Zero Day Security Vulnerability for Outlook is Fixed with March Patch, and more details are available now. This impacts all the versions of Windows Outlook clients (thick clients). This issue is regardless of where your mail is hosted (e.g., Exchange Online, Exchange Server, or some other platform).
Microsoft announced 2 Zero Day Security Vulnerabilities with Microsoft Outlook and Windows SmartScreen on March Patch Tuesday. CVE-2023-24880 and CVE-2023-23397 are the latest security vulnerabilities announced by Microsoft on 14th March 2023.
CVE-2023-24880 is Windows SmartScreen Security Feature Bypass Vulnerability, and it’s a publically disclosed vulnerability. Microsoft also confirmed that exploitation was detected for this vulnerability.
CVE-2023-23397 is Microsoft Outlook Elevation of Privilege Vulnerability and is not publicly disclosed. It’s already confirmed that the exploitation was detected.
Microsoft has released Windows 10 KB5023696 and Windows 11 KB5023706 + KB5023698 as part of patch Tuesday’s Latest Cumulative Update (LCU). And both these vulnerabilities have been fixed with the latest patches released for Outlook Client on March 14th.
Impacted Products with Zero-Day Outlook Client Vulnerability
Let’s check which are the impacted products for Zero-Day Outlook Client Vulnerability. As per Microsoft, all supported versions of Microsoft Outlook for Windows are affected.
There is NO impact for other versions of Microsoft Outlook such as Android, iOS, and Mac, as well as Outlook on the web and other M365 services.
| Outlook Versions | Impacted |
|---|---|
| Windows Outlook Client (Thick) | Yes – All supported versions are impacted |
| Android Outlook Client | NO |
| iOS Outlook Client | NO |
| macOS Outlook Client | NO |
| Outlook Web | NO |
| M365 services | NO |
Windows Autopatch – Office Update Configuration – Expedited
I thought of including additional details to this post with this, you can expedite updates of Microsoft 365 apps or Office Applications, including Outlook.
This is the Windows Autopatch configuration that you can check out from Office Update Configuration – Expedited policy. There are two policy settings configured, and those are Delay downloading and installing updates for Office and Update Deadline as discussed below.
NOTE! – Users that manage the Outlook desktop app using Windows Autopatch may be prompted to restart the application. Additionally, this update is a one-off remediation and will not appear in the next monthly update unless a similar case of immediate remediation is needed.
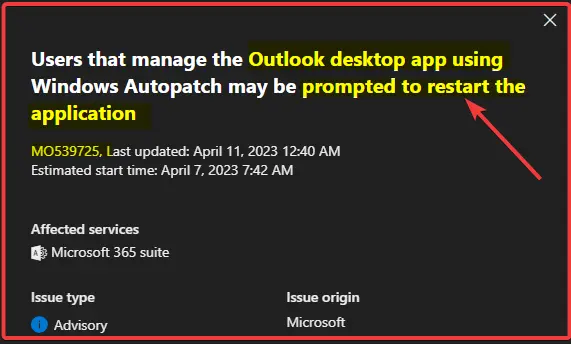
The Delay downloading and installing updates for Office policy setting allows you to delay downloading and installing updates for Office by a specified number of days. The maximum value that you can specify is 14. If you specify 0, Office will download and apply updates as soon as Office detects that updates are available.
The Update Deadline policy setting allows you to set a deadline by when updates to Office must be applied. You can set a deadline in one of two ways: Specify a date and time Specify a certain number of days after the update has been downloaded Prior to the deadline, users will receive multiple reminders to install the updates.
- Delay downloading and installing updates for Office – Enabled
- Days: (Device) – 0
- Update Deadline – Enabled
- Deadline: (Device) – 0
You can use the Settings Catalog (more details Create Intune Settings Catalog Policy). The search keywords you can use are the Policy Names mentioned above.
Autopatch to Update Office Apps Microsoft 365 Apps Updates
Let’s also quickly check how Autopatch can help to Update Office Apps or Microsoft 365 Apps. This Windows Autopatch service from Microsoft would be able to make sure that your Office apps are not updated with the latest patches.
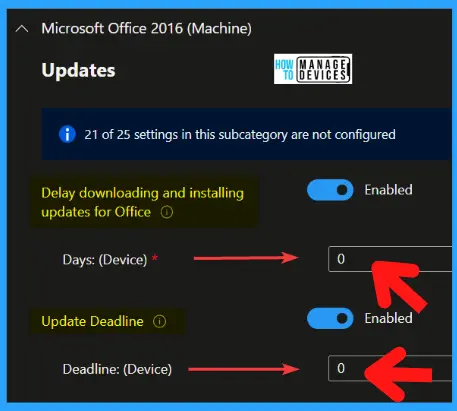
You can configure this Office Apps update from Autopatch – Devices – Release Management section. Microsoft 365 apps updates deployment will be managed by Autopatch service when set to Allow, Windows Autopatch will manage Microsoft 365 apps automatically. This helps you with Outlook Zero-Day vulnerabilities like this one.
NOTE! – To manage them yourself, select the switch to turn it off. You must be an Intune Administrator to make changes to the setting.
- You need to enable Autopatch as the first step. More details – Windows Autopatch Implementation Setup Guide.
- Navigate to Windows Autopatch from Intune Admin Center – Devices – Windows Autopatch.
- Click on Release Management – Release Settings to confirm Office Apps/Microsoft 365 Apps Autoupdate configurations.
Update Outlook Client Immediately
Let’s quickly update the Windows Outlook client to mitigate the issue immediately. You can open the Outlook client app and follow the steps. You can use SCCM or Intune (more details in the below section) to keep the Office applications up to date and fix this vulnerability.
- Select File -> Office Account -> Office Updates and select the Update Now button.

It’s time to download the updates from Microsoft Office CDN, Downloading the Outlook client updates. You can keep using the Outlook client while downloading Office Updates.
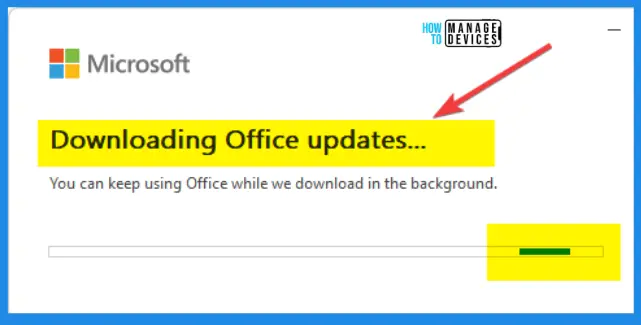
You need to close all Office applications including Word, Excel, PowerPoint, OneNote, and Outlook once the update is downloaded and ready for installation.
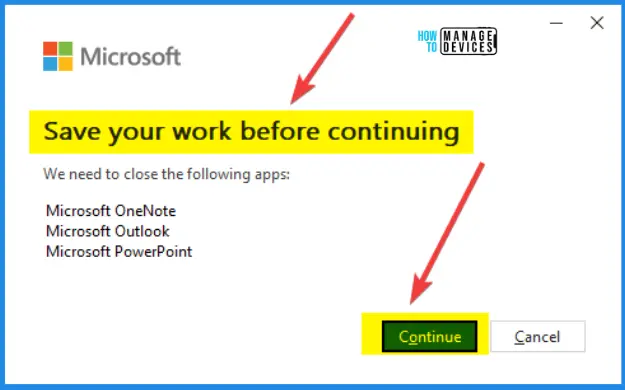
Applying Updates is happening. Wait for it completely.
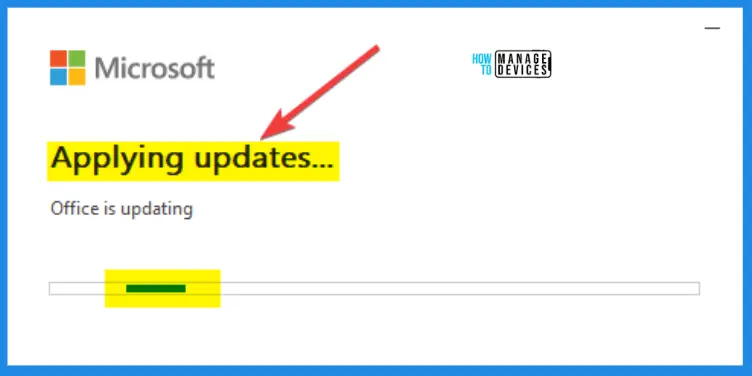
Office updates were installed. Your Office updates have been installed. You can use your Office apps now.

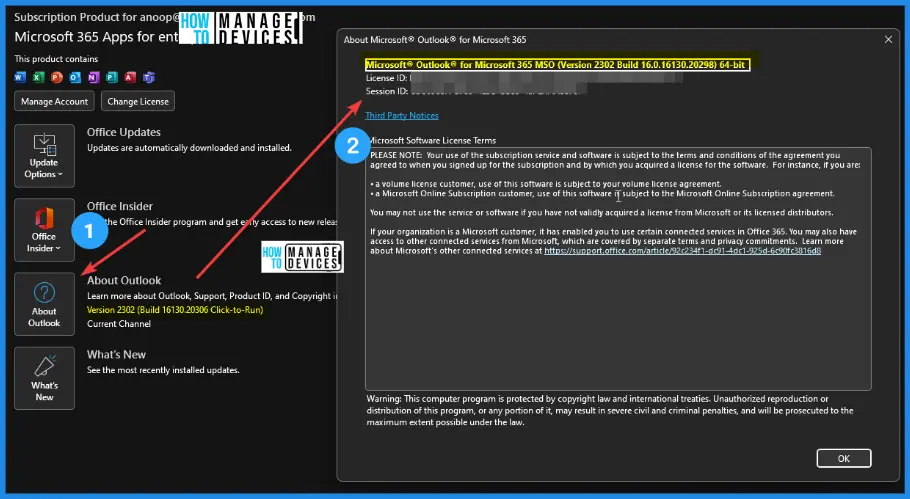
This is the latest version I got on my device. You can check the version by clicking Select File -> Office Account -> Office Updates and selecting the About Outlook button.
Microsoft® Outlook® for Microsoft 365 MSO (Version 2302 Build 16.0.16130.20298) 64-bit
Intune Policy to Force Office Apps to a Target Version
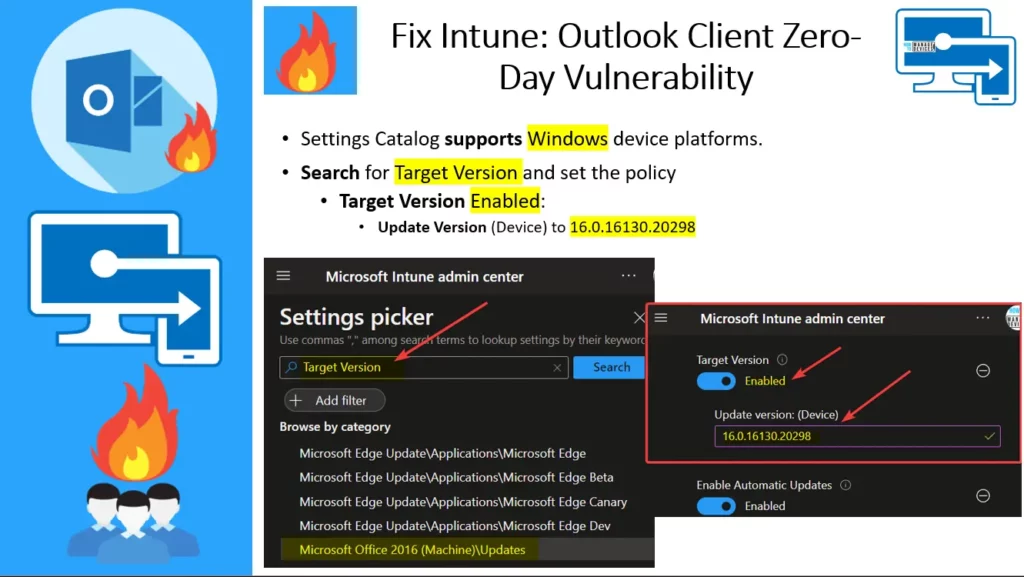
Let’s check the Intune Policy to Force Office Apps to a Target Version. You can use the Settings Catalog (more details Create Intune Settings Catalog Policy). Settings Catalog supports Windows device platforms.
NOTE! – You can also use the Custom Compliance policy in Intune to force users to update to the latest version of Office Apps. Once the users are updated to the latest version of Office Apps (including Outlook client), then only they can use the organization’s resources!
- Sign in to the Microsoft Intune admin center
- Select Devices > Configuration profiles > Create profile.
In Create Profile, You can select Platform: Select Windows 10 and later and Profile: Select Settings catalog (preview). Click on Create button. For Example – we have selected the platform Windows 10 and later.
- Search for Target Version and set the policy
- Target Version Enabled:
- Update Version (Device) to 16.0.16130.20298
There are other options as well, including the Intune proactive remediation scripts (additional licensing requirement), as discussed and added in the description of the following video. Let’s discuss FIX Outlook Client Vulnerability and Force Office Apps Update using Intune SCCM Manual Task Scheduler in this video.
Once the target version is set, the Task Scheduler Office Automatic Updates 2.0 (more details below section) will force the updates.
Force Office Auto Update using Task Scheduler
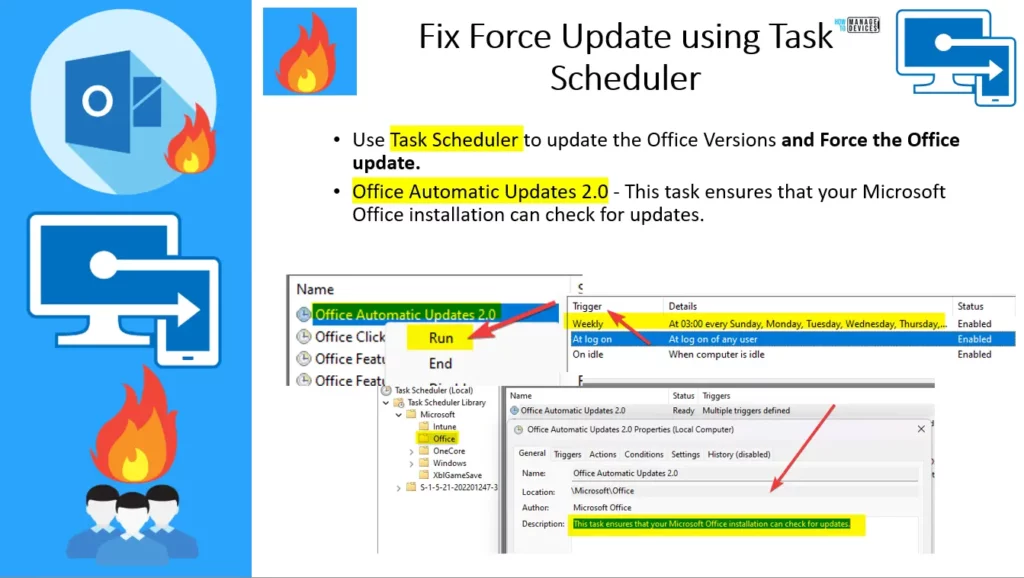
Let’s check how to use Task Seschuler to force Auto Update of Office Apps. If you didn’t change the target version using the Settings Catalog policy as discussed in the above paragraph, then you need to the registry change and RUN the scheduled Task called Office Automatic Updates 2.0.
- Clear the registry value
- Task Scheduler Clear the registry key: Go to \SOFTWARE\Microsoft\Office\ClickToRun\Updates.
- Double click- select the UpdateDetectionLastRunTime key, and delete the value data -OK.
Use Task Scheduler to update the Office Versions and Force the Office update. Office Automatic Updates 2.0 – This task ensures that your Microsoft Office installation can check for updates.
Windows Autopatch – Windows Update Detection Frequency
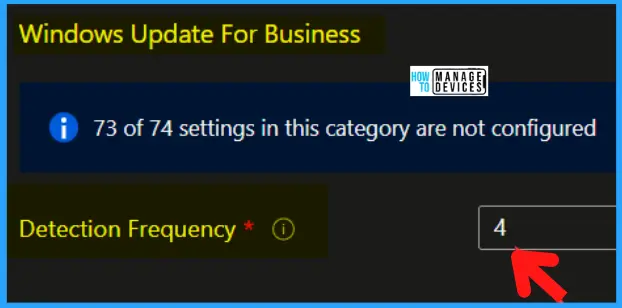
Let’s understand what is the use of Windows Autopatch – Windows Update Detection Frequency policy. This configuration profile sets Windows Update Detection Frequency. This policy is required by the Windows Autopatch service. Any changes you make to this policy will not be saved. Windows Autopatch will overwrite any changes.
The following policy specifies the scan frequency from every 1 – 22 hours. The default is 22 hours. You can use Settings Catalog Search Keyword Detection Frequency to find the policy.
- Detection Frequency = 4 Hours
Scripting – PowerShell to check Outlook Client Impact
Scripting options – PowerShell to check Outlook Client Impact of this issue. VE-2023-23397.ps1 is a script that checks Exchange messaging items (mail, calendar, and tasks) to see whether a property is populated with a UNC path.
If required, admins can use this script to clean up the property for items that are malicious or even delete the items permanently. Some of the examples are given below. You can download the PowerShell script from CVE-2023-23397 script – Microsoft – CSS-Exchange.
- Managing AzureADApplication: EXAMPLES:
This syntax runs the script to create an Azure application:
PS C:\> .\CVE-2023-23397.ps1 -CreateAzureApplicationThis syntax runs the script to delete the Azure application created by the script
PS C:\> .\CVE-2023-23397.ps1 -DeleteAzureApplication - Audit Mode: EXAMPLES:
This syntax runs the script to Audit all mailboxes in Exchange Online.
PS C:\> Get-Mailbox| .\CVE-2023-23397.ps1 -Environment "Online"
This syntax runs the script to Audit all mailboxes for items that were during a specific period.
PS C:\> Get-Mailbox | .\CVE-2023-23397.ps1 -Environment "Online" -StartTimeFilter "01/01/2023 00:00:00" -EndTimeFilter "01/01/2024 00:00:00"
- Cleanup Mode:EXAMPLES:
This syntax runs the script to clear the problematic property from messages.
PS C:\> .\CVE-2023-23397.ps1 -CleanupAction ClearProperty -CleanupInfoFilePath <Path to modified CSV>
This syntax runs the script to delete messages containing the problematic property.
PS C:\> .\CVE-2023-23397.ps1 -CleanupAction ClearItem -CleanupInfoFilePath <Path toCVE-2023-23397 Microsoft Outlook Elevation of Privilege Vulnerability
As per Microsoft, an attacker who successfully exploited this vulnerability could access a user’s Net-NTLMv2 hash which could be used as a basis of an NTLM Relay attack against another service to authenticate as the user.
The attacker could exploit this vulnerability by sending a specially crafted email that triggers automatically when it is retrieved and processed by the Outlook client. This could lead to exploitation BEFORE the email is viewed in the Preview Pane.
External attackers could send specially crafted emails that will cause a connection from the victim to an external UNC location of attackers’ control. This will leak the Net-NTLMv2 hash of the victim to the attacker, who can then relay this to another service and authenticate as the victim.
| CVE Number | CVE Title | Publicly Disclosed | Exploitability Assessment | Exploited | Details |
|---|---|---|---|---|---|
| CVE-2023-23397 | Microsoft Outlook Elevation of Privilege Vulnerability | NO | Exploitation Detected | Yes | CVE-2023-23397 |

Mitigation for Microsoft Outlook Elevation of Privilege Vulnerability
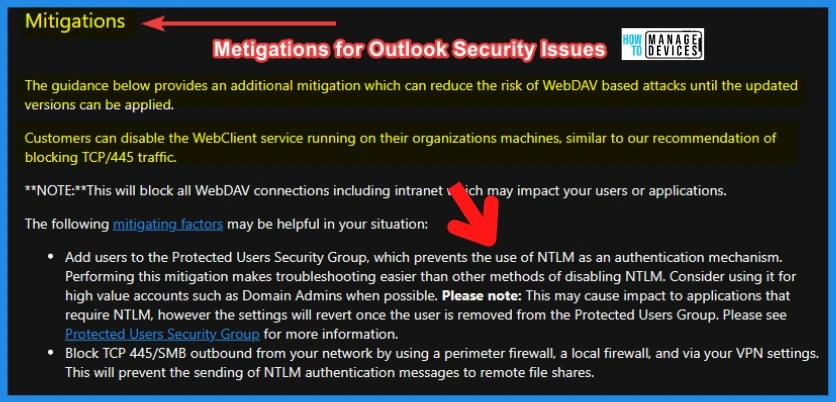
Add users to the Protected Users Security Group, which prevents the use of NTLM as an authentication mechanism. Performing this mitigation makes troubleshooting easier than other methods of disabling NTLM. Consider using it for high-value accounts such as Domain Admins when possible.
- The guidance below provides additional mitigation that can reduce the risk of WebDAV based attacks until the updated versions can be applied.
- Customers can disable the WebClient service running on their organization’s machines, similar to our recommendation of blocking TCP/445 traffic.
**NOTE:**This will block all WebDAV connections, including intranet, which may impact your users or applications.
- Please note: This may cause an impact on applications that require NTLM, however, the settings will revert once the user is removed from the Protected Users Group. More information Protected Users Security Group.
Block TCP 445/SMB outbound from your network by using a perimeter firewall, a local firewall, and via your VPN settings. This will prevent the sending of NTLM authentication messages to remote file shares.
CVE-2023-24880 Windows SmartScreen Security Feature Bypass Vulnerability
As per Microsoft, An attacker can craft a malicious file that would evade Mark of the Web (MOTW) defenses, resulting in a limited loss of integrity and availability of security features such as Protected View in Microsoft Office, which rely on MOTW tagging.
When you download a file from the internet, Windows adds the zone identifier or Mark of the Web as an NTFS stream to the file. So, when you run the file, Windows SmartScreen checks if there is a zone identifier Alternate Data Stream (ADS) attached to the file.
If the ADS indicates ZoneId=3, which means that the file was downloaded from the internet, the SmartScreen does a reputation check. For more information on SmartScreen Microsoft Defender SmartScreen overview | Microsoft Learn.
| CVE Number | CVE Title | Publicly Disclosed | Exploitability Assessment | Exploited | Details |
|---|---|---|---|---|---|
| CVE-2023-24880 | Windows SmartScreen Security Feature Bypass Vulnerability | Yes | Exploitation Detected | Yes | CVE-2023-24880 |
Author
About the Author – Anoop C Nair

Hi Anoop, this seems to be a update fix to the already known vulnerabilities..
https://www.bleepingcomputer.com/news/microsoft/microsoft-march-2023-patch-tuesday-fixes-2-zero-days-83-flaws/
OK. Thank you. This is not updated in the KB articles, though
1. https://support.microsoft.com/en-us/topic/march-14-2023-kb5023696-os-builds-19042-2728-19044-2728-and-19045-2728-9a6dafce-d387-410d-a1bc-9ff5a9cafdc1
2. https://support.microsoft.com/en-us/topic/march-14-2023-kb5023706-os-build-22621-1413-9d3f2de5-08e7-4462-8fba-d944201f4ae1
Or is this part of Office patches?
Thanks for the awesome post as usual, Anoop!
Can you confirm if the Office 2016 (Machine) policies require Enterprise version of Windows?
We are seeing a 65000 error in Intune typically related to ADMX/license entitlement
Oops … probably there is some support issue with this deployment? Have you already raised any support ticket with Microsoft? What is the Build number that you used in the policy.
Have you already checked the remediation script option that is mentioned in the video description?
Also can you share the error details from event logs?
Anoop i dont manage office updates through sccm as we let them auto update. if i want to turn it on to force the patch down, will turning off the setting in sccm after for office to go back to checking in online normally or will there have to be other remediation to get that to work?
Try to check the option mentioned in the Task Scheduler section of the post. You can find out a script to clean the registry and let the task scheduler do the rest of the work.
Hi Anoop,
As per your instructions, I created the Config profile in Intune, but users are getting Version 2302 Build 16.0.16130.20186.
Am I missing anything?
Hi, can you share the error details from the event logs?
There is no error message. Intune is showing that the device got the update. But building is not the same.
Have you checked the Task Scheduler section mentioned in the post? Try to run the Task Scheduler Office Automatic Updates 2.0 mentioned there. Also, check when is the last time that TS triggered.
Maybe tou need tô check your office Channel,
Sorry for my english