Let’s discuss how to Schedule iOS Automatic Updates Using Intune Policies. Do you have supervised iOS devices managed through Intune?
If so, you may know that iOS software updates will force installation updates on supervised mode iOS devices. Intune has a new policy to prevent/delay these force updates.
This option will also give more granular control over iOS software updates. This post will discuss how to Prevent iOS Automatic Updates Using Intune Policies.
New options have been added to the automatic iOS and iPad OS updates. The following are the exciting options available for this update.
Table of Contents
- Update policy schedule settings
- Update During the scheduled time
- Updates Outside the scheduled time
If you are looking for Windows 10 update ring policies with Intune, I have a blog post titled “How to Setup Windows 10 Software Update Policy Rings in Intune Azure Portal.”
- How to Block OS Updates on iOS Devices using Intune
- New Intune Settings for iOS iPadOS Web Clip App Deployment
- Intune Compliance Report for Device Settings
How to Create iOS Software Update Policies in Intune? iOS Automatic Updates Using Intune
This Intune policy will help delay iOS automatic updates. iOS devices should be part of the Apple DEP program and managed through supervised mode. Create a profile to force assigned devices to automatically install the latest iOS/iPadOS updates.
These settings determine how and when software updates deploy. This profile doesn’t prevent users from updating the OS manually, which can be controlled for up to 90 days with a device configuration restriction policy. Updates will only apply to devices enrolled through Apple’s Automated Device Enrollment (ABM or ASM).
| How to Create iOS Software Update Policies in Intune |
|---|
| Login to the MEM Admin Center portal |
| Navigate via the Devices – iOS/iPad Update Policies (Update policies for iOS/iPadOS) |
| Click on + Create update policy |
| From the Update Policy Settings page for iOS/iPad OS update – The version of iOS/iPadOS to install on devices at the time of update |
You can create a new policy with a proper name and description of the policy. This policy will prevent iOS Automatic Updates from forcefully getting installed on supervised iOS devices.
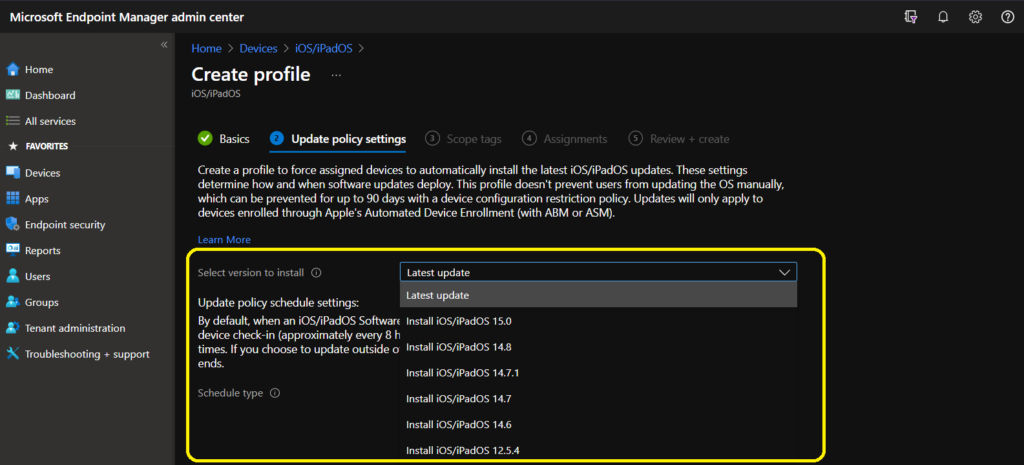
Update Policy Schedule Settings for iOS/iPad OS Devices
Update policy schedule settings: By default, when an iOS/iPadOS Software Updates policy is assigned to a device, Intune deploys the latest updates at device check-in (approximately every 8 hours).
You can instead create a weekly schedule with customized start and end times. If you choose to update outside the scheduled time, Intune won’t deploy updates until the scheduled time ends.
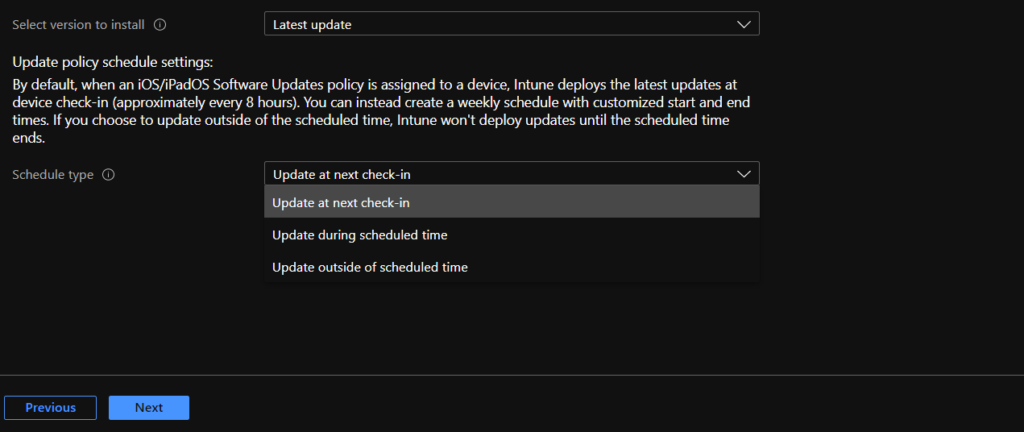
- Select Type and Schedule for iOS update (When the updates will occur. Additional input is required to schedule updates during or outside of scheduled times)
- Update at next check-in
- Update During the scheduled time
- Update Outside of the scheduled time
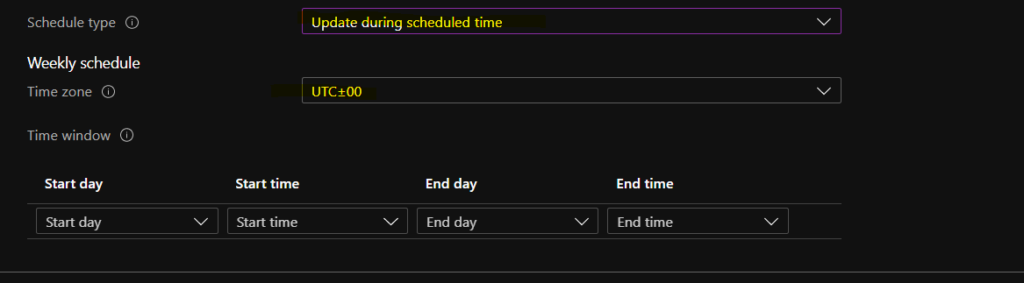
Update During the scheduled time, stop updates from being installed at any random time. By configuring this policy, you can delay the software update (automatic update) of iOS on the device.
Weekly Schedule -> TimeZone, Start Day, Start Time, End Day, End Time
You can select the Time zone, Date, and time for iOS/iPad OS updates. Select the time zone of the targeted devices – In this section, you must select the Time Zone of the devices you want to target for this policy. For the India Time Zone, I selected UTC+5:30.
Start Time—Select the beginning of the interval to stop iOS software updates from Installing on supervised iOS devices. You usually don’t want to install software updates on iOS devices during business hours. This will help you schedule iOS phone updates via Intune policies.
End Time – Select the end of the interval to stop iOS software updates from installing on supervised iOS devices.
Start Day of the update: You can select any day of the week from the start and end day options, from Sunday to Saturday. End the Day of the iOs/iPad OS update by selecting any day between Sunday and Saturday.
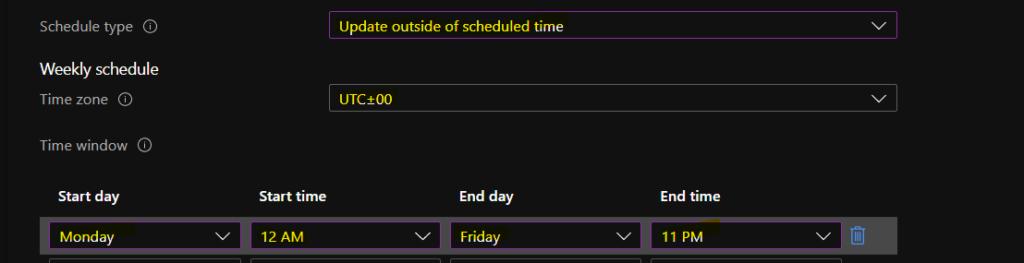
You can select the iOS/iPad updates outside the scheduled time. You must set a scheduled time when you don’t want this update to happen on iOS devices. The update will be initiated outside the scheduled time configured below.
How to Deploy or Assign Intune iOS Software Update Prevention Policy?
Once the Intune iOS Automatic Updates prevention Intune Policy is created, you can start assigning this policy to Azure AD Device groups. Deploy Updates Prevention Policy to iOS Devices.
Select Assignments—Click on Select Groups to find the appropriate Azure AD group to target the iOS update prevention policy. Once the policy is deployed to devices, the iOS software update will be postponed.
It would help to be careful about the policy settings while targeting the AAD device groups. In the policy configuration, there is an option to configure the devices’ time zones. Time zone configuration in this policy is a bit tricky.
It seems we need to segregate devices according to their time zones. I have not tested this, but it is my assumption regarding this policy setting. Learn how To Create Azure AD Dynamic Groups For Managing Devices Using Intune.
Reporting options for iOS update policies in Intune are coming soon.
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.

great guide.
Is there a way to stop users from manually updating?
A user voice item?
Perhaps this changed since you wrote the article. The “Days” field does not let you specify a delay, it lets you choose which weekdays to allow installations.
I found my own answer — it’s been moved to General Settings. More in this article: https://techcommunity.microsoft.com/t5/intune-customer-success/delaying-visibility-of-software-updates-in-intune-for-supervised/ba-p/345753
Do these updates happen over mobile data? Does it need Wi-Fi for update?
Apple restricts the ability to download iOS updates to WiFi or iTunes only. I don’t think we are able to control this from Intune.
If currently device has OS version 12.4, Can we install version 15.0.2 directly through intune policy?
Good Information. What options do we have for non-supervised iOS devices?
Is it possible for you to blog on similar lines for managing OS x?
Thanks for the information. I do have the same question as Srikanth above. Is there already a solutions for non-supervised IOS devices?
Could you also explain why this policy doesn’t work for non-supervised IOS devices? because when I enrolled my device as personal and installed the company portal app and installed the management profile, you should assume that it’s supervised from that point right?
Could you explain that part a little bit more?
Manual enrolment is not considered a Supervised mode. As per Apple’s policy, the company-owned devices can be put in the only supervised mode because of various reasons. I think privacy also matters here.
The option to get iOS devices into supervised mode is to enroll the device using DEP.
Hello,
I’m testing the iOS update policy,
Actually what`s happened afetr assigning the policy, the update has been downloaded but it didn’t get installled and it asks the user to install it now,
FYI: I have no update defer setting within the device configuration policy,
I would like the update to be installed automatiquely without any user intervention.
Thanks
Same Problem here. Get the Message that the Update couldnt installed and if i want to retry. If i retry the Installation i get a prompt to insert the Pin. But thats not what we want, right ?! I have read similar observations in various forums that the Policy only works with wifi, charged and that the User needs to confirm the update with the Pin. Is there any workaround to surpress this behavior ?
Hi Anoop,
Just one doubt: in my environment, we have almost 700 iOS devices, some of which are given by the company and some of which are personal IOS devices, but the enrollment method is not the Apple Device Enrollment Program (Apple DEP).
They have a manual method where users can download the company’s portal from the app store and enroll their device.
Will that policy work for that type of enrollment?