Joymalya Basu Roy
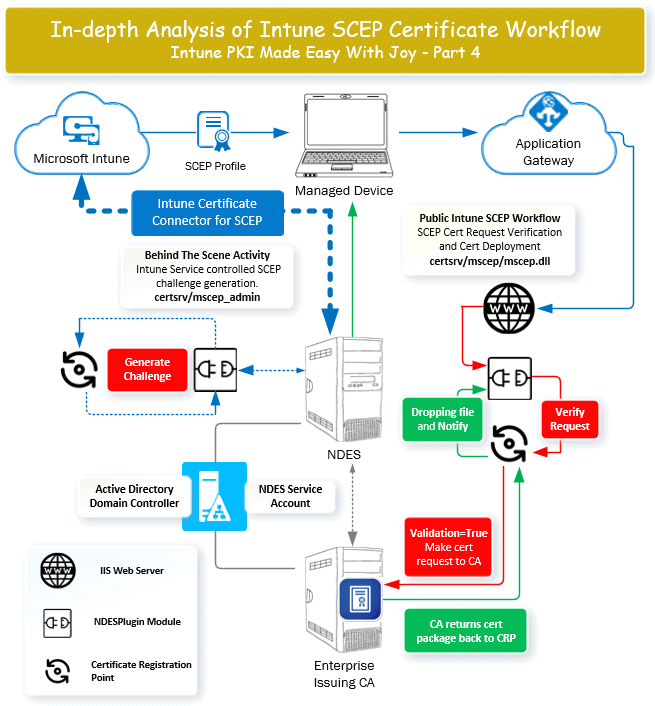
Intune SCEP Certificate Workflow Analysis – Intune PKI Made Easy With Joy – Part 4
[New Post Alert!] Intune SCEP Certificate Workflow Made Easy With Joy – Part 4
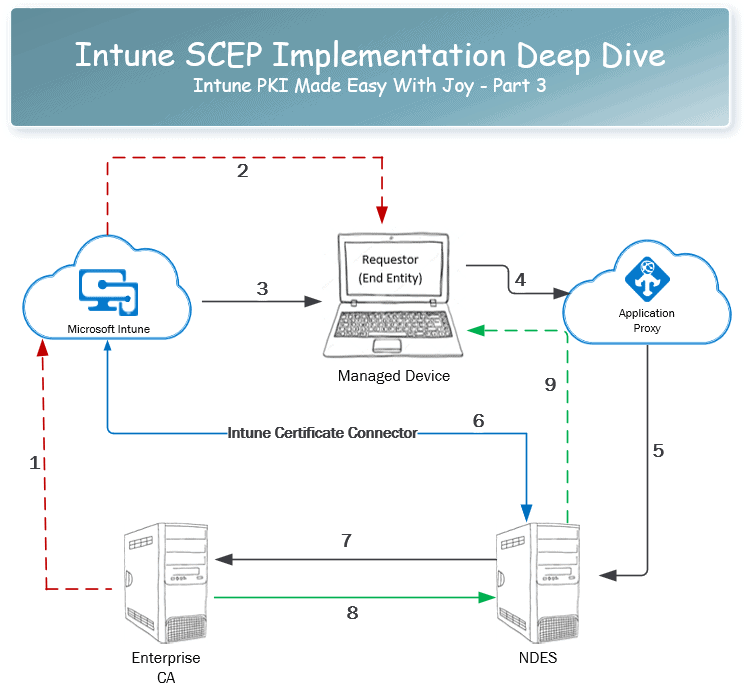
Intune SCEP Deep Dive – Intune PKI Made Easy With Joy – Part 3
[New Post Alert!] Intune SCEP Implementation Deep Dive – Intune PKI Made Easy With Joy – Part 3
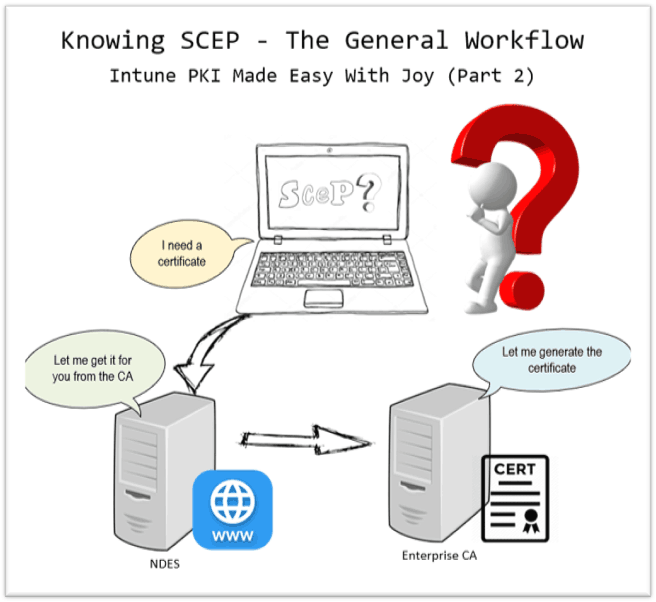
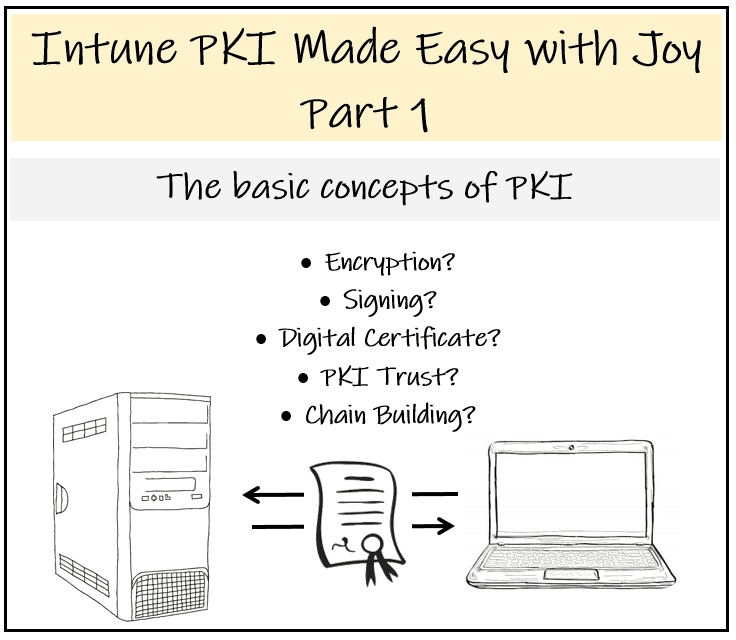
Learn The Basic Concepts of PKI – Intune PKI Made Easy With Joy Part-1
[New Post Alert!] Learn the Basic Concepts of PKI – Intune PKI Made Easy with Joy (Part 1)

![Android Enterprise: An Ultimate Use-case Guide for the Different Management Modes Available with Intune [3] 2 Android Enterprise management modes available with Intune](https://www.anoopcnair.com/wp-content/uploads/2020/11/AEMEMJoyCover-768x432.png)

![Android Enterprise Dedicated Devices in Azure AD Shared Device Mode - Learn Intune with Joy 5 [Cover Image] Android Enterprise Dedicated device Azure AD Shared mode provisioning - Learn Intune with Joy](https://www.anoopcnair.com/wp-content/uploads/2020/11/aededsharedcover-768x432.png)