Let’s check to understand Intune logs for Windows 10 and Windows 11 PCs. Intune is a SaaS (software as a service) solution, and I have not seen any Intune server-side logs. The server-side troubleshooting is mostly managed by Microsoft support.
The Intune client-side logs are one of the options you can troubleshoot issues. The other option to troubleshoot Intune issues from the client-side is using network traces. This is basically reverse engineering using Fiddler traces etc…
Some of the Intune server-side details are available through various reporting nodes in Intune portal. You can perform the basic Intune user policy deployment troubleshooting from the MEM admin center portal. You can directly collect Intune logs from the MEM Admin center portal using the Collect Intune Logs from the MEM Portal Diagnostic Data guide.
One example is given below How To Start Troubleshooting Intune Issues from the server-side. The next level of troubleshooting is with MDM Diagnostics Tool to collect the log and information from the client side.
We can divide Intune logs into two parts. One is the logs related to Intune Management Extension (IME), and the other section of the logs is related to Windows MDM event logs. Moreover, you can’t compare SCCM logs with Intune logging options.
- Intune User Policy Troubleshooting Tips For Prevent Changing Theme
- Intune Win32 App Deployment Troubleshooting Help Guide
- Intune Security Baseline Microsoft Defender Policy Troubleshooting Tips
- Troubleshoot Microsoft Edge Security Policy Deployment Issues
Intune Advanced Diagnostic Report
I recommend starting collecting Intune logs from the Windows 10 or Windows 11 settings app. This report shows the applied configuration states of your device, including Policy CSPSettings, certificates, configuration sources, and resource information.
How to collect Intune Advanced Diagnostic Report from Windows PCs:
- Go to the Settings app from the Start menu or button.
- Click on Accounts.
- Click on Access School or Work from the Accounts page.
- Click on the Azure AD account that you want to collect the logs/report for.
Diagnostic Report will be stored -> C:\Users\Public\Documents\MDMDiagnostics

Intune Logs in Windows – Management Logs
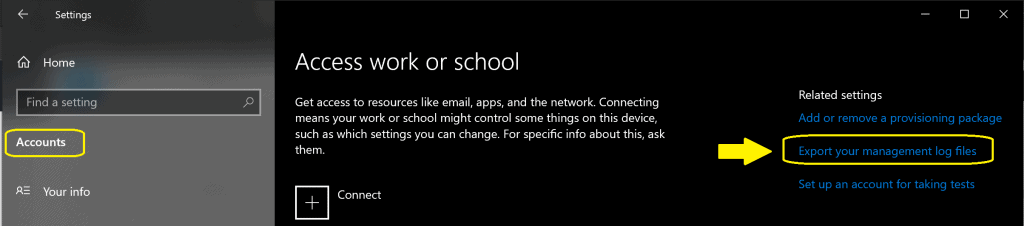
We have an option to collect all the Intune-related logs from a Windows PC. You can collect all the Intune management logs from the settings -> Accounts -> Access School or Work.
You can click on Export your management log files. The logs file will get stored in the same location as Intune diagnostic reports. Some of the log files collected during this process are given below.
C:\Users\Public\Documents\MDMDiagnostics ==> MDMDiagReport.cab (You can extract cab file to check the logs).
NOTE! – Command line option for getting Intune MDM Diag Log –
mdmdiagnosticstool.exe -area DeviceEnrollment;DeviceProvisioning;Autopilot -zip c:\users\public\documents\MDMDiagReport.zip
AgentExecutor.log, AutopilotConciergeFile.json, AutopilotDDSZTDFile.json, ClientHealth.log, DeviceHash_DESKTOP-EQI637E.csv, DiagnosticLogCSP_Collector_Autopilot_2020_11_10_16_17_18.etl, DiagnosticLogCSP_Collector_DeviceProvisioning_2021_7_5_17_44_24.etl, IntuneManagementExtension-20210623-103112.log, IntuneManagementExtension-20210630-185736.log, IntuneManagementExtension.log, MDMDiagHtmlReport.html, MdmDiagLogMetadata.json,MDMDiagReport.xml, MdmDiagReport_RegistryDump.reg, MdmLogCollectorFootPrint.txt.microsoft-windows-aad-operational.evtx, microsoft-windows-appxdeploymentserver-operational.evtx, microsoft-windows-assignedaccess-admin.evtx, microsoft-windows-assignedaccess-operational.evtx, microsoft-windows-assignedaccessbroker-admin.evtx, microsoft-windows-assignedaccessbroker-operational.evtx, microsoft-windows-crypto-ncrypt-operational.evtx, microsoft-windows-devicemanagement-enterprise-diagnostics-provider-admin.evtx, microsoft-windows-devicemanagement-enterprise-diagnostics-provider-debug.evtx, microsoft-windows-devicemanagement-enterprise-diagnostics-provider-operational.evtx, microsoft-windows-moderndeployment-diagnostics-provider-autopilot.evtx, microsoft-windows-moderndeployment-diagnostics-provider-managementservice.evtx, microsoft-windows-provisioning-diagnostics-provider-admin.evtx, microsoft-windows-shell-core-operational.evtx, microsoft-windows-user device registration-admin.evtx, Sensor.log, setupact.log
Intune Management Extension Logs
Intune management extension is the lightweight agent that helps deploy complex apps, PowerShell scripts, and many other services on Windows devices. IME logs are similar to ConfigMgr logs, and these logs are located in the following location. IME is the Intune Logs in Windows PCs.
C:\ProgramData\Microsoft\IntuneManagementExtension\Logs
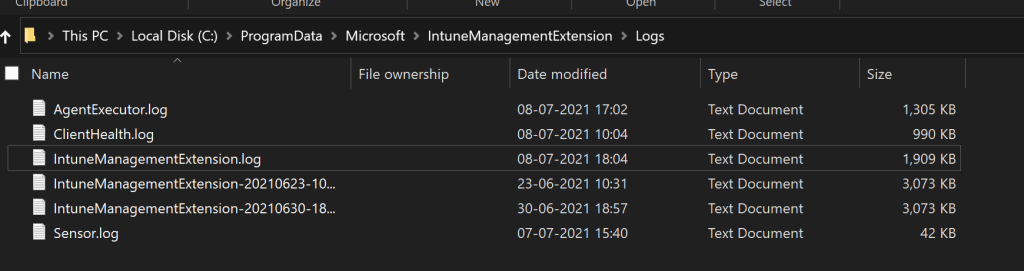
While writing this post, we have four (4) IME logs inside the IntuneManagementExtension\Logs folder.
- AgentExecutor.log
- ClientHealth.log
- IntuneManagementExtension.log
- Sensor.log
AgentExecutor.log
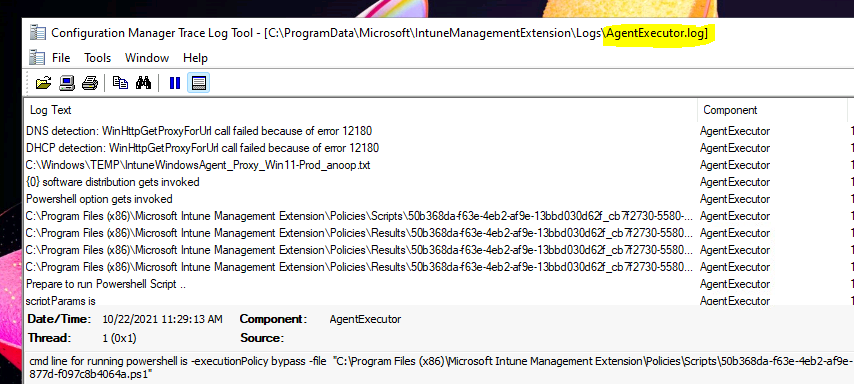
The AgentExecutor.log is part of Intune logs (IME), and this Intune log helps to troubleshoot the PowerShell script and Proactive Remediation script deployments to the Windows 11 or Windows 10 PCs.
C:\Program Files (x86)\Microsoft Intune Management Extension\Policies\Scripts\50b368da-f63e-4eb2-af9e-13bbd030d62f_cb7f2730-5580-4652-877d-f097c8b4064a.ps1
C:\Program Files (x86)\Microsoft Intune Management Extension\Policies\Results\50b368da-f63e-4eb2-af9e-13bbd030d62f_cb7f2730-5580-4652-877d-f097c8b4064a.output
cmd line for running powershell is -executionPolicy bypass -file “C:\Program Files (x86)\Microsoft Intune Management Extension\Policies\Scripts\50b368da-f63e-4eb2-af9e-13bbd030d62f_cb7f2730-5580-4652-877d-f097c8b4064a.ps1”
ClientHealth.log – IME Intune Logs
The ClientHealth.log records all the health and remediation actions related to Intune Management Extension agent on Windows 11 or Windows 10 clients.
More details on the IME health check-related activities are explained in Intune Management Extension Health Evaluation | IME Health Issue | ClientHealthEval.exe | Task Scheduler.
Summary: rule Verify/Remediate Intune Management Extension Service startup type. with ID 05980f21-0099-4ac4-8ba7-c9f5f0cd0b7f, result = Pass, details = N/A
Start processing rule Verify/Remediate Intune Management Extension service status.
Finish sending health report.
The client health report was sent successfully. Done.
Client Health evaluation completes.
IntuneManagementExtension.log – Intune Application Management Log File
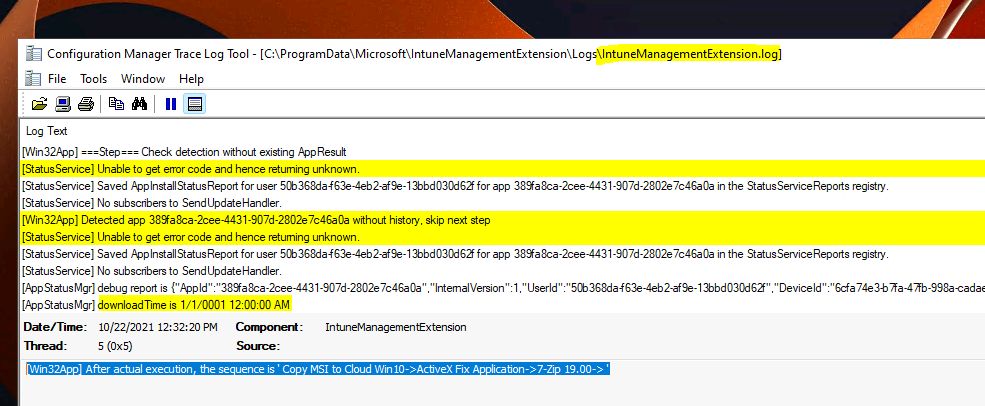
The log file IntuneManagementExtension.log is Intune Application Management Log File for IntuneWin applications. More details about IME troubleshooting is available – Intune Management Extension Deep Dive.
[Win32App] ===Step=== Check detection without existing AppResult
[StatusService] Unable to get error code and hence returning unknown.
[StatusService] Saved AppInstallStatusReport for user 50b368da-f63e-4eb2-af9e-13bbd030d62f for app 389fa8ca-2cee-4431-907d-2802e7c46a0a in the StatusServiceReports registry.
[AppStatusMgr] downloadTime is 1/1/0001 12:00:00 AM
Intune Registry Keys
Let’s check Intune registry keys to help with troubleshooting. You need to check a different registry path to confirm whether user policies are deployed. The PolicyManager\current\User SID is one of the registry locations for user-based Intune policies.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\S-1-12-1-3186897695-1137825691-1845872004-278613382\microsoft_edge~Policy~microsoft_edge
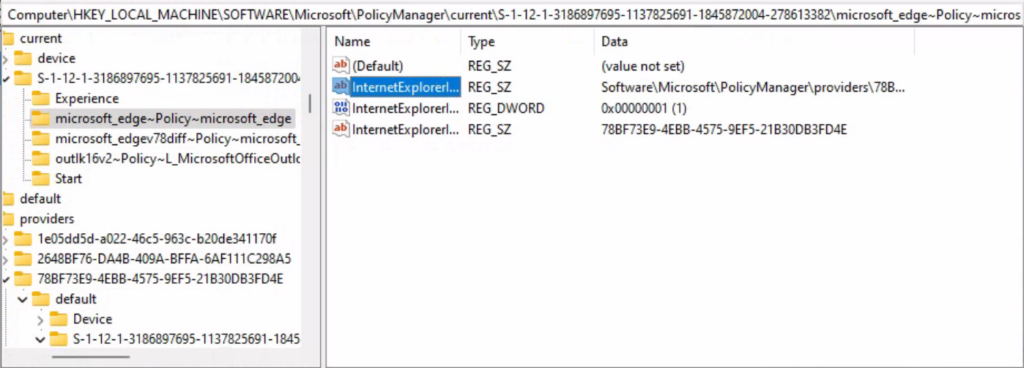
Intune (MDM CSP) User-based policy’s registry path is a bit different from the one that we have for devices. More details are available at Intune User Policy Troubleshooting Tips For Prevent Changing Theme.
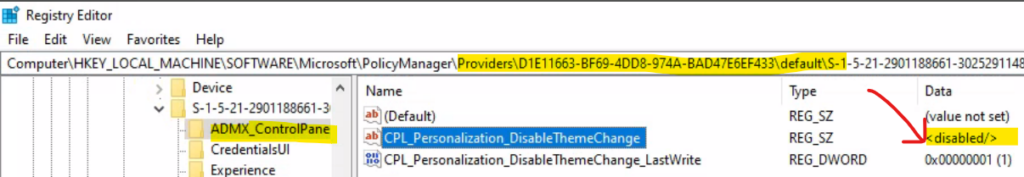
NOTE! – Another registry path with string value – Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\Providers\D1E11663-BF69-4DD8-974A-BAD47E6EF433\default\S-1-5-21-2901188661-3025291148-348095268-1124\ADMX_ControlPanelDisplay
Intune Event Logs
As mentioned above, Intune and Windows MDM-related component logs are available only in event logs. You can collect all the necessary event logs from the MDMDiagReport.cab file as discussed above. Let’s check which are the critical event logs that would be helpful for Intune deployment troubleshooting.
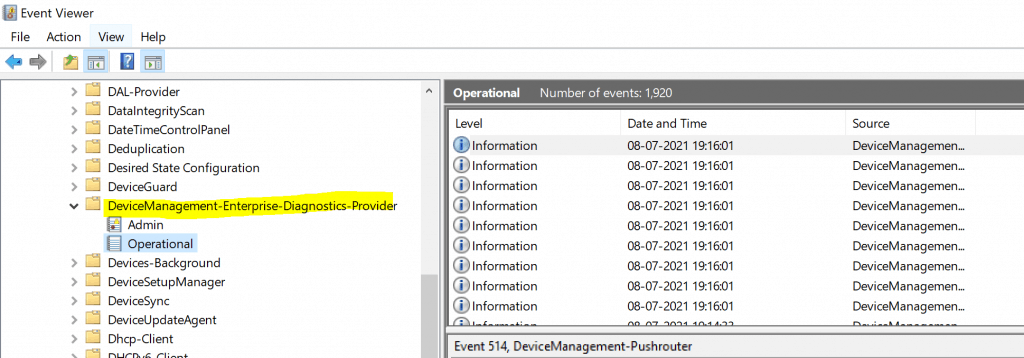
Event logs are the extended type of Intune Logs in Windows. In most of the scenarios, I use the event logs that are highlighted in bold. Those are core MDM event logs and are very helpful in troubleshooting Intune policy deployment issues.
Intune log (event) path is the Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
- microsoft-windows-aad-operational
- microsoft-windows-appxdeploymentserver-operational
- microsoft-windows-assignedaccess-admin
- microsoft-windows-assignedaccess-operational
- microsoft-windows-assignedaccessbroker-admin
- microsoft-windows-assignedaccessbroker-operational
- microsoft-windows-crypto-ncrypt-operational
- microsoft-windows-devicemanagement-enterprise-diagnostics-provider-admin (Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Admin)
- microsoft-windows-devicemanagement-enterprise-diagnostics-provider-debug
- microsoft-windows-devicemanagement-enterprise-diagnostics-provider-operational (Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Operational)
- microsoft-windows-moderndeployment-diagnostics-provider-autopilot
- microsoft-windows-moderndeployment-diagnostics-provider-managementservice
- microsoft-windows-provisioning-diagnostics-provider-admin
- microsoft-windows-shell-core-operational
- microsoft-windows-user device registration-admin
Event ID 208 – Intune Server Sync Initiated
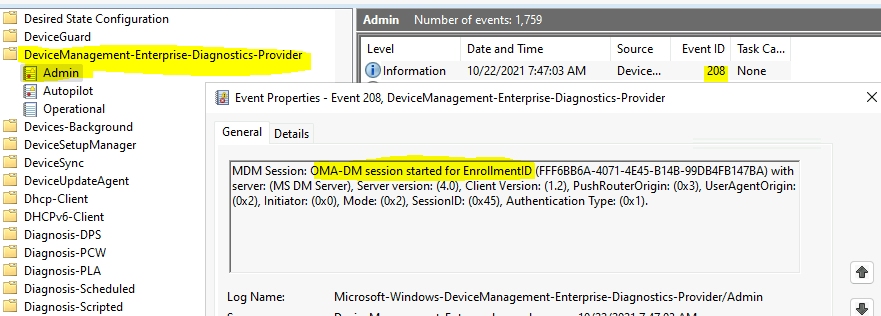
The event ID 208 indicates that the Windows MDM client-initiated policy sync with the MDM server, and in this scenario, it’s Intune. The event log clearly shows that the OMA-DM session started for a particular enrollmentID.
This is the first event ID you should look for when you initiate manual policy sync (Initiate a Manual Intune Policy Sync) from Windows 10 or Windows 11 PCs.
MDM Session: OMA-DM session started for EnrollmentID (FFF6BB6A-4071-4E45-B14B-99DB4FB147BA) with server: (MS DM Server), Server version: (4.0), Client Version: (1.2), PushRouterOrigin: (0x3), UserAgentOrigin: (0x2), Initiator: (0x0), Mode: (0x2), SessionID: (0x45), Authentication Type: (0x1).
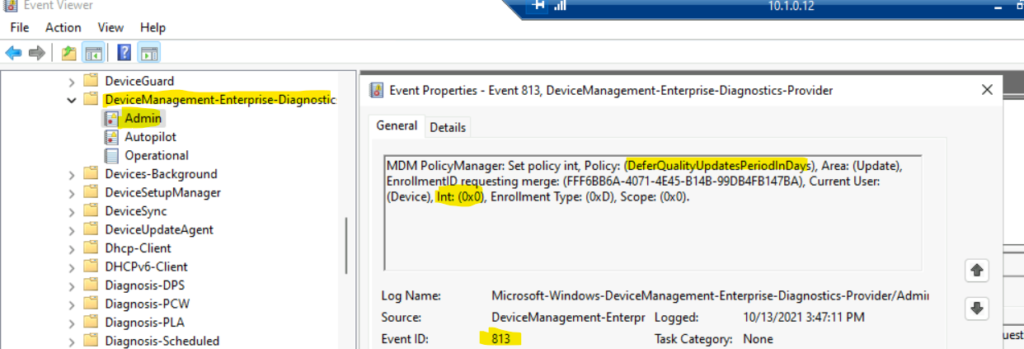
Event ID 813 for Intune Policy Integer
The event ID 813 indicates that the Windows CSP policy is applied on Windows 10 or Windows 11 PC. The Intune policy setting is based on an integer value. The 813 event ID also indicates that this policy setting is successfully applied on the client PCs.
EVENT ID 813 (Integer) – MDM PolicyManager: Set policy int, Policy: (DeferQualityUpdatesPeriodInDays), Area: (Update), EnrollmentID requesting merge: (FFF6BB6A-4071-4E45-B14B-99DB4FB147BA), Current User: (Device), Int: (0x0), Enrollment Type: (0xD), Scope: (0x0).
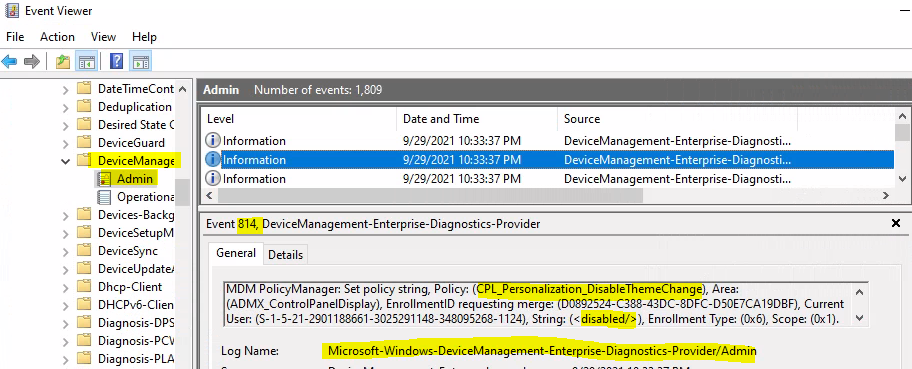
Intune Event Logs – Event ID 814
Let’s go through some of the details of important event logs as part of Intune logs post. Event ID 814 means the MDM client received a policy update from the server and successfully applied it on the Windows 10 or Windows 11 client PC.
The event ID 814 signifies the type of Intune policy received as well. This event ID indicates that the policy received is STRING. As you know, there are different types of policy types in Windows CSP. The string is one of those policies.
EVENT ID 814 – MDM PolicyManager: Set policy string, Policy: (CPL_Personalization_DisableThemeChange), Area: (ADMX_ControlPanelDisplay), EnrollmentID requesting merge: (D0892524-8DFC-D50E7CA19DBF), Current User: (S-1-5-21-2901188661-3025291148-348095268-1124), String: (), Enrollment Type: (0x6), Scope: (0x1).
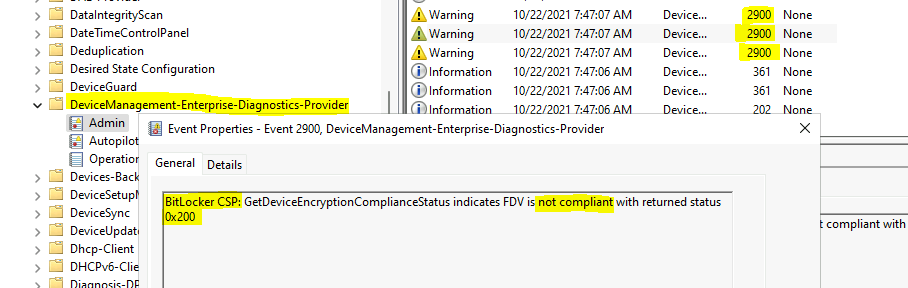
Event ID – 2900 – Warning Not Compliant
The event ID 2900 indicates a warning when the MDM client tries to assess the compliance state of the PC. In the following example, Bitlocker CSP is checking the compliance status on a Cloud PC, and obliviously my lab VMs are not BitLocker enabled.
BitLocker CSP: GetDeviceEncryptionComplianceStatus indicates FDV is not compliant with returned status 0x200
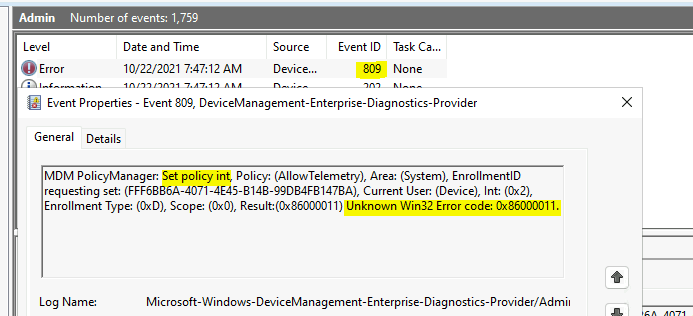
Event ID 809 – Unknown Win32 Error
The event ID 809 indicates an error with Intune policy implementation on Windows 10 or Windows 11 PCs. You will have to evaluate further and troubleshoot the issue. You will need to check the registry entries related to this particular policy and further troubleshoot this issue.
You can search the registry with any of the keywords in the event log below – AllowTelemetry, FFF6BB6A-4071-4E45-B14B-99DB4FB147BA, etc., to understand the issue further. Some further tips are available in Intune User Policy Troubleshooting Tips For Prevent Changing Theme.
MDM PolicyManager: Set policy int, Policy: (AllowTelemetry), Area: (System), EnrollmentID requesting set: (FFF6BB6A-4071-4E45-B14B-99DB4FB147BA), Current User: (Device), Int: (0x2), Enrollment Type: (0xD), Scope: (0x0), Result:(0x86000011) Unknown Win32 Error code: 0x86000011.
The event ID 820 indicates access denied error in the following example. The Windows 10 or Windows 11 MDM client is trying to check the status of RequireRetrieveHealthCertificateOnBoot, and this is not available for Cloud PCs (?) hence it gets the following error (0x80004005) Unspecified error.
Event ID 820 – MDM PolicyManager: Set policy precheck precheck call. Policy: (Security), Area: (RequireRetrieveHealthCertificateOnBoot), int value: (0x1) Result:(0x80004005) Unspecified error.
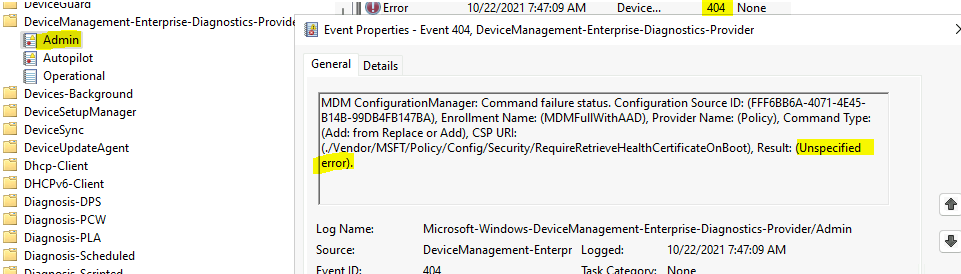
Event ID 404 Unspecified Error
The event ID 404 indicates different types of errors. One of them can be easily ignored, and that is the FakePolicy event log. This is a known bug with Windows 11 and Windows 10.
So you can safely ignore this error The system cannot find the file specified for fake policy OMA-URI.
MDM ConfigurationManager: Command failure status. Configuration Source ID: (FFF6BB6A-4071-4E45-B14B-99DB4FB147BA), Enrollment Name: (MDMFullWithAAD), Provider Name: (Policy), Command Type: (Add: from Replace or Add), CSP URI: (./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Receiver/Properties/Policy/FakePolicy/Version), Result: (The system cannot find the file specified.).
The event log 404 error (Unspecified error) for Intune policy assignment related to secure boot and PCHealth etc., could not be applied on most of the Windows 10 and Windows 11 virtual machines.
The RequireRetrieveHealthCertificateOnBoot might not be available for Azure VM/ AVD VMs / Cloud PCs in most of the scenarios. So, you might need to filter out the deployment of these policies to VMs or VDIs.
MDM ConfigurationManager: Command failure status. Configuration Source ID: (FFF6BB6A-4071-4E45-B14B-99DB4FB147BA), Enrollment Name: (MDMFullWithAAD), Provider Name: (Policy), Command Type: (Add: from Replace or Add), CSP URI: (./Vendor/MSFT/Policy/Config/Security/RequireRetrieveHealthCertificateOnBoot), Result: (Unspecified error).
Feedback Hub – Company Portal Log Collection
You also can provide feedback or record the issue via feedback hub integration with the Company portal. I have not used this option to give a full experience. However, this seems to collect a lot of data, including screenshots and screen recordings. I’m also not sure whether this type of data collection is allowed from all corporate organization privacy perspectives.
Make sure you save a local copy of the diagnostic and attachments created when giving feedback. The path where it gets stored is C:\Users\Anoop\Documents\FeedbackHub.

Community Tool to Collect Intune Logs
This package is used in conjunction with the Microsoft Support One Data Collector (ODC) tool to gather data from Windows Intune client machines.
The XML file contains data locations and scripts to collect a variety of files, registry keys, and command-line output to assist support engineers in troubleshooting Intune issues.
Resources
- Intune Management Extension Deep Dive – Win32 App Deployment Troubleshooting Help Guide
- How to Start Troubleshooting Intune Issues

It will be helpful while learning sir.