Let’s discuss What is Microsoft Defender XDR?. The latest news is the introduction of a built-in Deception capability. Microsoft Defender XDR is a unified security platform that provides comprehensive visibility, investigation, and response across the entire cyberattack chain.
Microsoft Defender XDR is a comprehensive enterprise defence designed to coordinate detection, prevention, investigation, and response across various domains, such as endpoints, identities, emails, and applications.
Microsoft Defender XDR’s deception technology produces high-confidence alerts by analyzing deception signals correlated with data from Microsoft Defender for Endpoint. It is a powerful solution that unifies security operations, enhances incident response, and protects your digital estate from advanced threats.
The deception capability integrated into Microsoft Defender XDR enhances cybersecurity measures. Also, we can say that this is the best and most important part of Microsoft Defender XDR to decoys (like digital traps) to catch and stop threats like malicious and tricky email scams.
- Protect Unmanaged Android Devices with Microsoft Defender for Endpoint
- Microsoft Defender ASR Rules to Block Rebooting Machine in Safe Mode
- MDE Microsoft Defender for Endpoint Telemetry Issues
What is Microsoft Defender XDR?
Microsoft Defender XDR now includes an integrated deception capability designed for cybersecurity defences. Deception technology generates high-confidence alerts based on deception signals correlated with Microsoft Defender for Endpoint data.
- The deception capability automatically generates decoy accounts, hosts, and lures that closely resemble real assets
- It involves deploying fake credentials, hosts, and decoys that appear to be high-value assets.
- When an attacker interacts with these decoys or lures, the deception capability raises high-confidence alerts.
| How the Deception Technology Works | Info |
|---|---|
| Decoy Creation | Deception technology involves creating decoys or fake assets within an organization’s network. These decoys mimic real systems, services, or data |
| Strategic Placement | These decoys are strategically positioned throughout the network, mimicking real elements. |
| Alerting System | When attackers interact with these decoys (e.g., attempting to access a fake server or steal credentials), it triggers high-confidence alerts |
| Incident Integration | These alerts don’t exist in isolation; they seamlessly integrate into incidents within the Microsoft Defender XDR ecosystem, facilitating rapid and effective threat investigation. |
| Seamless Integration | Integrated with Microsoft Defender for Endpoint. Subscription Requirements Available for organizations with subscriptions like Microsoft 365 E5, Microsoft Security E5, or Microsoft Defender for Endpoint Plan 2. |
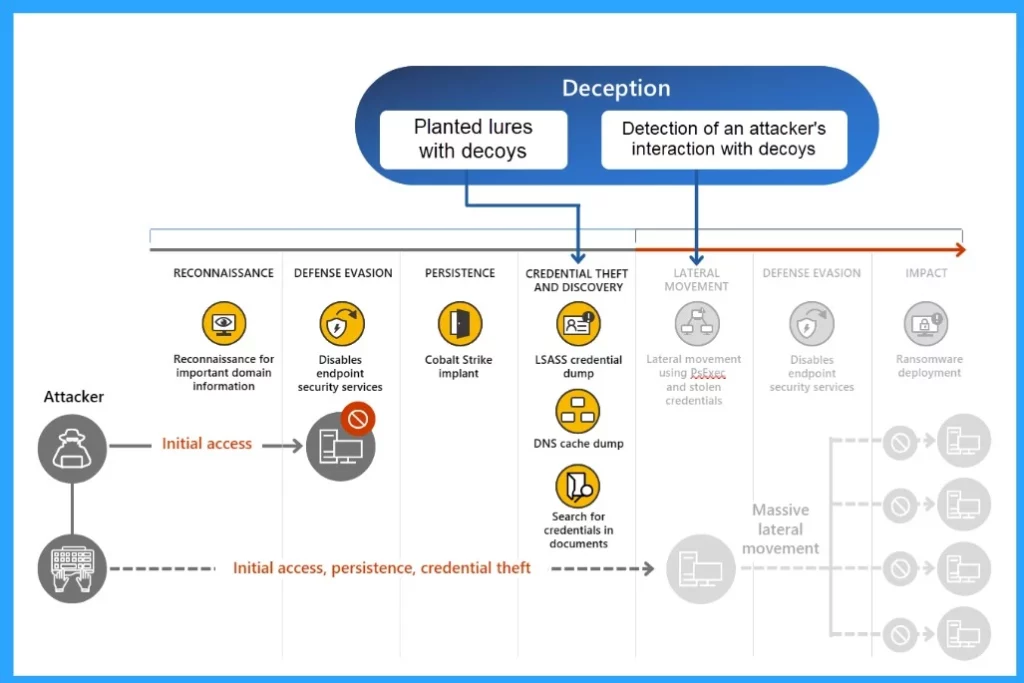
Defender XDR’s Deception Technology empowers security teams to identify attackers within the network proactively. By closely monitoring their interactions with decoy assets, this capability enhances detection and deepens the security team’s understanding of attackers.
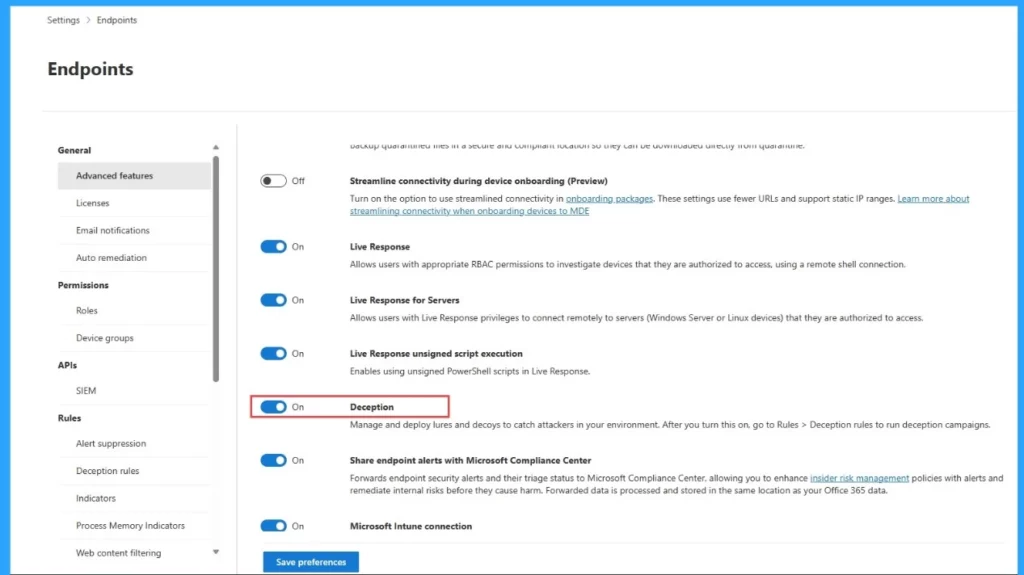
- Go to the Microsoft Defender portal at https://security.microsoft.com
- The Deception Capability is turned off by default.
- Select Settings > Endpoints.
- Under General, select Advanced features.
- In Deception capabilities, toggle the switch to On
- Microsoft Defender Antivirus Periodic Scanning in Windows 11
- Microsoft Defender Training and Certification
- Deploy Microsoft Defender for Endpoint Policies using Intune
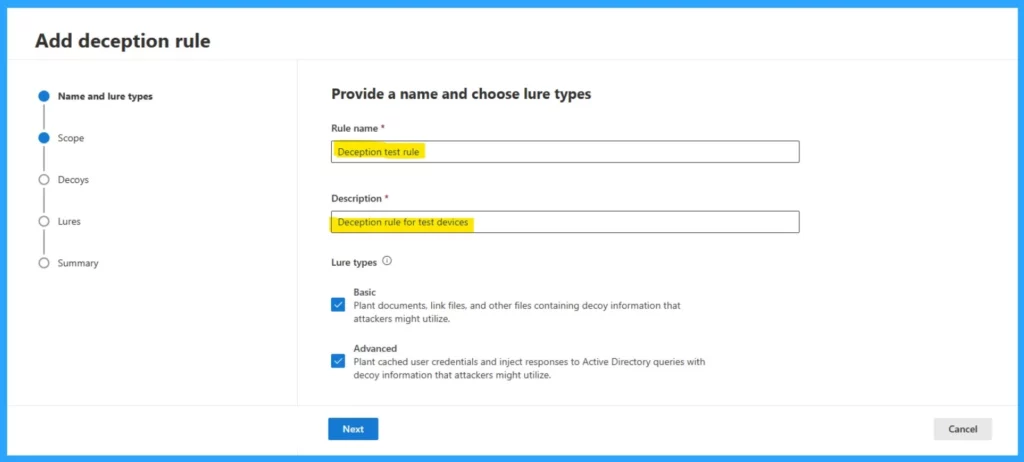
Microsoft Defender XDR currently supports the creation of 10 deception rules. You can easily set up deception rules by navigating to Settings > Endpoints. Under rules, select Deception rules. Click Add deception rule to create a new rule.
- Each rule can be a Rule Name, description, and specific lures
The Benefits for Security Teams
This feature allows security teams to proactively identify attackers within the network by monitoring their interactions with the decoy assets. It also enriches security teams’ understanding of attackers’ tactics and improves overall security posture.
Implementation Prerequisites
Organizations must have Defender for Endpoint as their primary EDR solution and meet specific deployment requirements, such as hybrid/fully joined devices in Microsoft Entra and PowerShell enabled on devices.
Reference
Configure the deception capability in Microsoft Defender XDR
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Krishna. R is a computer enthusiast. She loves writing about Windows 11 and Intune-related technologies and sharing her knowledge, quick tips, and tricks about Windows 11 or 10 with the community.
