Let’s check how to Manage Local Admins using Intune Local User Group Membership Management Policy. There are many ways to manage Local groups on Azure AD Joined Windows 11 or Windows 10 PCs. However, the new Intune MEM policy helps to manage local groups using the native MDM channel.
Local user group membership policies help MEM admin to add, remove, or replace members of local groups on Windows devices. You can manage Local groups with on-prem domain Users/Groups and Azure AD Users/Group SIDs.
I recommend using the SID option wherever possible in the Local user group membership policy. The SIDs will help to avoid regional language issues with Local Group Names. You can use the group name as Administrators for English language Windows PCs but not for French or German Language PCs.
NOTE! – I have not tested the LOCAL Administrator account with non-English language to confirm whether this works fine without any SIDs. I think this is already taken care of by this workflow. There could be a chance that this CSP and workflow might work without SIDs as well for the local administrator scenario.
The local user group management policy in Intune is based on a policy CSP called LocalUsersAndGroups policies. The RestrictedGroups/ConfigureGroupMembership policy setting allows you to configure members (users or AAD groups) to a Windows 10 or Windows 11 local group.
- Collect Intune Logs from MEM Portal Diagnostic Data
- Intune Logs Event IDs IME Logs Details for Windows Client Side Troubleshooting
- Intune Audit Logs Track Who Created Updated Device Compliance Policy
Create Local User Group Membership Policy to Manage Local Admins using Intune
Let’s learn how o create a local user group membership policy to manage local admins of Windows 10 or Windows 11 devices. This local user group membership policy is supported for Hybrid Azure AD joined, and Azure AD joined devices.
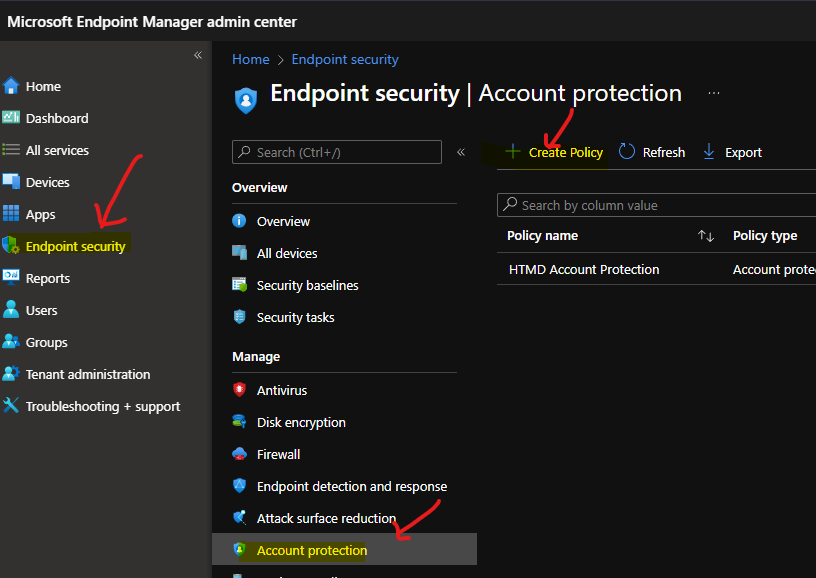
To create a local user group membership policy, you will need to login into the endpoint.microsoft.com portal.
- Navigate to Endpoint Security tab.
- Scroll down and on Account Protection tab.
- Click on +Create Policy button to start the policy creation process.
Starting from Windows 10, version 20H2, it is recommended to use the LocalUsersandGroups policy instead of the RestrictedGroups policy.
- From the create a profile blade – Select Windows 10 and later as the platform.
- Select Local User Group Membership as profile.
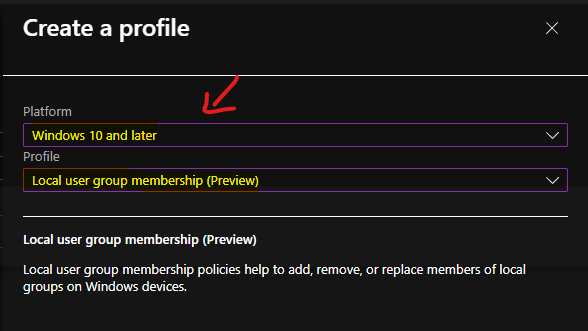
Enter the Name and description of the local user group membership management policy from Intune.
- Name – Manage Local Administrators Group
- Description – This policy is to manage Local Administrators Group
Click on the Next button to continue.
Video Tutorial Intune Policies for Managing Local User Groups
Let’s check the video tutorial – Intune Policies for Managing Local User Groups for Azure AD Joined Devices | Hybrid Azure AD Joined.
Supported Local User Groups
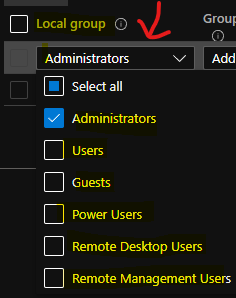
Only six (6) local user groups are supported with the Local User Group Management policy. You will need to select any of the following local user groups to manage the membership. You can use any of these groups to remove or add members.
- Administrators
- Users
- Guests
- Power Users
- Remote Desktop Users
- Remote Management Users
NOTE! – This policy allows only for a full replacement of the existing groups with the new members and does not allow selective add or remove.
You can have only ONE LocalUserAndGroups policy deployed to a Windows Device. If you deploy more than one local user group membership policy to the same devices, it will create a Conflict error in Intune.
Local Group and User Actions – Management
There are two actions available for the Local User group management policy. In the XML and event logs, you would be able to see the two actions as U (Update) and R (Replace/Restrict).
- Update action must be used to keep the current group membership intact and add or remove members of the specific group.
- Restrict action must be used to replace current membership with the newly specified groups.
NOTE! – The Restrict action provides the same functionality as the RestrictedGroups/ConfigureGroupMembership policy setting.
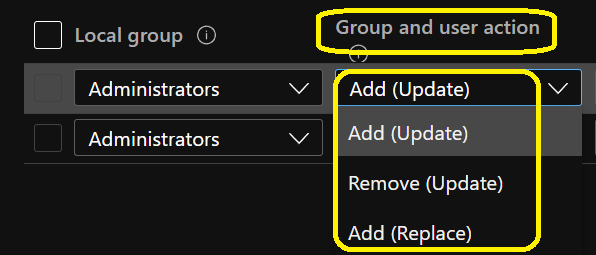
The Intune MEM portal has the following list of Group and User Action in place. You can check the options below.
- Add (Update): Adds members to specified group while keeping the current group membership intact.
- Remove (Update): Removes members of specified group while keeping the current group membership intact.
- Add (Replace): Replaces current membership of specified group with newly specified group.
Azure AD Joined Scenario – Add Azure AD Users/Groups to Local User Group
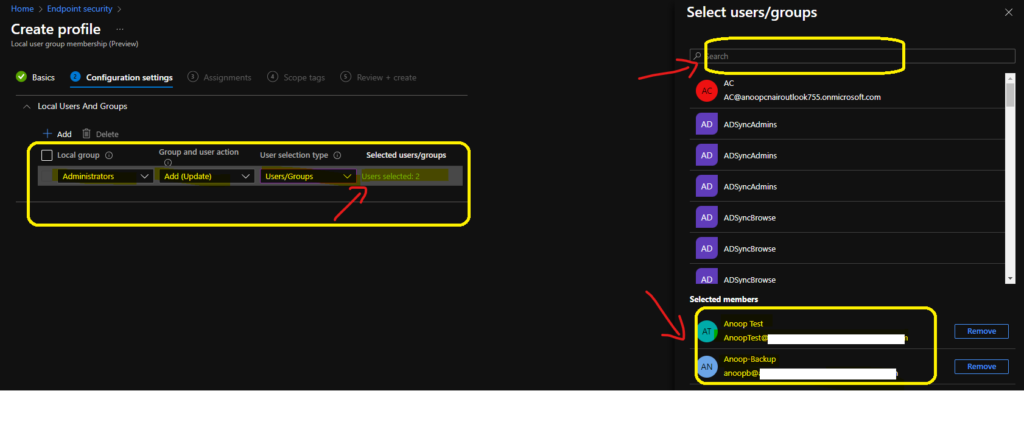
I have selected the add (update) option to add new members to the local user group. To add Azure AD Users/User Groups into Windows 10 or Windows 11 local user groups, you must select Users/Groups from User Selection Type.
Now, click on the Users under selected users/groups to choose the Azure AD users/groups from the search menu below. Click on the Select button to continue.
Hybrid Azure AD Joined – Add Domain Users or SIDs to Local User Groups
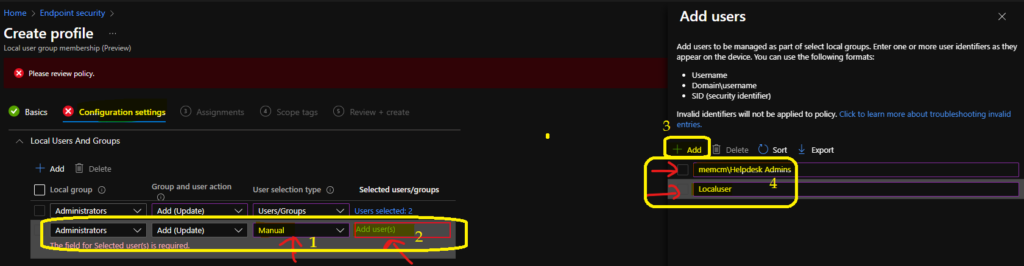
Add users to be managed as part of select local groups. Please enter one or more user identifiers as they appear on the device. You can use the following formats:
- Username
- Domain\username
- SID (security identifier)
You have to select the Manual option from the drop-down menu under the User Selection type. Once selected, click on the link to manually add SIDs/User Names/Group Names of on-prem active directory to Hybrid Azure AD Windows 10 and Windows 11 PCs.
Click on the OK to continue.
Now, you can click on the Next button.
Click on the Next button. From this page, you can perform the assignment actions. I have added the Local User group Management policy to two Azure AD device groups.
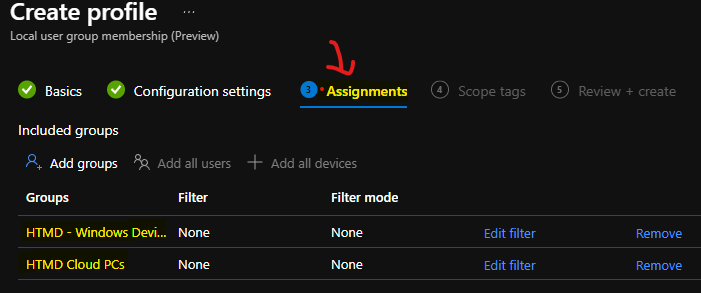
You can click on the Create button to complete the Manage Local Administrators Group policy.
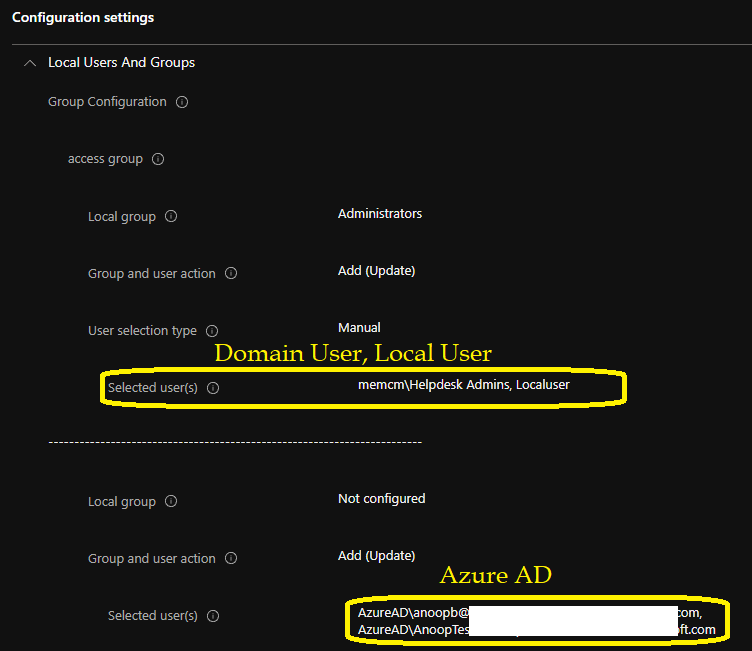
Group Configuration
Access group
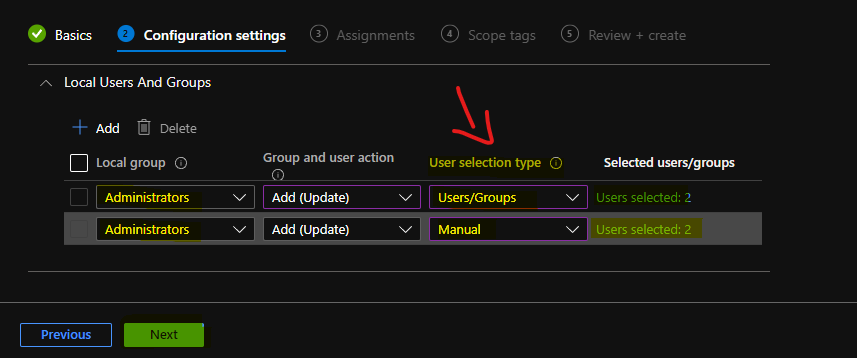
Local group – Administrators
Group and user action – Add (Update)
User selection type – Manual
Selected user(s) – memcm\Helpdesk Admins, Local User
Local group – Not configured
Group and user action – Add (Update)
Selected user(s) – AzureAD\anoopb@aoft.com, AzureAD\AnoopTest@aoft.com
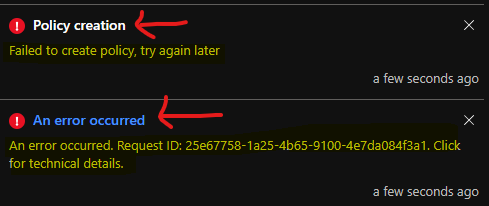
Local Admin Management Policy Creation Failed
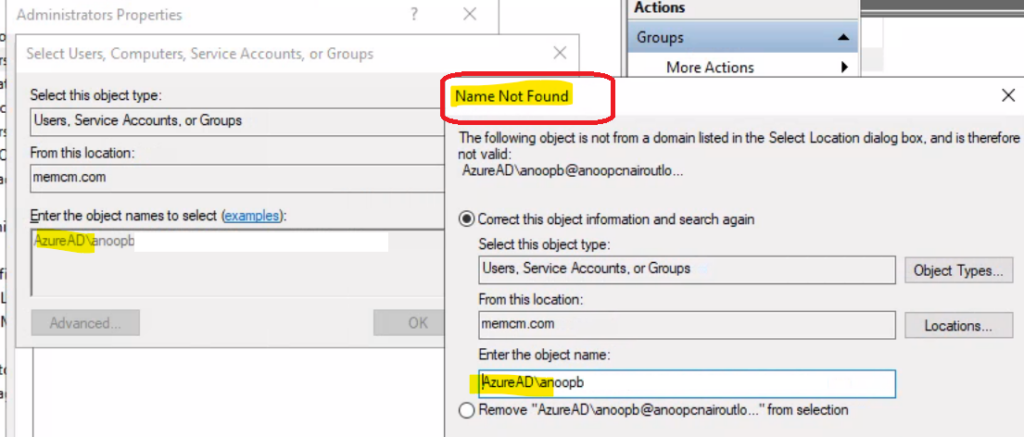
Local Admin Management Policy creation using local user group membership policy is failed. This policy creation error was mostly because Local Group was shown as NOT Configured on the review page as shown above. This is strange because, in the above screenshot, you can see I have selected the Administrators as the local group name for both.
I deleted the entry that is under the User Selection Type – Manual. And added back to fix the issue with policy creation.
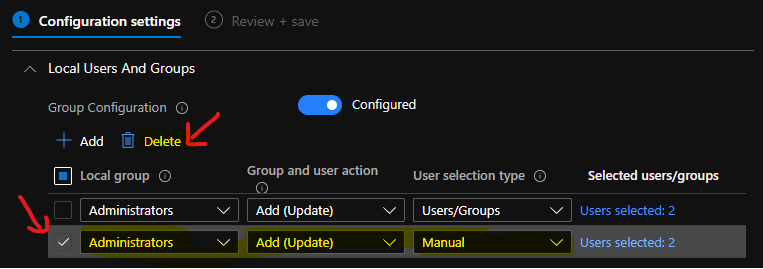
Now, you can see that the local user membership management policy creation issue was fixed, and the policy was successfully created.
Local User Group Management Policy Error 0x80070534
I have received 3 errors with the local user group management policy. I tried this with Cloud PC, and this is a Hybrid Azure AD joined PC. The error 0x80070534 is because of lookup failures.
It seems the name/SID lookup failed for Azure AD users and Local Users. Hence the event log errors as explained below. If there are multiple errors, the last error is returned at the end of the policy processing.
Event Log path for Intune logs – > Applications and Services -> Microsoft->Windows->DeviceManagement-Enterprise-Diagnostics-Provider->Admin
Event ID 806 – MDM PolicyManager: Merge string, Area: (LocalUsersAndGroups), Policy: (Configure), EnrollmentID requesting merge: (A2866686-F537-49AD-86C6-0038967B86C9), Result:(0x80070534) No mapping between account names and security IDs was done..
Event ID 821 – MDM PolicyManager: Merge of policy did not complete successfully, Policy: (LocalUsersAndGroups), Area: (Configure), Result:(0x80070534) No mapping between account names and security IDs was done.
Event ID 810 – MDM PolicyManager: Set policy string, Policy: (Configure), Area: (LocalUsersAndGroups), EnrollmentID requesting set: (A2866686-F537-49AD-86C6-0038967B86C9), Current User: (Device), String: ( ), Enrollment Type: (0x6), Scope: (0x0), Result:(0x80070534) No mapping between account names and security IDs was done.
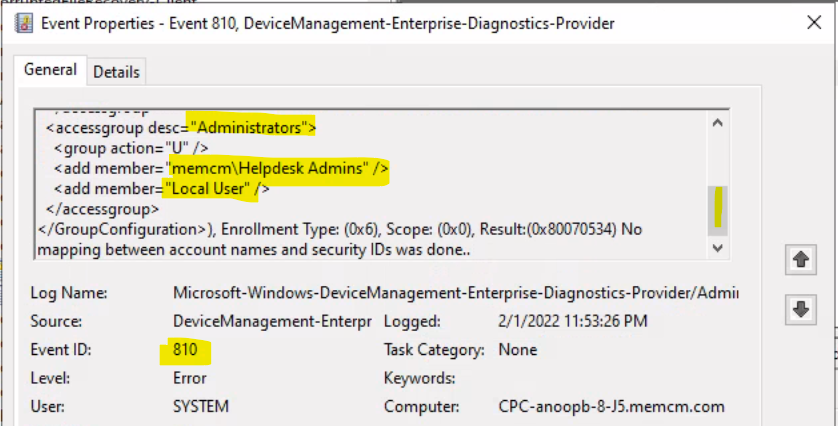
Event ID 404 – MDM ConfigurationManager: Command failure status. Configuration Source ID: (A2866686-F537-49AD-86C6-0038967B86C9), Enrollment Name: (MDMDeviceWithAAD), Provider Name: (Policy), Command Type: (Add: from Replace or Add), CSP URI: (./Device/Vendor/MSFT/Policy/Config/LocalUsersAndGroups/Configure), Result: (No mapping between account names and security IDs was done.).
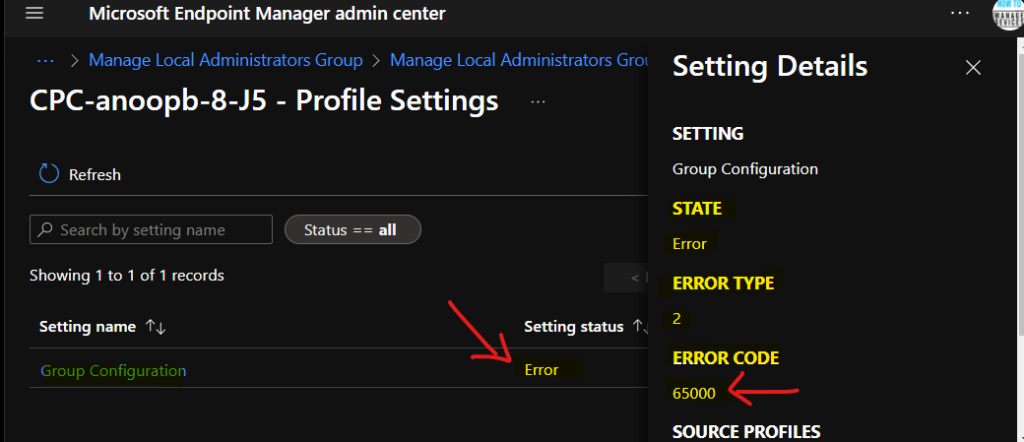
Intune Error Code 6500 and Fix
I see the Intune error code 6500 when I looked at Intune reports for the local user group membership policy that I have created above. It’s because of the oblivious reasons mentioned below. I explained the issue related to Manage Local Admins using Intune Local User Group Membership Management Policy.
Group Configuration
STATE – Error
ERROR TYPE – 2
ERROR CODE – 65000
You should create a separate local user group membership policy for Hybrid Azure AD joined and a separate one for Azure AD joined Windows 11 or Windows 10 devices. This will help to avoid the above-mentioned errors in Intune.
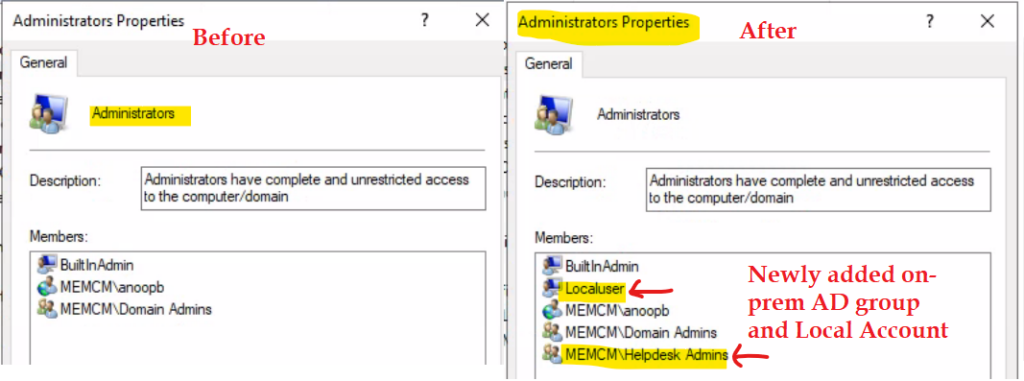
As you can see in the results, the memcm\Helpdesk Admins on-prem Active directory group is added to the local administrators group. Adding the Azure AD user accounts is failed because this is Hybrid Azure AD joined Windows PC.
You can add Azure AD User or Group only to the Local user group of Windows 11, or Windows 10 Azure AD joined device.
I need to perform more tests to understand how the Azure AD joined scenario works with the local user group management policy with Intune. I’ll update the post once I have tested the Manage Local Administrators Group policy.
The “Local User” account configured above didn’t get added to the local Administrators group because of the typo in the policy configuration. The actual Local user account name is LocalUser (there is no space in between).
Result
You can launch CompMgr.msc from the run menu to confirm whether the local user and on-prem AD group are added to the Local Administrators group. The best method to manage the local user group membership is to use Intune policy explained in this post.

Hello Anoop!!!
There is a point that I’d like to clarify. You suggest to use the SIDs to avoid regional language issues with Local Group Names and that’s fine; but what about local Administrator account ? The name is different depending on OS language and it isn’t possible to use its SID because changes on every device. Any advice ?
Hi Luca – I know what you meant I have seen issues with a local administrator account. I have updated the post with the following note.
I have not tested the LOCAL Administrator account with non-English language to confirm whether this works fine without any SIDs. I think this is already taken care of by this workflow. There could be a chance that this CSP and workflow might work without SIDs as well for the local administrator scenario.
Hello Anoop C Nair,
reading this Microsoft TechCommunity article: https://techcommunity.microsoft.com/t5/intune-customer-success/new-settings-available-to-configure-local-user-group-membership/ba-p/3093207 it seems the issue for with a non-english OS will be fixed with ~2204 release (April 2022).
Hello Anoop,
reading this Microsoft TechCommunity article: https://techcommunity.microsoft.com/t5/intune-customer-success/new-settings-available-to-configure-local-user-group-membership/ba-p/3093207 it seems the issue with a non-english OS will be fixed with the ~2204 release (April 2022).
Thank you for the comment. Indeed I have noticed that a few days before but didn’t get time to update the post.
Hi Anoop
I would like to make a more generic option where I would like to add the current logged in user to the adminstartor group. By this theory, i could then assign the polciy to a group of machines but only the logged on user on that specifc device would get added to the admin group. Something like: Selected user(s)
AzureAd\%username%@domain.com
Do you know if that is possible, or I would need to assign policy multiple times for each device?
Our machines are Azure joined devices. When we try to use Add (Replace) on Administrator group, it is not working. With the OMA-URI, we can do /R and add Administrator user. https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localusersandgroups. Any advice on this ? We don’t want to use OMA since it can’t handle non English OS where we need to have different config for each language.
Hi Anoop,
I have deployed this policy only to Hybrid but still getting same Error for many devices:
SETTING
Group Configuration
STATE
Error
ERROR TYPE
2
ERROR CODE
65000
SOURCE PROFILES
can you advise please
Yes of course check out the event logs on a client to understand the details of this error. More detail -> https://www.anoopcnair.com/intune-logs-event-ids-ime-logs-troubleshooting/
Hi Anoop and fellow admins,
did you got this policy working for “Remote Desktop Users” by any chance?
We are currently trying to use this policy to enable only a specific AAD group of users to remotely connect to a specific machine which works to a certain point were the SID is visible in the local group but RDP does not seem to be able to resolve it properly.
When adding the same group members manually to that local “Remote Desktop Users” group it will work. Your thoughts would be highly appreciated 😉
Hello everyone,
I’ve set my policy to Remove the user who joined the device in Azure AD from the admin group so that they don’t have local admin permissions and in Intune I see the policy status as OK, even when I go to view the admin group in my devices, I no longer see the user I deleted with my policy, i.e. the user who enrolled the device, should no longer have local admin permissions, is that correct? However, it still has the permissions and they are only changed when I log out or restart the device. Is this normal behavior? Will it only work after reboot or logout?
Hi,
May I ask you if I will create local account on machine by UserName what will be the password for this account is there any option how to set password for this account ?
Hi, This policy is not to create local accounts but manage local admin permissions. A local account must be created using some other process.
Hi Anoop,
I am trying to change existing local administrator password through Intune. I got some script to achieve this but that would be a security breach as script has tobe hard coded with password.
Please suggest if you have any solution to this.
Hu Anoop,
Need your help.
I looking for a Script to create local admin user with secure password, with option password never expires. Need this local user to elevate user during remote session using logmein.
Please guide me for this.
Hello, this is great however I would like to be able to get information from an AAD joined Windows 10 device. Specifically what accounts are members of the local administrators group. How can I do that with Azure AD or MEM admin center? Or is there another admin center I need to use for this?
Dear Anoop,
Thank you kindly for the amazing guide!
May i know whether it is technically possible to add the “domain admins” builtin AD group to the local administrators , as well? Or whether there’s some prerequisites required for it or even workarounds.
I followed your guide precisely, I added “domain\Domain Admins” in the policy with the “manual” value –> I get no errors in event viewer, the “domain admins” group appears in the local admininistrators group “visually”, but none of the members of the domain admins have any admin privileges on the machine.
I forgot to mention that i am using a hybrid joined machine.
Also, i see in your screenshots that domain admins group is already added, is it supposed to be there by default?
Hi Anoop, thanks for that great articel, solved a problem for me I have been long trying around with.
In general I like your articles, I appreciate your efforts and your knowledge.
Thanks and greetings
Thorsten