Hello, everyone. Let’s learn how to Remediate Vulnerabilities identified by Microsoft Defender for Endpoint using Intune. Threat and Vulnerability Management in Microsoft Defender for Endpoint identifies vulnerabilities and provides remediations as well.
Integrating Intune with Microsoft Intune allows us to take advantage of threat and vulnerability management via Intune Security tasks. This will bring a risk-based approach to remediating and prioritizing vulnerable devices and help organizations improve the remediation response time.
The core feature of vulnerability management is reducing cyber risk by identifying, assessing, remediating, and tracking all vulnerabilities in a single solution. Defender Threat Vulnerability is part of Microsoft Defender for Endpoint. It delivers asset visibility, intelligent threat assessment, and built-in remediation tools for various platforms like Windows, Android, iOS, and network devices.
Our previous article taught us how to onboard Android and iOS devices to Microsoft Defender for Endopint. We will use the Security Tasks tab under Endpoint Security to review and remediate the threats and vulnerabilities identified and sent by Microsoft Defender.
Integrate Microsoft Intune with Microsoft Defender for Endpoint
In order to remediate vulnerabilities using Intune, we must enable a service-to-service connection between Intune and Microsoft Defender for Endpoint. Once we enable it, Defender will collect the device details of those enrolled or managed by Intune and assess their risk level. Based on the risk level, we can either allow or block corporate data access using compliance and conditional access policies.
Now, let’s see below how to enable a service-to-service connection.
- Sign in to the Microsoft Defender portal
- Click on Settings > Endpoints
- Under the General tab, click on Advance
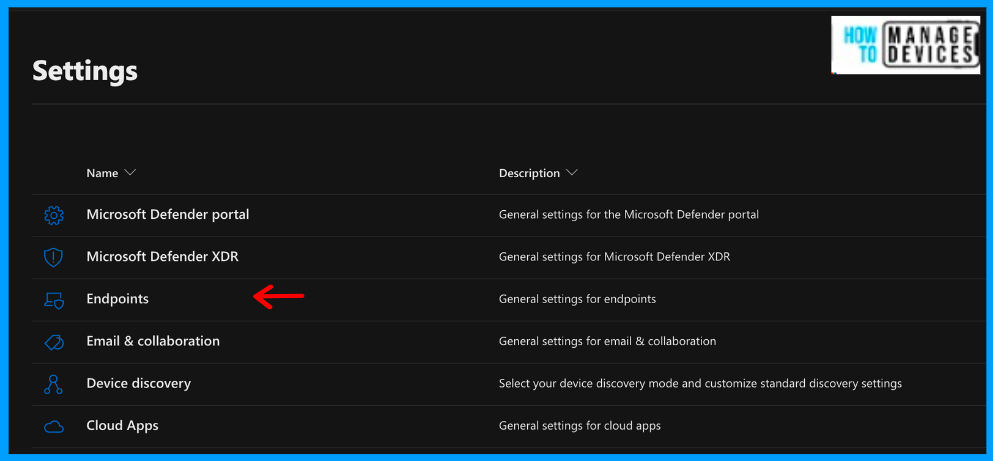
Now look for the Microsoft Intune connection and turn it On. Now click on Save Preferences. This will initiate the sync between Intune and Microsoft Defender for Endpoint. It’s that simple. Once the sync is enabled, the services are expected to sync with each other at least once every 24 hours.
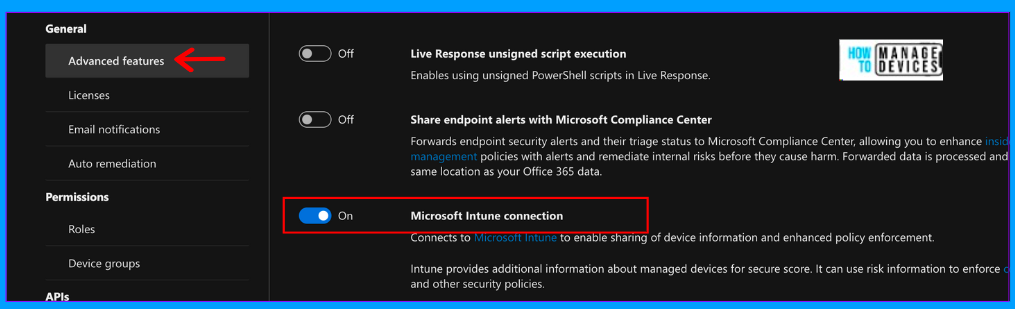
Now log in to Microsoft Intune Admin Center. Click on Endpoint Security > Microsoft Defender for Endpoint. If you want to use compliance policies along with Microsoft Defender, enable Compliance Policy Evaluation for different platforms.
- Set Connect Android devices to Microsoft Defender for Endpoint to On
- Set Connect iOS/iPadOS devices to Microsoft Defender for Endpoint to On
- Set Connect Windows devices to Microsoft Defender for Endpoint to On
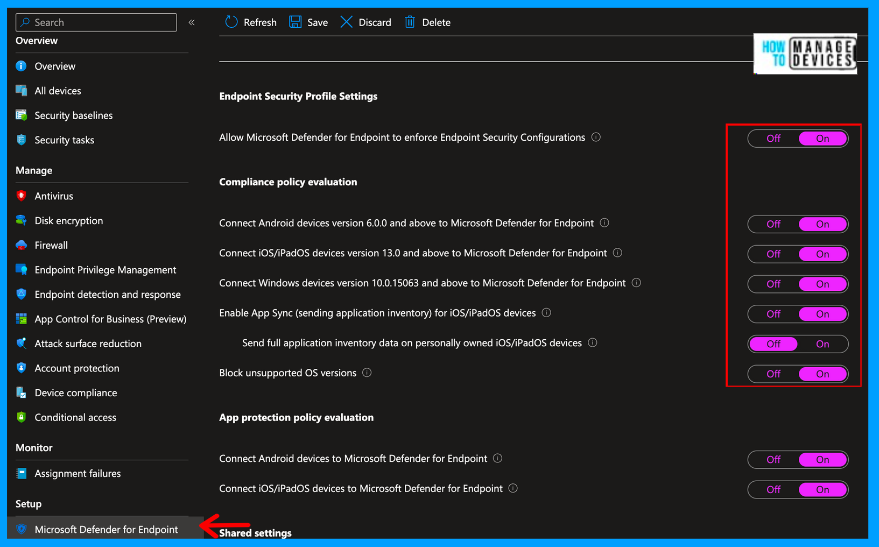
Once enabled, save the settings. Now, the Connection status will show as Enabled, and Intune will start reporting the last sync time and date under the Last synchronized section. In the next section, let’s see how Defender provides vulnerability remediations as security tasks in Intune.
Remediate Vulnerabilities identified by Microsoft Defender
After integrating both services, Intune-managed devices send threat and vulnerability details to Defender for Endpoint, which are visible to security admins in the Microsoft Defender Security Center console. In the console, the admin can review the vulnerability and act upon it by taking actions that will create security tasks in Intune.
Once the connection is established, we need to onboard devices to Microsoft Defender, which will enable Defender to collect data about device risk levels. Microsoft Defender’s intelligent threat vulnerability engine continuously monitors the devices for vulnerabilities. Once identified, vulnerabilities are captured under the Vulnerability section in the Microsoft Defender Security Center console.
Now, let’s see how we can review and provide an action to trigger security tasks in Microsoft Intune using the steps below. For our testing, I have onboarded two devices, Android and iOS. The two devices have software updates available for installation. As you know, an OS update might involve new features and a few bug fixes. MDE identifies and finds vulnerabilities and captures them.
- Sign in to the Microsoft Defender portal
- Click on Vulnerability Management
- Click on Recommendations
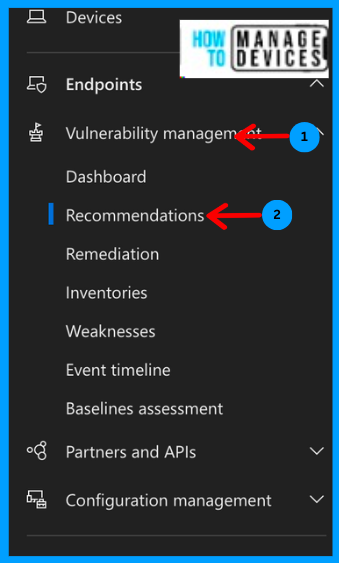
Under recommendations, we can view all the vulnerabilities identified. As I mentioned above, we have two recommendations to update the OS version of iOS and Android devices. Let’s see why Microsoft Defender treats them as vulnerabilities.
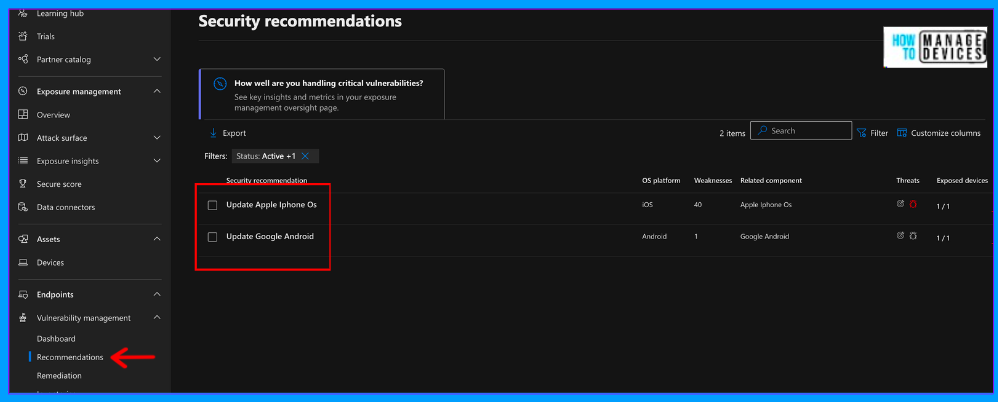
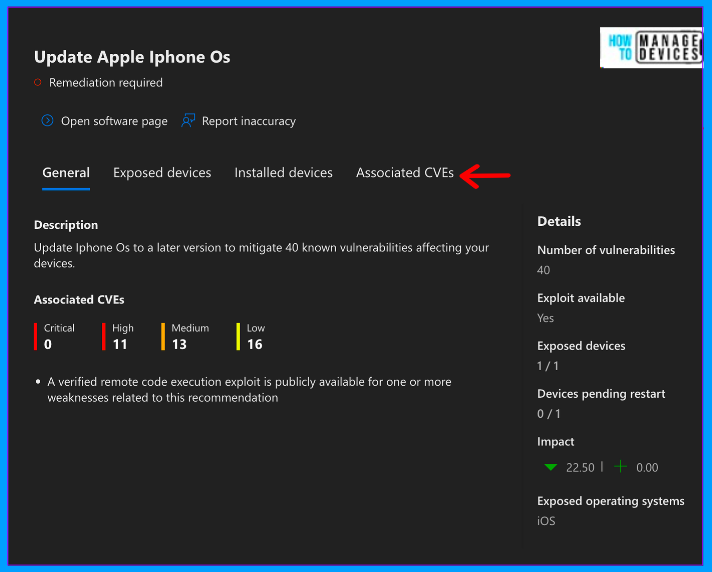
Click on any of the recommendations. For our understanding, I have selected the iOS update. You can view the recommendations and associated CVEs(Common Vulnerabilities and Exposures). You can also view how many CVEs are critical, high, medium, or low impact. We can view the devices associated under the Exposed Device tab.
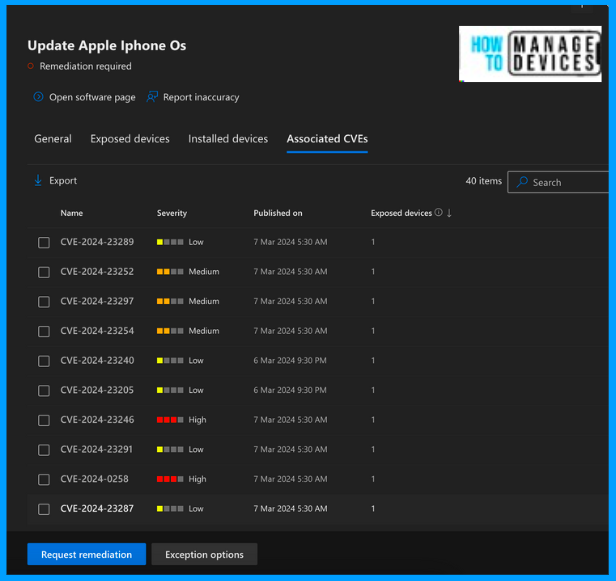
Now, click the Associated CVEs tab to view each CVE and its associated CVE number. You can select any CVE and view its details and the devices that will be impacted. I have chosen one of the CVEs, and you can view the vulnerability details in the below screenshot.
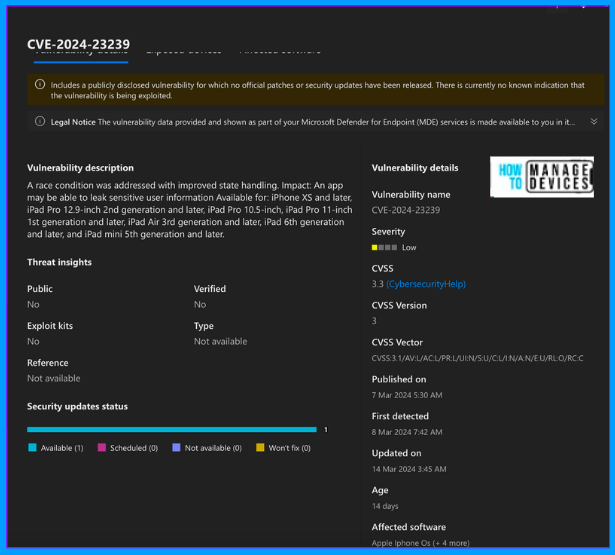
After selecting any CVE, we can view the Vulnerability description under the CVE description page. What kind of devices are affected by this CVE, and what is the severity of the CVE? It also provides the list of devices exposed to this CVE and Affected software.
To create a remediation for this vulnerability, click on Request remediation at the bottom of the vulnerability. This opens a Remediation Request page where we have options to provide remediations and a due date to complete the Remediation. We can also select the priority for the Remediation. To make this Remediation a security task in Intune, check the box “Open a ticket in Intune”.
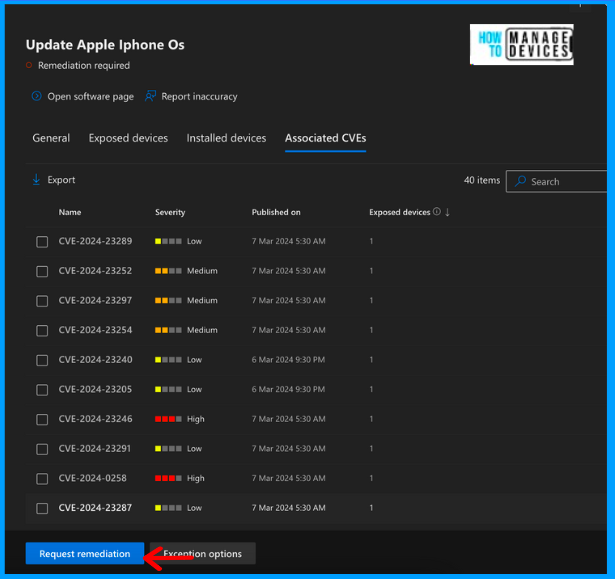
The Microsoft Defender Vulnerability provides multiple options based on the vulnerability on the Remediation request page. In our example, MDE provides Remediation to a Software update (recommended), Software uninstall, or Attention required. If the vulnerability is related to any application, these options will differ.
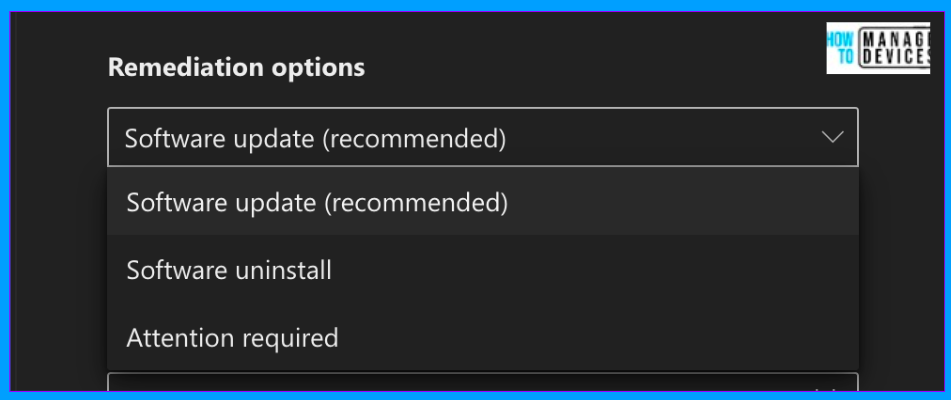
Once we define the Remediation, due date, and priority, click Next to proceed to the Review and Finish page. Review all the remediations and click on Submit. Once we create the Remediation, it will immediately generate a security task.
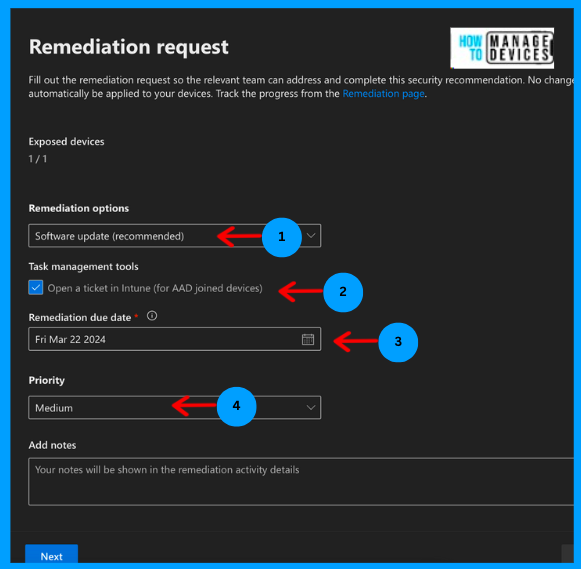
We can view all the Remediation we created just now under the remediation tab in the Vulnerability section of Microsoft Security Console. From here, we can track the status of our Remediation, such as whether it was accepted, rejected, or completed.
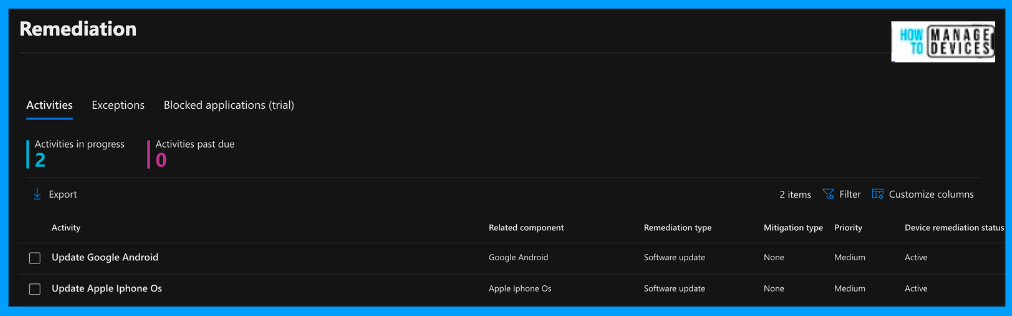
We have now created the Remediation for the Apple OS update Vulnerability identified by Microsoft Defender. In the next section, let’s see how we can provide remediation for this Vulnerability using Microsoft Intune.
Security Tasks in Intune
When Remediation is created in the Security console, a task is created under security tasks in Intune. In the steps below, let’s see how to remediate the vulnerabilities using Intune. We can either create configuration policies or app protection policies to resolve the vulnerability.
- log in to Microsoft Intune Admin Center
- Click on Endpoint Security
- Click on Security Tasks
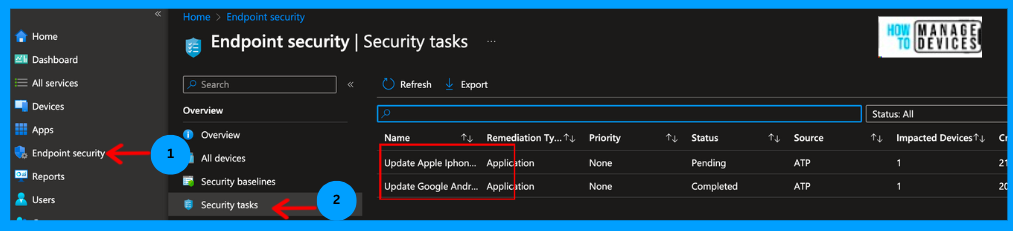
We can view all the remediation recommendations we created in the Microsoft Security Console. As discussed above, we have two remediation recommendations for updating the software update for Android and iOS devices. You can view all the details, such as priority, due date, status, remediation name, and source from where it was generated.
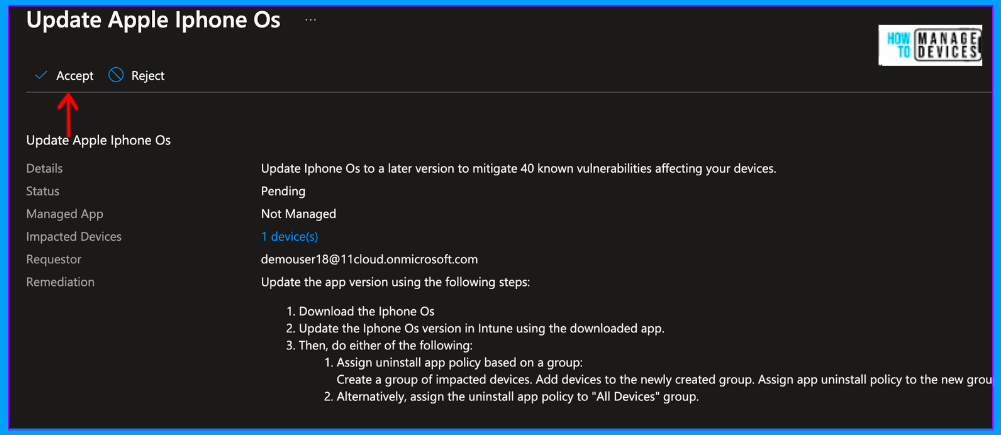
Click on the Remediation. We can also see the steps to remediate in Intune in the Remediation. Intune admin has the option to either accept or reject it. For our discussion, let’s accept the Remediation. Once accepted, we must create configuration profiles or app protection policies to control the vulnerability. The Common remediation actions include:
- Block an application from being run.
- Deploy an operating system update to mitigate the vulnerability.
- Deploy endpoint security policy to mitigate the vulnerability.
- Modify a registry value.
- Disable or Enable a configuration to affect the vulnerability.
- Require Attention alerts the admin to the threat when there’s no suitable recommendation to provide.
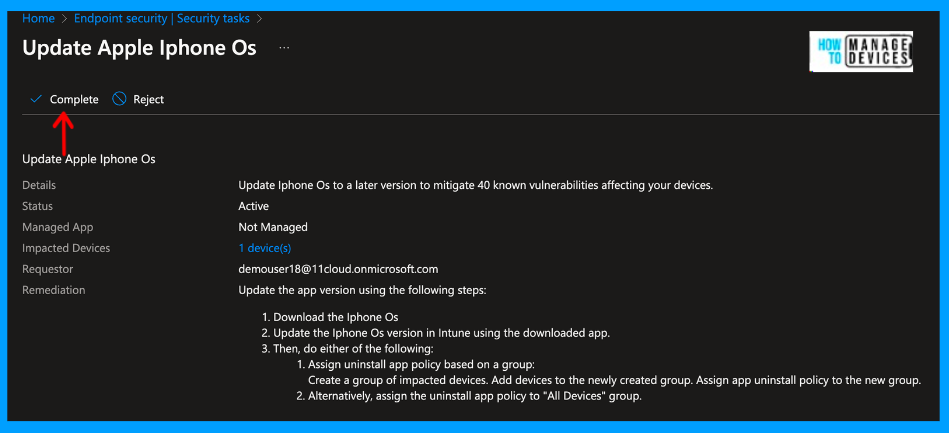
After creating the policies to fix the vulnerability, click on Remediation. Now, you can mark the Remediation as completed or Reject it. Let’s mark this Remediation as complete. As admins, we need to create the required policies to remediate the vulnerability found.
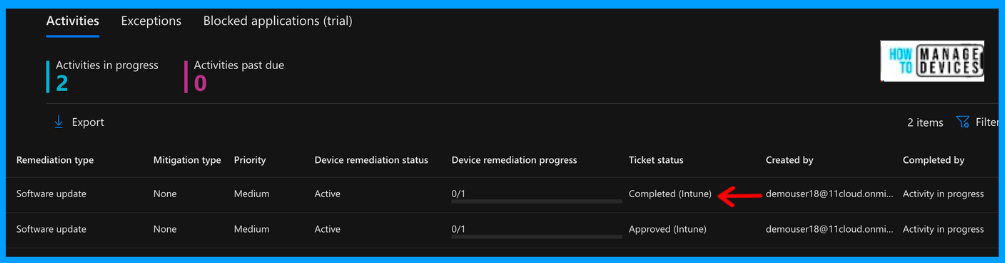
The status of remediations created in Microsoft Security Console also updates as completed. Upon successful Remediation, the risk exposure score in Defender for Endpoint will definitely decrease based on updated information from the remediated devices.
Conclusion
So, we can use both Microsoft Defender for Endpoint and Intune to remediate the vulnerabilities detected by Defender on devices. In this article, we have given a small example of updating the Software. In reality, this might differ. You can remediate as per your requirement. Let’s meet in another article. Till then, have a happy learning.
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here – HTMD WhatsApp.
Author
About Author – Narendra Kumar Malepati (Naren) has 11+ years of experience in IT, working on different MDM tools. Over the last seven years, Naren has been working on various features of Intune, including migration from different MDMs to Intune. Naren mainly focuses on Android, iOS, and MacOS.

Hello Naren,
really good and detailed description and instructions.
I’m stuck on one thing and maybe you know the solution to it quickly:
After I have activated the remediation and the checkbox for intune ticket creation, I receive the error message in the ticket status column after a short time: Failed to create (Intune)
no task is created in intune in the security tasks either.
Do you have a clue as to why this could be?
Best regards from Germany
Marco
I am seeing this issue also did you get a fix for it?