Let us learn about Intune Endpoint Security Policies and Microsoft Endpoint Manager Updates.
Sneak peek of Microsoft Endpoint Manager security topics discussed in the section hosted by Paul Mayfield, Terrell Cox, and Micro-Scott.
You can utilize Intune endpoint security policies to manage device security settings effectively. Each endpoint security policy can support one or more profiles, akin to a device configuration policy template and encompass a logical group of related settings.
More details about the session and Intune Endpoint Security are given below.
Ignite 2019 Coverage
- Microsoft Endpoint Management SCCM Intune Windows Updates
- Microsoft Endpoint Manager is the future of SCCM Intune MEMMI MEMCM
- iOS Android macOS Mobile Enrollment Options with Intune
- Basics of Windows Dynamic Update Explained Update Management
- WVD End User Experience Availability Updates
- MSIX Updates from Ignite Reliability Network Disk-space
- Microsoft Learning Certification Exams Updates
- On-Prem WVD Options Azure Quantum Qualys Scan Integration
- Intune Reporting Strategies Advanced Reporting
- Intune Endpoint Security Policies Enhancements
Intune Endpoint Security Policies Microsoft Endpoint Manager
Following are the key pillars of Microsoft Endpoint Manager security enhancements announced in Microsoft Ignite.
- Dedicated Sec Admin node workspace
- Cross persona workflows
- Covers both cloud and on-premises endpoints (SCCM and Intune)
- Integrated with Microsoft Defender ATP
Two Personas and Two Portals
- Endpoint Management (Device Management) and Security Admin -The team manages both devices and security applications.
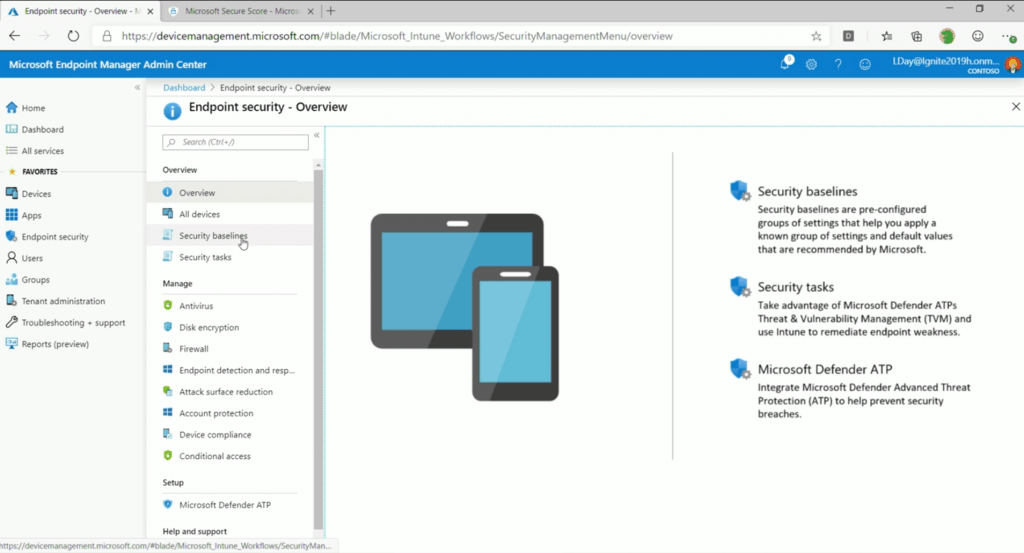
- Only Security Admin (manage only security products like ATP, Symantec, etc.)
This team can log in to the following URL and work accordingly – https://security.microsoft.com/homepage
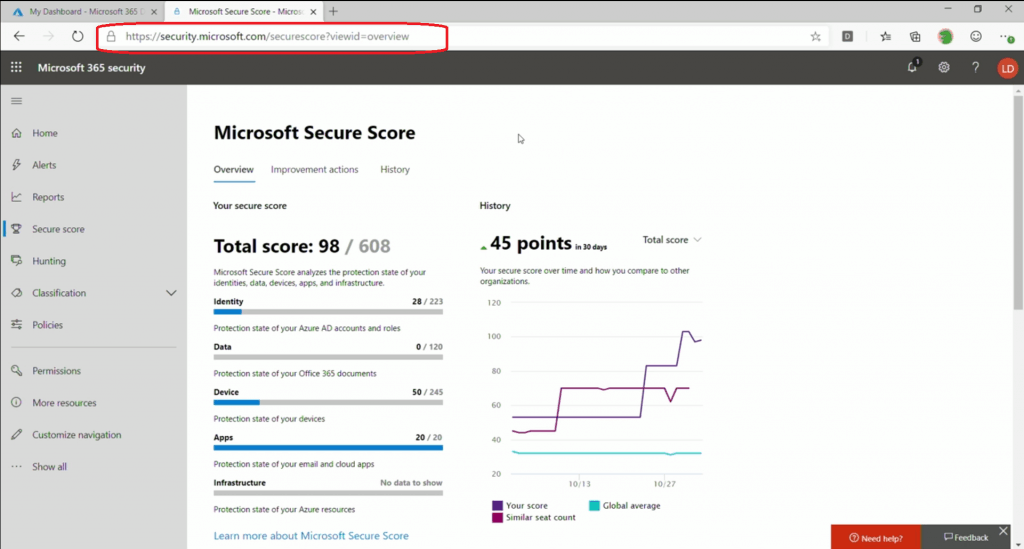
Security Baselines Overview
Intune’s security baselines are preconfigured settings representing best practices from Microsoft security teams. They can be used to quickly deploy recommended device and application settings for protection. Intune is compatible with Windows 10 version 1809 and later and Windows 11.
Following are the security configuration policy options (Security baselines) from Microsoft Endpoint Manager(MEM).
- Microsoft Recommended Settings
- Baseline Drift Reports
- Windows 10 and Defender ATP are available
- Edge and Office Pro Plus (Coming Soon)

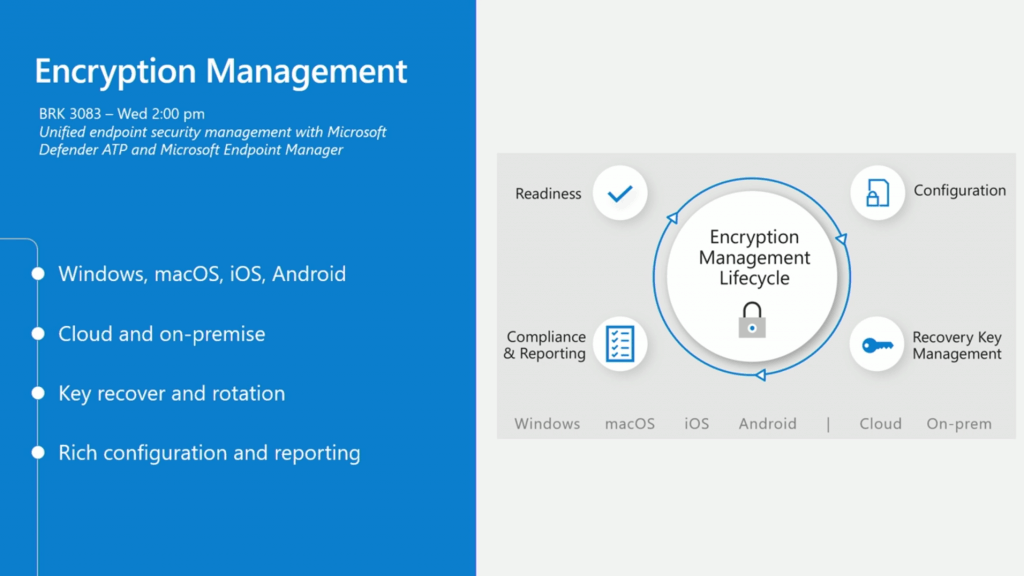
Encryption Management Overview
- Windows, macOS, iOS, Android
- Cloud and on-premises
- Key recovery and rotation
- Rich configuration and reporting
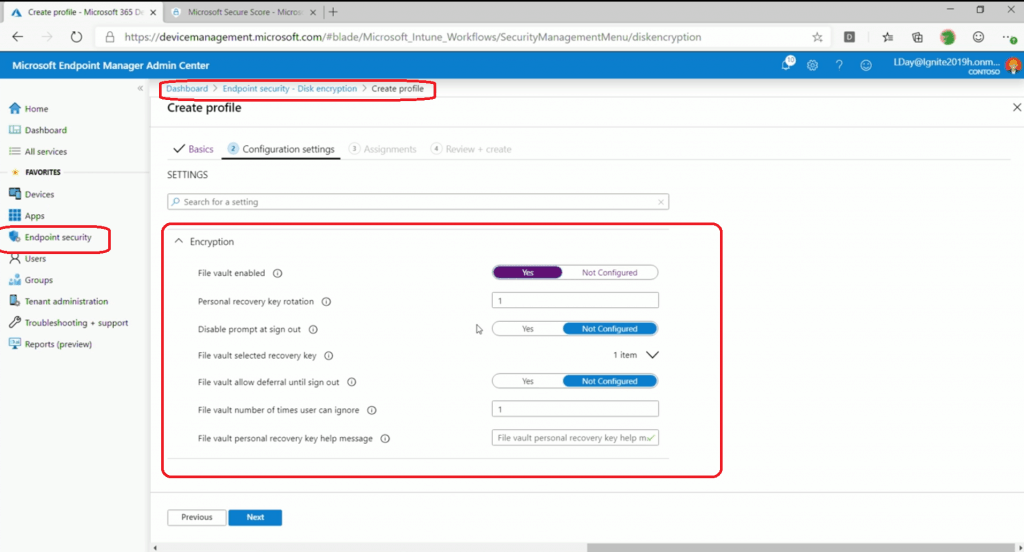
Disk Encryption – Bitlocker or File Vault
The encryption policy option for macOS and Windows is available in the Microsoft Endpoint Portal.
- macOS – File Vault
- Windows – Bitlocker
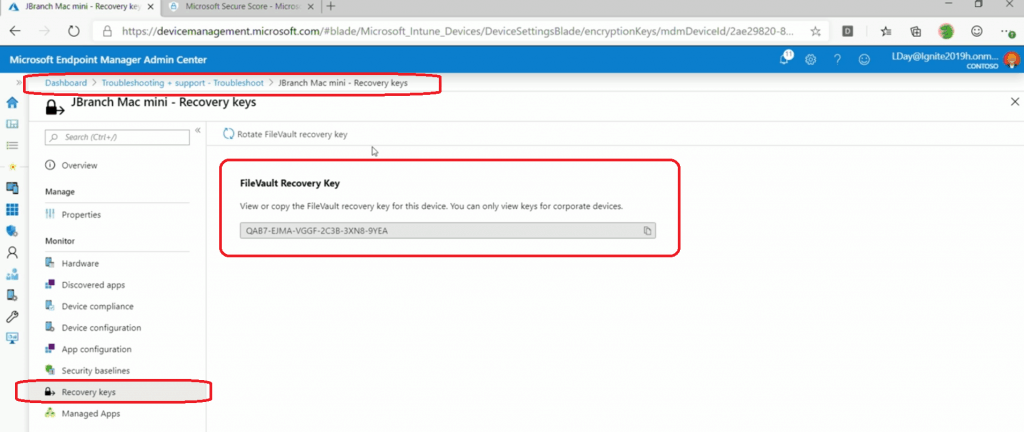
Encryption Recovery Keys Experience
You can go to the troubleshooting + support node from Microsoft Endpoint Manager and select a macOS or Windows device to see the recovery key. This would be very useful for the helpdesk team.
URL -> https://devicemanagement.microsoft.com/#blade/Microsoft_Intune_DeviceSettings/SupportMenu/troubleshooting
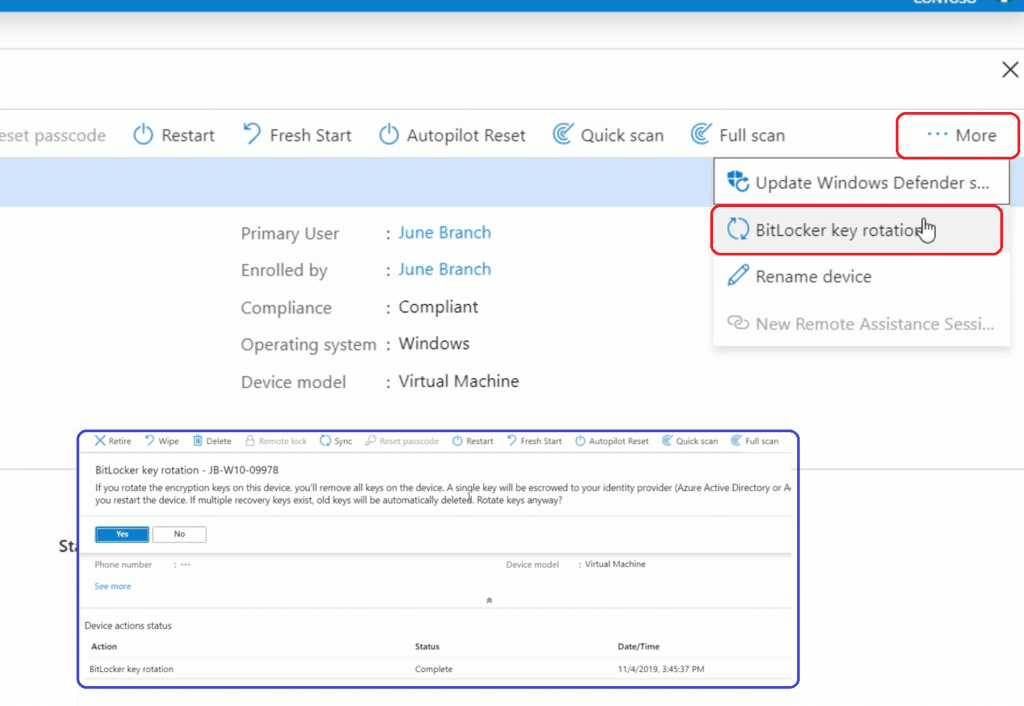
Encryption Key Rotation – Bitlocker Options
Bitlocker key rotation is also available from the Troubleshooting + support node in Microsoft Endpoint Manager. Go to Overview of Windows device -> click on ….More -> select “Bitlocker key Rotation” option.
Resources
- User Enrollment with Intune
- Supported actions with User Enrollment
- End-user privacy with Microsoft Intune
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.
