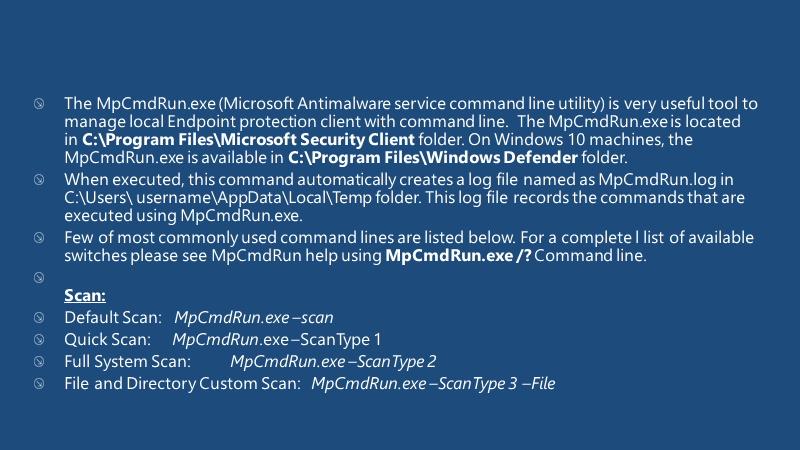
Managing Endpoint Protection client with Command Line Interface – MpCmdRun.exe
Below are a few of the most commonly used command lines. For a complete list of available switches, please see MpCmdRun help using the MpCmdRun.exe/? Command line.
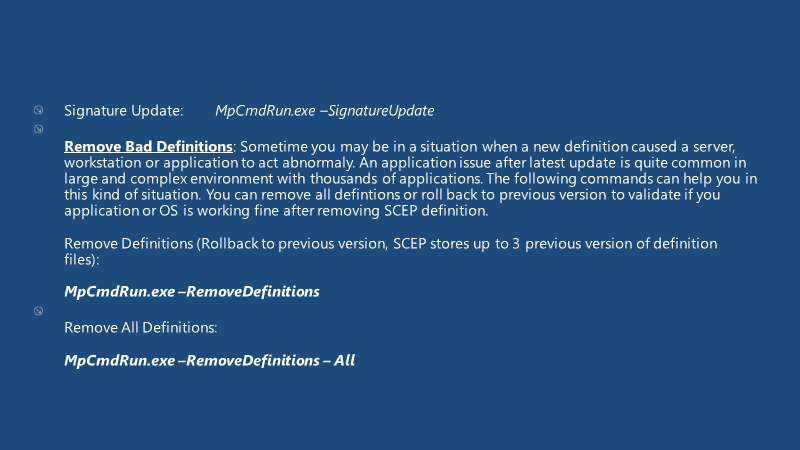
Managing Definitions:
Remove definitions (Rollback to previous version, SCEP stores up to 3 previous version of definition files):
MpCmdRun.exe- Remove definition.
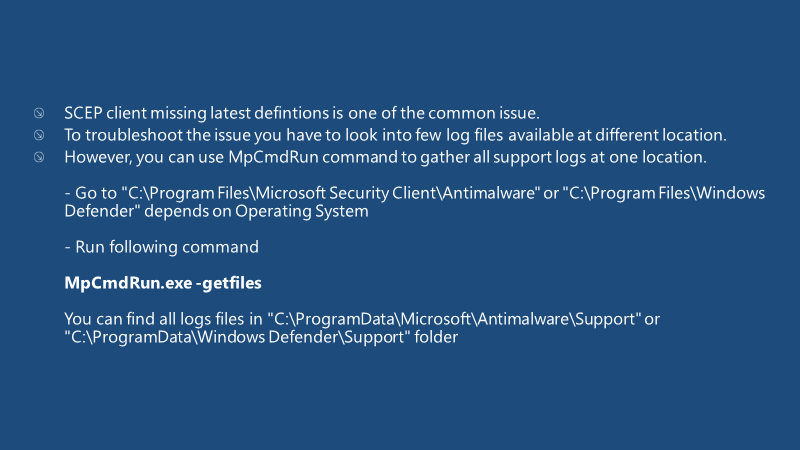
Collecting SCEP support logs:
SCEP client missing the latest definitions is a common issue.To troubleshoot the issue, you have to look into a few log files available at different locations.
Endpoint Protection Log Files
C:\ProgramData\Microsoft\Microsoft Antimalware\Support: This folder contains a bunch of log files that provide more information about SCEP definition updates and SCEP functionality.

WMI Namespace and Classes for System Center Endpoint Protection
Before we move with troubleshooting tips & tricks, let’s have the information about the WMI namespace and classes for SCEP.
AntiMalware Health Status
As the name suggests, this WMI class represent the status of Microsoft Antimalware service. The PowerShell command below lists all properties of this class.
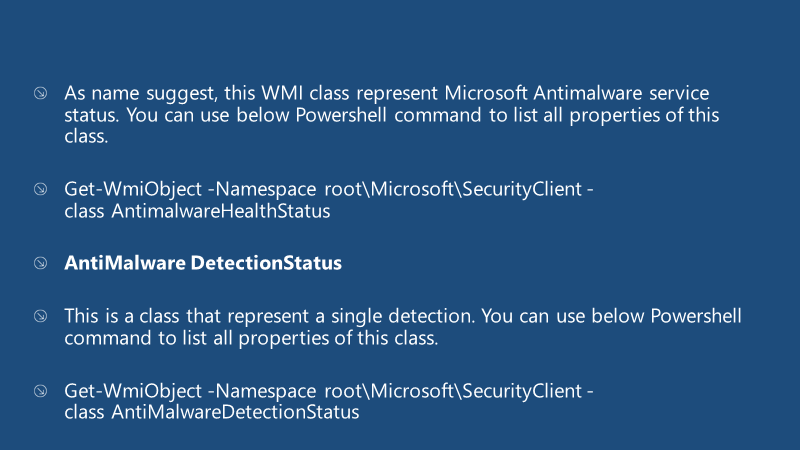
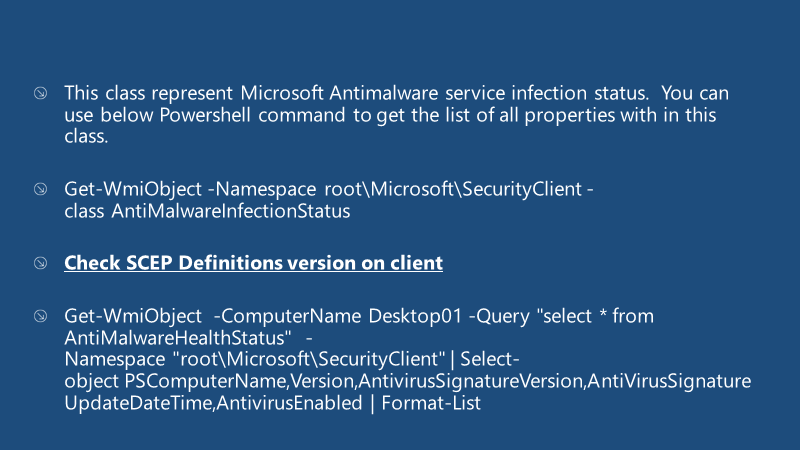
AntiMalware Infection Status
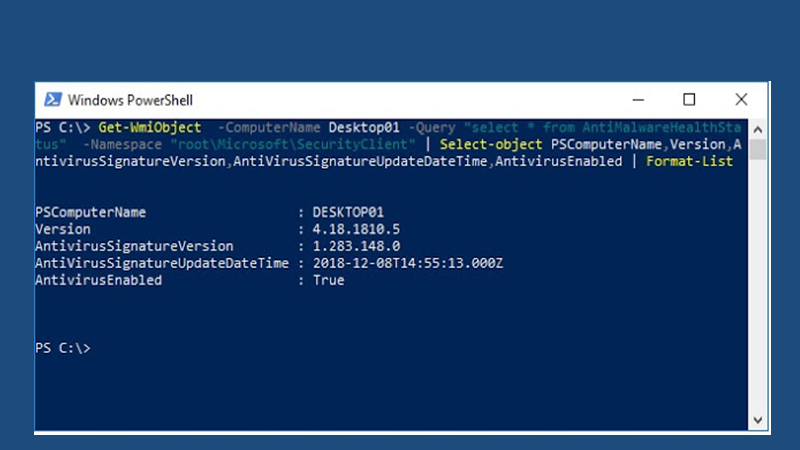
This class represents Microsoft Antimalware service infection status; you can use the Powershell command below to get the list of all properties within this class.
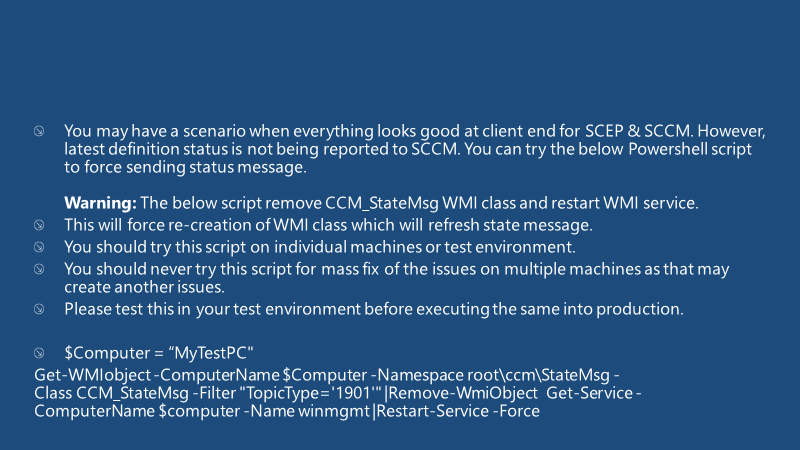
Force State Message for SCEP on SCCM Client
You may have a scenario when everything looks good at the client end for SCEP&SCCM. However, the status of the latest definition has not been reported to SCCM. You can try the below powershell script to force sending status messages.
Disclaimer – The information provided on site is for general informational purposes only. All information on the site is provided in good faith, however, we make no representation or warranty of any kind, express or implied regarding the accuracy, adequacy, validity, reliability, availability, or completeness of any information on the website.
Resources
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here – HTMD WhatsApp
Author
Deepak Rai is a Technical Lead with over 14 years of experience in IT. He specializes in SCCM (AKA ConfigMgr, CB, MECM, etc.), Intune, and Azure (Runbooks). Throughout his career, he has worked on various platforms such as Active Directory, Exchange, Veritas NETBACKUP, Symantec Backup Exec, NDMP devices like Netapp, EMC Data Domain, Quantum using Backup Exec 2010 and 2012, and HP StorageWorks 4048 MSL G3. He also has experience in data deduplication-related troubleshooting. Ultimately, he returned to his roots as an IT Engineer focusing on SCCM technology.

Hi Anoop. We have a problem in our environment where around 3k machines are still stuck on the anti malware engine version that’s shipped with 1909. Despite all efforts it’s not updating to latest anti malware version. Have already tried a few solutions posted on technet, but no joy so far. These machines however are up to date with virus definitions. Could you please advise, what are we not doing to fix aforementioned issue?
Hello Ashu,
Thanks a lot for the question. If you can post it here http://forum.howtomanagedevices.com/ we will make sure we address it ASAP.