Hi everyone. In today’s article, we will learn how to Protect unmanaged Android Devices with Microsoft Defender for Endopint. Mobile app management doesn’t require device management, and you can protect company data on both managed and unmanaged devices.
Not every organization wants to manage end users’ personal devices to access corporate data. So, these organizations manage only apps via App Protection Policies for Android and iOS devices. With the help of Application Protection policies, we can protect the corporate data lying inside the applications.
App Protection policies are a set of rules that restrict data transfer and ensure corporate data stays within the managed apps. Managed apps have App Protection Policies applied and are managed by Intune. Intune provides options to apply App Protection Policies for enrolled devices in Intune(managed devices) or those not enrolled or enrolled in other third-party MDM solutions.
Microsoft Defender for Endpoint on Android threat information can be managed/applied using the Intune App Protection Policies to protect the managed applications. In this article, we will use this feature of Intune to onboard Android devices to Microsoft Defender for Endpoint.
- Onboard iOS/iPadOS Devices to Microsoft Defender for Endpoint
- Use MTD To Protect IOS And Android Devices With Microsoft Defender For Endpoint
Integrate Microsoft Defender for Endpoint with Intune
To enable App Protection Policies to apply for threat protection and protect the devices by Microsoft Defender for Endpoint, we must integrate Microsoft Defender for Endpoint and Intune. We have covered the integration steps in a different article. You can refer to this article. Once the integration is completed, we can create an App Protection policy.
Create Filters for Deploying APP Protection Policies
Earlier, Intune supported the creation of app protection policies separately for managed devices(devices enrolled on Intune) and unmanaged devices(devices not enrolled on Intune). Now, Microsoft has changed the way and allows admins to have a single App Protection policy for these two kinds of devices and manage the assignment using Filters.
Filters in Intune can help us narrow down the scope of assignment of policies or configuration profiles we create. We can use filters to assign policies to a specific OS version or only to managed or unmanaged devices. The Filters are divided into two categories – Managed Devices and Managed Apps. Let’s create a Filter for Managed apps.
- Log in to Microsoft Intune Admin Center.
- Click on Tenant Administrator > Filters.
- Click on Create and select Managed Apps.
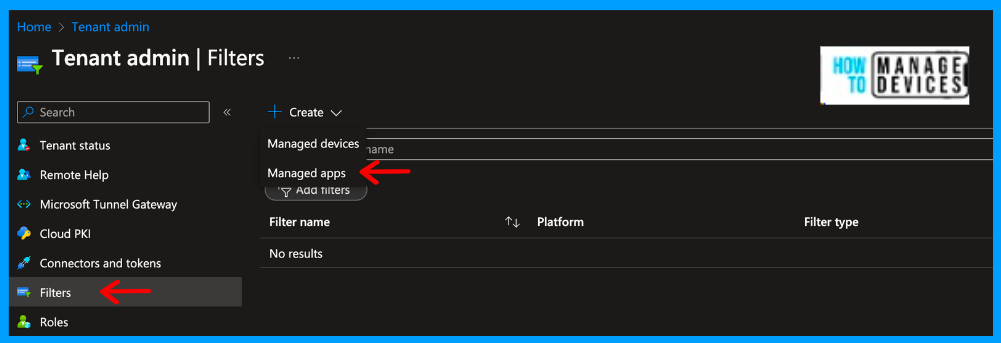
Now, on the Basics page, provide the Filter’s Name and description. Ensure you provide a proper name so we can use this FilterFilterere. After providing the details, click on the Next to Rules page.
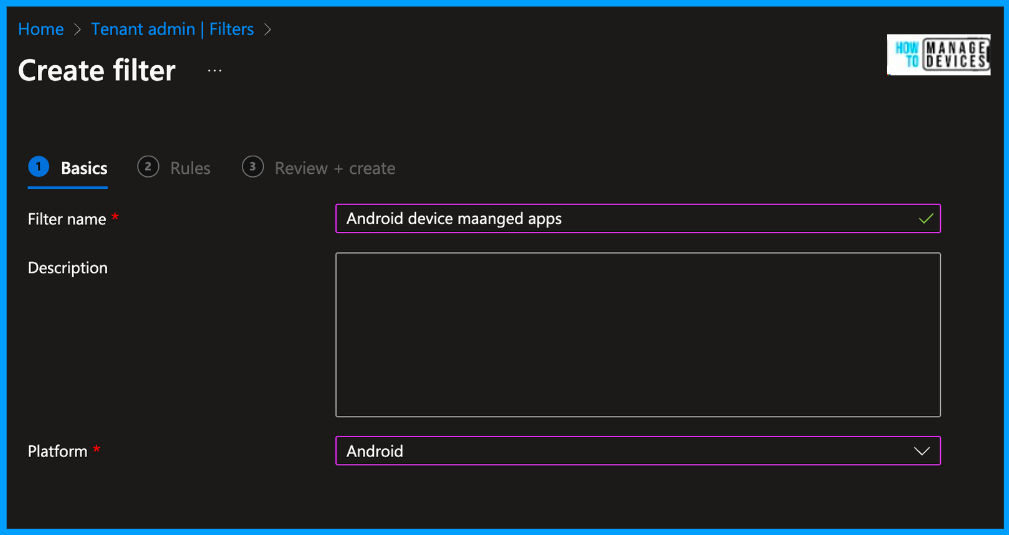
As we want to assign the App Protection Policies to unmanaged devices, we will now create a simple rule to filter out all unmanaged devices. Under the rule builder, select “deviceManagementType” and select the Operator as “Equals” and Value as “Unmanaged,” as shown in the screenshot below.
Now click on Next to move to the Review + Create page. Review the changes and rules created, then click on Create. This will create a filter of unmanaged devices.
Create an App Protection Policy to Protect Unmanaged Android Devices
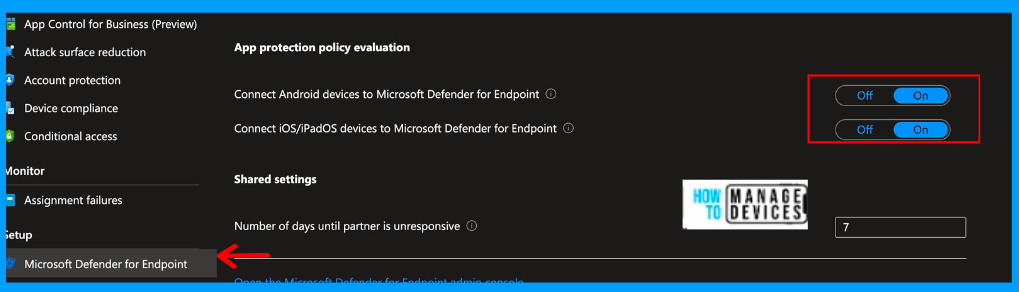
While Integrating the Microsoft Defender for Endpoint with Intune, we must also enable the App Protection policy Settings for Android and iOS. Intune will not use device risk details sent over this connector during app protection policies calculation for policies with a Device Threat Level configured if you do not enable this. You can refer to the settings in the below screenshot.
Now, let’s create an App protection policy to protect the managed apps on Android devices that are not enrolled in Intune. I’ll use a few applications like Outlook, Word, and Excel for our discussion. Let’s see the steps to create an app Protection policy below.
- Log in to Microsoft Intune Admin Center.
- Click on AApp App Protection Policies.
- Click on CrePolicyicy > Android.
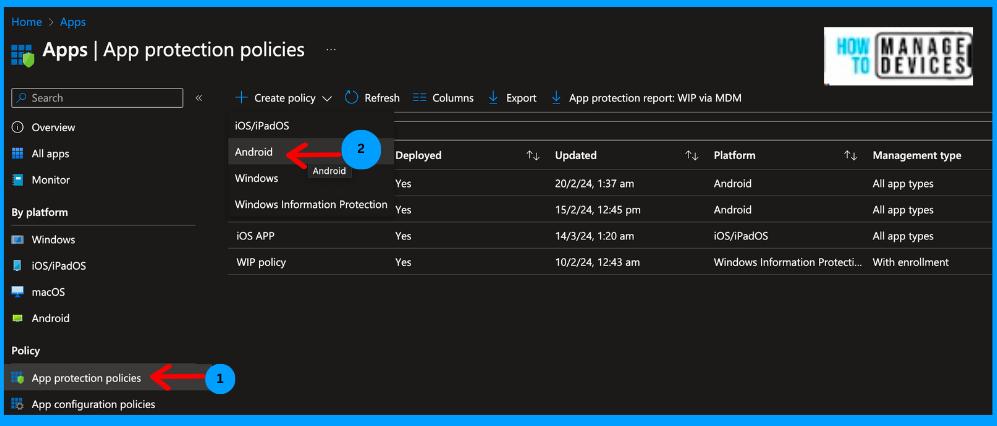
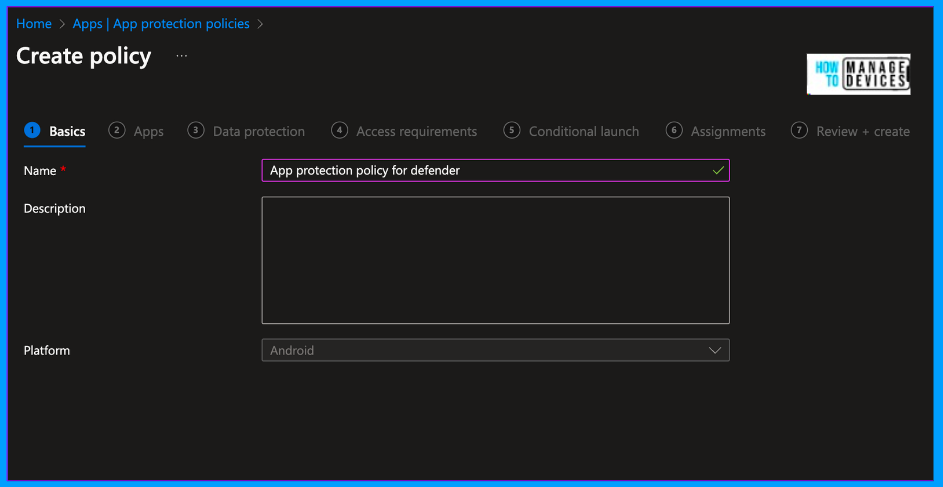
Now, provide a name and description for the App Protection Policies. You can also observe the platform as an Android. Click on the Next to Apps page. In order to understand the app protection policies, apps should be enabled or integrated with Intune SDK.
Most of the Microsoft applications support App Protection Policies as they are integrated with Intune SDK. We can also integrate Intune SDK for your Organizational Line of Business Applications, which requires code-level changes. If you wish to have basic App restrictions like cut, copy, and paste, we can wrap the Application with the help of the Intune App Wrapping Tool.
On the Applications page, we can select All Apps, All Core Apps, All Microsoft Apps, or Public Apps. I have selected Public Apps and selected a few apps, as discussed above. You can refer to the screenshot below for the apps I have selected.
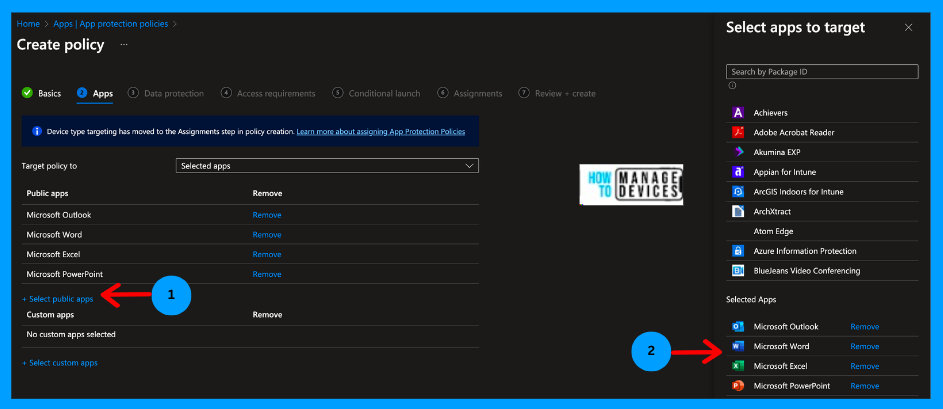
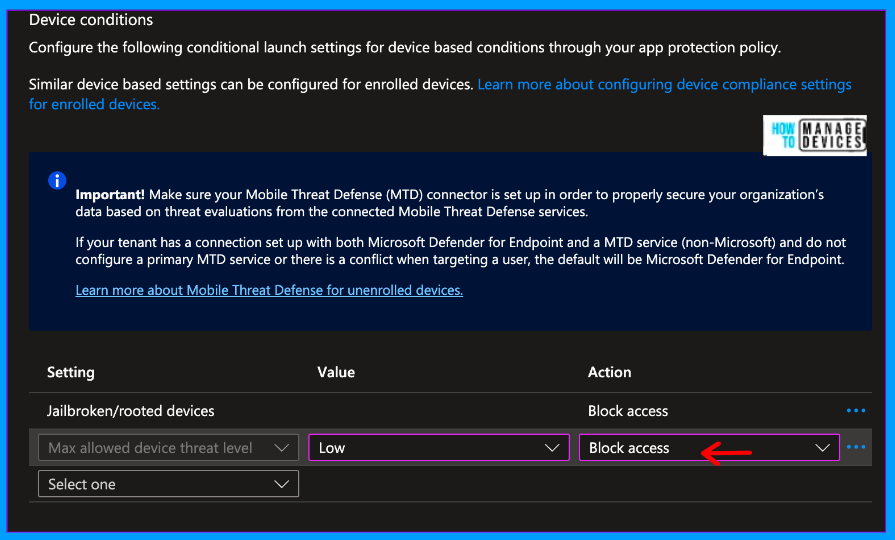
Click Next to the Data Protection page, and skip the settings on the Data Protection and Access Requirement pages, as we are focused on protecting the device with Defender. Click next on the Conditional Launch page under Device conditions, select Max allowed device threat level and define the value as either Low, Secured, Medium or High. Secured is more secure, and High is less protected.
Under the Action column, we can define either Wipe the data or Block access. Block Acess will block access if the device threat level meets the specified criteria. Wipe data will remove the App Data. I have selected Block access as an action.
Click Next to the Assignment page. Under the Assignment page, add the user group, and under the Filter, add the Filter we created in the above section to assign tPolicylicy to only unmanaged devices.
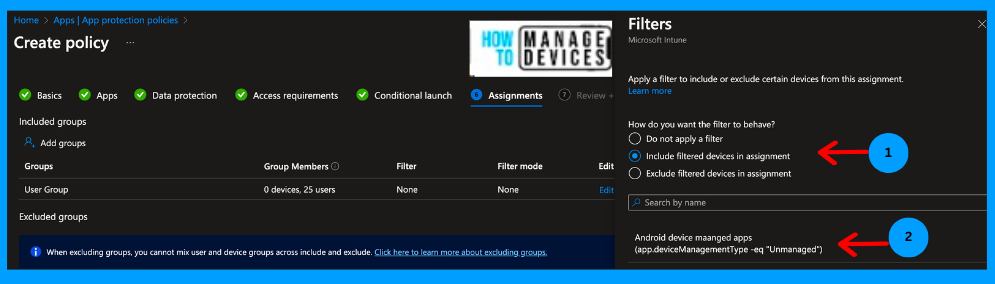
Click on the Next to Review + Create page, review all the changes made, and click Create to create the app protection policy for unmanaged devices. In the next section, we will see the user experience.
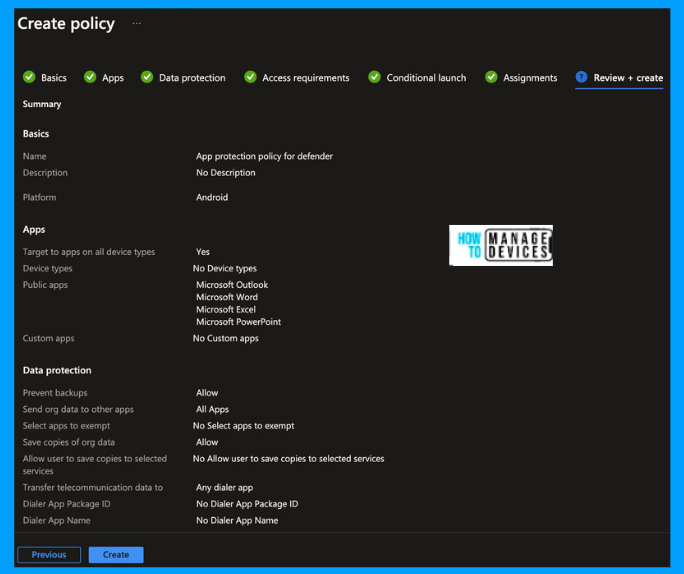
NOTE: If you have a conditional access policy that requires the device to be compliant to access corporate data, make sure you exclude the users accessing the corporate data on unmanaged devices from Policylicy. If we do not exclude them, they will be prompted to enrol in the device.
End User Experience
Now let’s see how the user can set up the App and how the Defender app protects the apps in this. As we have targeted more than four apps, I have selected Microsoft Outlook for our discussion. Download the Outlook app from PlayStore, open the App and Sign in. As soon as the App is authenticated, it detects that it has App Protection Policies prompted and asks the user to restart it.
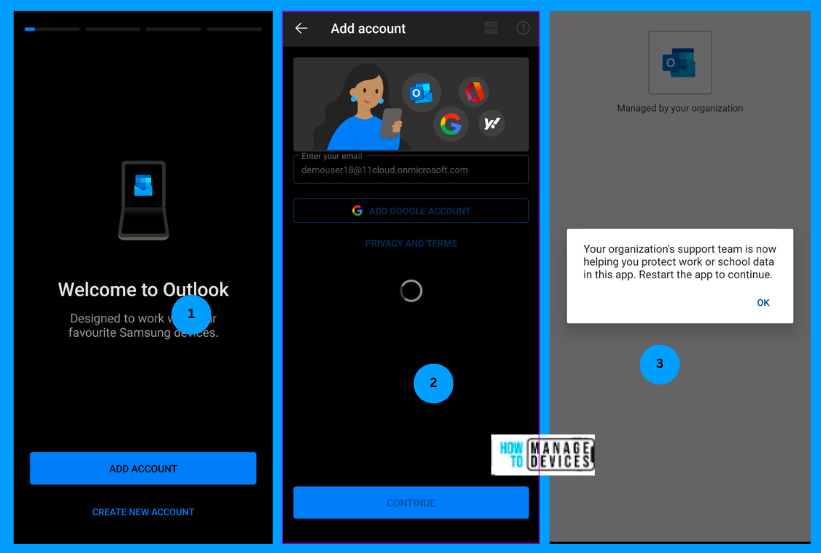
Android devices require installing the Intune Company Portal app to have App Protection Policies work. After the restart, I was prompted to install the Company Portal app, as I do not have it installed on the device. Once installed, it checks everything and finds the Device’s health status couldn’t be found. Click on Continue, and the user will be prompted to install the Microsoft Defender app to determine the Device’s Health.
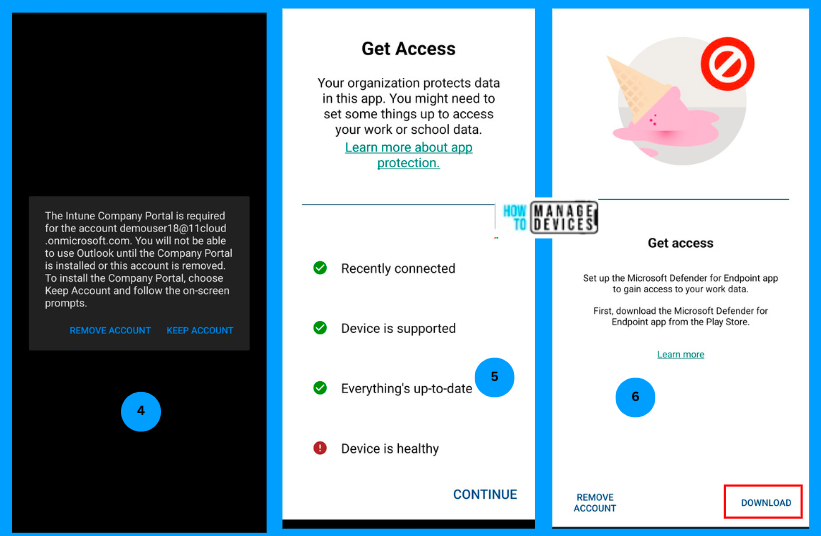
Click on Download. The user will be navigated to Playstore to install the Microsoft Defender application on the device. Once installed, click on launch. Defender app automatically fetches the user account information and asks the user to select the correct user.
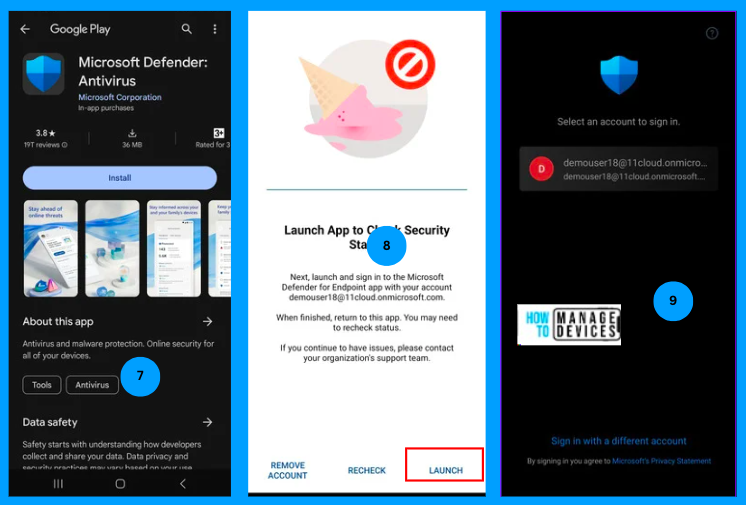
Once the user is authenticated, he or she is prompted to set up the Defender application. The user is prompted with multiple permissions for the App. We can suppress these permissions using the App Configuration Policy. Once all permissions are provided, the user is prompted to Open Outlook, as shown in the screenshot below.
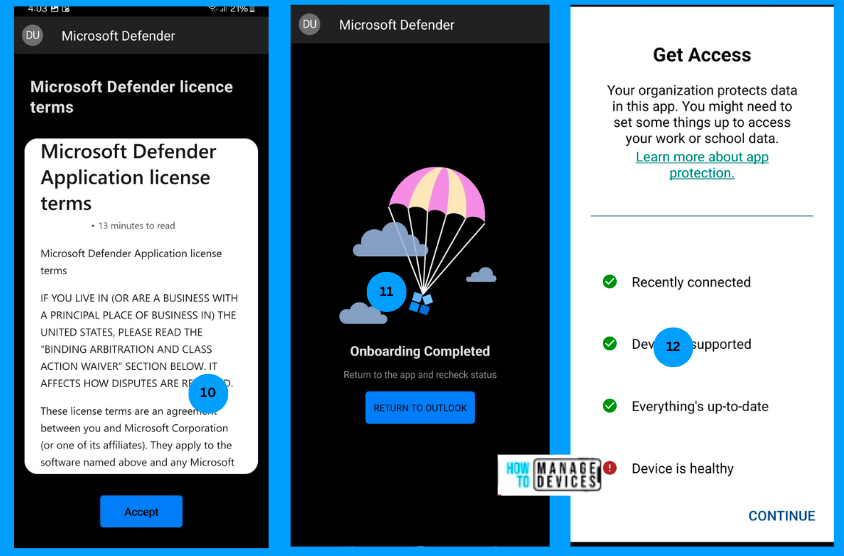
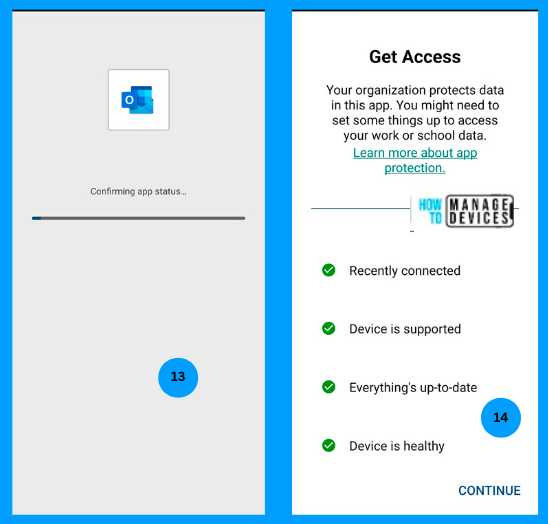
Now click on Continue to validate the Device Health. Once Defender provides the device health, the user will be allowed to access the Outlook app. Outlook validates the Defender application installation, and the Defender app provides information on device health. You can observe now that all the requirements are fulfilled.
Now let’s see how this device will be shown in Microsoft’s Security portal, i.e., Microsoft Defender for Endpoint portal. Login to the MDE portal, click on devices and click on All Devices. You can observe the list of devices onboarded to Microsoft Defender for Endpoint.
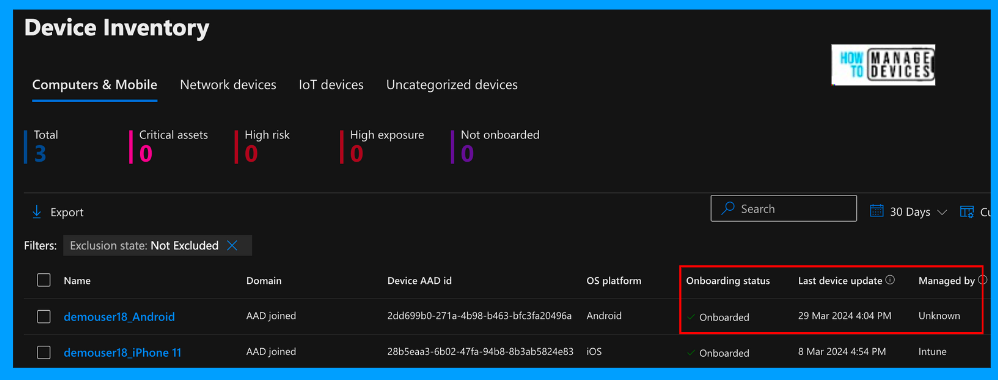
All the devices are shown as Onboarded. If you observe closely, we can differentiate the devices enrolled in Intune and Onboard to Defender for Endpoint from those not enrolled in Intune by the Manage by section. Devices not enrolled in Intune are shown as unknown under the Managed by section.
NOTE: We can configure the Network protection and anti-phishing policies for the Defender using Managed App Configuration policies and protect the network traffic on unmanaged apps as well.
Conclusion
So, Microsoft provides various ways to onboard mobile devices to Microsoft Defender for Endpoint. It is always advised to use unmanaged apps with an app configuration profile to protect networks and avoid corporate data leakage that is bound to happen due to malware or phishing. That’s it from me for this article. We will meet again with another exciting topic.
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
About Author – Narendra Kumar Malepati (Naren) has 11+ years of experience in IT, working on different MDM tools. Over the last seven years, Naren has been working on various features of Intune, including migration from different MDMs to Intune. Naren mainly focuses on Android, iOS, and MacOS.
