Let’s discuss Fixes for 6 Exchange Server vulnerabilities in the August patch Tuesday. This post focuses on some common Microsoft Exchange vulnerabilities and exposures (CVEs) recently published or revised in the Microsoft Security Update Guide. If you are still using the Exchange server instead of Exchange Online, you should be very careful about all these vulnerabilities.
In the latest updates, the Microsoft Security Update Guide provided, a set of common vulnerabilities and exposures (CVEs) have either been newly published or undergone revisions. These changes reflect ongoing efforts to enhance the security landscape and protect systems against potential threats. Stay informed to ensure your systems remain safeguarded.
We have an article highlighting the FIX Windows Boot Manager Vulnerability CVE-2023-24932 BlackLotus UEFI bootkit. The article details how users can safeguard themselves against a possible security breach caused by disclosing a vulnerability in Secure Boot. Microsoft released patches for Office Apps, Windows 11 KB5029253 KB5029263, Windows 10 KB5029244, etc, during May 2023 patch Tuesday to fix the issue.
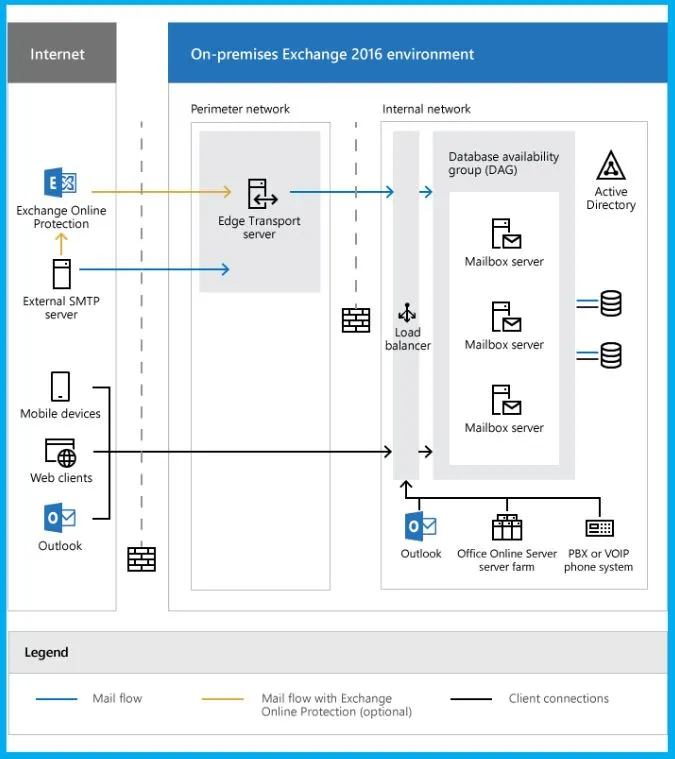
Exchange Server vulnerabilities refer to security flaws and weaknesses identified within Microsoft Exchange Servers. It is important for organizations that use Exchange Server to stay up to date with the latest security advisories and patches from Microsoft to ensure the security and integrity of their systems.
- FIX Zero Day Security Vulnerability for Outlook
- Apple Emergency Patch Released to Fix WebKit Security Vulnerabilities
- FIX Office for Mac Vulnerabilities CVE-2023-24953 and CVE-2023-29344 Urgent Update Required
What is CVE?
CVE stands for Common Vulnerabilities and Exposures. It’s a standardized system to identify and reference publicly known information-security vulnerabilities and exposures.
What is Security Update Guide?
The Security Update Guide is a resource provided by Microsoft that offers detailed information about security updates and patches for their products and services.
Fixes for 6 Exchange Server Vulnerabilities Released in August
The Microsoft Security Response Center (MSRC) examines all reports of security vulnerabilities affecting Microsoft products and services. It provides the information as part of the ongoing effort to help you manage security risks and also help keep your systems protected.
With this post, we are covering 6 common Exchange Server vulnerabilities and exposures, such as CVE-2023-21709, CVE-2023-35368, CVE-2023-35388, CVE-2023-38181, CVE-2023-38182, CVE-2023-38185.
The common vulnerabilities and exposures (CVEs) were recently published or revised in the Microsoft Security Update Guide.
| Exchange Server vulnerabilities | Title |
|---|---|
| CVE-2023-21709 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| CVE-2023-35368 | Microsoft Exchange Remote Code Execution Vulnerability |
| CVE-2023-35388 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-38181 | Microsoft Exchange Server Spoofing Vulnerability |
| CVE-2023-38182 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-38185 | Microsoft Exchange Server Remote Code Execution Vulnerability |
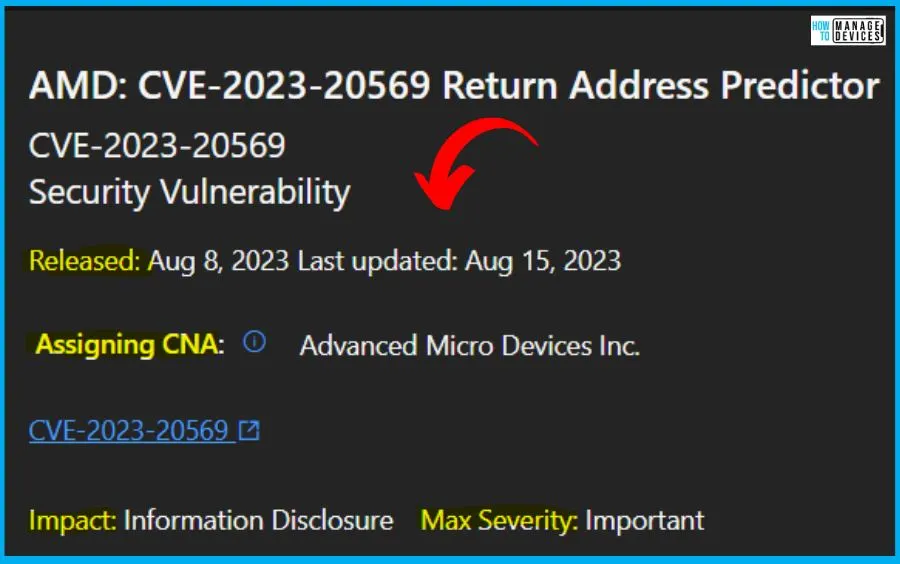
1. CVE-2023-20569 Return Address Predictor
The CVE-2023-20569 Return Address Predictor is an Exchange Server vulnerability released on August 8, 2023. Advanced Micro Devices Inc issued these common vulnerabilities and exposures. The impact of the CVE is Information disclosure, and the Max severity is important.
- The CVE pertains to specific processor models offered by AMD.
- The mitigation for this vulnerability requires a Windows update.
- The Security Update Guide documents this CVE to communicate that the most recent Windows builds incorporate the required mitigation, effectively safeguarding against the vulnerability.
Below is a table that offers an assessment of exploitability for this particular vulnerability as of its initial publication.
| Publicly disclosed | Exploited | Exploitability assessment |
|---|---|---|
| No | No | Exploitation Less Likely |
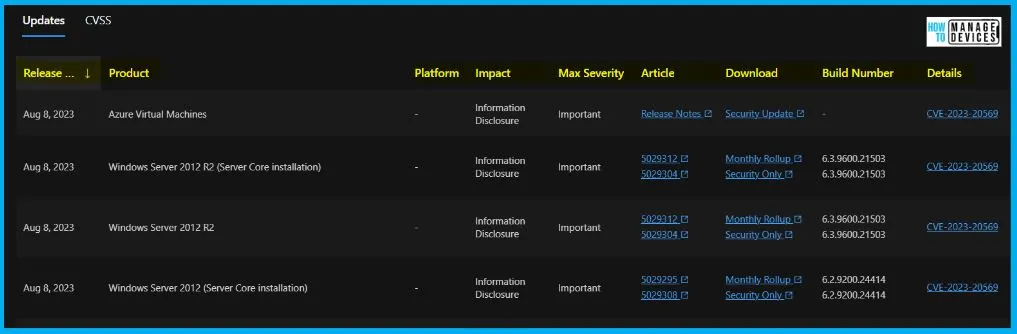
The screenshot below helps you show the CVE-2023-20569 Return Address Predictor security updates; it shows Updates and CVSS menus. It also shows the Release date, Product name, Platform, Impact, Max severity, Article, Download, Build Number and Details.
2. CVE-2023-21709 Microsoft Exchange Server Elevation of Privilege Vulnerability
Microsoft issues this CVE. It is an Exchange server vulnerability released on August 8, 2023. With this CVE, the base score metric is 9.8, and the temporal score is 8.8. The Impact of the CVE is the Elevation of privilege, and the Max severity is important.
- The reason for revision is the known issue affecting the non-English August updates of the Exchange Server has been resolved. Microsoft recommends installing the updated packages as soon as possible.
- To ensure protection against this vulnerability, an additional step is required. Alongside the installation of updates, a script must be executed.
- Install Exchange Server 2016 or 2019 August Security Update (SU) or a subsequent version.
- Run the “CVE-2023-21709.ps1” script on your servers to apply the solution for the CVE automatically.
- Apply the CVE solution manually on each server by executing the following command from an elevated PowerShell window.
Clear-WebConfiguration -Filter "/system.webServer/globalModules/add[@name='TokenCacheModule']" -PSPath "IIS:\"Run the following to roll back the solution for the CVE manually on each server.
New-WebGlobalModule -Name "TokenCacheModule" -Image "%windir%\System32\inetsrv\cachtokn.dll"The below table provides an exploitability assessment for this vulnerability at the time of original publication.
| Publicly disclosed | Exploited | Exploitability assessment |
|---|---|---|
| No | No | Exploitation Less Likely |
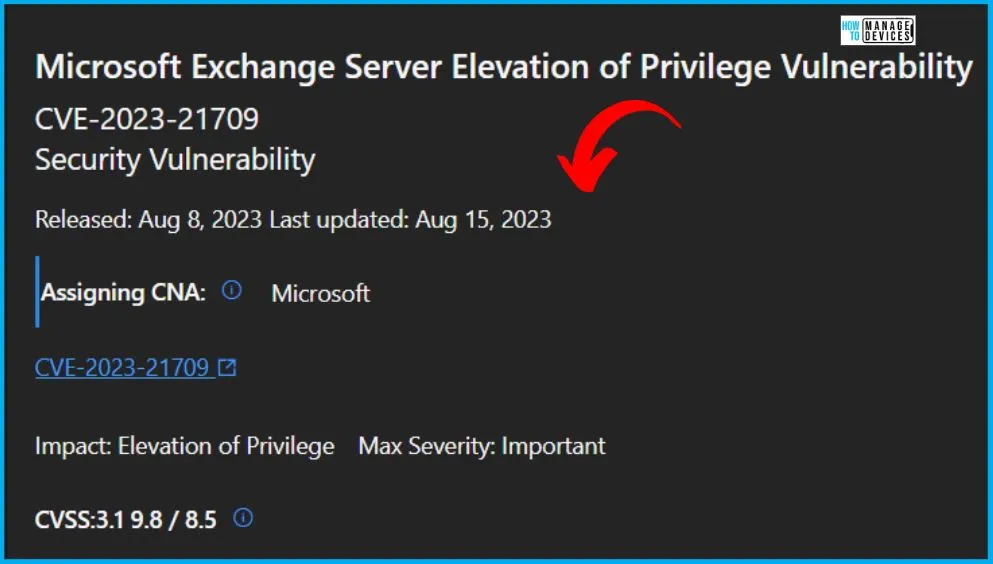
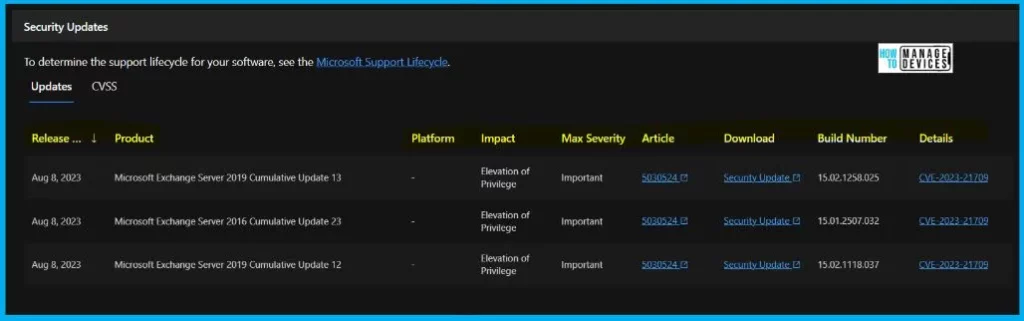
The below window helps you to show the CVE-2023-21709 Microsoft Exchange Server Elevation of Privilege Vulnerability security updates, and it also shows the release date of the update, Product name, Platform, Impact, Max severity, Article, Download, Build number, Details etc.
3. CVE-2023-35368 Microsoft Exchange Remote Code Execution
The CVE-2023-35368 Microsoft Exchange Remote Code Execution is an Exchange Server vulnerability released on August 8. Microsoft issued the CVE. The Impact of the CVE is Remote code execution, and the Aggregate CVE Severity Rating is Important. The Base score metric is 8.8, and the Temporal score metric is 7.7.
- Reason for revision: The known issue affecting the non-English August updates of the Exchange Server has been resolved. Microsoft recommends installing the updated packages as soon as possible.
- If this vulnerability is exploited, an attacker could get hold of a user’s Net-NTLMv2 hash. This hash might then launch an NTLM Relay attack on another service, allowing the attacker to pretend to be the user and authenticate themselves.
- The attackers can focus on server accounts through remote code execution. They might try to activate harmful code using the server’s account through a network connection. Importantly, the attacker doesn’t require any special permissions for this attack.
- Successful exploitation of this vulnerability could allow an attacker to gain remote code execution via an in-network attacker calling arbitrary endpoints.
Note! – August 15, 2023 Update: The known issue affecting the non-English August updates of the Exchange Server has been resolved. Microsoft recommends installing the updated packages as soon as possible.
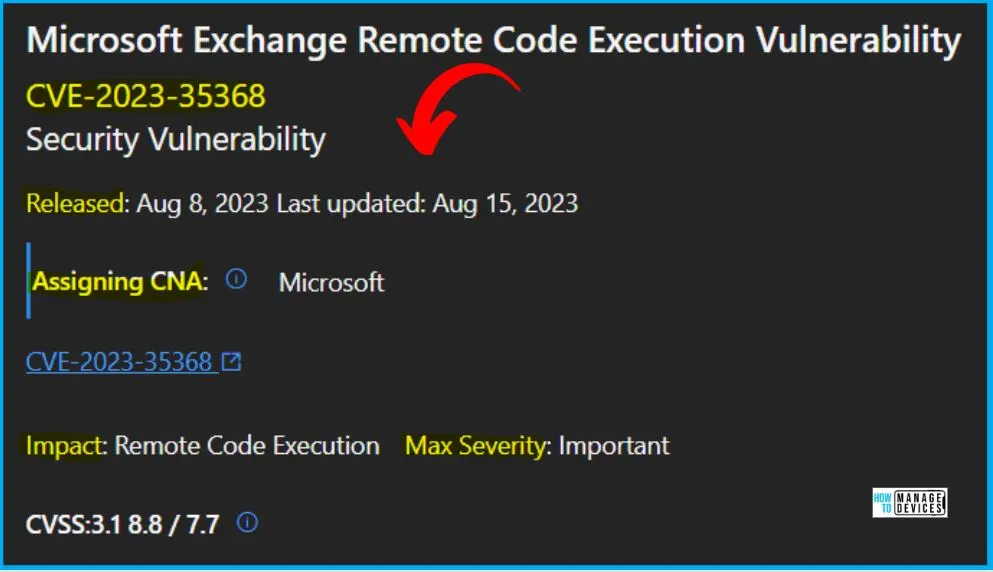
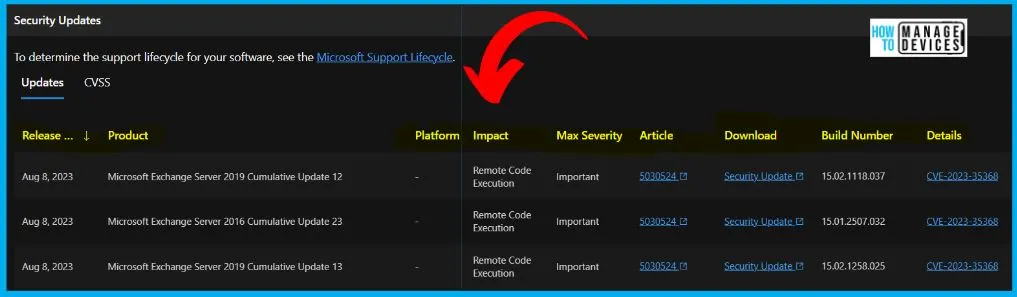
The below window allows you to access information about the security updates for CVE-2023-35368, which addresses the Microsoft Exchange Remote Code Execution Vulnerability. It displays the update’s release date and key details such as the product name, platform, impact, maximum severity, associated article, download options, build number, and additional particulars.
4. CVE-2023-35371 Microsoft Office Remote Code Execution Vulnerability
Microsoft issued this CVE-2023-35371 Microsoft Office Remote Code Execution Vulnerability, and the release date is August 8, 2023. The impact of the CVE is Remote code execution, and the Aggregate CVE Severity Rating IS Important. The Base score metric is 7.8, and the Temporal score metric is 6.8/.
- Reason for revision: Updated the build numbers. This is an informational update only.
- The security update for Microsoft Office 2019 and Microsoft Office LTSC for Mac 2021 is not immediately available.
- The word Remote in the title refers to the location of the attacker.
- Successfully exploits this vulnerability causing downtime for the targeted environment.
| Publicly disclosed | Exploited | Exploitability assessment |
|---|---|---|
| No | No | Exploitation Less Likely |
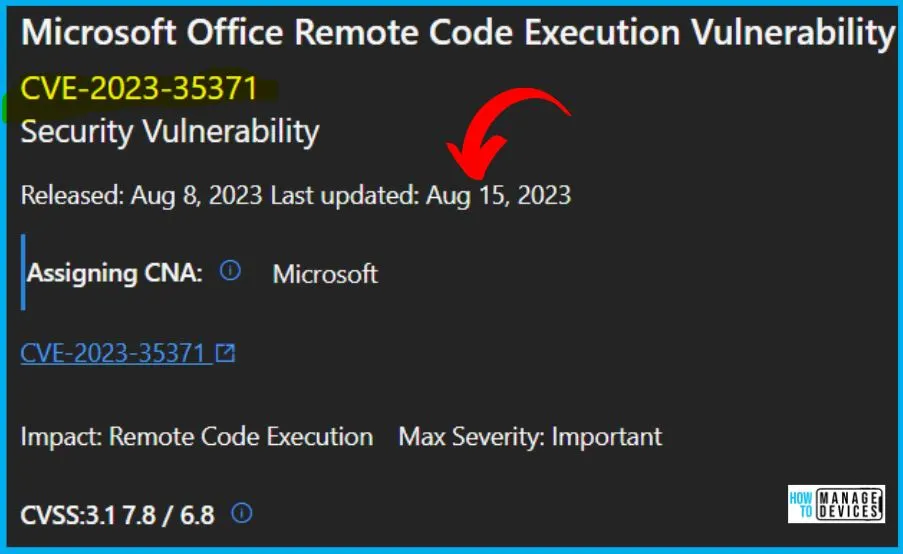
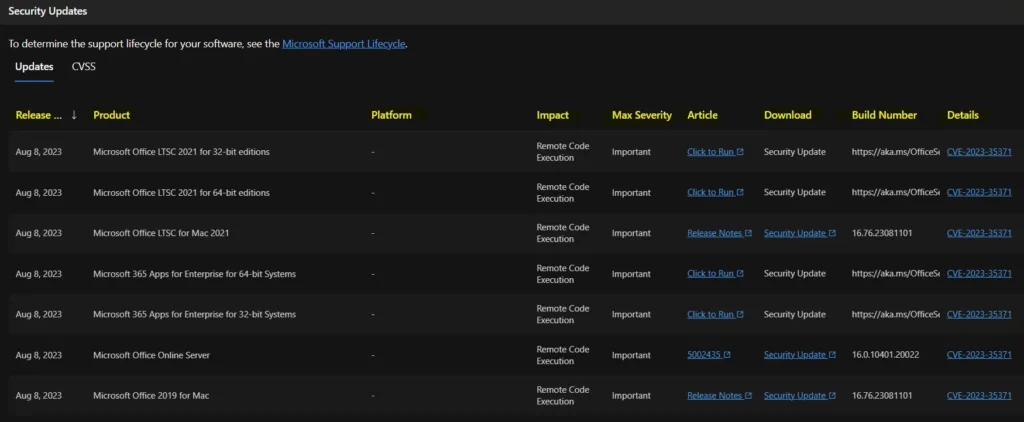
The below window helps you to show the CVE-2023-35371 Microsoft Office Remote Code Execution Vulnerability security updates, and it also shows the release date of the update, Product name, Platform, Impact, Max severity, Article, Download, Build number, Details etc.
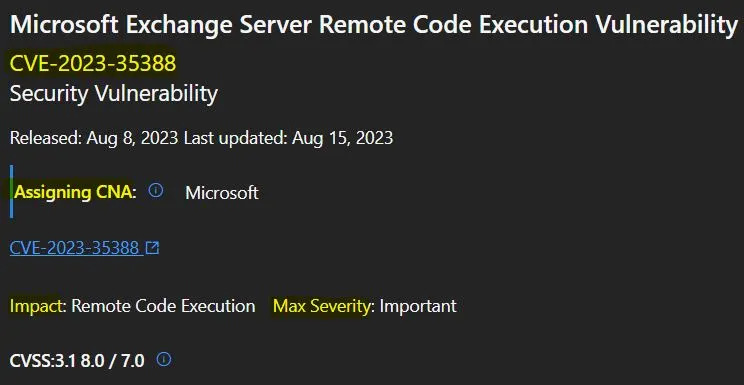
5. CVE-2023-35388 Microsoft Exchange Server Remote Code Execution Vulnerability
Microsoft issued this CVE-2023-35388 Microsoft Exchange Server Remote Code Execution Vulnerability. The reason for revision is that the known issue affecting the non-English August updates of the Exchange Server has been resolved. Microsoft recommends installing the updated packages as soon as possible.
- An authenticated attacker on the same intranet as the Exchange server can achieve remote code execution via a PowerShell remoting session.
- August 15, 2023 Update: The known issue affecting the non-English August updates of the Exchange Server has been resolved. Microsoft recommends installing the updated packages as soon as possible.
- An authenticated attacker could exploit this vulnerability with LAN access.
| Title | Version | Originally released | Last updated | Aggregate CVE Severity Rating |
|---|---|---|---|---|
| Microsoft Exchange Server Remote Code Execution Vulnerability | 2.0 | August 8, 2023 | August 8, 2023 | Important |
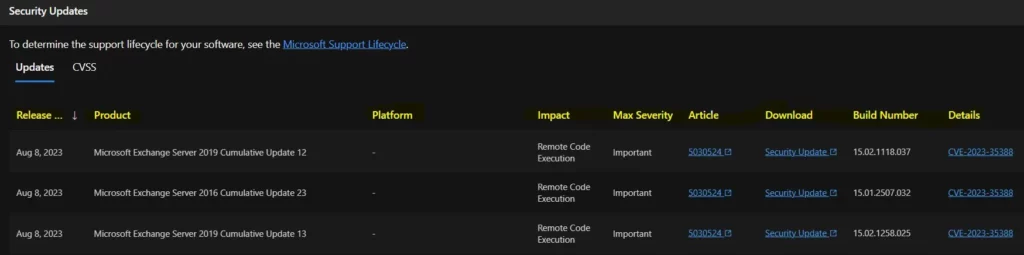
The below window allows you to access information about the security updates for CVE-2023-35388, which addresses the Microsoft Exchange Remote Code Execution Vulnerability. It displays the update’s release date and key details such as the product name, platform, impact, maximum severity, associated article, download options, build number, and additional particulars.
6. CVE-2023-36769 Microsoft OneNote Spoofing Vulnerability
Microsoft issued CVE-2023-36769 Microsoft OneNote Spoofing Vulnerability. The version is 1.0, and the Reason for revision: Information published. This CVE was addressed by updates released in August 2023, but the CVE was inadvertently omitted from the August 2023 Security Updates.
- Microsoft strongly recommends that customers running affected versions of OneNote install the updates to be protected from this vulnerability.
- This was originally released; the last updated date is August 15, 2023. The Aggregate CVE Severity Rating is Moderate.
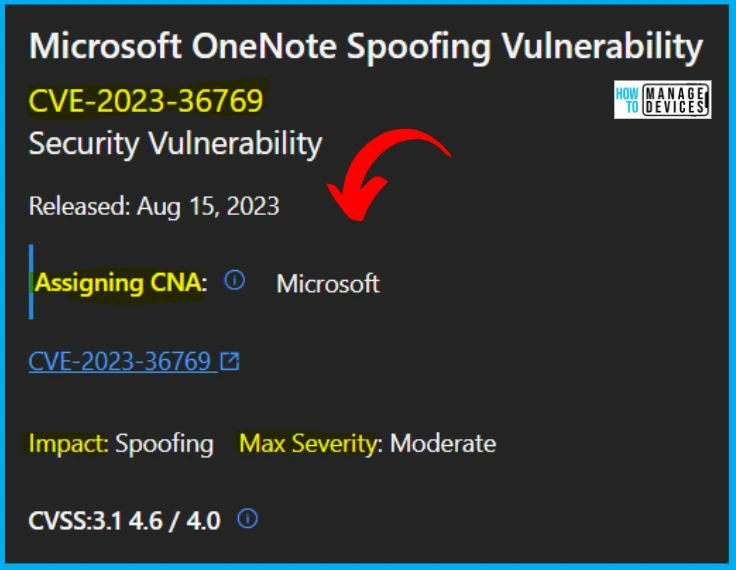
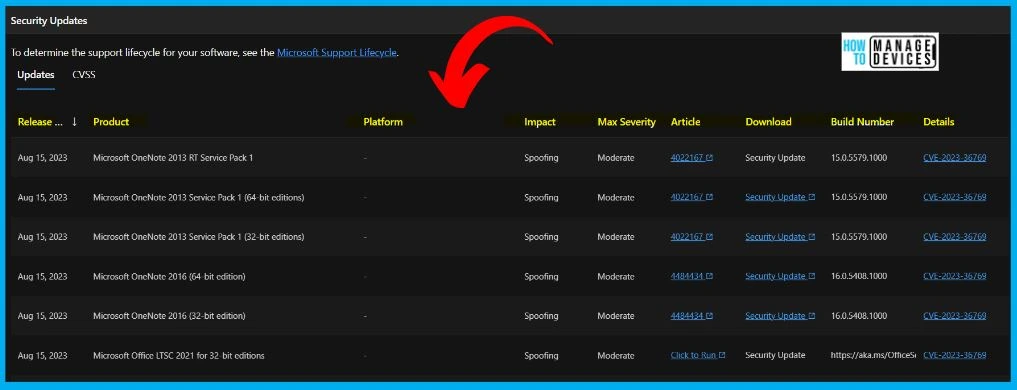
The below window helps you to show the CVE-2023-36769 Microsoft OneNote Spoofing Vulnerability security updates, and it also shows the release date of the update, Product name, Platform, Impact, Max severity, Article, Download, Build number, Details etc.
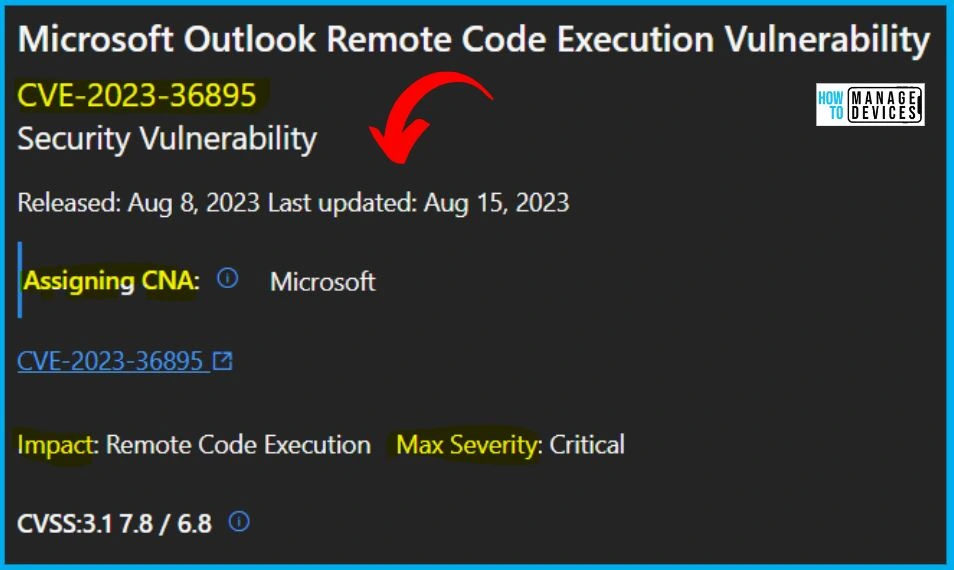
7. CVE-2023-36895 Microsoft Outlook Remote Code Execution Vulnerability
CVE-2023-36895 Microsoft Outlook Remote Code Execution Vulnerability was released on August 8, 2023, and last updated id August 15, 2023. The version is 1.2, and the Aggregate CVE Severity Rating is Critical. Reason for revision: Updated the build numbers. This is an informational update only.
| Publicly disclosed | Exploited | Exploitability assessment |
|---|---|---|
| No | No | Exploitation Less Likely |
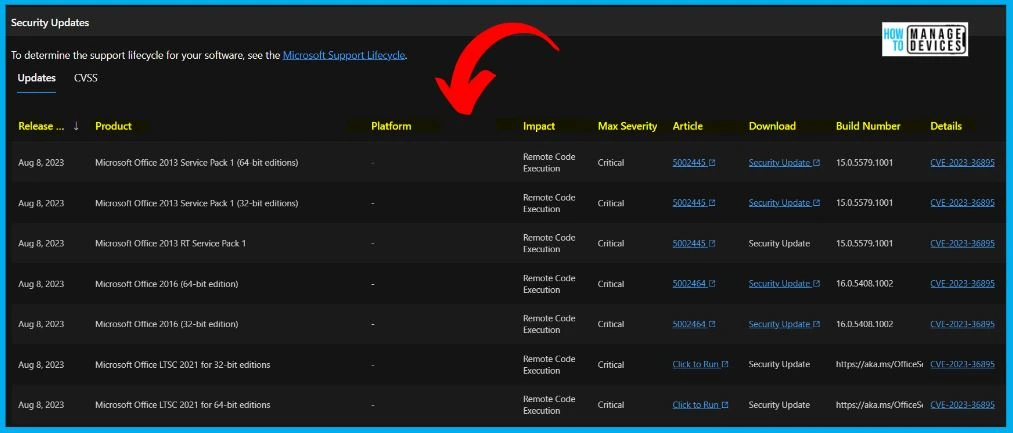
The below window allows you to access information about the security updates for CVE-2023-36895, which addresses the Microsoft Outlook Remote Code Execution Vulnerability. It displays the update’s release date and key details such as the product name, platform, impact, maximum severity, associated article, download options, build number, and additional particulars.
8. CVE-2023-36896 Microsoft Excel Remote Code Execution Vulnerability
Microsoft issued CVE-2023-36896 Microsoft Excel Remote Code Execution Vulnerability. The version is 1.1, and the Reason for the revision is to update the build numbers. This is an informational update only. The Originally released is August 8, 2023, and the Last updated: August 15, 2023. The Aggregate CVE Severity Rating is Important.
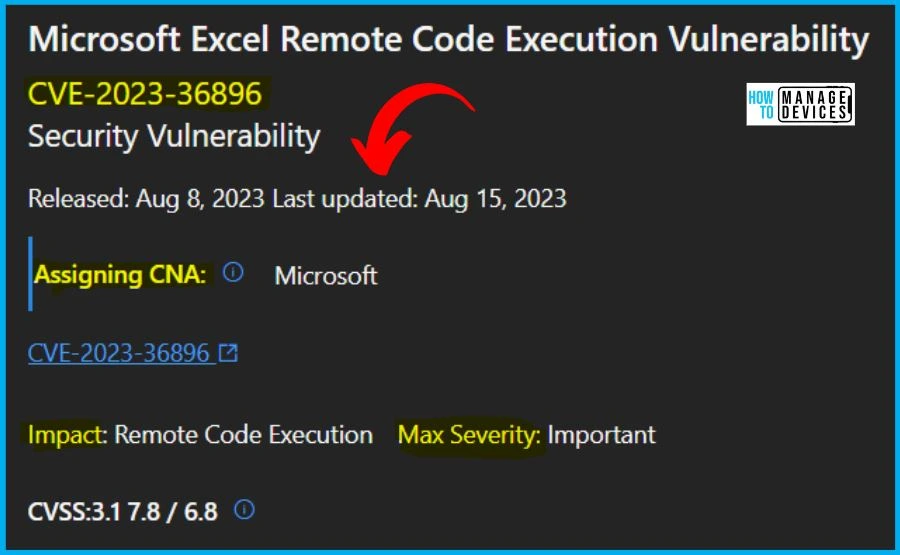
The below window helps you to show the CVE-2023-36896 Microsoft Excel Remote Code Execution Vulnerability security updates, and it also shows the release date of the update, Product name, Platform, Impact, Max severity, Article, Download, Build number, Details etc.
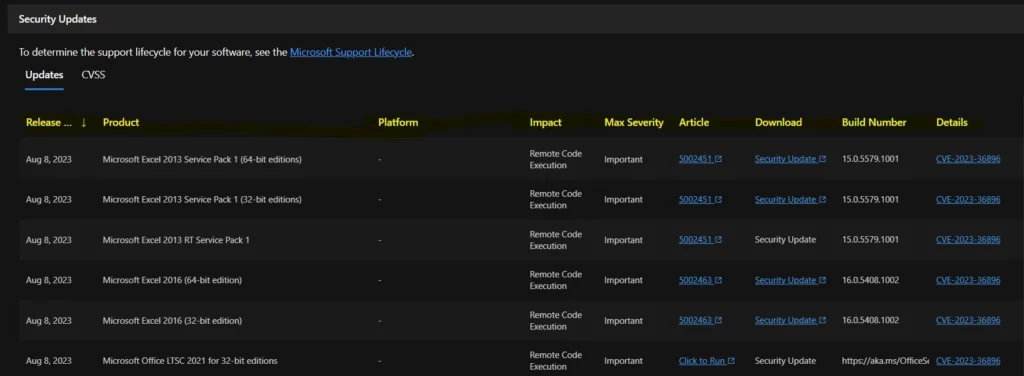
9. CVE-2023-36897 Visual Studio Tools for Office Runtime Spoofing Vulnerability
Microsoft issued CVE-2023-36897 Visual Studio Tools for Office Runtime Spoofing Vulnerability, and the Version is 1.1. Reason for revision: The Visual Studio 2010 Tools for Office Runtime Download link was added to the Security Updates table. The Originally released date is August 8, 2023, and the Last update is August 15, 2023. The Aggregate CVE Severity Rating is Important.
| Publicly disclosed | Exploited | Exploitability assessment |
|---|---|---|
| No | No | Exploitation Less Likely |
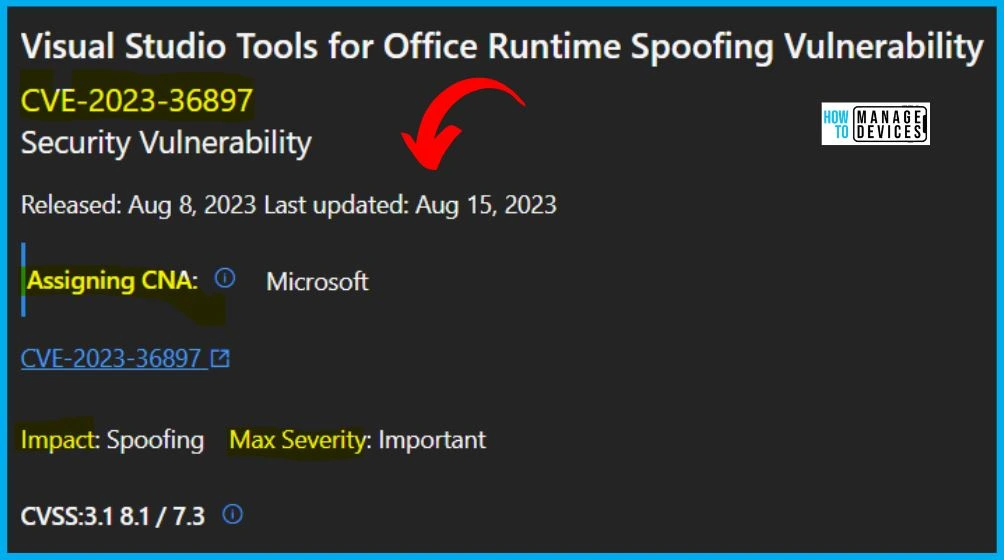
The below window allows you to access information about the security updates for CVE-2023-36897, which addresses the Visual Studio Tools for Office Runtime Spoofing Vulnerability. It displays the update’s release date and key details such as the product name, platform, impact, maximum severity, associated article, download options, build number, and additional particulars.
10. CVE-2023-38167 Microsoft Dynamics Business Central Elevation Of Privilege Vulnerability
CVE-2023-38167 Microsoft Dynamics Business Central Elevation Of Privilege Vulnerability was Originally released on August 8, 2023, and Last updated on August 15, 2023. The Aggregate CVE Severity Rating is Important, and the version is 2.0.
- Reason for revision: In the Security Updates table, I made the following revision
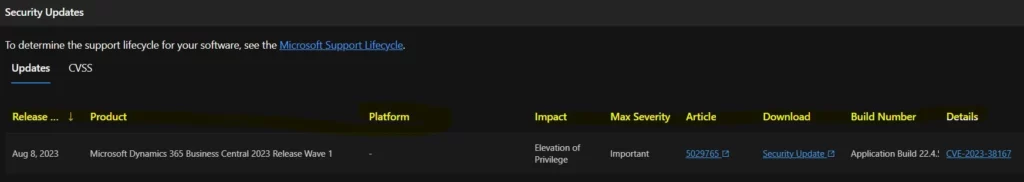
- The security update for Microsoft Dynamics 365 Business Central 2023 Release Wave 1 is now available.
- Customers running this affected version of Microsoft Dynamics 365 Business Central 2023 should install the update to be protected from this vulnerability.
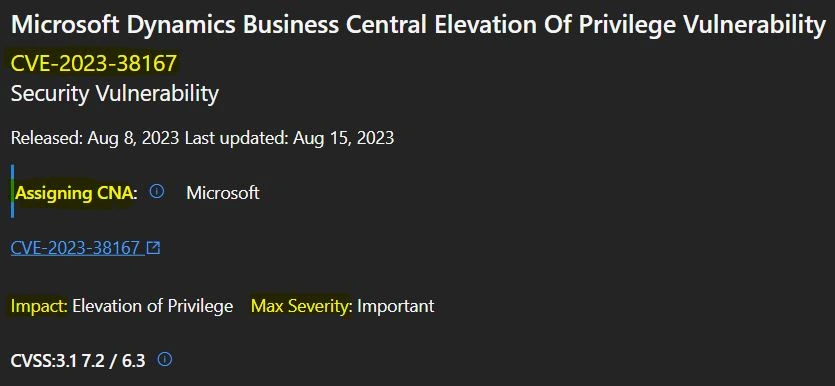
The below window helps you to show the CVE-2023-38167 Microsoft Dynamics Business Central Elevation Of Privilege Vulnerability security updates, and it also shows the release date of the update, Product name, Platform, Impact, Max severity, Article, Download, Build number, Details etc.
11. CVE-2023-38181 Microsoft Exchange Server Spoofing Vulnerability
Microsoft issued CVE-2023-38181 Microsoft Exchange Server Spoofing Vulnerability. The reason for revision: The known issue affecting the non-English August updates of the Exchange Server has been resolved. Microsoft recommends installing the updated packages as soon as possible.
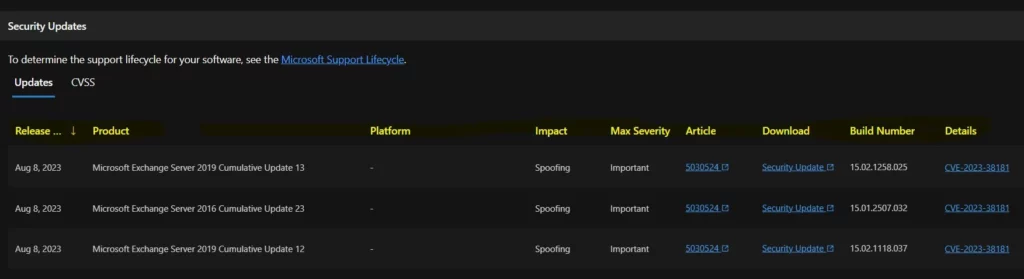
| Title | Version | Originally released | Last updated | Aggregate CVE Severity Rating |
|---|---|---|---|---|
| Microsoft Exchange Server Spoofing Vulnerability | 2.0 | August 8, 2023 | August 8, 2023 | Important |
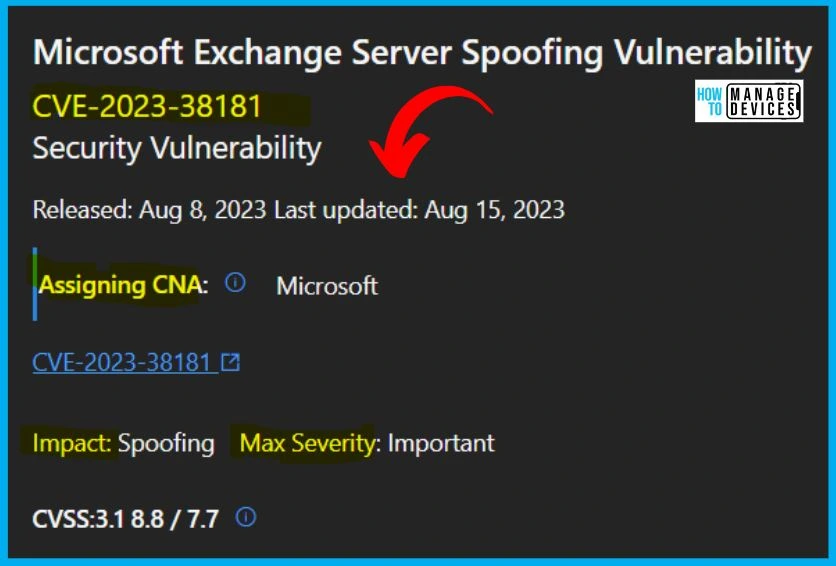
The below window allows you to access information about the security updates for CVE-2023-38181, which addresses the Microsoft Exchange Server Spoofing Vulnerability. It displays the update’s release date and key details such as the product name, platform, impact, maximum severity, associated article, download options, build number, and additional particulars.
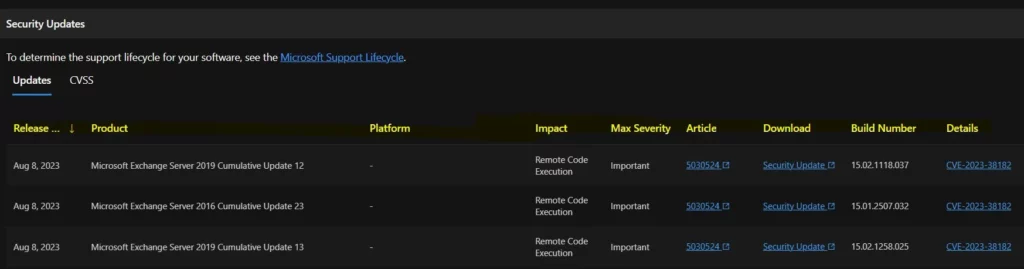
12. CVE-2023-38182 Microsoft Exchange Server Remote Code Execution Vulnerability
Microsoft issued CVE-2023-38182 Microsoft Exchange Server Remote Code Execution Vulnerability; the version is 2.0. The reason for revision is the known issue affecting the non-English August updates of the Exchange Server has been resolved. Microsoft recommends installing the updated packages as soon as possible.
| Publicly disclosed | Exploited | Exploitability assessment |
|---|---|---|
| No | No | Exploitation More Likely |
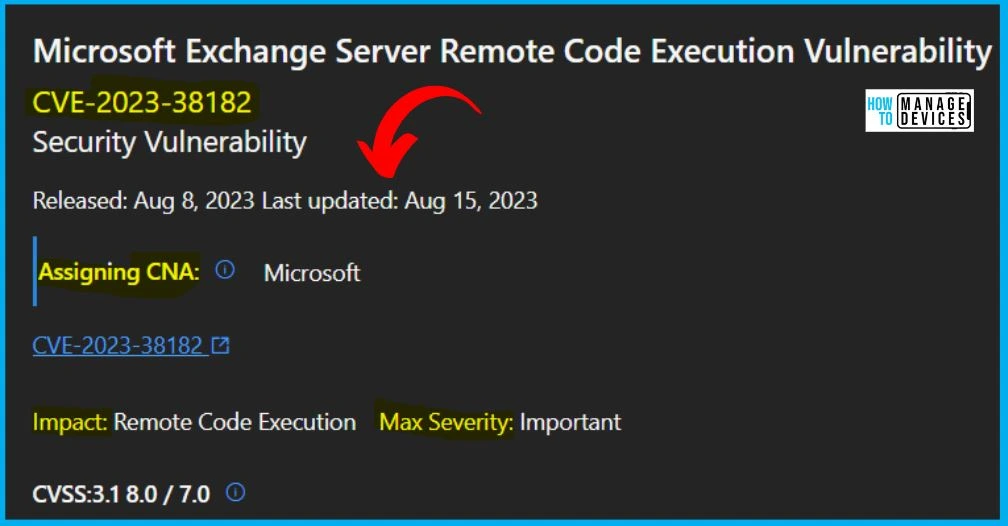
The below window helps you to show the CVE-2023-38182 Microsoft Exchange Server Remote Code Execution Vulnerability security updates, and it also shows the release date of the update, Product name, Platform, Impact, Max severity, Article, Download, Build number, Details etc.
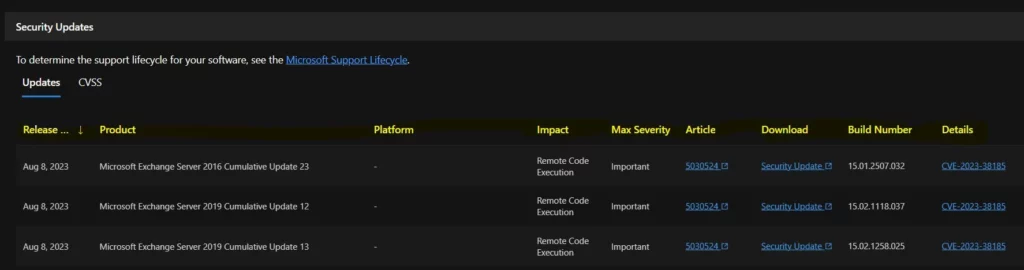
13. CVE-2023-38185 Microsoft Exchange Server Remote Code Execution Vulnerability
CVE-2023-38185 Microsoft Exchange Server Remote Code Execution Vulnerability is Originally released on August 8, 2023. The Reason for revision is the known issue affecting the non-English August updates of the Exchange Server has been resolved. Microsoft recommends installing the updated packages as soon as possible.
| Title | Version | Aggregate CVE Severity Rating | Impact | Base score metrics | Temporal score metrics |
|---|---|---|---|---|---|
| Microsoft Exchange Server Remote Code Execution Vulnerability | 2.0 | Important | Remote Code Execution | 8.8 | 7.7 |
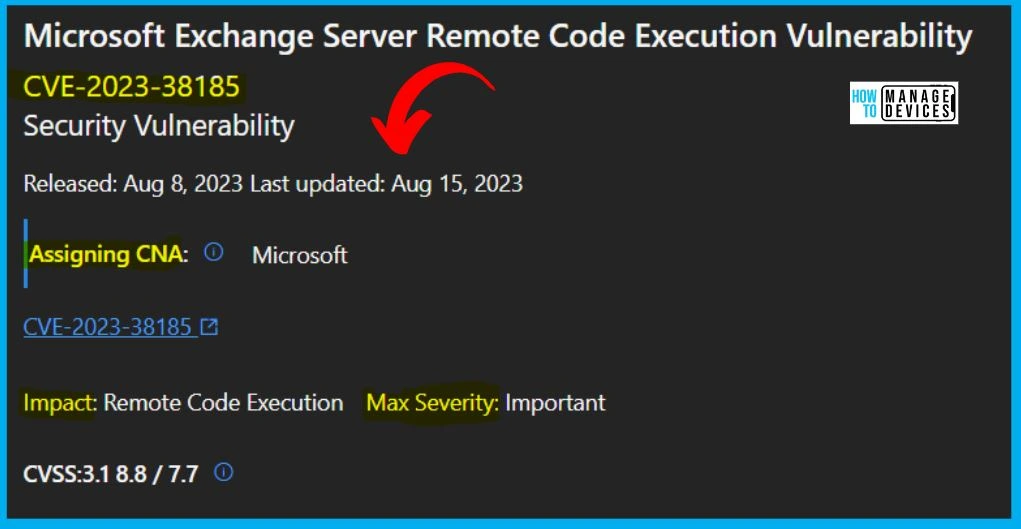
The below window allows you to access information about the security updates for CVE-2023-38185, which addresses the Microsoft Exchange Server Remote Code Execution Vulnerability. It displays the update’s release date and key details such as the product name, platform, impact, maximum severity, associated article, download options, build number, and additional particulars.
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.
