Let’s discuss Enable or Disable Microsoft Account Connection Policy using Intune. Microsoft Account Connection is a policy available in the Microsoft Intune Settings catalog. This policy specifies whether the user is allowed to use an MSA account for non-email related connection authentication and services in Windows devices.
As we know that, we are regularly using various Microsoft services in our day to day life. It includes OneDrive, Xbox services, Microsoft Store, and other cloud-based features. With Microsoft Account Connection Policy an Admin can control accessing MSA.
Microsoft Intune provides many Microsoft Account related policies. We have post related to Allow Manual Start of Microsoft Account Sign In Assistant Using Intune Settings Catalog. This policy helps to provide access only to only on authorised devices.
Like this, Microsoft Account Connection Policy also has many benefits. By configuring this policy it provides many advantages to admins, users and organization. Through this blog post I would like to guide you to configure this policy.
Table of Contents
What are the Security Benefits of Account Management Connection Policy?
Your Enterprise Security can be enhance with Account Management Connection Policy. It control how user account are created, maintained and terminated.
1. Access allowed only for authorized user
2. Enforce Role based access
3. Inactive accounts will be disables
4. Unique user ID is needed
Enable or Disable Microsoft Account Connection Policy using Intune
As mentioned above, this policy provides many benefits. Here I will explain with an Example. If you are an admin who manages Windows 11 devices in an organization. You want users to access Microsoft Store apps with MSA. This policy helps to enable or disable Microsoft Account Connection.
| Benefits for Admin | Benefits for User | Benefits for Organization |
|---|---|---|
| Enhance Security | Helps to access to personal services | Control over Data Flow |
| Policy Consistency | It helps users to separate | Simplified compliance |
- How to Allow Adding Non Microsoft Accounts Manually Using Intune Setting Catalog
- Intune Allow Microsoft Accounts to be Optional Policy
- Create Intune Policy to Block Microsoft Accounts
CSP Details of Microsoft Account Connection Policy
The CSP page provides many details of the Microsoft Account Connection Policy. By checking this page you can efficiently deploy the policy to your organization. This page shows Description framework properties and Allowed values of the policy.
The below table shows the Description Framework properties of the Microsoft Account Connection Policy. It includes property name and Property value. Look at the below screenshot.
| Property Name | Property Value |
|---|---|
| Format | int |
| Access Type | Add, Delete, Get, Replace |
| Default Value | 1 |
The Allowed values shows the applicable values in Microsoft Account Connection settings. So you can prefer applicable value to configure the policy. The table below shows the Values.
| Value | Description |
|---|---|
| 0 | Not allowed |
| 1 (Default) | Allowed |
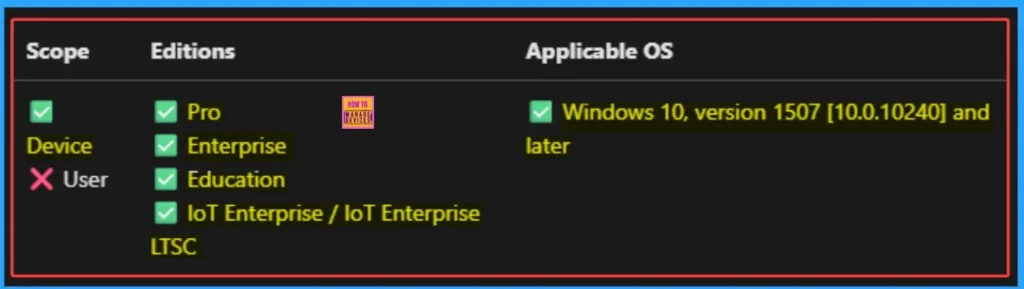
Steps to Configure Policy
By sign in to Microsoft Intune Admin center you can easily configure this policy. You can configure this policy to Pro, Enterprise, Education, IoT Enterprise / IoT Enterprise LTSC editions. This policy is applicable for Windows 10, version 1507 [10.0.10240] and later OS.
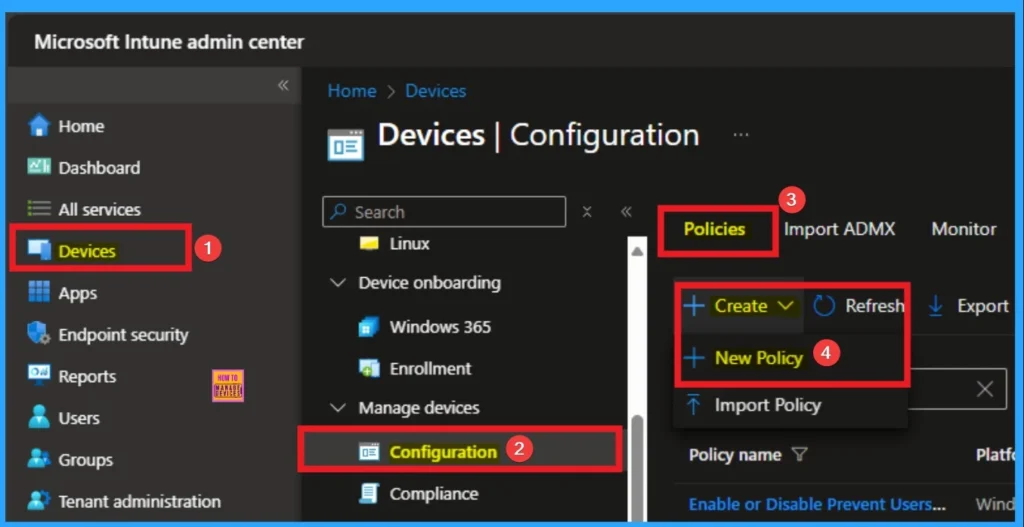
- Go to the Intune Admin Center portal
- Go to Devices > Windows >Configuration > Create > New Policy
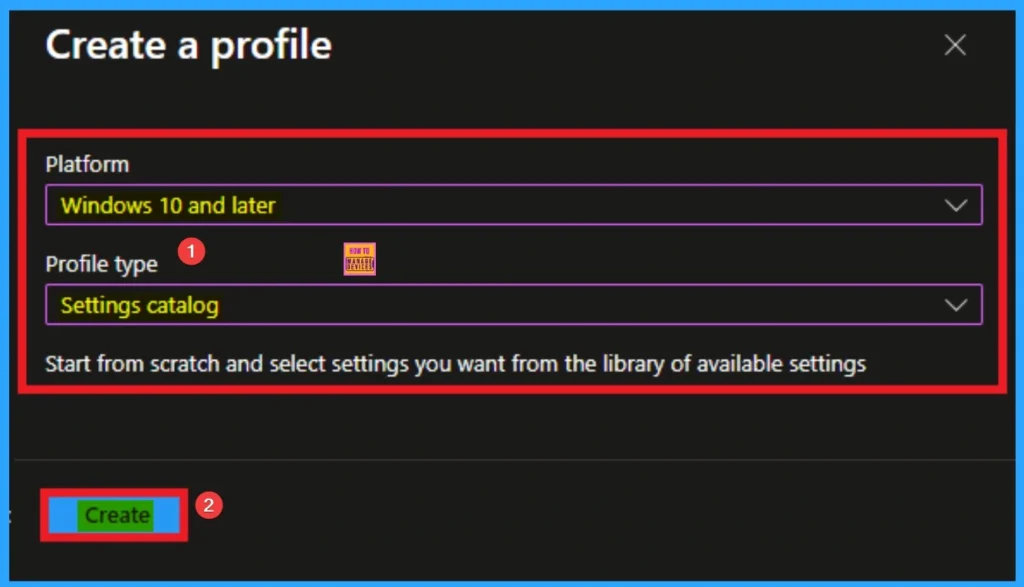
Profile Creation of Policy
Next steps is to Create a Profile for the policy which you want to configure. To create a profile you have to select platform and profile type. Here I selected Windows 10 and later as the Platform and Settings catalog as the profile type. Then click on the Create button.
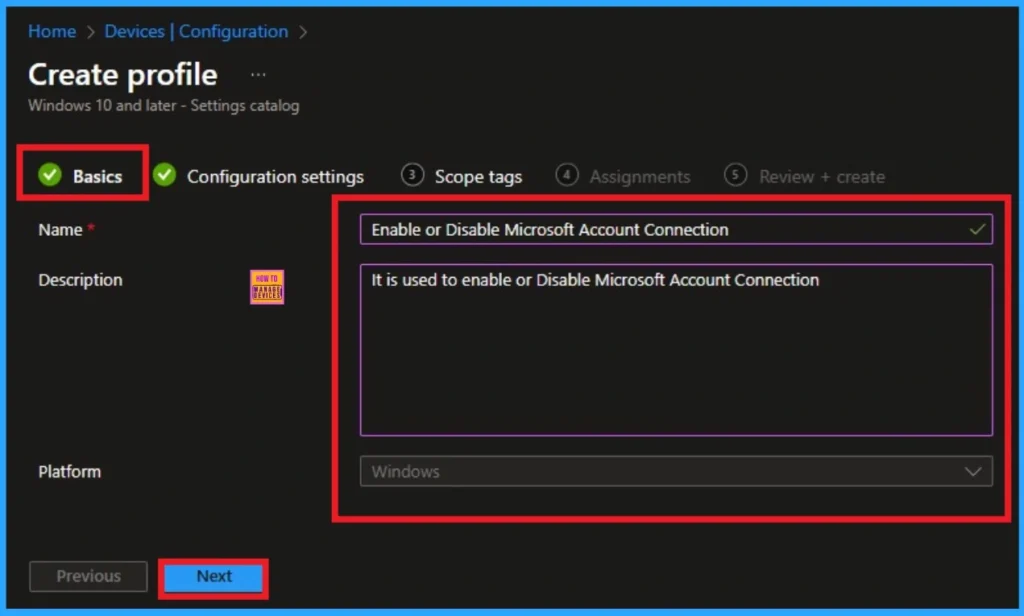
Starting Step of Policy Creation
The below screenshot shows the Basic tab which is very necessary to create the policy. On this tab you have to add Name and Description for the selected policy. The Name is mandatory and if you like to add description you can add.
- Name – Enable or Disable Microsoft Account Connection Policy
- Description – This policy isused to Enable or Disable Microsoft Account Connection
- Platform – Windows
- Click on the Next Button
Configure the Microsoft Account Connection Settings
The Configuration settings page is provided to select the settings to create the policy. The Settings Catalog provides a huge number of settings. To select a settings click on the +Add settings hyperlink. Then you will get Settings Picker.
After clicking on the +Add settings, you will get the Settings Picker. Here you can select a particular settings by searching or browse by category. Here I would like to select the settings by browse by Category. I choose Accounts category and select Allow Microsoft Account Connection settings. Then I close the Settings Picker.
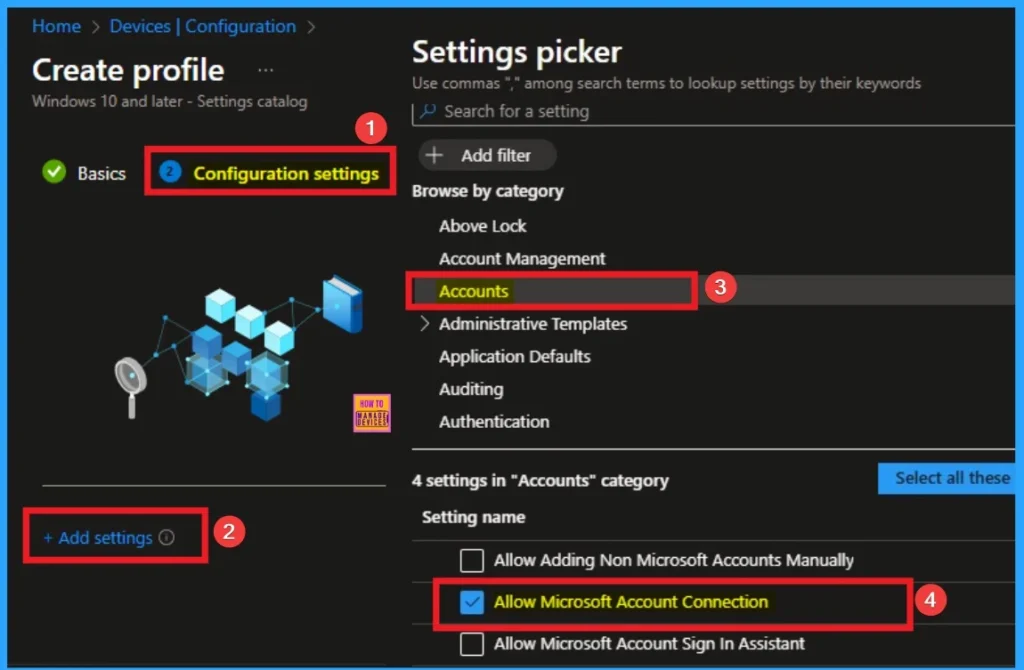
Enable Microsoft Account Connection Settings
After selecting this policy, it will shown on the Configuration Settings Page. By enabling this policy seamless experience will get to personal Microsoft services alongside work accounts. This policies default, value is Enable. If you are go with this click on the Next Button
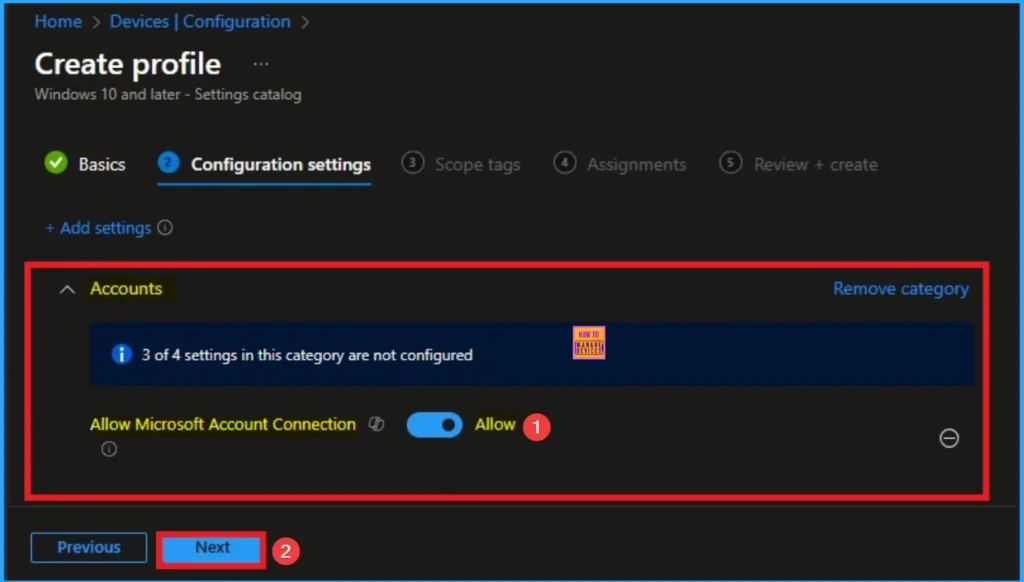
Disable Policy
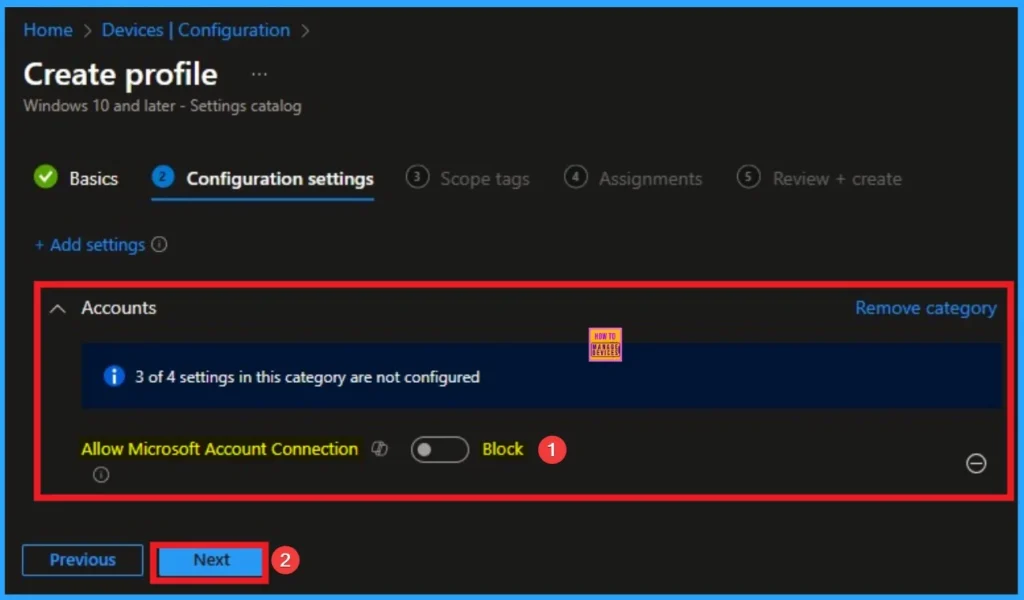
By disabling this policy, you can create a controlled environment by blocking personal account and you can prevent data leakage. Here I choose Disable value to configure this policy. Then click on the Next button.
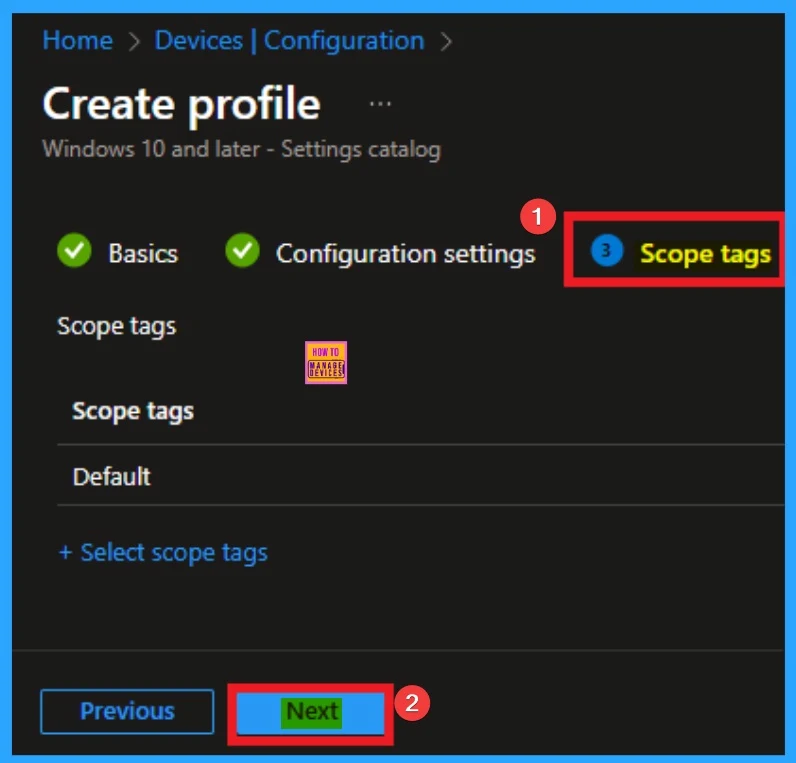
Scope Tags
By using scope tags you can restrict the visiblity of Microsoft Account Connection Settings. It is helps to organize resources as well. Here I would like to skip this section, because it is not mandatory. Click on the Next button.
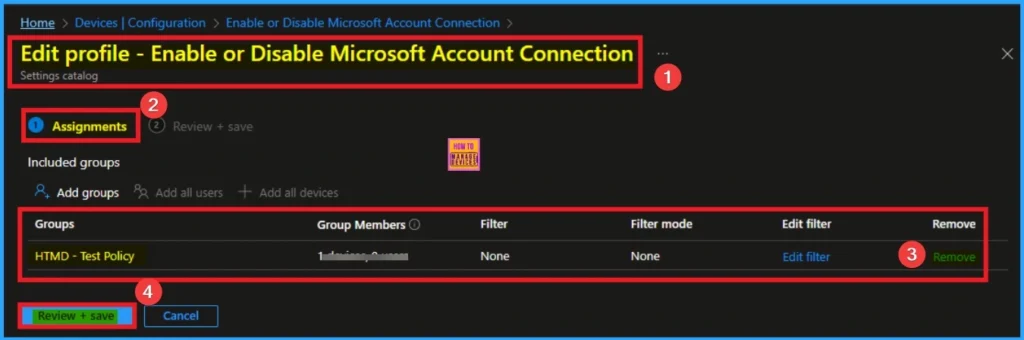
Assign this Policy to Specific Groups
To assign the policy to specific groups you can use Assignment Tab. Here I click, +Add groups option under Included groups. I choose a group from the list of group and Click on the Select button. Again I click on the Select button to continue.
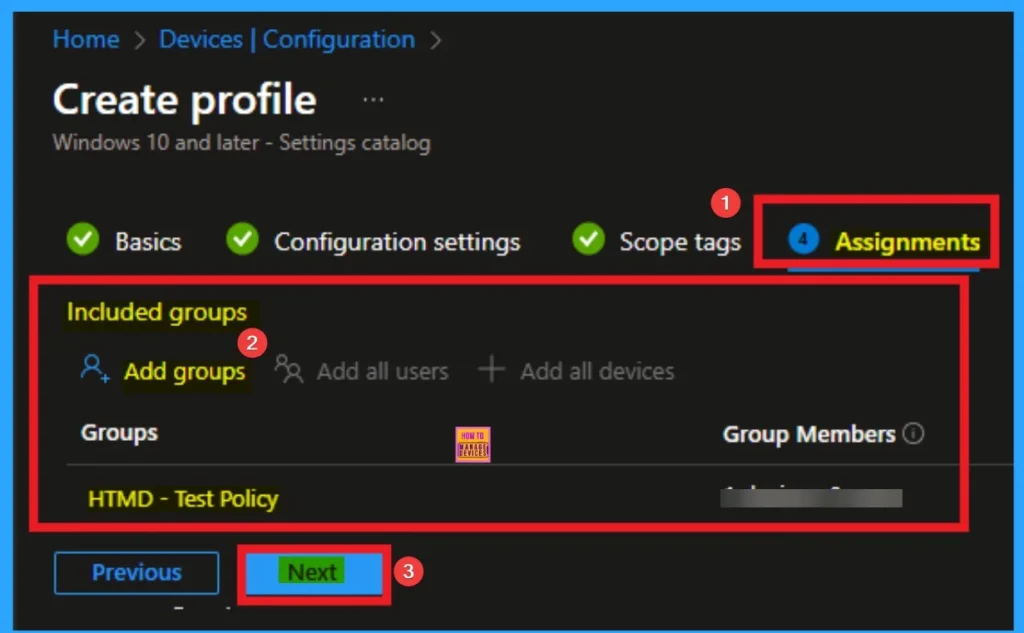
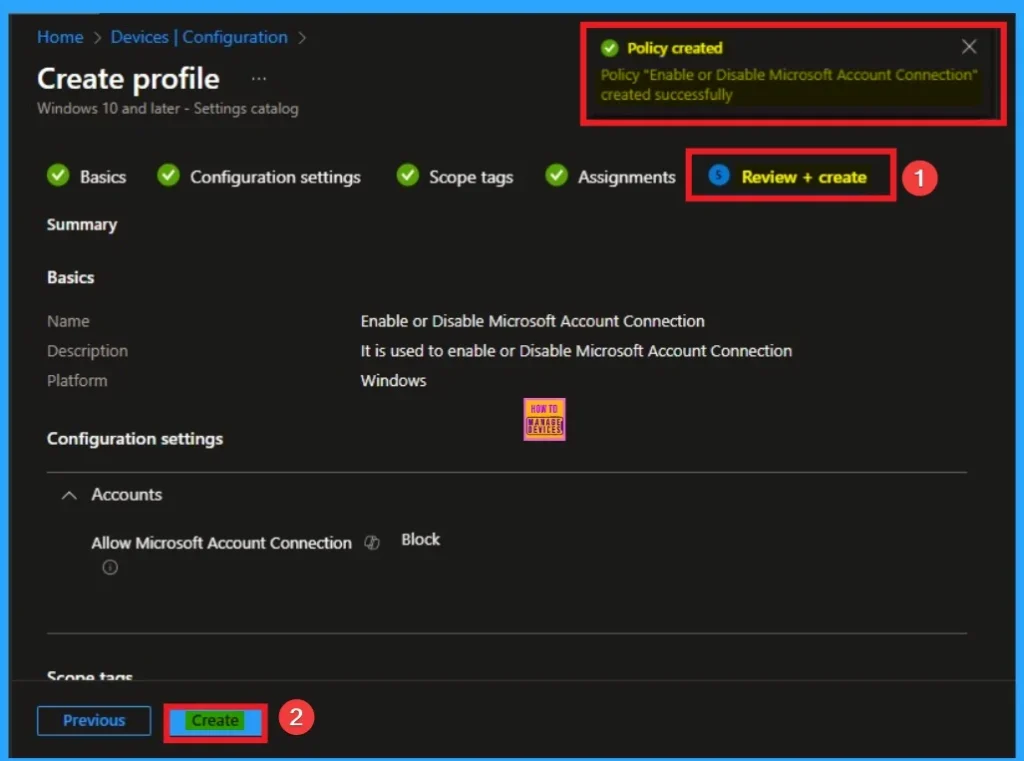
Final Step of Policy Creation
To complete the policy creation you can review all the policy details on the Review + create tab. It helps to avoid mistakes and successfully configure the policy. After varifying all the details click on the Create Button. After creating the policy you will get success message.
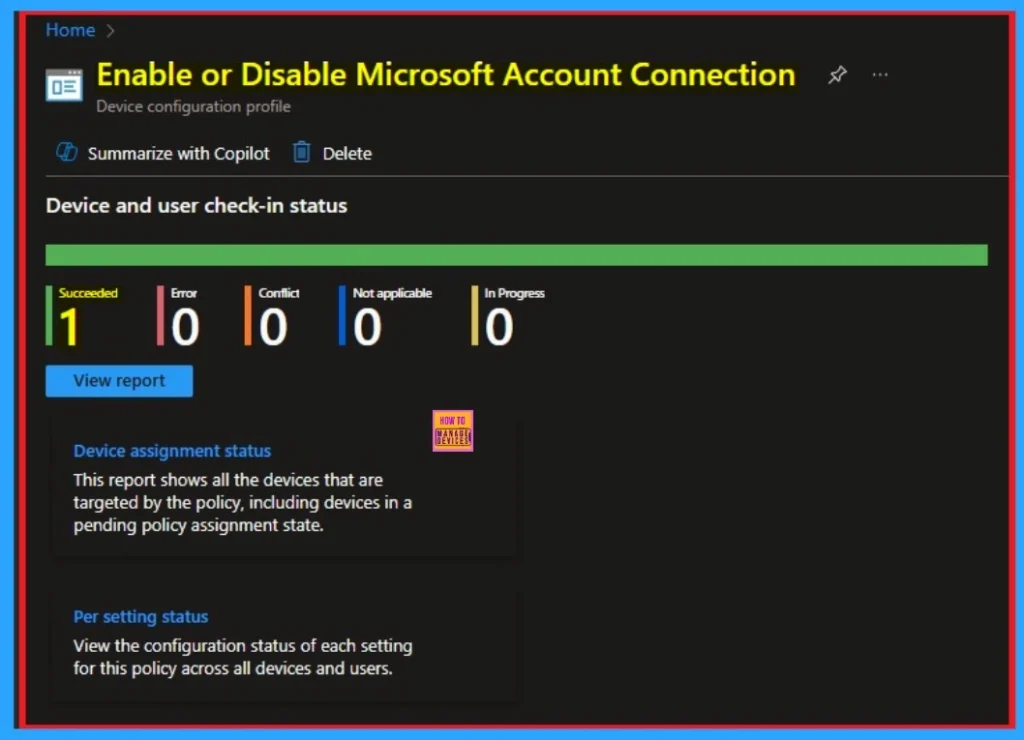
Device Checking Status
To quickly configure the policy and take advatage of the policy sync the assigned device on Company Portal. Open the Intune Portal. Go to Devices > Configuration > Search for the Policy. Here the policy shows as succeeded.
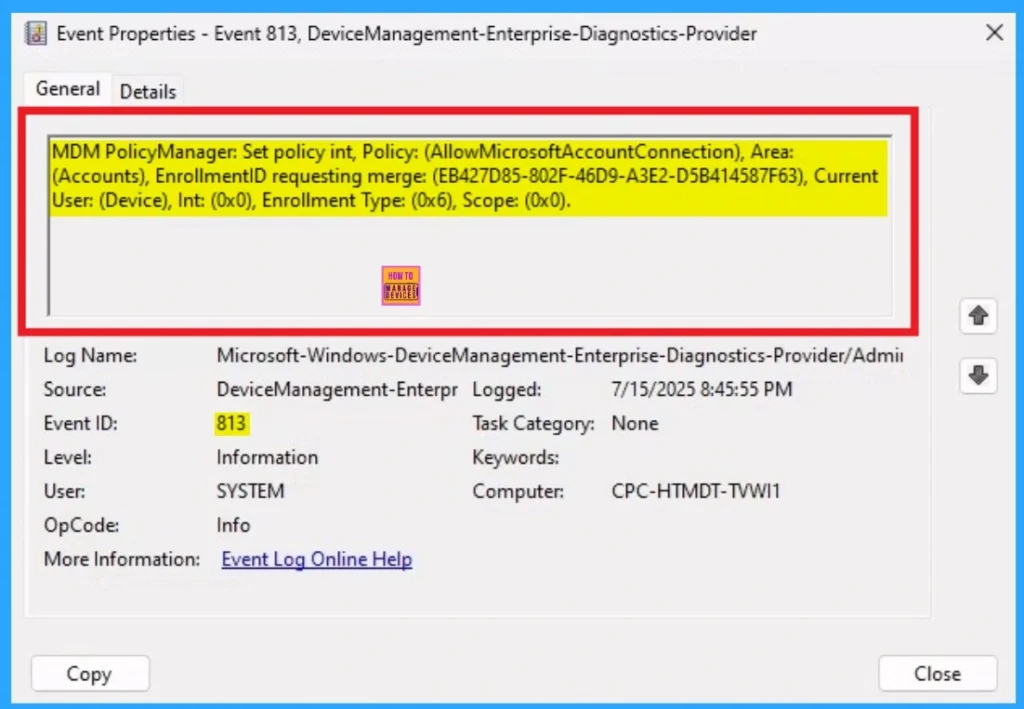
Client Side Verification with Event Viewer
If you get success message, that doesn’t means you will get the policy advanatges. To varify the policy successfully configured to client device check the Event Viwer.
- Open Event Viewer: Go to Start > Event Viewer.
- Navigate to Logs: In the left pane, go to Application and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider > Admin.
- Filter for Event ID 813: This will help you quickly find the relevant logs.
MDM PolicyManager: Set policy int, Policy: (AllowMicrosoftAccountConnection), Area:
(Accounts), EnrollmentID requesting merge: (EB427D85-802F-46D9-A3E2-D5B414587F63), Current
User: (Device), Int: (0x0), Enrollment Type: (0x6), Scope: (0x0).
Removing the Assigned Group from Microsoft Account Connection Settings
If you want to remove the Assigned group from the policy, it is possible from Intune Portal. To do this open the Policy on Intune Portal and Edit the Assignments tab and Remove the Policy.
To get more detailed information, you can refer to our previous post – Learn How to Delete or Remove App Assignment from Intune using by Step-by-Step Guide.
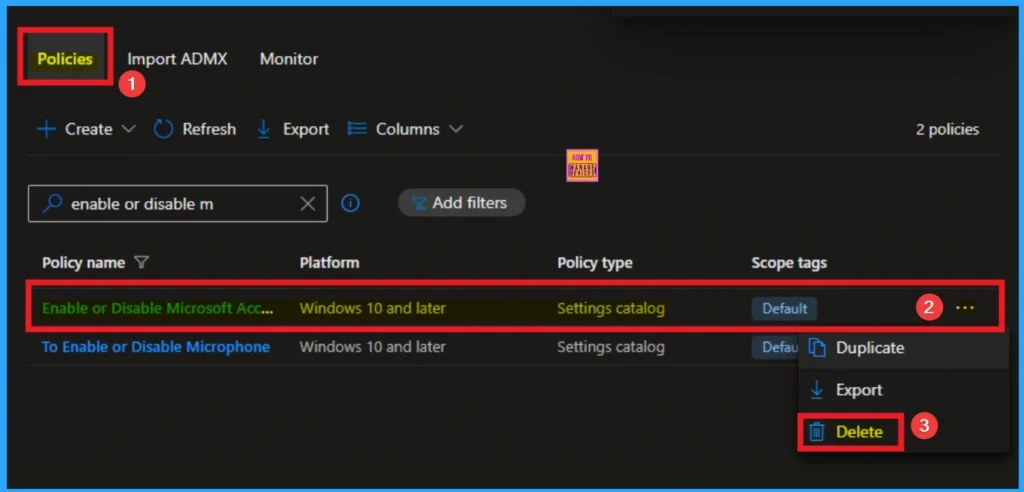
How to Delete Microsoft Account Connection Settings
You can easily delete the Policy from Intune Portal From the Configuration section you can delete the policy. It will completely remove from the client devices.
For detailed information, you can refer to our previous post – How to Delete Allow Clipboard History Policy in Intune Step by Step Guide.
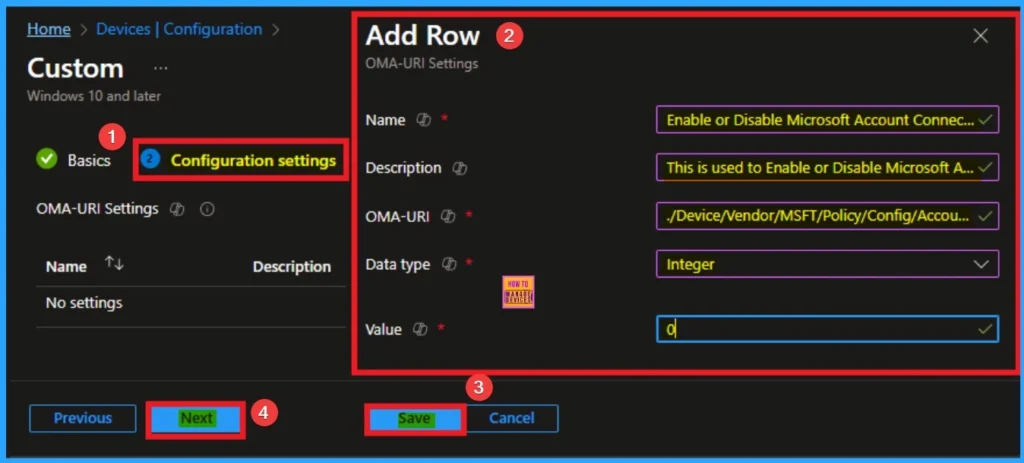
OMA URI Settings
It can be easily configured throug CSP. You can create OMA URI Settings by Sign in Intune Portal. Devices > Configuration. Click on Create to start a new policy. Choose the platform as Windows 10 or later. For the Profile type, select Templates, then choose Custom. Provide a name for the policy, such as Allow Search Engine Customisation and add a description if needed.
| Steps |
|---|
| Click on + Add under OMA-URI Settings to configure the specific setting. |
| To Configure the OMA-URI Setting Enter Name and Description |
| Enter the following OMA-URI path: ./Device/Vendor/MSFT/Policy/Config/Accounts/AllowMicrosoftAccountConnection |
| Enter the value 0 – Not allowed. 1 – (Default) Allowed. |
| After entering the above details, click the Save button. |
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


