Hi, Let’s discuss PowerShell 7.2 7.3 Vulnerability with CVE 2023 28260. Let’s learn how to fix PowerShell 7.2 7.3 Vulnerability with CVE 2023-28260. Anoop shared this on April 14, 2023, in YouTube short.
Microsoft takes the security of its products and services seriously and has set up the Microsoft Security Response Center (MSRC) to investigate and address any reported security vulnerabilities. Let’s discuss Powershell vulnerability.net DLL hijacking remote code execution vulnerability.
The MSRC provides regular updates and information to help users understand and manage security risks and protect their systems from potential threats. By actively monitoring and responding to security concerns, Microsoft aims to provide its users with a safer and more secure computing environment.
A vulnerability is a weakness or flaw in a system, software, or hardware that attackers can exploit to compromise the system’s security, gain unauthorized access, steal data, or cause damage to the system.
- FIX Zero Day Security Vulnerability for Outlook
- Intune Advanced App and Vulnerability Management for 3rd Party Patch Management from Microsoft
According to the CVSS metric, the privileges required are low (PR:L). What does that mean for this vulnerability?
Any authenticated user could trigger this vulnerability. It does not require admin or other elevated privileges.
According to the CVSS metric, the attack vector is local (AV:L). Why does the CVE title indicate that this is a remote code execution?
The word Remote in the title refers to the location of the attacker. This type of exploit is sometimes called Arbitrary Code Execution (ACE). The attack itself is carried out locally. This means an attacker or victim needs to execute code from the local machine to exploit the vulnerability.
How do you know if your version of Powershell 7 is affected

Run pwsh -v, then check the version in the table in Affected Software to see if your version of PowerShell 7 is affected.
How do you update to an unaffected version?
Follow the instructions for Installing PowerShell 7 to install the latest version of PowerShell 7.
What if the update breaks my script or module?
You can uninstall the newer version of PowerShell 7 and install the previous version of PowerShell 7. This should be treated as a temporary measure. Therefore, the script or module should be updated to work with the patched version of PowerShell 7.
FIX PowerShell 7.2 7.3 Vulnerability CVE 2023-28260
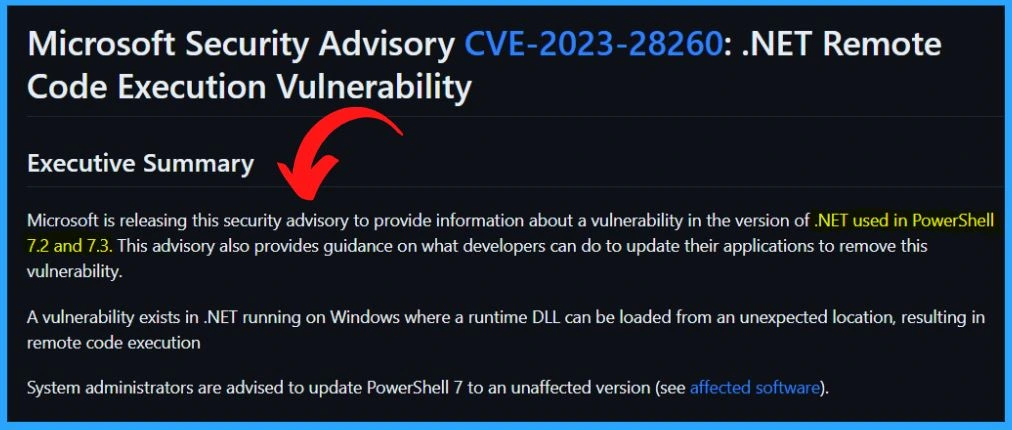
The Powershell vulnerability.net DLL hijacking remote code execution vulnerability impacts Powershell 7.2 and 7.3 versions. Microsoft released the CVE for this, and Microsoft provided a GitHub article explaining how to update the Powershell when the 7.2 and 7.3 versions are impacted. Microsoft recommends updating the Powershell version, which is affected, to fix the issue.
- A vulnerability exists in .NET running on Windows where a runtime DLL can be loaded from an unexpected location, resulting in remote code execution.
- System administrators are advised to update PowerShell 7 to an unaffected version
| Version | Revision Date | Description |
|---|---|---|
| 1.0 | Apr 11, 2023 | Information published |
| 2.0 | April 11, 2023 | Revised the Security Updates table to include PowerShell 7.2 and PowerShell 7.3 because these versions of PowerShell 7 are affected by this vulnerability. |
How to Update the Powershell 7.2 and 7.3 Versions
Let’s discuss how to update the Powershell 0.2 and 7.3 Versions. Microsoft released the CVE for this Powershell update, and Microsoft released a GitHub article to explain how to update Powershell.
| PowerShell 7 Version | Fixed with PowerShell version |
|---|---|
| 7.2 | 7.2.11 |
| 7.3 | 7.3.3 |
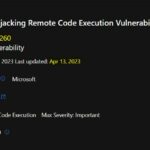
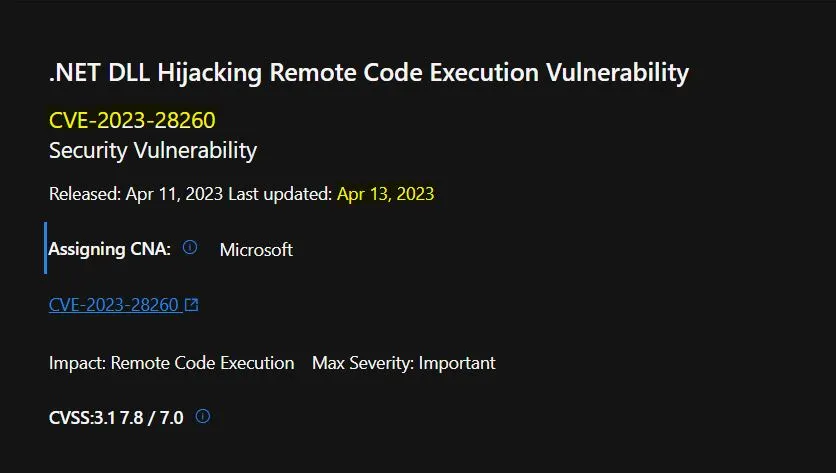
.NET DLL Hijacking Remote Code Execution Vulnerability
Microsoft is releasing this security advisory to provide information about a vulnerability in the version of .NET used in PowerShell 7.2 and 7.3. The advisory contains important information and recommendations for developers to update their applications and remove the vulnerability.
By releasing this advisory, Microsoft aims to help users take necessary measures to ensure the security of their systems and prevent any potential security breaches.
- CVE-2023-28260
- Title: .NET DLL Hijacking Remote Code Execution Vulnerability
- Version: 2.0
- Reason for revision: Revised the Security Updates table to include PowerShell 7.2 and PowerShell 7.3 because these versions of PowerShell 7 are affected by this vulnerability.
- Originally released: April 11, 2023
- Last updated: April 13, 2023
- Aggregate CVE Severity Rating: Important
Details of Vulnerability Exploitation
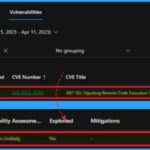
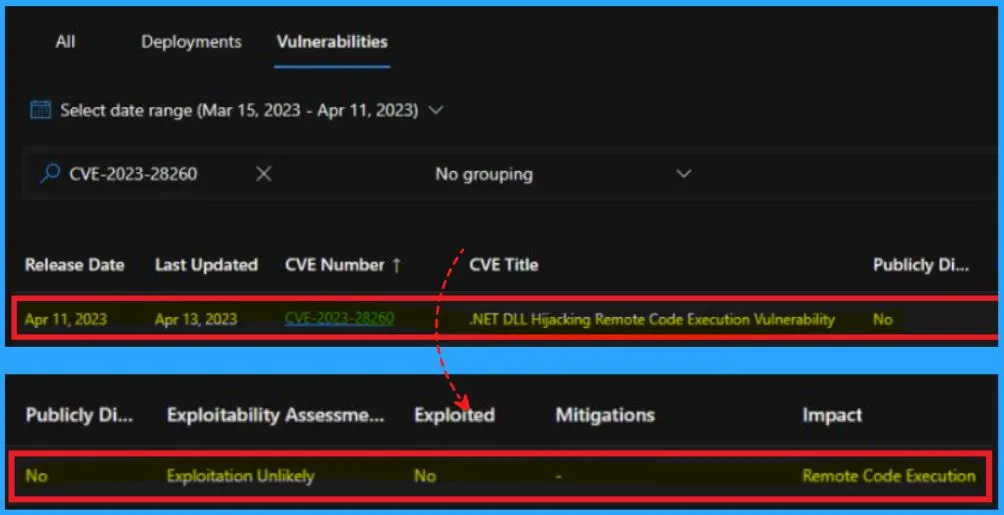
Let’s look at the details of vulnerability “exploitation is not likely,” “exploited is No“, which means it is not exploited yet as per Microsoft documentation and analysis. So you can get the CV details from here.
| Release Date | Last Updated | CVE Number | CVE Title | Publicly Disclosed | Exploitability Assessment | Mitigations | Impact |
|---|---|---|---|---|---|---|---|
| April 11, 2023 | April 11, 2023 | CVE-2023-28260 | .NET DLL Hijacking Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Remote Code Execution |
Resources – https://github.com/PowerShell/Announcements/issues/39
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions to and write about day-to-day tech problems.
