Bonjour, fellas. Let’s learn how to Onboard Android devices to Microsoft Defender for Endpoint. We will explore the options for onboarding the Android device to MDE. As you know, Android devices can be enrolled in different ways; we will discuss the onboarding process for each enrolment type.
Most organizations will proactively protect endpoints like Laptops/PCs, but they leave Mobile devices unmonitored. Mobile OS has built-in protection features like app isolation and encryption. However, these mobile devices are vulnerable to web-based attacks. As the usage of Mobile devices for work-related tasks increases daily, organizations are focusing on how to protect mobile devices.
Microsoft Defender for Endpoint on Android and iOS devices is Microsft’s Mobile Threat Defense Solution. It provides actionable, near real-time threat and advanced attack detections. When a threat is detected, MDE creates alerts in the system to investigate. It logs the incident, and at the same time, MDE also provides remediation to the threats and attacks.
Our previous blog taught us about Onboarding iOS/iPad OS Devices to Microsft Defender for Endpoint. Microsoft Defender provides solutions for web-based attacks and malware protection by scanning applications, networking protection, Microsoft Defender vulnerability management, integration with Microsoft Tunnel, and unified reporting.
Onboard Android Devices to Microsoft Defender
As we all know, Intune supports various enrollment options for Android devices, such as Android Device Admin and Android Enterprise. Microsoft Defender for Endpoint on Android supports Android Enterprise enrolled devices except for Corporate Owned dedicated devices. To onboard Android devices, we need to follow the steps below.
- Deploy the Microsoft Defender application as a required app.
- Create Application Configuration policy for Defender
- Create a Configuration profile for Auto Setup of Always-on VPN
- Onboard the Android devices
Deploy the Microsoft Defender Application as a Required App
To protect Android devices, deploying the Microsoft Defender app as a required app for devices that enrol on Intune is always advised. So, let’s deploy the Defender app for Android enterprise devices. The DDefender application is readily available in the Play Store, and we will deploy the app from the Managed Playstore, as shown in the below steps.
- Sign in to Microsoft Intune Admin Center
- Click on Apps > Android > Android apps
- Click on Add Apps and select Managed Google Play App under App type
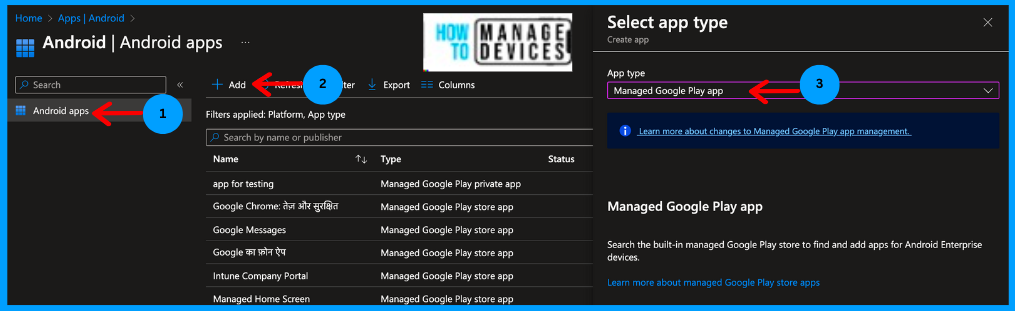
Click on Select and search for the Microsoft Defender application in the Manage Google PlayStore view, and click on Select and click on Sync. This will add the MS Defender application to the Android Applications in the Intune list. please wait for a while, and the app will be shown in the list
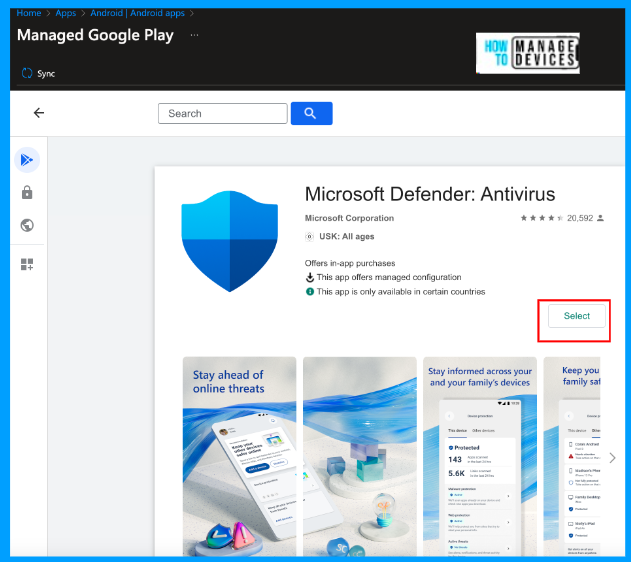
Now select the app and click on Properties. If you want to edit the app information, you can click on edit next to the App information. As we want to assign the application to the defender users, click on edit next to Assignments
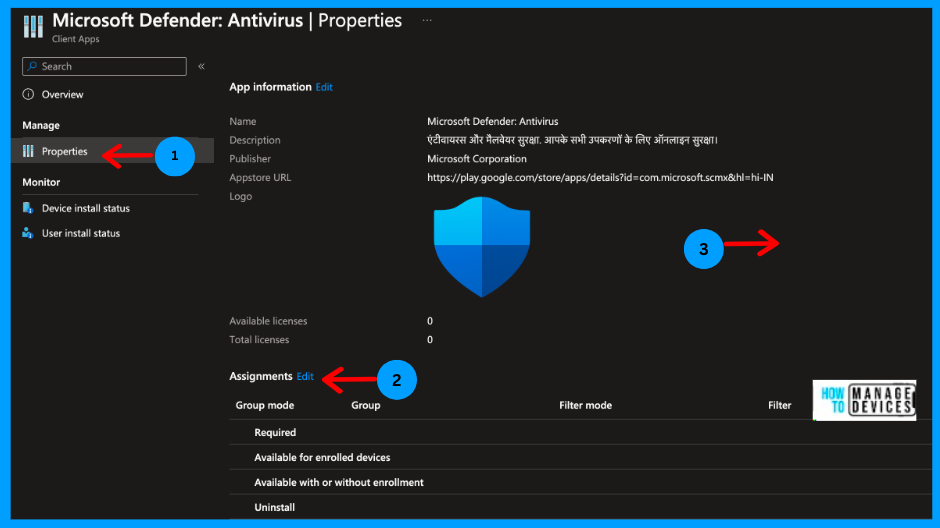
Now, under Required assignment type, click Add group and search for the group to which we need to assign the defender application. Click on Select, click Next to Review and Save the changes
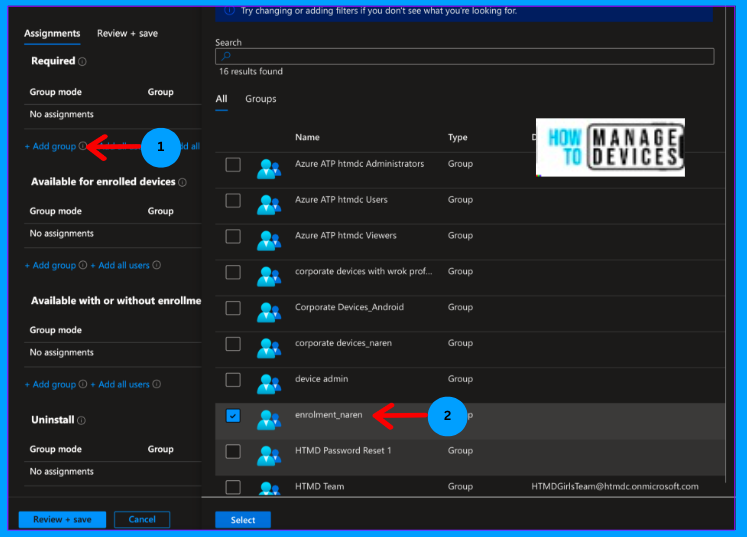
On the Review+save page, review the groups. Add the user under the exclusion if you want to exclude any user group. Validate the changes you made and click on save the changes. Now, we have successfully assigned the Defender application to the users.
Create Application Configuration Policy for Defender
Now, we need to create an Application Configuration for the Defender application to control the Application features. Defender for Endpoint supports App configuration policies for managed devices via Microsoft Intune. Let’s look at the steps to create the application configuration.
- Sign in to Microsoft Intune Admin Center
- Click on Apps > Application Configuration Policies
- Click on Add > Managed Devices
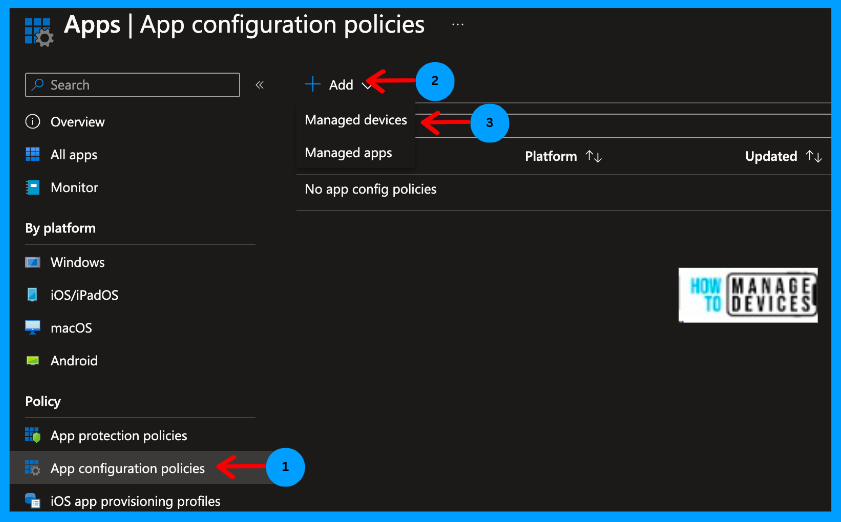
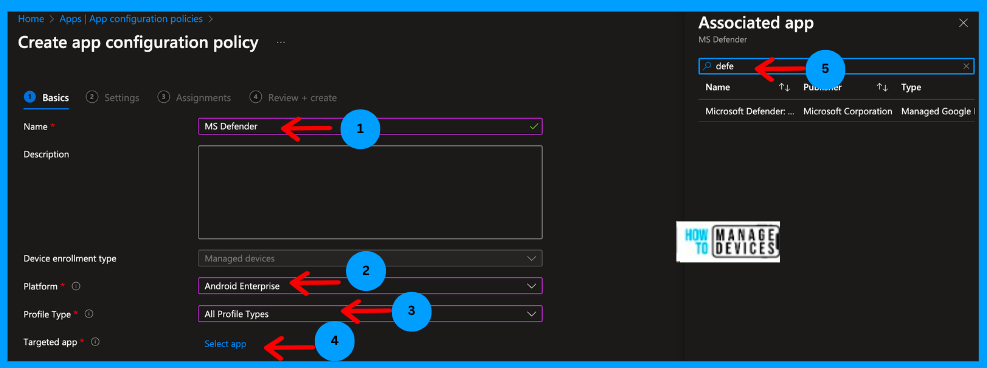
Under the Create App configuration policy page, please provide the policy’s Name and Description and select the Platform as Android Enterprise and the Profile Type as All Platforms. We can choose whether the policy is for Android for Work devices or Fully Managed, Dedicated, or corporate-owned devices with a Work profile. Now, select the app as Defender.
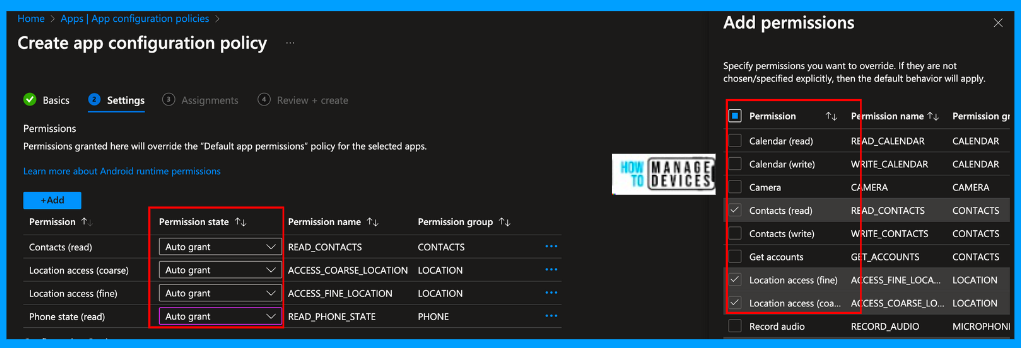
Click on Next. Under the settings page, we can configure the required permissions and configurations for the app. Click on Add under Permissions, and select the permission to be Auto Grant or Auto Deny. If we choose the Auto Grant App, we will not request permission from the users. I have chosen a few permissions.
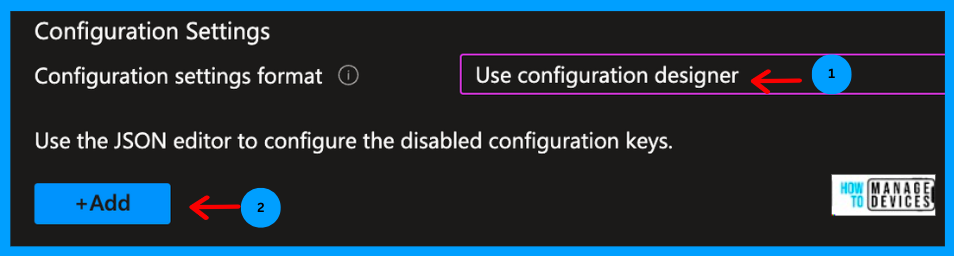
Now, let’s configure the app’s configuration under Configuration Settings. Select Configuration Settings format as Use Configuration Designer, and click Add to select Configuration settings from the configuration page.
Now, in the Configuration Designer pane, you can view all the configurations that can be configured for the Defender app. Select the required configurations according to your requirements. I have selected Anti Phishing(works only for Fully Managed or corporate devices with work profile), Network, Defender in Personal Profile, and VPN configurations.
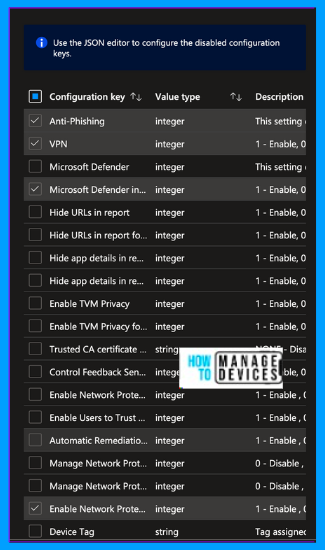
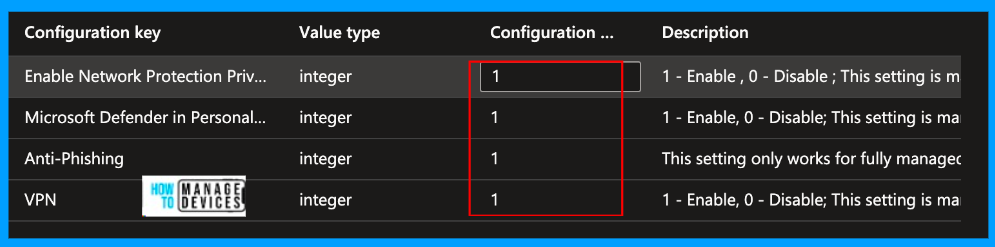
Click OK after selecting the required configurations, and you can view all the configurations you have chosen. Now, we need to add the configure Value, which is an integer value; 1 enables the configuration, whereas 0 disables it. I have enabled a few configurations, as shown in the screenshot below.
- Enable Network Protection
- Microsoft Defender in Personal Profile
- VPN
- Anti-phishing (works only for Fully Managed or corporate devices with work profiles)
Click Next to move to the Assignment page. Here, click Add Groups and add the user group to which we need to deploy the configuration profile. You can exclude any user group under the exclude section if you want to exclude any user group.
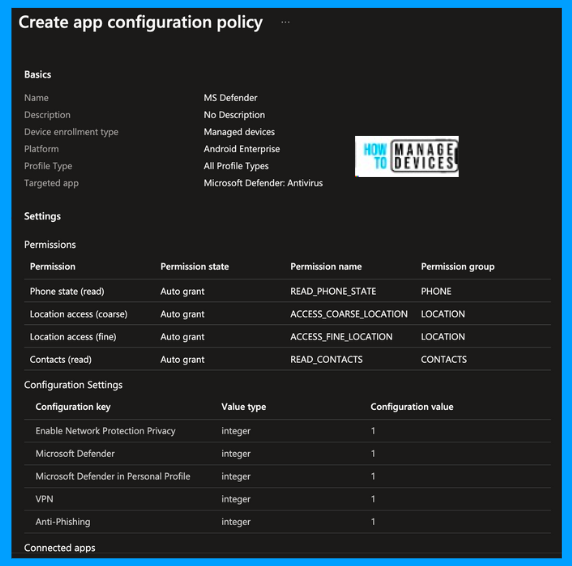
Click Next to Review+Create page, review all the settings configured, and click on Create. This will create the App configuration policy, and users who enrol the devices will get the configuration profile on their devices. Now, we have completed two major Admin tasks: App Deployment and App Configuration. The only remaining task is to create an Always-on VPN profile.
Create a Configuration profile for Auto Setup of Always-on VPN.
Microsoft Defender supports Device configuration policies for managed devices via Microsoft Intune. We can use this option to create a VPN profile, which eliminates the step of creating a VPN by users while onboarding the devices.
- Sign in to Microsoft Intune Admin Center
- Click on Devices > Configuration
- Click on Create > New Policy
- Under Platform, select Android Enterprise > select Device Restriction under Profile.
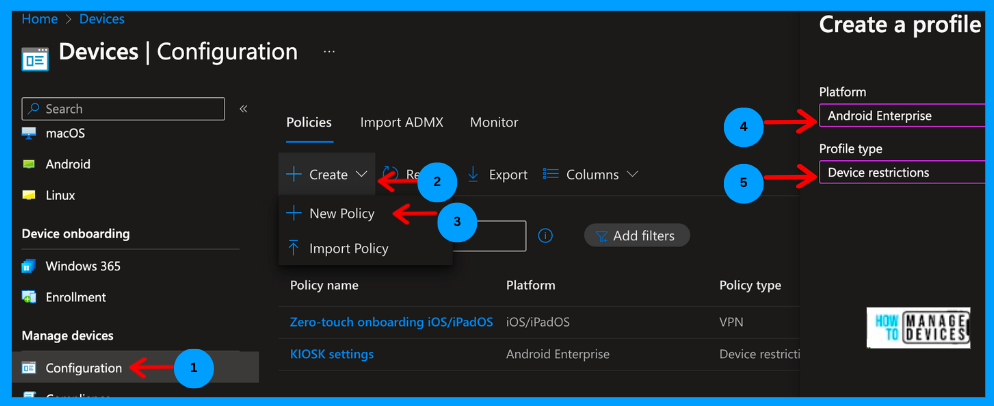
Click on Create. On the basics page, provide the Name and Description of the policy. You can validate the Platform and Profile type as Android Enterprise and Device Restrictions, respectively. Now click on Next to proceed to the Configuration page.
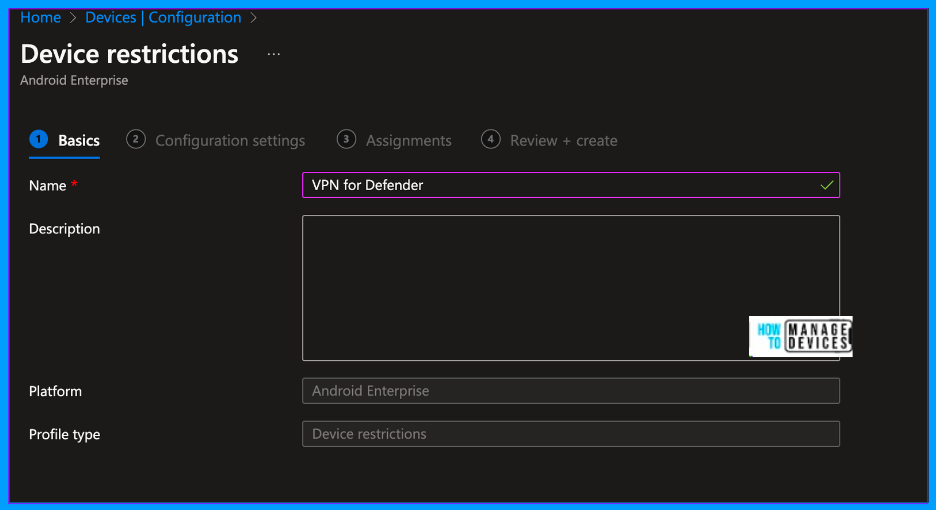
On the Configuration Settings page, you can view multiple categories. Select the Connectivity category and click on Enable Always-on VPN. Now, we must provide the VPN Client and select it as Custom. Once we select Custom, we need to provide the package ID of the custom VPN client. The package ID for the Defender application is com.microsoft.scmx.
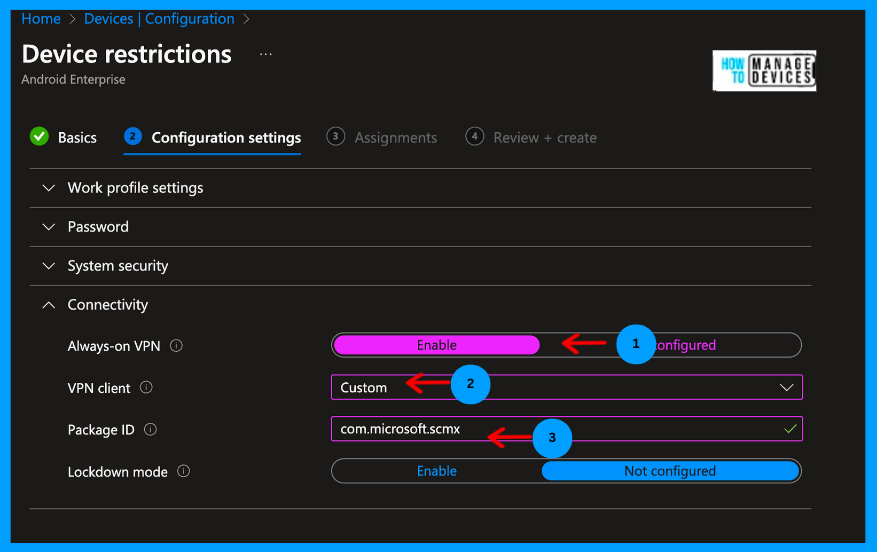
Note! The Defender app must be installed on the user’s device to auto-setup the VPN. Therefore, we are pushing the Defender app as the required application.
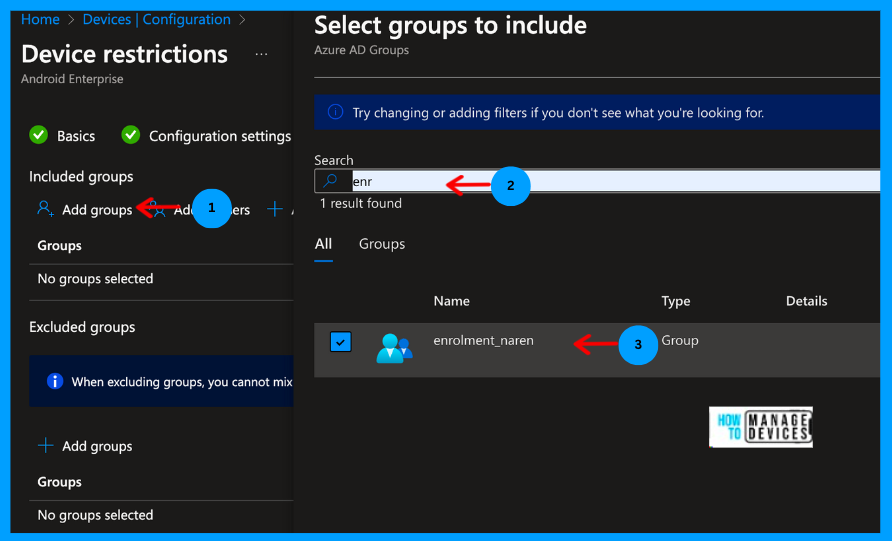
Click Next to move to the Assignment page. On the Assignment page, assign the group to which we must push the device restrictions. Ideally, it should be the same group to which we have assigned application configurations and pushed the Defender app.
Now click Next to the Review+create page. Validate the configured settings, and if any changes are required, click on edit and make changes. Once everything is ready, click on Create. This will create the policy.
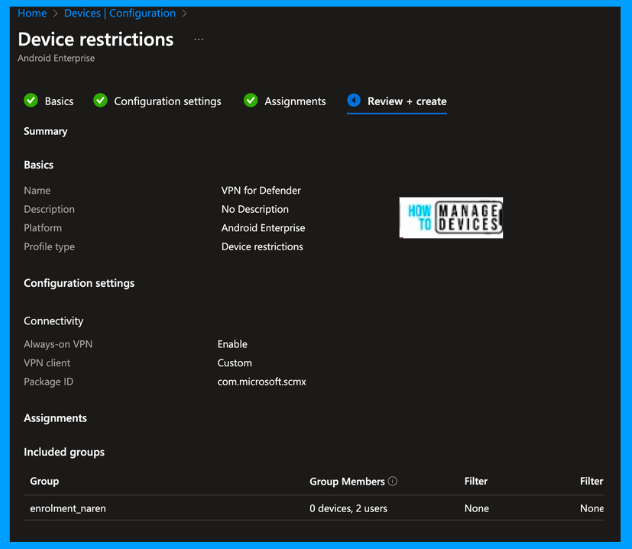
We have completed all the required configurations to onboard the Android devices to Microsoft Defender for Endpoint. In the section below, let’s examine the user experience.
User Experience
As we have created the profile for Android enterprise devices with a work profile, let’s enrol a device in Intune with a Work profile. The user experience for fully managed and Corporate devices with a Work profile will be the same as Android for Work profile devices.
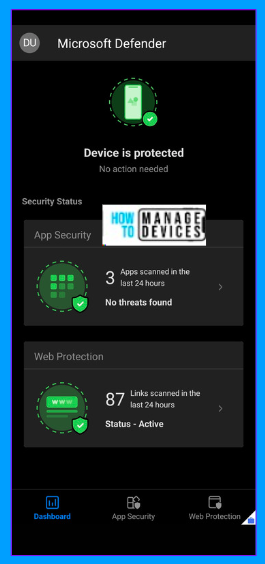
As soon as I enter credentials, the user is shown the Dashboard. The Defender app scans the device and shows it in the Dashboard, as shown in the screenshot above. If the user tries to access any malicious site, it flags the site and blocks access to it.
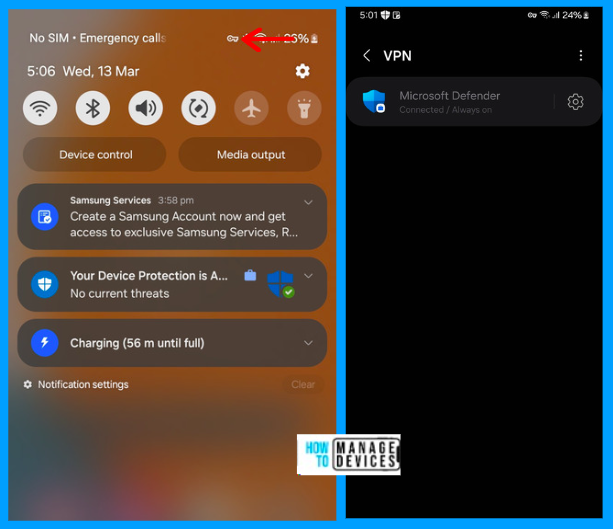
As we set Auto VPN, the user’s device will always be on VPN. You can verify the same by going to the device settings and VPN settings. So, the device is onboarded successfully, and internet traffic is monitored for malicious sites. The Defender does not track personal information.
Monitor Onboarding in the Defender Portal
In the above, we have seen the user experience. Now, let’s see how the admins can check if the devices are onboarded in the Defender portal. Let’s see the steps below.
- Sign in to the Microsoft Defender portal
- Click on Assets > Devices
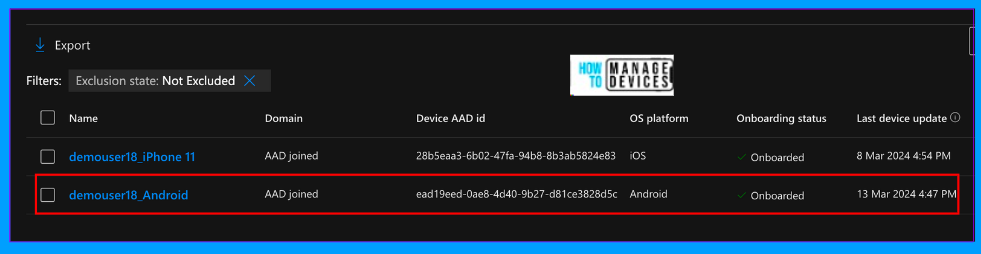
I have two devices, one iOS and the other one Android. In the same, you can see onboarded status as Onboarded. This way, we can Onboard the devices to Microsoft Defender for Endpoint. If there is an update for a device, it will also show a flag to update the device.
Conclusion
It is always better to onboard Android devices to Defender to protect organizational data. The Defender, on the other hand, monitors the device but never tracks/shares personal usage. I hope you like the article. We will meet again in another post. Till then, have a happy learning.
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here – HTMD WhatsApp.
Author
About Author – Narendra Kumar Malepati (Naren) has 11+ years of experience in IT, working on different MDM tools. Over the last seven years, Naren has been working on various features of Intune, including migration from different MDMs to Intune. Naren mainly focuses on Android, iOS, and MacOS.
