Hello, Everyone. We are back with another exciting topic: how to force users to Use Approved Apps with App Protection Policies using Conditional Access Policies. In this article, we will discuss how to create a Conditional Access Policy that forces users to use Approved apps and has App Protection policies applied to them.
Entra Conditional access policies are rules that users should satisfy if they want to access resources. They are just like IF-THEN statements. Conditional Access policies are enforced after the first authentication factor (after validating the user credential).
Organizations allow users to access corporate data on their mobile devices. Users can access it from different apps, which may cause data leakage. To prevent this, Organizations can mandate users to use Approved client apps to access cloud apps that are aware of Modern Authentication.
These cloud apps know Intune App Protection Policies and work independently of OS platforms. To enforce this control, the user’s device must be registered to Entra ID. This requires a broker app like Microsoft Authenticator for iOS devices and the Company portal or Microsoft Authenticator for Android devices.
- Intune Onboard Android Devices to Microsoft Defender for Endpoint
- Revoke and Delete Cloud PKI Certification Authorities in Intune
Table of Contents
List of Approved Client Apps
Microsoft has 30+ apps for accessing various cloud apps, such as Emails and SharePoint. Some applications are Microsoft Outlook, Microsoft Excel, Microsoft Azure Information Protection, and Microsoft Dynamics 365. This list is growing.
Create a Conditional Access Policy to Use Approved Apps
Now, let’s see how to create a Conditional Access policy. An administrator can use access controls to grant or block resource access based on certain conditions within a Conditional Access policy. These conditions can be user-based, device OS-based, location-based, etc.
- Login to the Entra ID portal
- Click on Protection > Conditional Access Policy
- Now click on Create New Policy
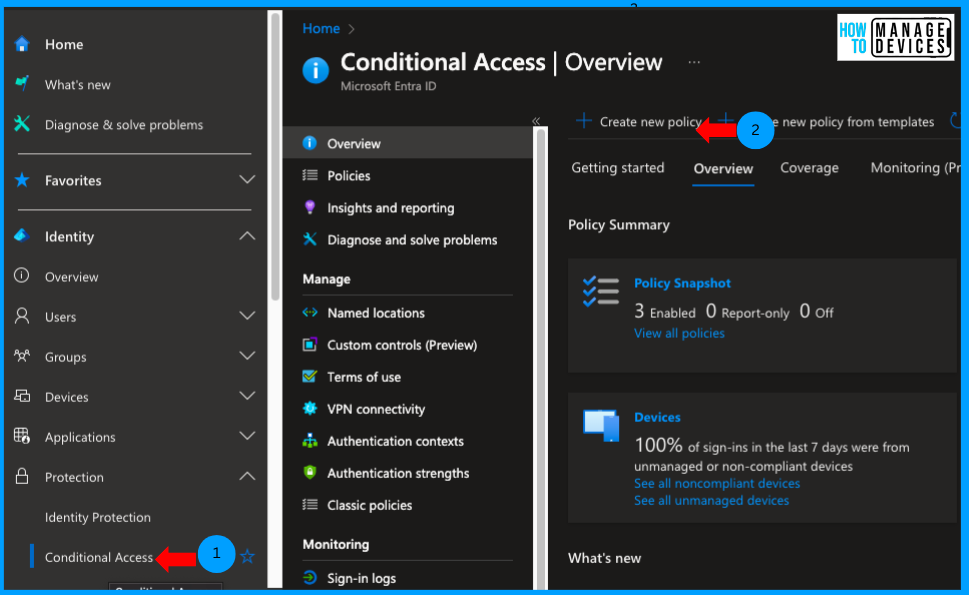
Now provide the name for the conditional access policy and click on Users and Groups to add the user groups or individual users you want to enforce for users to use approved apps only. We can add individual users or groups as per your requirements. For our discussion, I have added a single user.
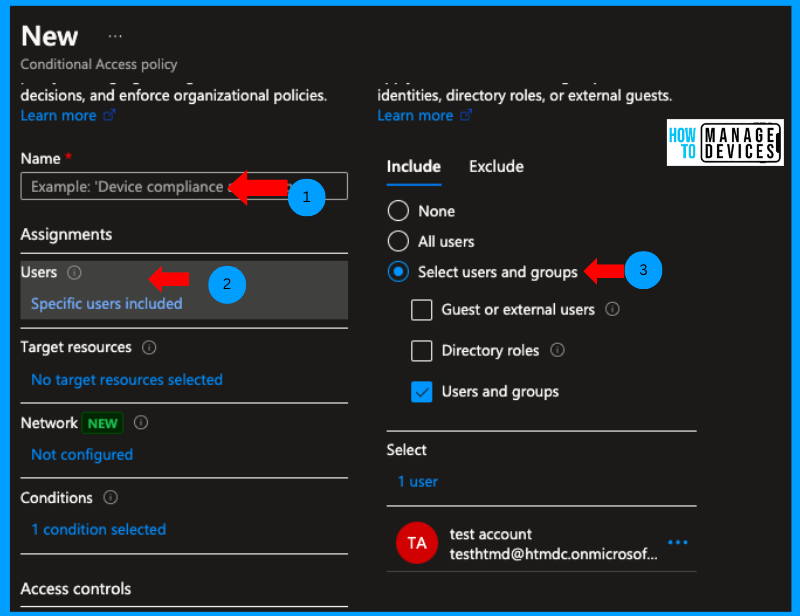
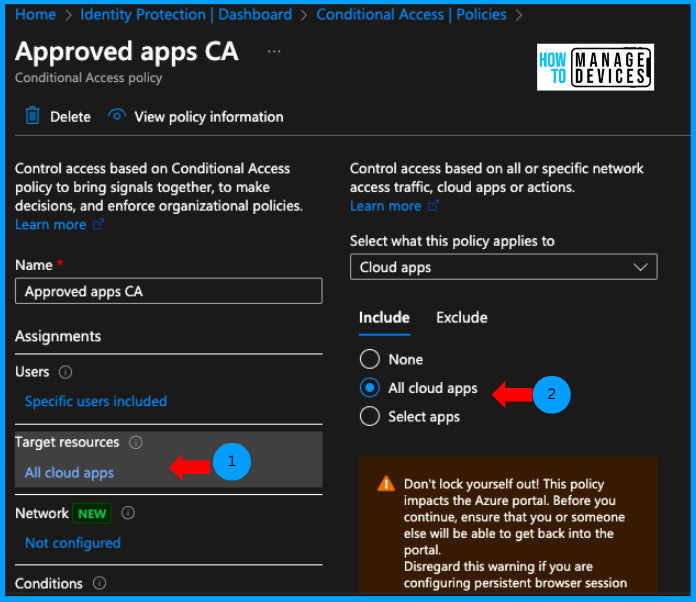
Now click on Target Resources. Here we need to select the target apps to which we need to apply the CA policy. For our discussion, I’m selecting the All Cloud Apps, which will include any Enterprise apps that are registered in Azure
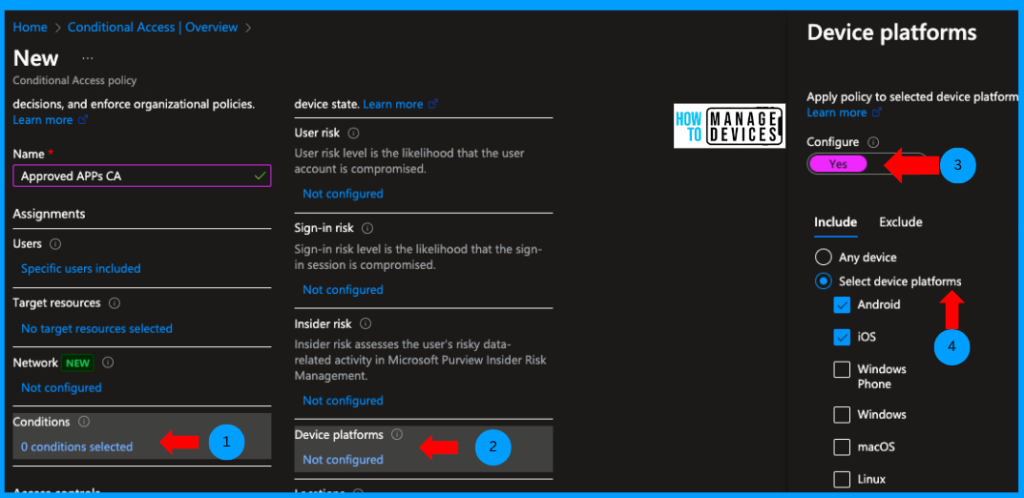
As we target this policy to Android and iOS, click on the Conditions tab and select Device Platform. Now click on Configure > Yes. Under the include section, click Select device platforms, select Android and iOS, and click Done.
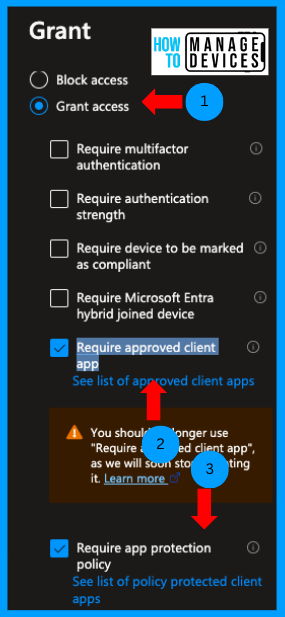
Now click on Grant Control. This section will configure whether to block or allow resource access based on the conditions configured. As we need to provide access to the application, I have selected Grant Access, and the condition Requires an approved client app and Require app protection policy. We can also view the list of Approved apps and apps that support APP policies.
Click on Select, then on Enable policy, and click on On to create the Conditional Access Policy and apply it to the selected users or user groups. We can also create a CA policy and make it Read-Only to validate the Policy before assigning it to the users in Production.
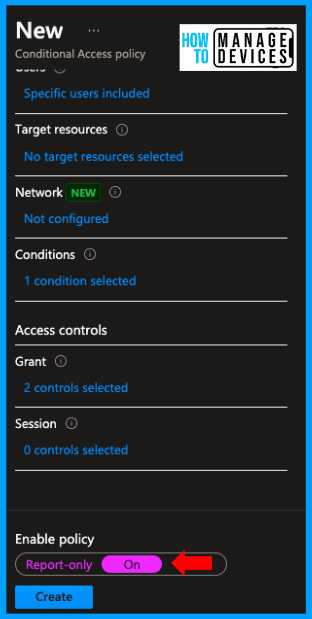
Thus, we have created a Conditional Access policy that will force users to use only Approved apps and Apps with App Protection Policies. In the next section, let’s look at the user experience and how users are forced to use approved apps only while accessing corporate.
NOTE: Microsoft is retiring the approved client app grant in early March 2026. If you plan to implement grant control using Approved apps, you are advised to use only Grant Control with Required app Protection Policies.
User Experience
Now that I have created the Conditional Access policy, it’s time to test it. I do not have an App Protection policy assigned to the test user. When I try to configure even the Approved apps(like Outlook), the user will be unable to log in to the app and will be shown an error message below for iOS and Android, as I don’t have an App Protection Policy assigned.
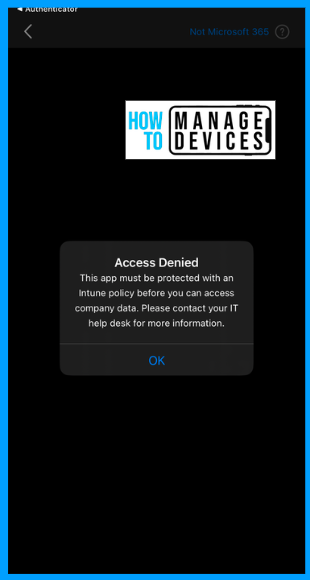
As shown in the screenshot, users will blocked and advised to use apps that have App Protection policies assigned or to contact IT, if they are accessing corporate data on any apps other than Approved apps and apps that do not have App Protection Policies
Conclusion
So, while creating the Conditional Access policies, ensure you are excluded from the policy so you are not blocked from accessing the resources. Also, make sure you create a Conditional Access Policy in Report-only Mode to validate the settings. Once you are sure, you can move the policy to ON
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here – HTMD WhatsApp.
Author
About Author – Narendra Kumar Malepati (Naren) has 11+ years of experience in IT, working on different MDM tools. Over the last seven years, Naren has been working on various features of Intune, including migration from different MDMs to Intune. Naren mainly focuses on Android, iOS, and MacOS.

Is it possible to create’ Approved Client Apps’ or is there a list of non-Microsoft Approved Client Apps?