In this article, let’s explore how to set up Multi Admin Approval for three new device actions in Microsoft Intune. Intune’s Multi Admin Approval (MAA) capability has now been extended to include three powerful device-related actions: Device delete, Device retire, and Device wipe. These actions directly impact device lifecycle and data security, so adding an approval workflow helps organizations implement stronger governance.
Instead of a single admin being able to trigger these actions, Intune now requires that requests go through an approval chain defined in your access policies. This ensures sensitive tasks are monitored, reduces the chance of mistakes, and adds accountability. With this update, when an Intune administrator submits a request to delete, retire, or wipe a device, the action won’t be executed immediately.
Instead, it enters a pending approval state, visible to the approvers defined in your MAA access policy. Only after another authorized admin reviews and approves the request will the action proceed. This workflow provides an extra safeguard for scenarios such as retiring devices at scale, wiping a lost/stolen device, or permanently removing a record from Intune. This update is generally available (GA) from Intune Service Release 2508 onwards.
For enterprises with strict compliance or audit requirements, this enhancement brings more control and visibility. Organizations can now prevent accidental or malicious device actions that could impact business continuity or compromise security. Combined with auditing and reporting, MAA ensures there is always a clear trail of who requested and who approved critical device operations. This makes Intune not just a device management solution but also a governance-ready platform for modern IT operations.

Table of Contents
Details on Multi Admin Approval for Three New Device Actions in Intune
Here’s a clear comparison table for the three new Intune device actions supported with Multi Admin Approval (MAA).
| Policy Type/Action | What It Does | Typical Use Case | Risk Without Approval |
|---|---|---|---|
| Device delete | Permanently removes the device record from Intune and Entra ID (if applicable). | When a device is no longer in use or needs to be re-enrolled from scratch. | Loss of historical records, accidental removal of active devices, compliance gaps. |
| Device retire | Removes company data and apps from the device but leaves personal data intact. | When an employee leaves the company or transitions to BYOD (Bring Your Own Device). | Company data exposure if retired unintentionally or without authorization. |
| Device wipe | Performs a factory reset, removing all data (corporate and personal) on device. | Lost, stolen, or repurposed corporate devices requiring complete reset for security. | Permanent data loss, business disruption if triggered by mistake or malicious activity. |
- Intune Zero Trust Implementation using EPM and MAA
- Secure Remote Actions Retire Wipe and Delete with MAA Multiple Administrative Approval in Intune
- Best Method to Enable and Disable Windows 365 Cloud PCs Redirections using Intune
- How to Create New Platform Specific Device Clean-up Rule in Intune
Create an Access Policy to Set Up Multi Admin Approval for Device Delete
To configure multi-admin approval for Device delete, sign in to the Microsoft Intune Admin Center using your administrator credentials. You can follow similar steps for actions such as device retire and device wipe.
- Navigate to Tenant administration > Multi Admin Approval > Access policies
- Click on +Create
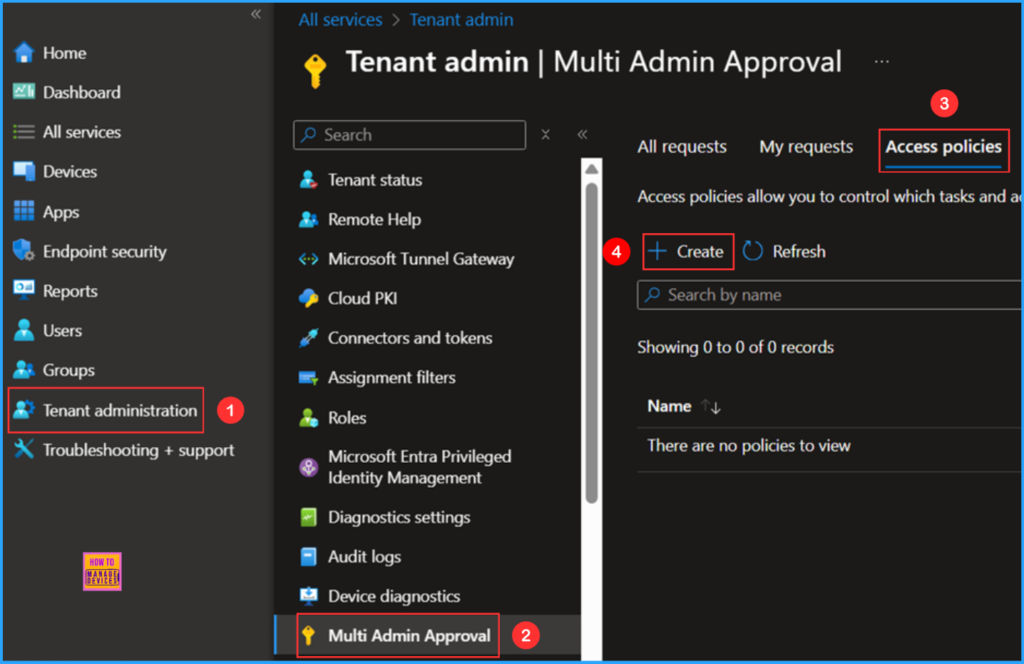
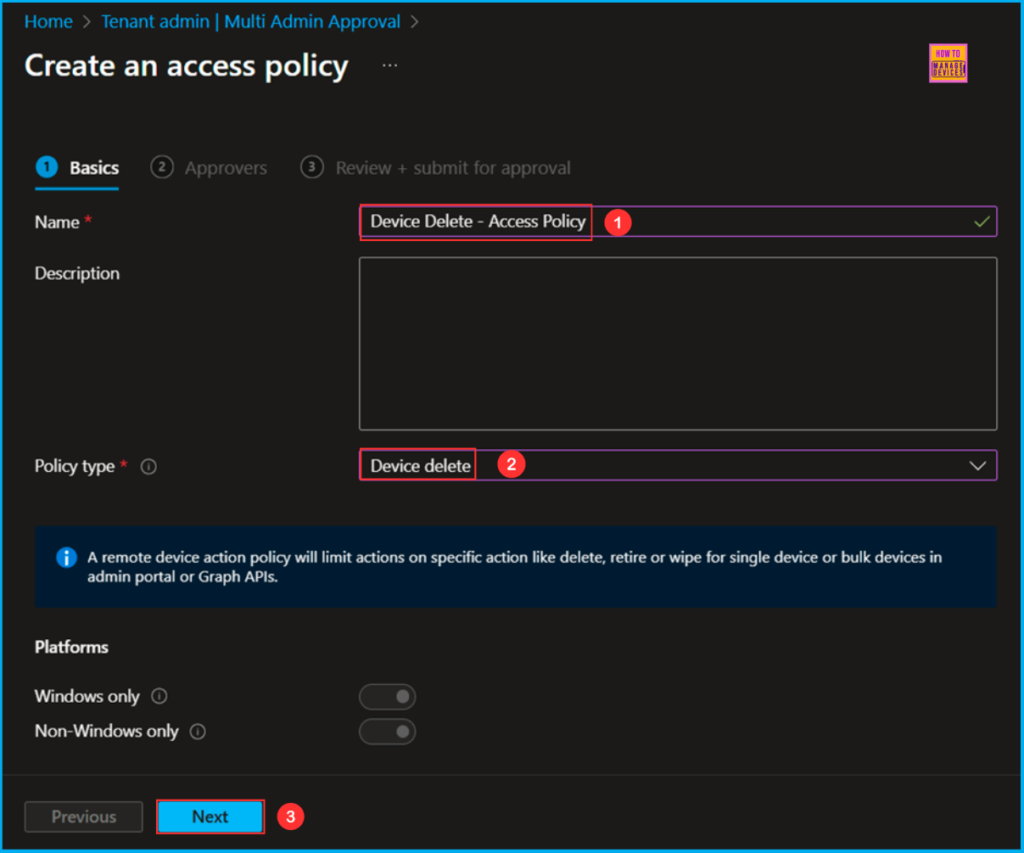
In the Basics details pane, name the access policy as Device Delete – Access Policy It is also helpful to provide a brief description of the policy’s purpose. Select the options below and click Next.
- Description – Optional
- Policy type – Choose Device delete from the drop-down
- Platforms – Windows only & Non-Windows only
Note: A remote device action policy will limit actions on specific action like delete, retire or wipe for single device or bulk devices in admin portal or Graph APIs.
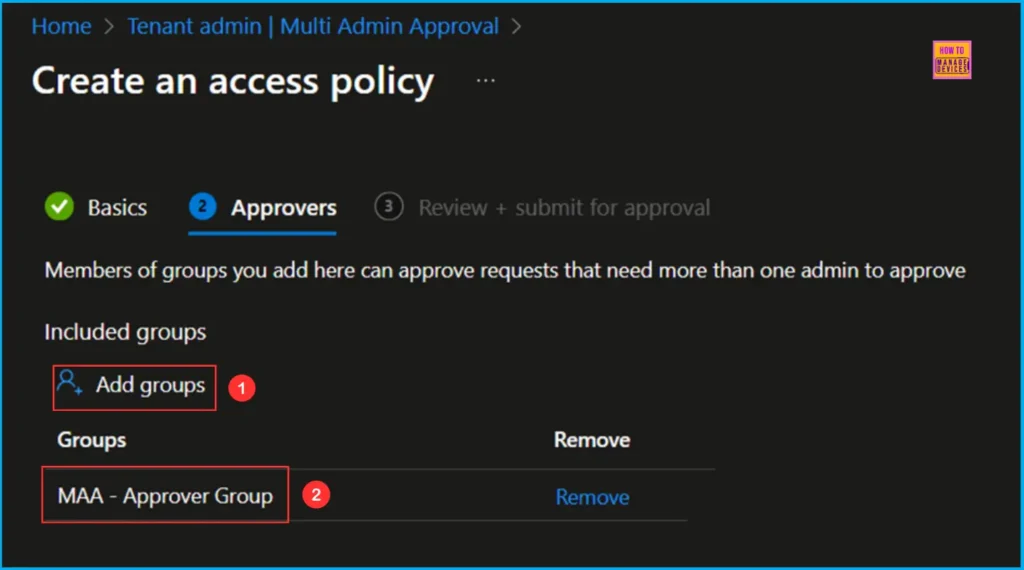
To set up a user group for approvers, first create the group and then add the approvers as members. Click on +Add groups and select the MAA – Approver Group. Members of this group will have the authority to approve requests that require more than one admin’s approval.
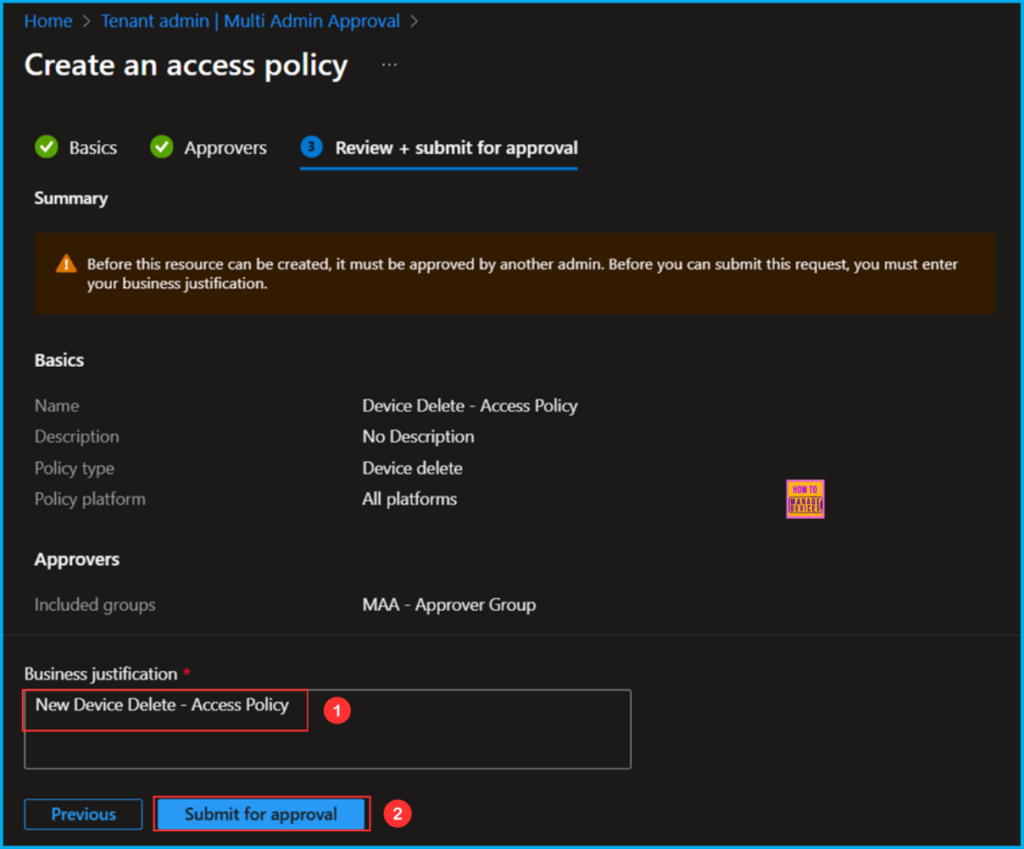
In the Review + submit for approval pane, carefully review all settings for the Device Delete – Access Policy policy. Be sure to include a valid business justification. I am entering “New Device Delete – Access Policy” here. Once you have confirmed everything, select Submit for approval.
Review the Submitted Approval
The other admin who is part of our MAA – Approver Group can now review and approve your submitted request. Please log in using the account of the other admin who is a member of our MAA – Approver Group. Navigate to Tenant administration > Multi Admin Approval > All requests to find the request.
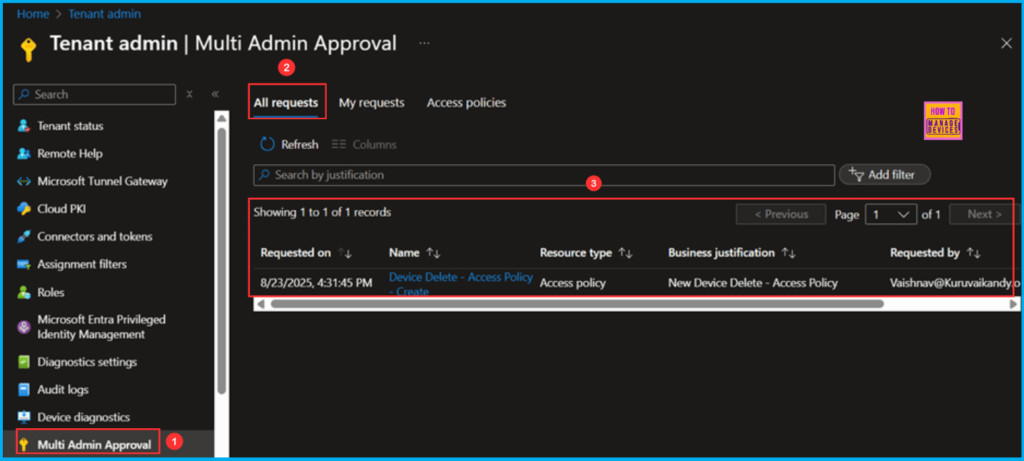
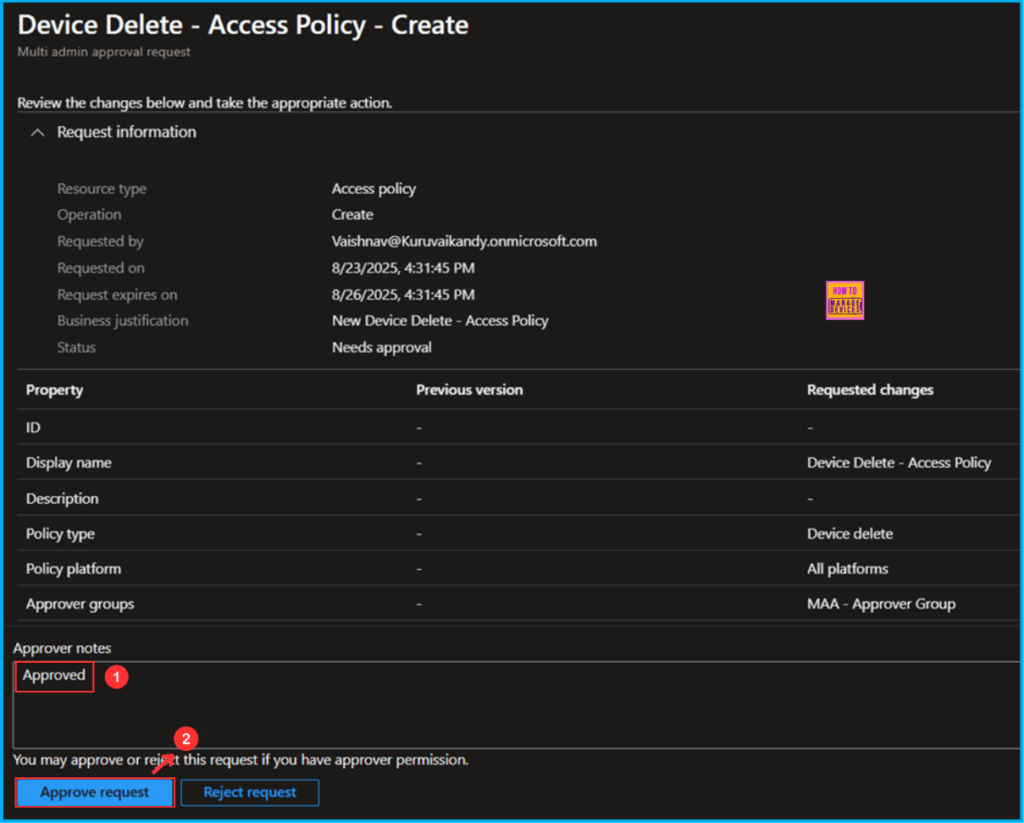
Click on the Device Delete – Access Policy – Create hyperlink. This will take you to a section where you can review the changes below and take the appropriate action. In the Approval notes section, add a note stating I am added as Approved, and then click on the Approve request button.
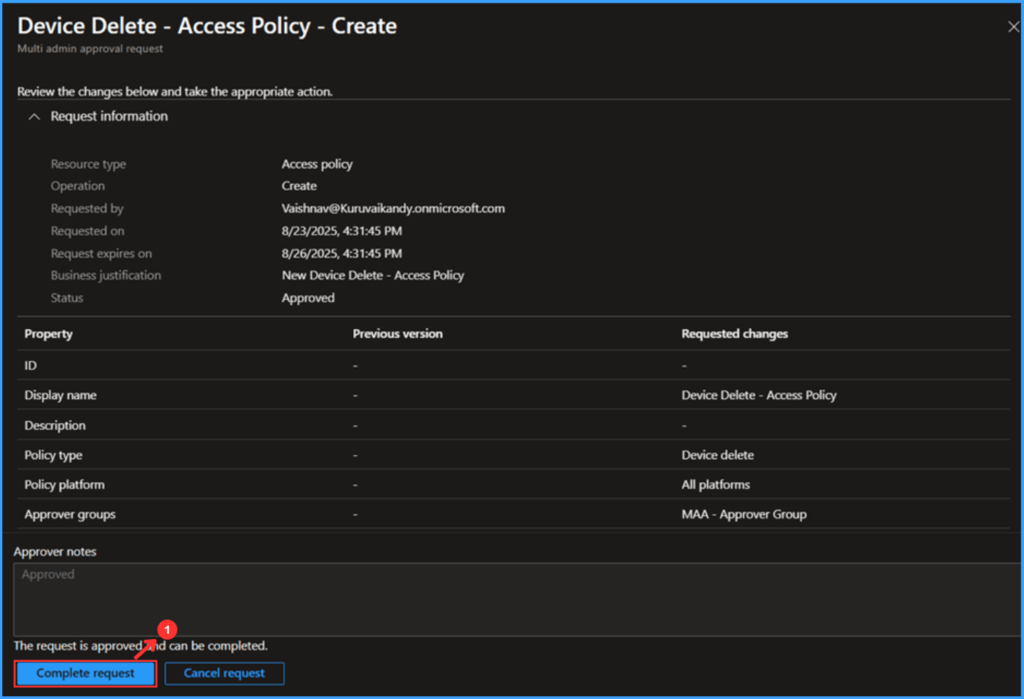
After the other Admin approves your request, you can complete it by navigating to Tenant administration > Multi Admin Approval > My requests, then clicking on Device Delete – Access Policy – Create.
- Explore Microsoft Intune Multi Admin Approval MAA Scenarios | What is MAA in Intune?
- How to Create New Platform Specific Device Clean-up Rule in Intune
- How to Create Autopilot Device Preparation Policy for Windows 365 Frontline Devices using Intune
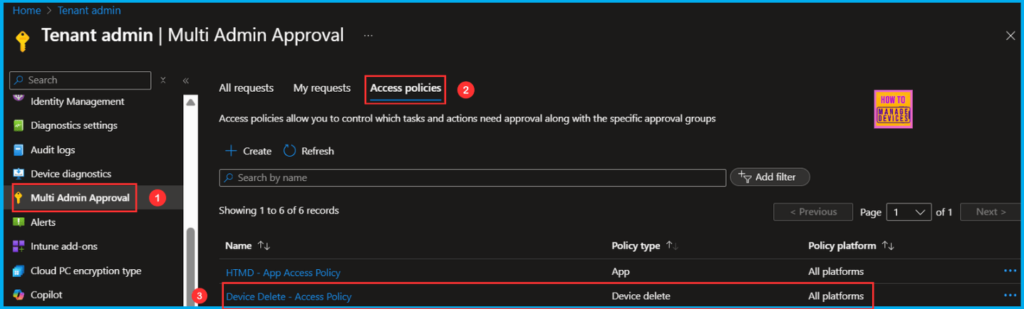
The new Device Delete – Access Policy has been created successfully. We can find this under Tenant administration > Multi Admin Approval > Access policies tab.
Intune Admin Experience
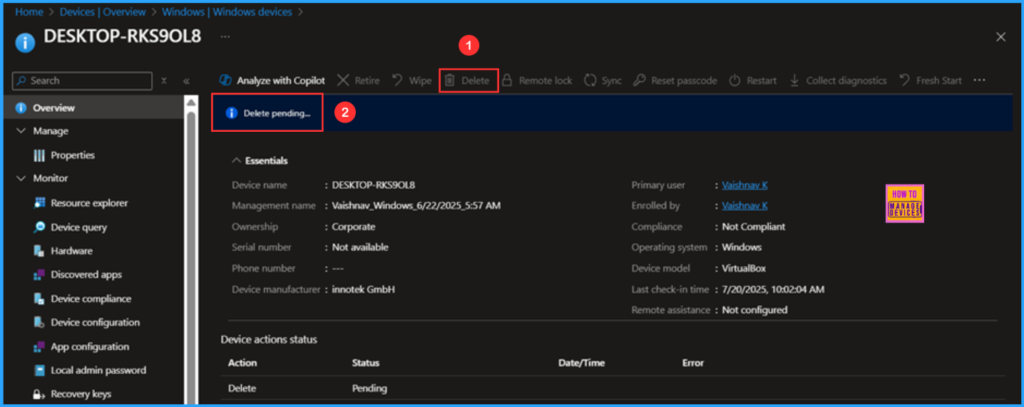
It’s time to review the functionality of this policy. From now on, whenever you delete any Intune enrolled devices from the Intune Admin Center, you will be required to submit a Multi Admin approval. The delete action will remain in a pending status until another admin approves or denies the request.
In this example, I am trying to delete a device named DESKTOP-RKS9OL8. However, the action is still showing as “Delete pending” due to the MAA access policy. Therefore, we can conclude that our policy is functioning as expected.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has 12 years of experience in SCCM, Intune, Modern Device Management, and Automation Solutions. He writes and shares knowledge about Microsoft Intune, Windows 365, Azure, Entra, PowerShell Scripting, and Automation. Check out his profile on LinkedIn.


