This post will help you create the Intune Audit User Account Management Policy. We are using Intune’s Settings Catalog to install this policy and using Intune’s Configuration Profiles to create it.
Audit User Account Management Policy logs every occurrence of user account management events, including the creation, modification, or deletion of a user account and activities such as renaming, disabling, enabling, and setting or changing passwords.
Enabling this Audit policy setting allows administrators to monitor these events, aiding in identifying potentially malicious, accidental, or authorized activities related to creating user accounts. Events within this subcategory include:
- 4720: A user account was created.
- 4722: A user account was enabled.
- 4723: An attempt was made to change an account’s password.
- 4724: An attempt was made to reset an account’s password.
- 4725: A user account was disabled.
- 4726: A user account was deleted.
- 4738: A user account was changed.
- 4740: A user account was locked out.
- 4765: SID History was added to an account.
- 4766: An attempt to add SID History to an account failed.
- 4767: A user account was unlocked.
- 4780: The ACL was set on accounts that are members of administrators groups.
- 4781: The name of an account was changed:
- 4794: An attempt was made to set the Directory Services Restore Mode.
- 5376: Credential Manager credentials were backed up.
- 5377: Credential Manager credentials were restored from a backup.

Audit User Account Management Policy
To create an Audit User Account Management Policy, follow the steps stated below:
- Sign in to the Intune Admin Center portal https://intune.microsoft.com/.
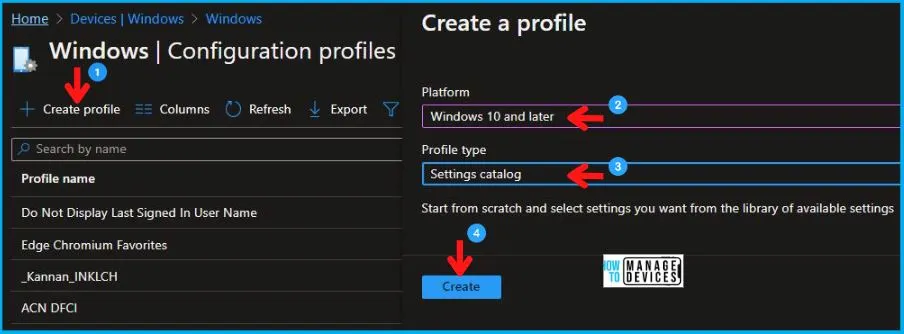
- Select Devices > Windows > Configuration profiles > Create a profile.
In Create Profile, I select Windows 10 and later in Platform, I choose the Profile Type as Settings catalog. Click on the Create button.
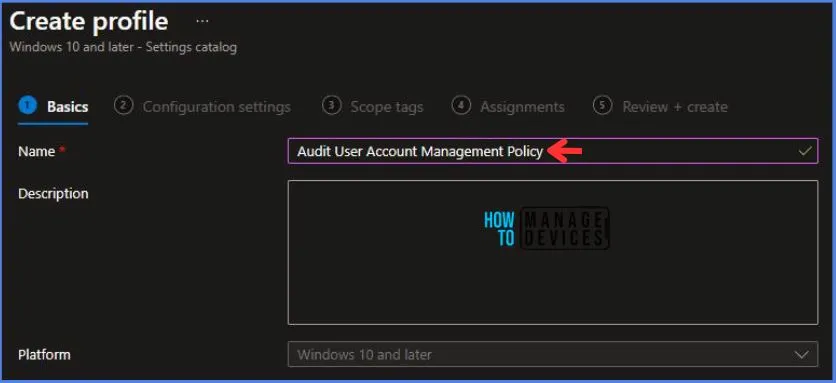
On the Basics tab pane, I provide a name for the policy as “Audit User Account Management Policy.”
- Optionally, if you want, you can enter a policy description and proceed by selecting “Next“.
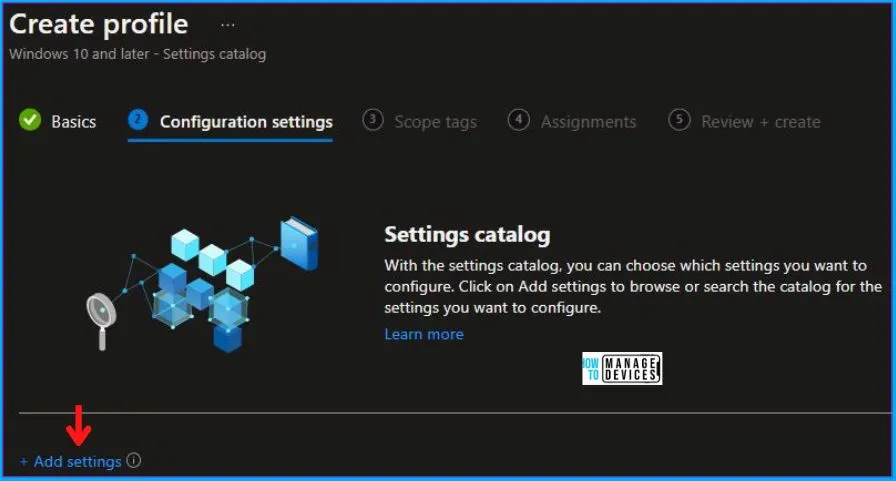
Now, in Configuration Settings, Click Add Settings to browse or search the catalog for the settings I want to configure.
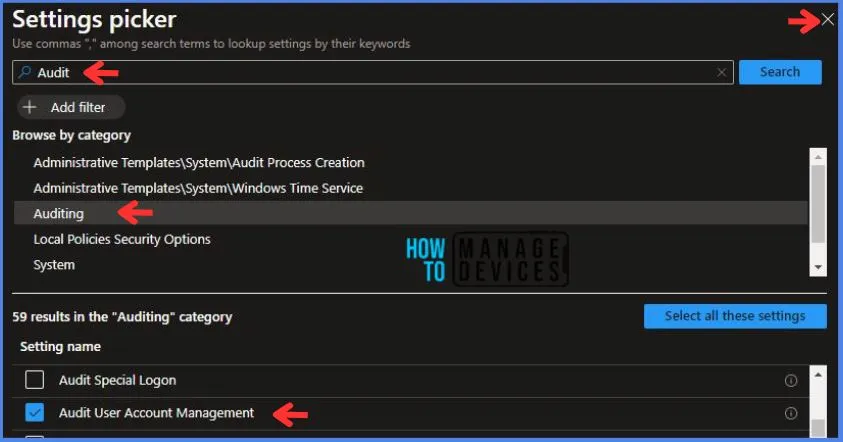
In the Settings Picker windows. I searched for the keyword Audit. I found the category Auditing and selected this.
- I see the sub-category Audit User Account Management. After selecting that, click the cross mark at the right-hand corner, as shown below.
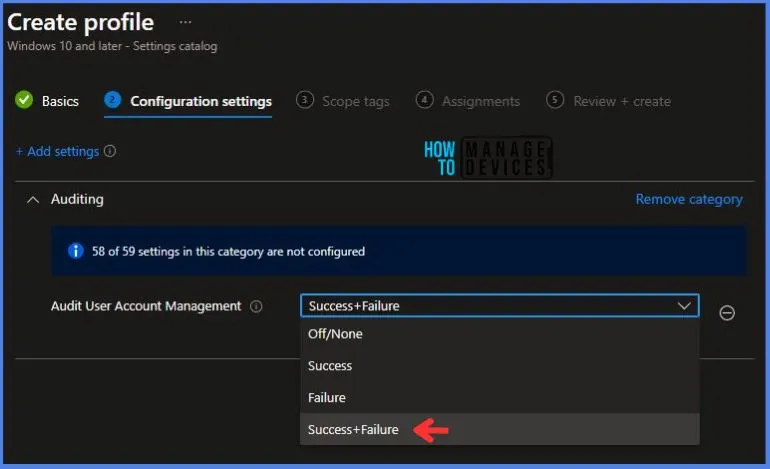
Here in Auditing, the Audit User Account Management setting has multiple options:
- Off/ None
- Success
- Failure
- Success + Failure
As a recommended state, here I am choosing Success + Failure.
Using Scope tags, you can assign a tag to filter the profile to specific IT groups. One can add scope tags (if required). More details on Intune Scope Tags Implementation Guide.
- Click Next to continue.
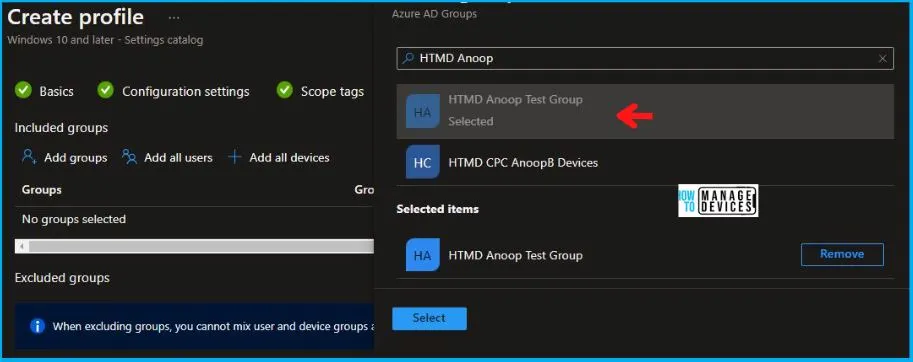
Now in Assignments, in Included Groups, you need to click on Add Groups and choose Select Groups to include one or more groups. Click Next to continue.
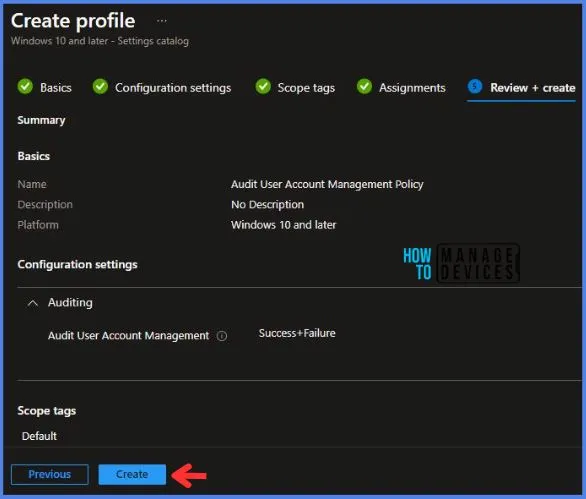
In the Review + Create tab, I review settings. After clicking on Create, changes are saved, and the profile is assigned.
After successfully creating the “Audit User Account Management Policy,” a notification will appear in the top right-hand corner confirming the action. You can also verify the policy’s existence by navigating to the Configuration Profiles list, where it will be prominently displayed.
Your groups will receive your profile settings when the devices check in with the Intune service. The Policy applies to the device.
Intune Report for Audit User Account Management Policy
From the Intune Portal, you can view the Intune settings catalog profile report, which provides an overview of device configuration policies and deployment status.
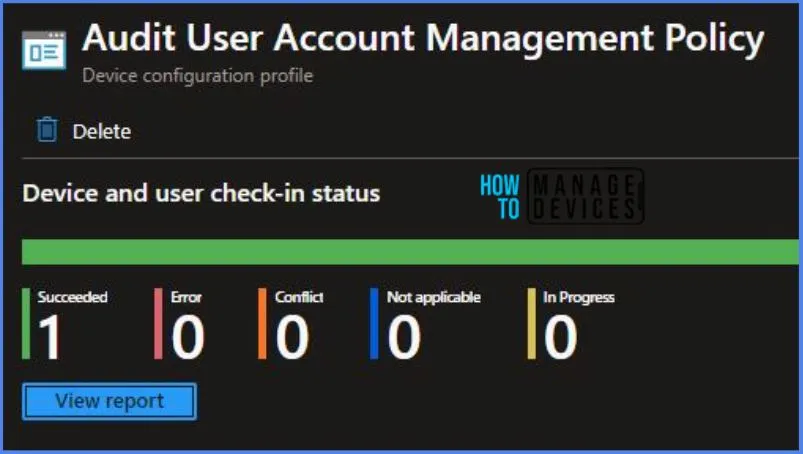
To track the policy’s assignment, you need to select the relevant policy from the Configuration Profiles list, which is the Audit User Account Management Policy. Then, you can review the device and user check-in status to determine whether the policy has been successfully applied.
- If you require more detailed information, you can click on “View Report” to access additional insights.
Registry Key Verification – Audit User Account Management Policy
Now we will verify whether the policy was successfully deployed or not by accessing the registry settings that will hold the group policy configurations on a specific computer. To accomplish this, you can execute “REGEDIT.exe” on the target computer and navigate to the precise registry path mentioned below, where these settings are stored.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\5B88AEF1-09E8-43BB-B144-7254ACBBDF3E\default\Device\Audit
When you navigate the above path in the Registry Editor, you will find the registry key named
