In today’s article, let’s learn how to Managing Apps on the Personal profile of COPE Devices Using Intune: Allow Lists and Block Lists, which are enrolled as Corporate Owned Personal Enabled devices. Intune helps admins manage what apps can be installed on a personal profile as well.
As Google provides various ways of managing Android devices, Corporate Owned Personal Enabled devices are one of the compelling models for modern workplaces. This enrollment method satisfies both organisations and their employees as it provides more device management control for organisations and allows users to use their personal usage on corporate devices.
This model inherently relies on the tight separation of profiles, typically through work profiles or containers, to keep corporate data secure and personal data private. Managing a work profile is never a challenge, now the question is, should we manage a personal profile?
Managing Work Profile is rightful as the corporate data lies in it. Venturing into a Personal profile and managing it should be a delicate way of protecting the data, and has to be managed in a balanced way to safeguard the data residing on the personal side as well.
Table of Contents
Managing Apps on Personal Profile of COPE Devices using Intune?
The Corporate Owned Personal Enabled model of enrollment is designed with a specific balance in mind. It provides privacy for both organisations and users’ personal usage, managing apps on the personal side of the device might look like invading the users’ privacy.
Managing which applications can or cannot be used on these COPE devices is critical to maintaining security, compliance, and productivity. Organisations should ensure corporate data is protected while not intruding into the personal space.
Android device management framework doesn’t provide granular control over personal profile as it violates the users’ privacy, at the same time, provides few controls to control the app installation and some security features without violating privacy and government laws in some countries. Intune helps IT admins to either block a few apps or allow a few apps to be installed on the personal side of the devices.
- Enforce Users to use Intune Approved Apps with App Protection Policies using Conditional Access Policies.
- Configure Android Shared Devices using Intune
Allow List or Block List using Intune
Users may install unapproved apps or transfer sensitive data to personal apps (e.g., copying work emails to personal notes). As the IT admins have no access to the personal app inventory or user behaviour within personal apps. This creates blind spots in threat detection and limits the effectiveness of compliance enforcement.
This challenge makes organisations control apps that can be installed or at least block apps that are malicious to protect corporate data. Let’s see below how we can achieve this challenge using Intune device restrictions.
- Log in to the Microsoft Intune Admin Centre
- Click Devices > Configuration > Create > New Policy
- Select Platform as Android Enterprise
- Select Profile Type as Device Restrictions
- Click on Create
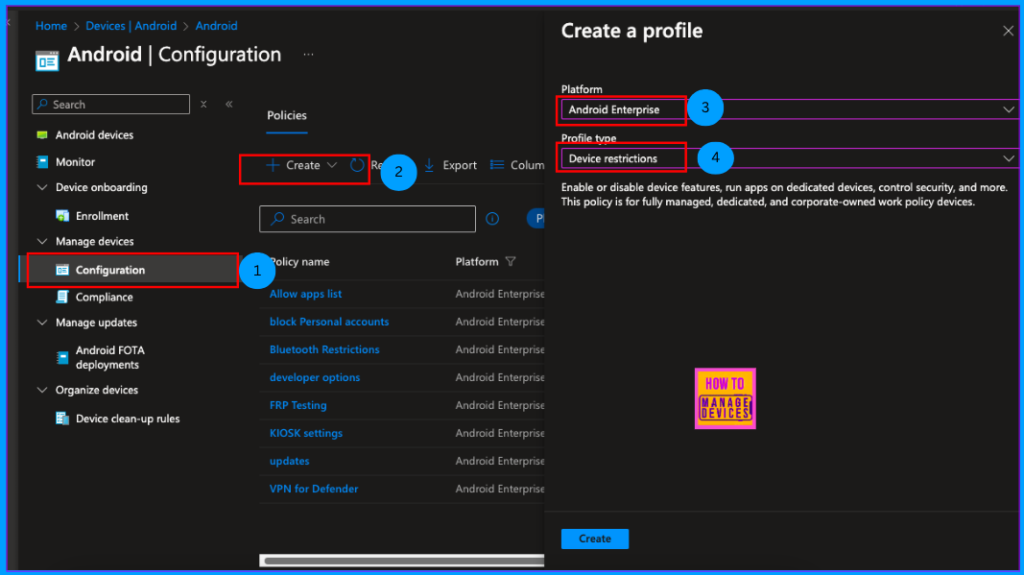
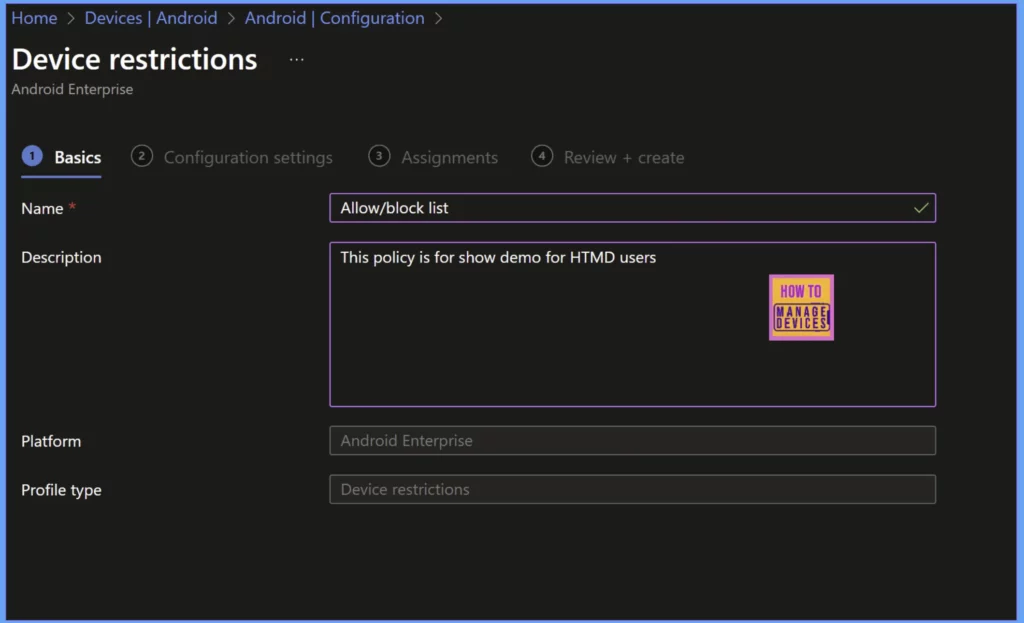
Provide a meaningful Name for the policy that reflects its purpose by reading. Use the Description field to include context such as the reason for the policy, related change number, or scope to help track its intent and change history.
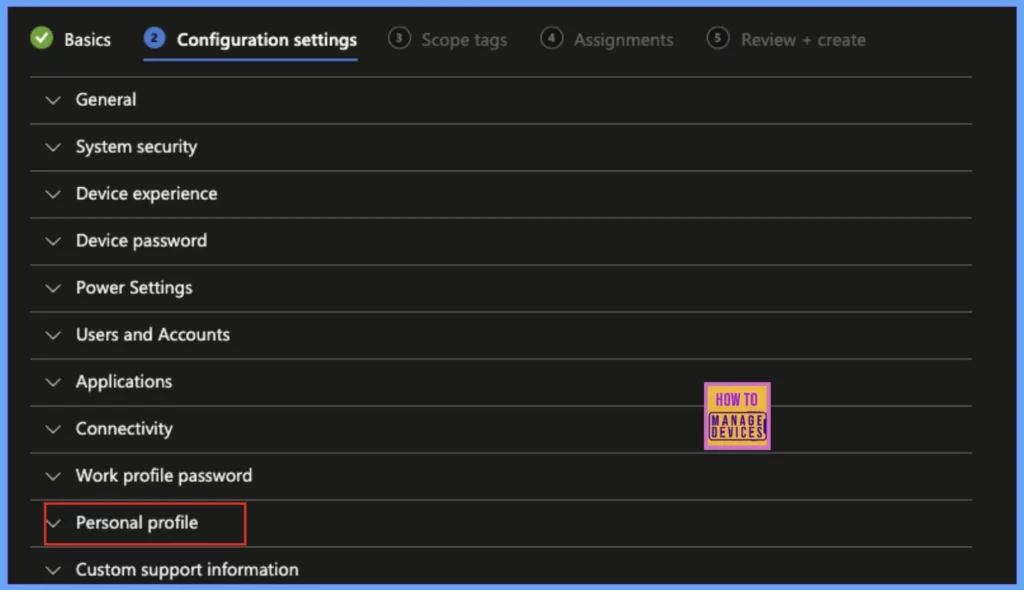
Microsoft Intune categorised all the restrictions into various categories. All the General restrictions like Developer Settings, Software Updates are in General category, Password related settings are under Password cateogry.
Our required restrictions are under the Personal Profile category. Click on Personal Profile, now you will find “Type of restricted apps list“, by default the value is Not Configured. Now we can either Allow list of apps or Block list of Apps.
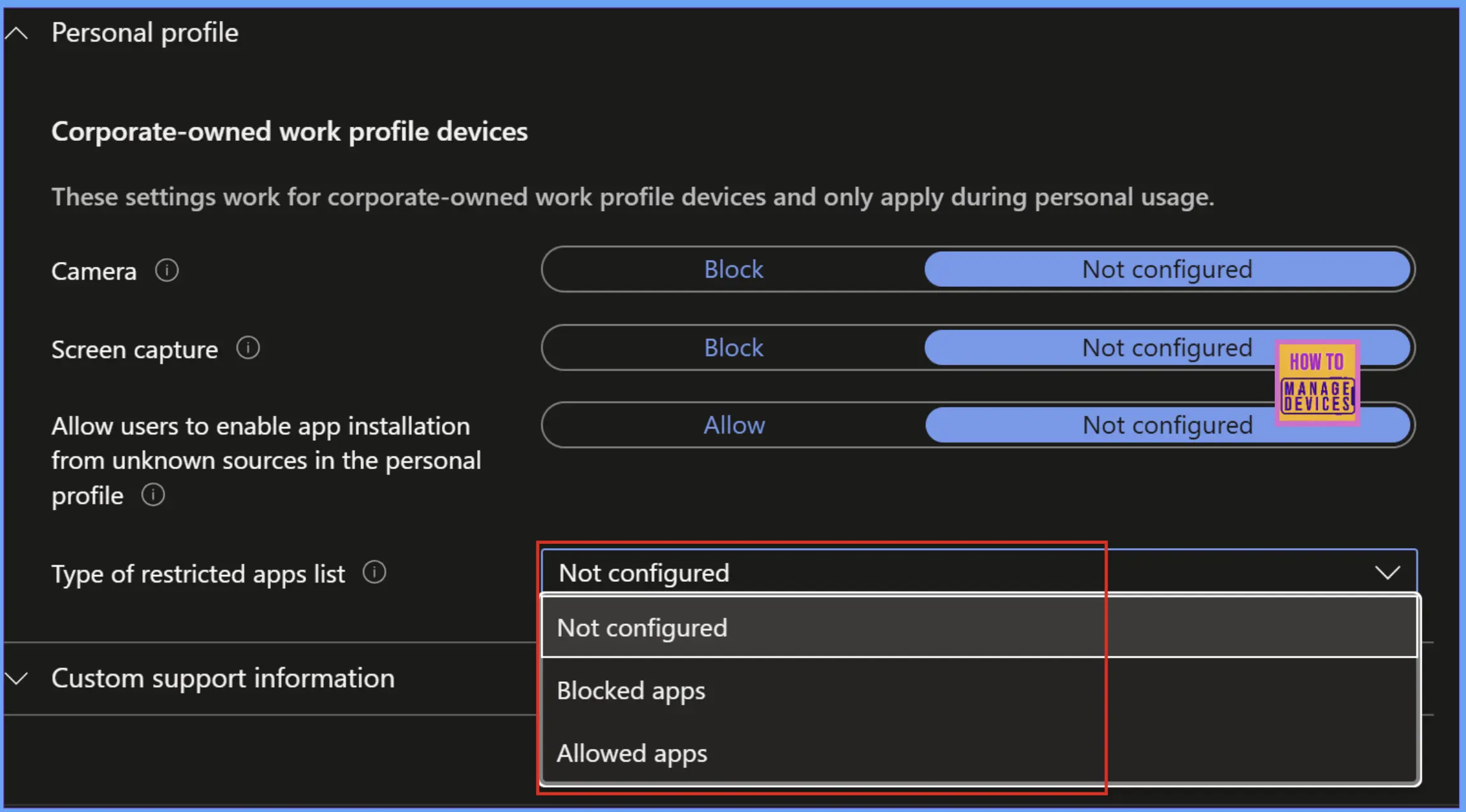
Before adding the apps to either the Block List or Allow List, these apps have to be added or deployed in Intune. You can use Managed Google Play Store apps as well to add them to Intune. Let’s see in the table below what happens when we select a particular setting.
| Settings | Function |
|---|---|
| Allow apps List | The user will be able to install the apps that are allowed from their personal Palystore. They cannot install any other apps, or they cannot view any other public apps. |
| Block apps List | The user can install any apps from the Play Store except for the apps that are blocked. |
Now select the Allow apps or Block apps as per requirement. Now, click on Add to add the apps to the Allow list or the Block list. Search for the apps you want and add them to the block list. For our discussion, I have selected the Block list apps
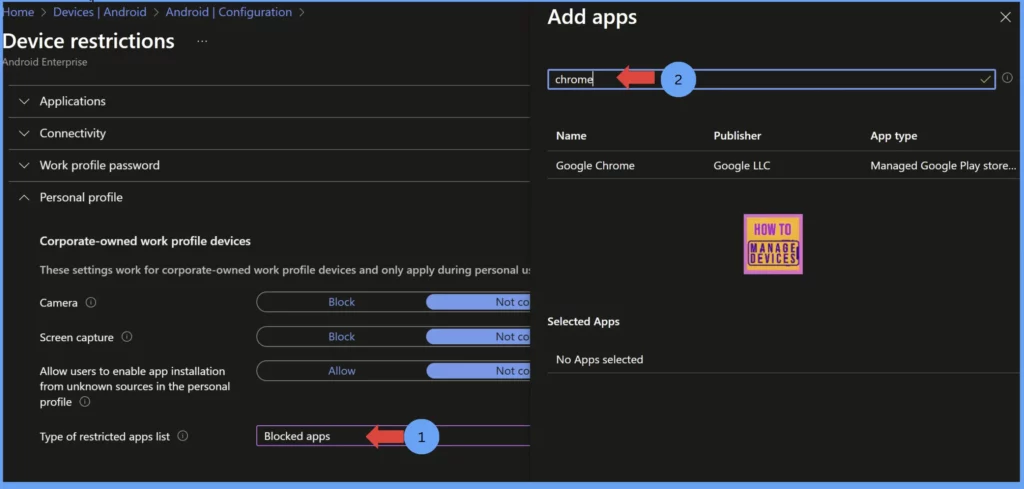
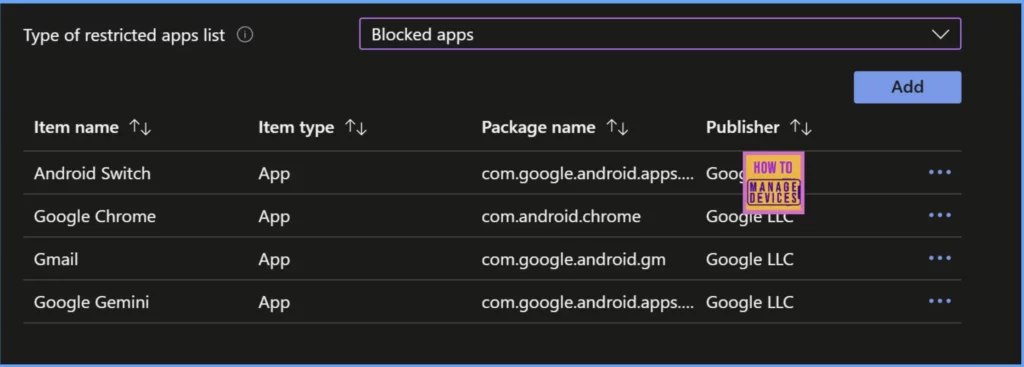
After selecting the required apps, click on Done. You can view all the apps that you added as part of the Block list. Validate them. You can add again if you need to add more. Select the apps you need and click Next to the Scope tags page. Add Scope tags if you have any, else click on Next
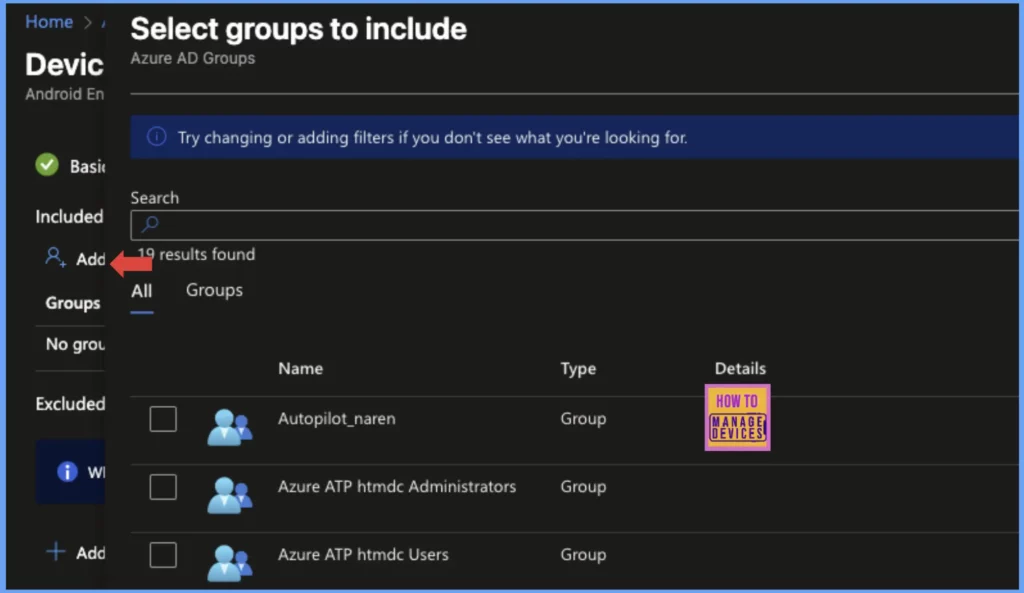
In the Assignment page, click on Add groups and select the user group to which the configuration is to be assigned. You can add exclusions as well if you wish to not apply these settings for a set of users. Add the user group under Excluded groups below.
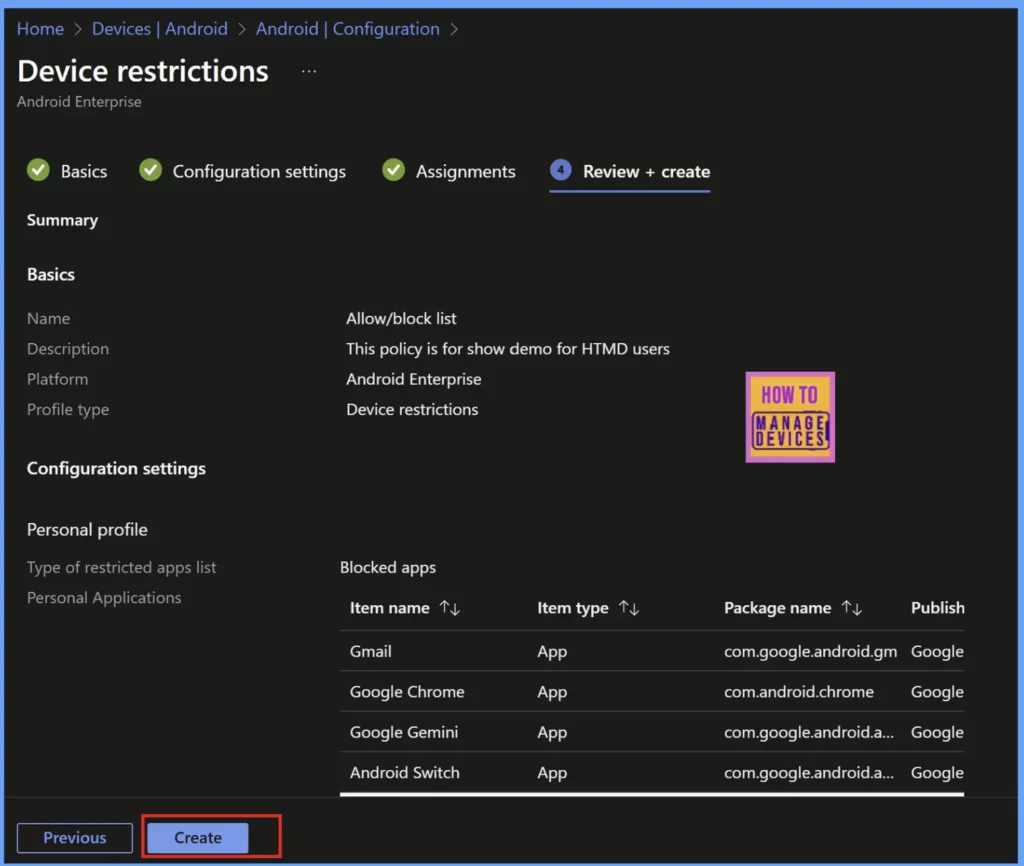
Once you have successfully added the required user group to your configuration, proceed by clicking the “Next” button. This action will take you to the Review + Create page, where you can meticulously assess the settings you’ve implemented. After confirming that everything aligns with your requirements, click the “Create” button to finalise and deploy the policy to the users.
It will take a while to create the policy. Once the policy is created, based on the configuration on personal play store users may see only allowed apps in case of the allowed app list, or the user can view all apps except for the blocked apps.
User Experience
Now let’s see the User Experience, or how the configuration actually looks in realtime. I have enrolled one of the devices in COPE model. I have assigned a few Allow list first for our discussion. As soon as the policy applied, I can view only the allow apps in the Play Store as shown in the screenshot below.

Now, I have made changes and added the same apps to the Blocked apps list. After the configuration is applied, I can now view all the apps. But I’m unable to view the apps that I added to the blocked apps list. Even if I search for the apps I blocked, I don’t get the results of those applications.
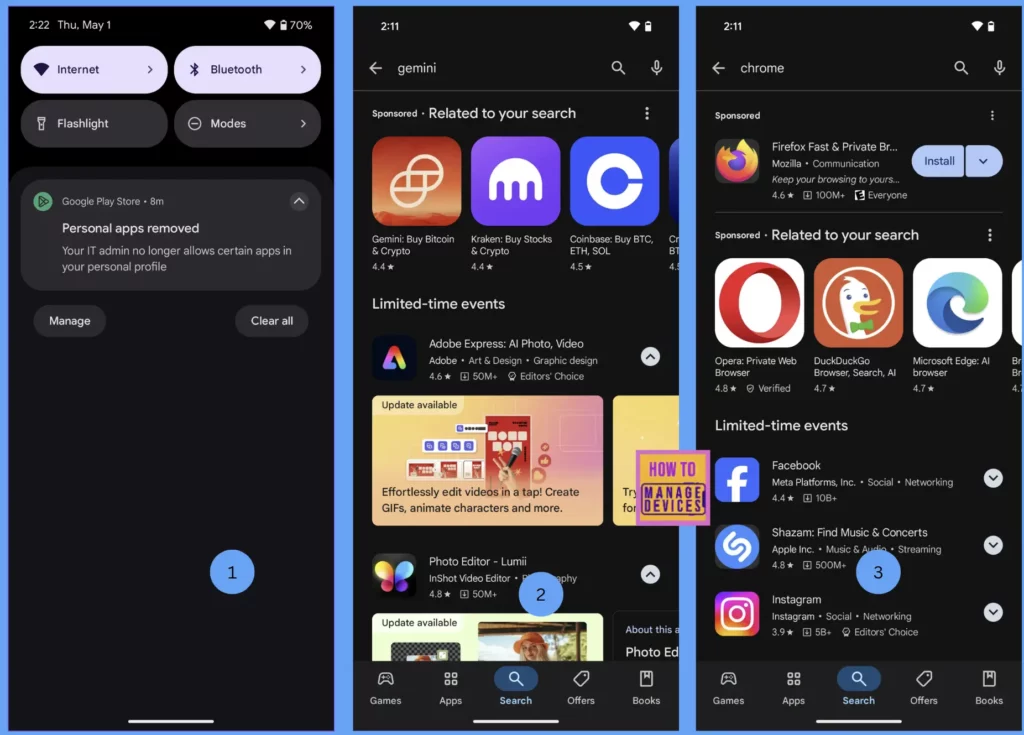
When we add apps in the block list, Intune not only helps to block them, but also uninstalls the blocked apps if they’re already installed on the device as shown in the screenshot 1. We can uninstall even the System apps as well. So, Block apps list would be a better way of controlling the apps on the personal side of the COPE devices.
Conclusion
While Intune provides a better solution for controlling the apps in the Personal Profile of COPE devices, it has its limitations due to user Privacy. Before applying these configurations, make sure you are following the respective country’s Privacy rules and Guidelines.
These use cases can be viewed mainly in Banking and Finance, HealthCare, Government sectors, Legal and Law firms. In short, we can say the allow list and block list app management capabilities of Microsoft Intune are highly used in industries where data security, privacy, compliance, and productivity.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
About Author – Narendra Kumar Malepati (Naren) has 13+ years of experience in IT, working on different MDM tools. Over the last seven years, Naren has been working on various features of Intune, including migration from different MDMs to Intune. Naren mainly focuses on Android, iOS, and MacOS.
