Today, we are discussing Password Spray Activity from CovertNetwork–1658 Infrastructure. As you all know, cybersecurity is high today, and we have to be more careful and take better security measures to prevent this. Recently, Microsoft shared the details on the Password Spray Activity from CovertNetwork-1658 Infrastructure.
Password spray activity is a very common cyber threat that has been happening for a long time. This attack method involves using many passwords on one account, but attackers use a few common passwords on many accounts to avoid detection.
As you know, CovertNetwork-1658, also known as Botnet-7777, is a network of compromised devices, mainly TP-Link routers, controlled by Cyber attackers. CovertNetwork-1658 includes internet addresses used by some Chinese threat actors and consists entirely of hacked devices. Microsoft believes that a threat actor in China has set up and managed this network.
Password Spray Activity from CovertNetwork-1658 Infrastructure is a way to show users how we have to ensure security measurements and how cyber threats are increasing. In this post, we can look at an overview of the Password Spray Activity from CovertNetwork-1658 Infrastructure and discuss its benefits.
Table of Contents
What is Password Spray Activity?
This type of Password Spray Activity always depends on the cybercrime that occurs when the Cybercriminal gains unauthorized access to accounts and networks. It’s a brute-force attack in which the attackers try common passwords for different accounts.
Password Spray Activity From CovertNetwork-1658 Infrastructure
Above, we discussed an overall view of Password Spray Activity from CovertNetwork-1658 Infrastructure. CovertNetwork-1658 makes it difficult for cybersecurity professionals to determine the low volume of attacks and botnets spreading. Once the account information reaches the attackers, security has to be compromised.
- It is challenging to detect low-volume attacks.
- So the user can take some action against these types of attacks
- One of our best solutions is to provide the strongest passwords for accounts.

- Online Scams and Attacks Stay Informed and Protect Yourself
- 40% of All Incoming emails Pose a Potential Cybersecurity Threat
- XSPM vs XDR Illustration in Microsoft Security Stack
Password Spray Campaigns from CovertNetwork-1658
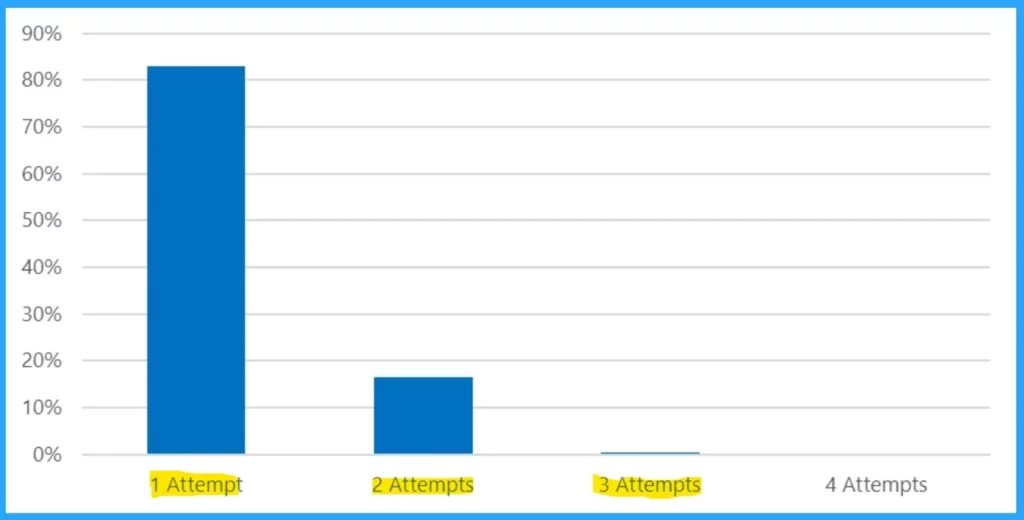
Recently, Microsoft has noticed many Password Spray attacks from CovertNetwork-1658. In this case, attacks, such as CovertNetwork-1658, make few sign-in attempts to many accounts in a target organization. They try to sign in to each account 80% of the time daily.
- Attackers always use different IP addresses.
- A device in CovertNetwork-1658 usually stays active for about 90 days.
- The password spray process involves very few sign-in attempts, making it hard to detect with monitoring systems that look for multiple failed attempts from one IP address or account.
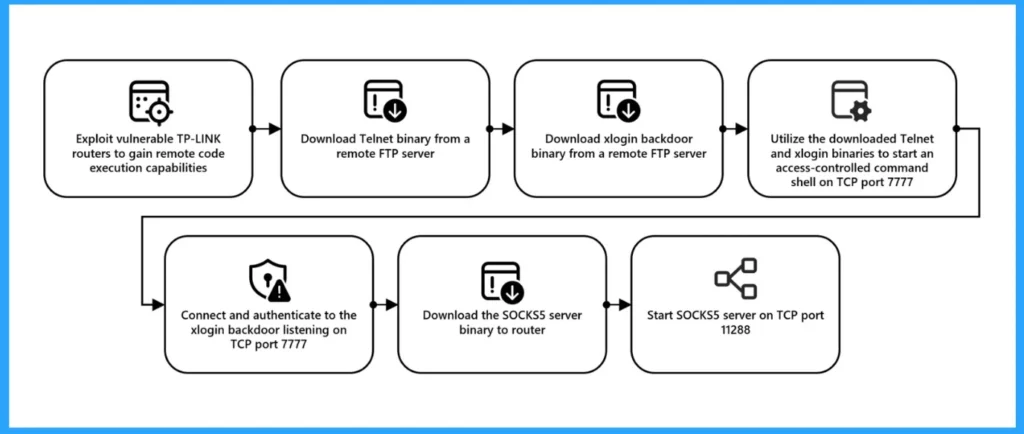
Microsoft believes that a threat actor in China created and managed this network, exploiting issues in the routers to run code remotely. Multiple Chinese threat actors use the login information gained from CovertNetwork-1658’s password spray attacks for cyber operations.
| No. | After Compromising Routers |
|---|---|
| 1 | Download the Telnet program from a remote FTP server. |
| 2 | Download the xlogin backdoor program from a remote FTP server. |
| 3 | Use the Telnet and xlogin programs to set up a command shell on TCP port 7777. |
| 4 | Connect and log in to the xlogin backdoor on TCP port 7777. |
| 5 | Download a SOCKS5 server program to the router. |
| 6 | Start the SOCKS5 server on TCP port 11288. |
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for ten consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
