Hi, In this post, we are discussing the XSPM vs XDR Illustration in Microsoft Security Stack. As you all know, cybersecurity is essential for every user. Many security features are used to secure organizational data. This post mainly discusses the most critical XSPM and XDR crucial in enhancing organization security.
XDR (Extended Detection and Response) is the best cybersecurity system that provides smooth detection and response capabilities. Microsoft Defender XDR is essential to enterprise defence; it will help detect, prevent investigation, and respond to the Endpoint.
Do you know about XSPM? XSPM stands for Extended Security Posture Management. It’s a method used in cybersecurity to monitor, diagnose, and improve organizations’ security posture. XSPM is also designed to identify organisations’ challenges in managing their security posture.
XDR and XSPM are two essential parts of the Microsoft security stack, as you can see in the illustration of various Microsoft security stacks. They’re beneficial for IT admins to check security weaknesses, analyse security threats, and provide information about Security risks. This post can discuss some comparisons between XSPM and XDR in the security stack.
- Protect Unmanaged Android Devices with Microsoft Defender for Endpoint
- MDE Microsoft Defender for Endpoint Telemetry Issues
- Microsoft Sentinel is the Best Tool for Security Information and Event Management, as per the Gartner Report

XSPM vs XDR Illustration in Microsoft Security Stack
Above, I mentioned a brief explanation of XDR and XSPM. They both have very crucial features to enhance the organization’s security. XSPM is the best tool for improving the organization’s security posture. XDR and XSPM are cybersecurity tools, so we can compare them in a table.
| XDR | XSPM |
|---|---|
| Microsoft Defender XDR focuses on threat detection and response | XSPM is about managing and improving the security posture of an organization |
| XDR combining all signals across the endpoint | XSPM is a comprehensive approach to cybersecurity that addresses challenges faced by legacy validation methods. |
| It utilizes automation for continuous monitoring and threat detection. | It combines continuous automated red teaming (CART), purple teaming, breach and attack simulation (BAS), and attack surface management (ASM) |
| XDR will detect threats but may not optimize the existing security posture | XSPM helps organizations identify critical threats, assess risks, and optimize their security investments effectively |
| The XDR plays a crucial role in enterprise defence detection, preventing investigation and responding to the Endpoint. | XSPM offers a wide range of clear visibility and optimization of cybersecurity investments. It is helpful for security professionals to improve security measures. |
See More: Microsoft Security Exposure Management using Defense Techniques
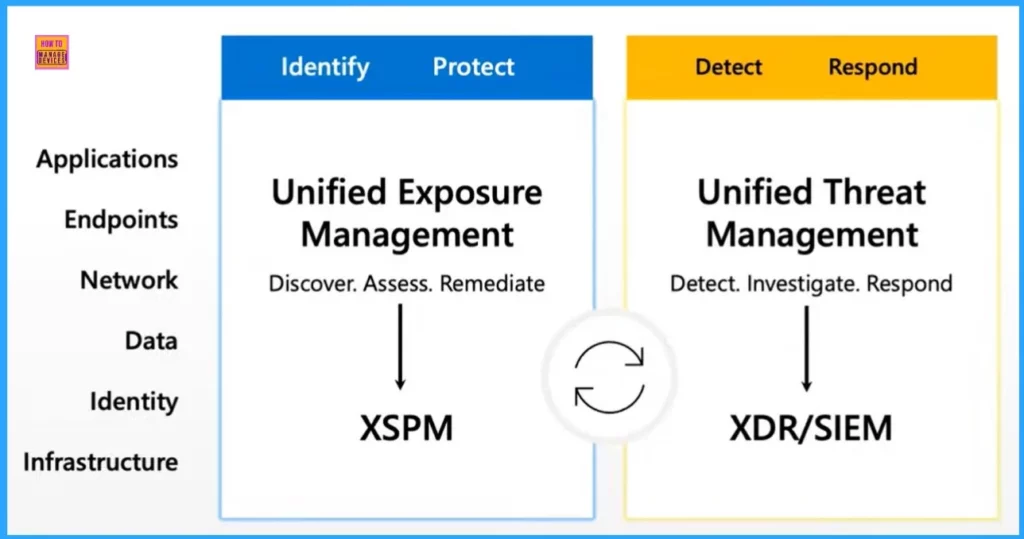
- XSPM identifies potential exposures across applications, endpoints, networks, data, identity, and infrastructure.
- Unified Exposure Management – XSPM – Discover, Assess and Remediate
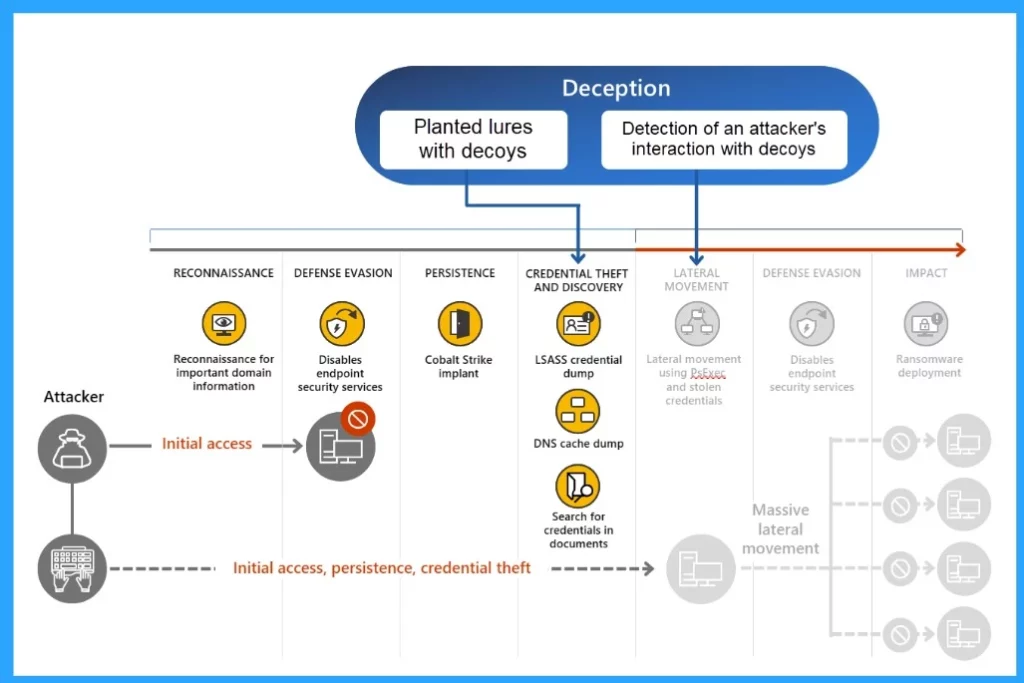
The XDR has recently integrated a powerful cybersecurity defence tool with the deception capability. Deception technology generates high-confidence alerts by leveraging deception signals correlated with Microsoft Defender for Endpoint data.
See More: What is Microsoft Defender XDR?
- High Level Overview of Identity Protection in Microsoft Entra ID
- Protect Unmanaged Android Devices with Microsoft Defender for Endpoint
- 50% of Identities have Access to Full Access as per Microsoft Security Report 2024
Marko Lauren recently posted a comparison of XSPM and XDR on his social media page (he is a Cyber Security Technical Specialist at Microsoft). In the screenshot below, he explains that XSPM is about managing and improving an organization’s security posture. At the same time, XDR extends detection and response to include proactive threat and incident response across various domains.
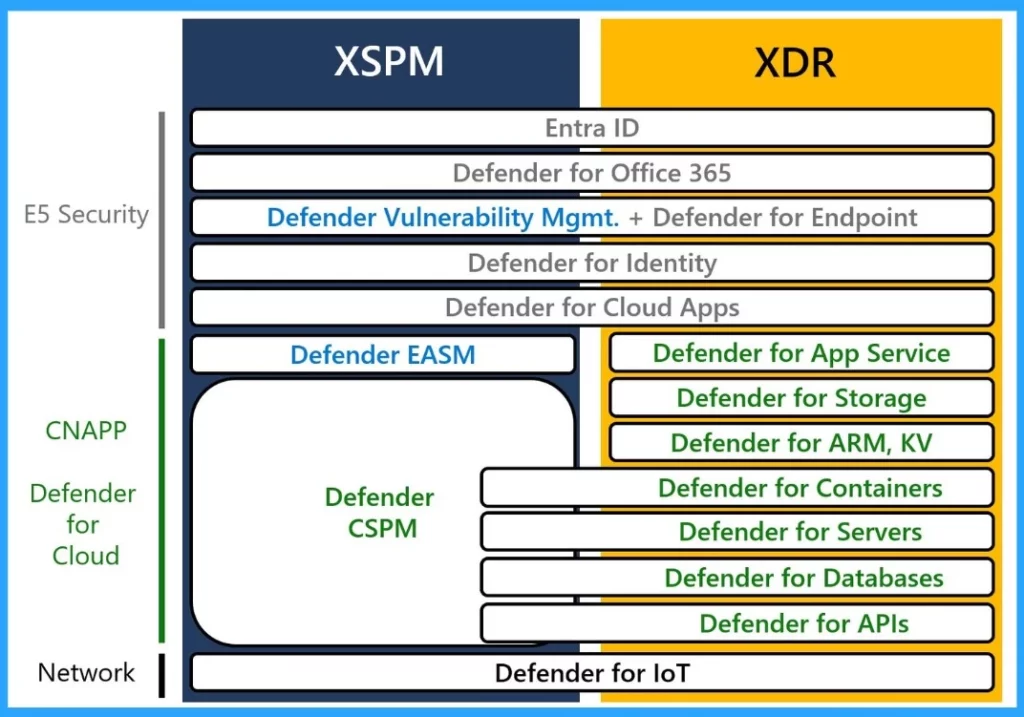
- E5 Security– will Provide components related to end-user Extended Detection and Response (XDR) and posture.
- CNAPP Defender For Cloud – It allows hybrid and multicloud XDR and posture capabilities
- Defender For IoT – It explains the XDR and posture for IoT and Operational Technology (OT) environments.
- Defender EASM – Monitors your external attack surface
- DefenderVulnerabilityManagement – An add-on that extends core Microsoft Defender for Endpoint (MDE) vulnerability management capabilities.
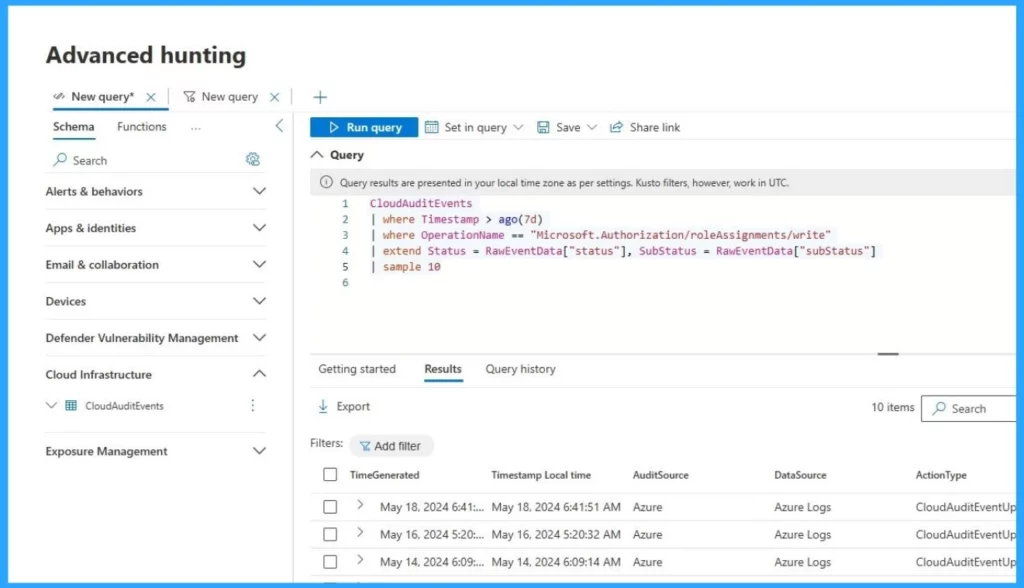
Advanced Hunting Capabilities for Microsoft Defender for Cloud
Advanced Hunting Capabilities for Microsoft Defender for Cloud is a feature that is now in public preview. This feature allows the security professional to hunt threats in various Microsoft services proactively.
This feature mainly focuses on Query-Based Threat Hunting. It allows 30 days of detailed records of data to find signs of security threats.
- XDR’s advanced haunting capabilities now include Defender for Cloud alerts and incidents in its advanced hunting features.
- This integration allows security teams to hunt across cloud resources, devices, and identities in a single query.
- Another feature, the ‘CloudAuditEvents’ table in advanced hunting, enables you to search through cloud audit events in Microsoft Defender for Cloud.
- Security analysts can run their KQL queries on their cloud infrastructure control plane logs.
- The security system can also set up custom alerts to spot unusual Azure Resource Manager and Kubernetes activities.
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Krishna. R is a computer enthusiast. She loves writing about Windows 11 and Intune-related technologies and sharing her knowledge, quick tips, and tricks about Windows 11 or 10 with the community.
