Let’s learn about fixing Windows Boot Manager Vulnerability CVE-2023-24932. Microsoft published Three (3) Zero Day Vulnerabilities with May 2023 Patch Tuesday. The article details how users can safeguard themselves against a possible security breach caused by disclosing a vulnerability in Secure Boot, which could allow attackers to bypass its security features.
Specifically, it focuses on the BlackLotus UEFI bootkit associated with the CVE-2023-24932 tracking number. By implementing the measures outlined in the post, users can mitigate the risk of falling victim to this type of security threat. Microsoft released patches for Windows 11 KB5026368, KB5026372, & Windows 10 KB5026361 during May 2023 patch Tuesday to fix this issue.
Let’s discuss enabling the protections and guidance to update bootable media. A bootkit is a malicious software program designed to load as early as possible in a device’s sequence. A bootkit can exploit the operating system’s vulnerabilities and gain continued access to the device. Another vulnerability fixed by Microsoft is FIX Windows Boot Manager Vulnerability CVE-2023-24932 BlackLotus UEFI Bootkit.
The security update provides a solution to the vulnerability by updating the Windows Boot Manager; it is important to note that the update does not enable by default. This means that users must take action to allow the update and ensure their system is secure. SCCM and Intune methods to fix the boot manager Manager Vulnerability CVE-2023-24932 are explained in the below section.

[🆕🎥] 🔥BlackLotus Fix with May Patch Tuesday https://www.youtube.com/shorts/oFurMUvNjjc 🔥Detection and Remediation options from MS and Community🔥Event Logs and Registry detection options 🔥Fix the issue without reimaging the devices 🔥CVE-2022-21894 and CVE-2023-24932. A quick overview is given below.
How can an Attacker Successfully Exploit this Vulnerability?
An attacker would require physical access to the targeted device or administrative privileges to leverage the vulnerability. With these permissions, the attacker could install a boot policy susceptible to the exploit. This would enable the attacker to gain unauthorized access to the device’s boot process and execute malicious code, potentially leading to significant security breaches and data theft.
What kind of Security Feature could be Bypassed by Successfully Exploiting this Vulnerability?
If an attacker were to take advantage of this vulnerability successfully, they could circumvent the Secure Boot feature. This means that the attacker can easily load and execute malicious code on the device without being detected, potentially leading to a range of security threats, including unauthorized access to sensitive information, installation of additional malware, etc.
According to the CVSS Metric, the Privileges Required are high (PR:H). What does that mean for this Vulnerability?

To successfully exploit this vulnerability requires an attacker to compromise admin credentials on the device.
Are there Additional steps I need to take to be Protected from this Vulnerability?
While the security update is designed to address the vulnerability by updating the Windows Boot Manager, it is important to note that the update is not automatically activated.
As such, users must take additional steps to ensure that their device is protected from the vulnerability. This may involve enabling the security update manually or taking other measures to mitigate the risks associated with the exploit. Failure to take these additional steps could leave the device vulnerable to attack.
Do we need to reimage the Windows Devices to Fix this issue?

Not really, even though some of the Microsoft articles linked below suggest that the community has come up with other options to fix this vulnerability without reimaging the devices.
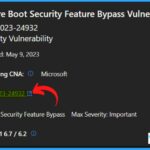
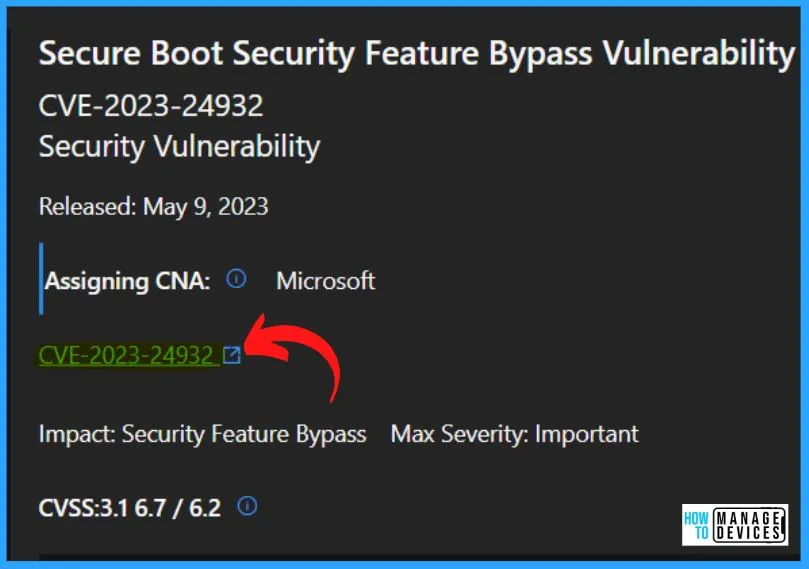
CVE-2023-24932 Windows Boot Manager Vulnerability
Microsoft recommends Secure Boot as a key security feature that establishes a trusted path from the UEFI to the Trusted Boot sequence in the Windows kernel. Secure Boot provides crucial protection against various security threats by preventing bootkit malware from infiltrating the boot sequence.
- Disabling this feature can significantly increase a device’s vulnerability to attack, particularly from bootkit malware capable of evading other security measures.
- Therefore, users must ensure that Secure Boot remains enabled on their devices to maintain security and protect against potential security breaches.
- Fixing the Secure Boot bypass described in CVE-2023-24932 requires revoking boot managers. This could cause issues with some devices’ boot configurations.
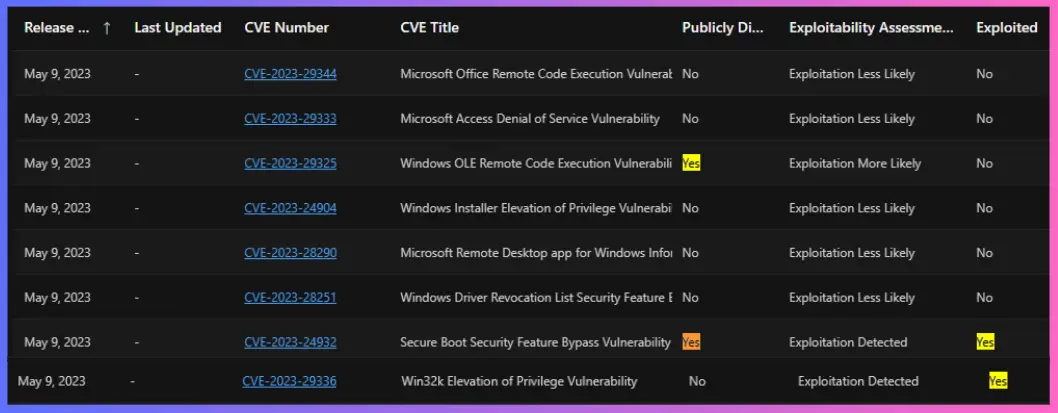
| Release Date | CVE Number | CVE Title | Publicly Disclosed | Exploitability Assessment | Exploited | Impact | Max Severity | Tag |
|---|---|---|---|---|---|---|---|---|
| May 9, 2023 | CVE-2023-24932 | Secure Boot Security Feature Bypass Vulnerability | Yes | Exploitation Detected | Yes | Security Feature Bypass | Important | Windows Secure Boot |
Take Actions to Secure Boot Changes Associated with CVE-2023-24932
By following these steps, users can help safeguard their systems against various potential security threats and ensure that their devices remain secure and protected.
1. Install May 9, 2023, Updates on All Supported Versions of their Operating System
Install the May 9, 2023, updates on all supported versions. It is essential to restart the device to complete the installation process. Once the device has been restarted, users can apply the necessary revocations to address the Secure Boot bypass vulnerability described in CVE-2023-24932.
2. UPDATE Bootable Media
You should ensure that bootable media is up-to-date and fully protected against potential security threats; it is essential to update it with the latest Windows updates released on or after May 9, 2023. Suppose users do not create their media.
- In that case, they can obtain the updated official media from Microsoft or their device manufacturer (OEM) to ensure their bootable media is correctly updated and configured.
- By updating their bootable media in this way, users can help to ensure that their devices are protected against a range of potential security threats and that their system configurations are optimized for maximum performance and security.
3. APPLY the Revocations
To fully protect against the potential security threat posed by the Secure Boot bypass vulnerability described in CVE-2023-24932, applying the relevant revocation files is essential. These files, included in the updates released on or after May 9, 2023, have a “Code Integrity Boot Policy” and a “Secure Boot UEFI Forbidden List” update.
Note! After applying the relevant updates and revocation files, an additional restart is required.
Complete the following steps on all Windows devices to apply the revocations. More details are available in the below section of the post. There are some sample PowerShell scripts provided by the community and Microsoft in the bottom section of the post.
- Apply the Code Integrity Boot Policy
- Apply the Secure Boot UEFI Forbibben List (DBX)
- Restart the device
- Verify installation and revocation list was successfully applied
- Wait at least 5 minutes and then restart the device again
Scope of Impact on CVE-2023-24932 Windows Boot Manager Vulnerability
All Windows devices with Secure Boot protections enabled are affected by this issue, both on-premises physical devices and some virtual machines (VMs) or cloud-based devices. Protections are available for supported versions of Windows.
The Secure Boot bypass vulnerability identified by CVE-2023-24932 is not limited to Windows devices alone; this issue also impacts Linux systems. However, Microsoft has been working closely with representatives from leading Linux distributions to develop and distribute the necessary fixes to address this vulnerability for Linux users.
- Suppose you are a Linux user and believe your system may be affected. In that case, it is recommended that you contact the support team for your particular Linux distribution to obtain guidance on how best to mitigate this issue and implement the necessary protections for your device.
- By taking appropriate steps to secure your Linux system, you can help to minimize the risk of security breaches or other potentially damaging security incidents.
Avoiding Issues with Your Bootable Media
To avoid any issues with bootable media, it is important to ensure that the media has been updated with the security updates released on or after May 9, 2023. Failure to update the media may result in the device being unable to start after the revocations have been applied.
- This applies to all forms of bootable media, including discs, external drives, network boot recovery, and restore images.
- It is recommended to apply the necessary security updates before creating new bootable media or using existing ones.
Bootable Media Updated with the Security Updates
It is crucial to update your bootable media to ensure that the new boot manager and other necessary files are installed for starting your device after applying the mitigations. Updating the bootable media before using the revocations to your device is recommended.
Note! – It is important to note that the updated SKUSIPolicy.p7b file containing the revocations should not be applied on bootable media such as ISOs, USBs, DVDs, and other similar media. This file should only be used on your supported Windows devices after installing the updates released on or after May 9, 2023. Applying the SKUSIPolicy.p7b file on bootable media could result in issues and should be avoided.
Timing of Updates
The update timing includes the initial deployment, second deployment, and enforcement. The updates will be released on the following dates. It is important to note that the next release schedule might be revised later.
- Initial Deployment – The Initial Deployment is released on May 9, 2023, and provides basic mitigations.
- Second Deployment – The Second Deployment is released on July 11, 2023, which adds additional support to mitigate the issue.
- The final enforcement phase will make the mitigations permanent—tentatively scheduled for the first quarter of 2024.
PowerShell Script and Other Resources
Gary created a PowerShell script to fix the issue using SCCM CI and Intune Remediation script. More details on his solution are available on his GitHub page – garytown/ConfigMgr/Baselines/CVE-2023-24932 at master · gwblok/garytown · GitHub.
Resource – KB5025885: How to manage the Windows Boot Manager revocations for Secure Boot changes associated with CVE-2023-24932.
- Guide to Update the Windows PE add-on for the Windows ADK.
- Guidance for investigating attacks using CVE-2022-21894: The BlackLotus campaign – Microsoft Security Blog
- A sample script to extract and parse these logs is presented here, based on GitHub – mattifestation/TCGLogTools: A set of tools to retrieve and parse TCG measured boot logs.
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.

Hi Anoop, Thanks for Sharing. How can we create an SCCM Application with the detection method of Event viewer
Event ID:1035
Error message: Secure Boot DBX update applied successfully
Your assistance really appreciated.