Hello Everyone; we are back with another interesting topic Restrict Malicious Apps on iOS and Android devices using Intune. In this article, let’s learn how to block an app on Android and IOS devices. Bring Your Own Device (BYOD) policies allow employees to use their own smartphones, tablets, and laptops for work-related tasks.
However, with this convenience comes the risk of employees installing apps that are not work-related or potentially harmful to the company’s security. Fortunately, there are ways to block apps and remove specific unapproved apps on Android and iOS devices through Intune.
In our previous articles, we have learned how to create Compliance policies for Android and iOS devices to protect the data on users’ devices. We can use compliance policies to make devices non-compliant if they installed the apps, and with Conditional access policies, we can block access to non-compliant devices.
If the apps are managed apps, we can uninstall the apps from users’ devices. This can be done by deploying apps in uninstall mode to the user group. If the apps are not managed, the devices still become non-compliant due to the Compliance policy that we created. Let’s discuss this in more detail in the below sections.
- Easy Way to Create a Compliance Policy for Android Devices in Intune
- Create Intune Compliance Policy for iOS iPadOS Devices
This article is helpful for the below scenarios
| iOS/iPadOS devices enrolled via the Apple Device Enrolment program(Supervised devices) |
| iOS/iPad OS devices enrolled as personal devices |
| Corporate Owned Devices Fully managed devices |
| Corporate Owned Devices with Work Profile |
| Personal Android devices enrolled with Work Profile |
Block malicious apps on iOS Corporate devices
Corporate iOS/iPadOS devices are enrolled in Intune using Automated Device Enrolment. These devices are Supervised devices, which provide full control over the devices. So we can restrict the users from using Apple Store in the Device Enrolment profile.
In case your Organization blocks access to the app store on corporate devices, we don’t require to create any restrictions. Users can install apps only from the Company Portal app, which is available to them.
If your organization allows users to install apps from App Store, we must create Device Restriction policies to hide/launch restricted apps. We need to create 2 Configuration profiles for iOS/iPad OS devices to restrict the launch of apps and Monitor the devices which have installed the blocked apps. Let’s see how we can create the configuration profiles for the same. I’m using one of the Apple default Application Notes for our example.
Configuration Profile to Block Launch/hide Restricted Apps
First, we will create a Device restriction profile to hide/launch the App on the user’s device. By creating this Profile, you can easily hide or launch specific apps as needed, giving you greater control over your device’s usage.
- Sign in to Microsoft Intune Admin Center
- Click on Devices > iOS/iPadOS devices > Configuration Profiles
- Click on Create Profile> Select Settings under profile type
- Click on Create
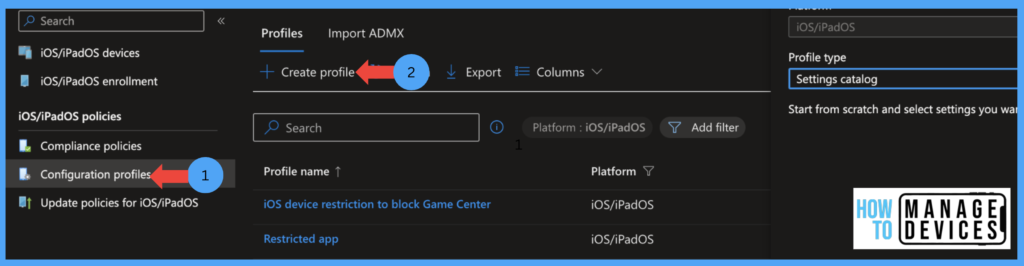
Now under the Basics page, provide the Name and Description for the configuration profile and click Next. Now under the Configuration Settings page, click Add Settings to view all the settings. Select the Restriction category and select Blocked App Bundle IDs. Now provide a Bundle ID for the App. In our case, the bundle ID for the Notes app is “com.apple.mobilenotes”.
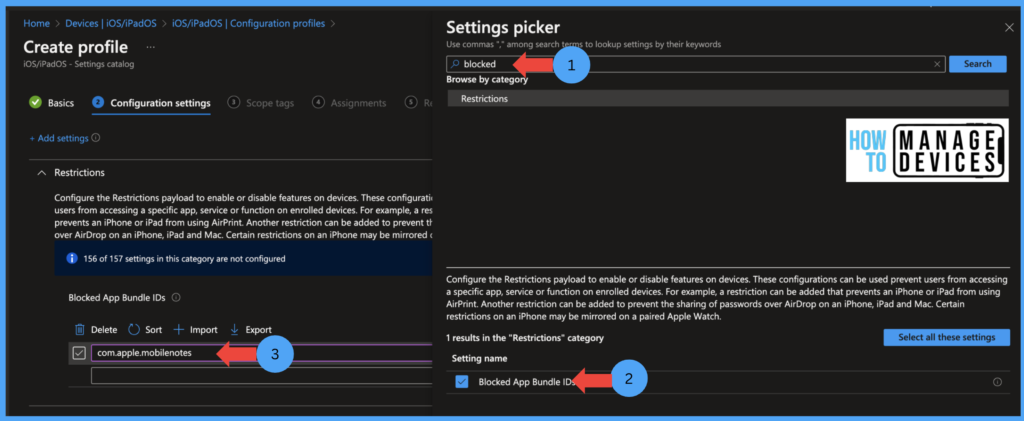
Click on Next, and under the Scope tags page, provide scope tags if you have any, and click on Next to Assignment Page. Now select the group to which the Profile needs to be added. If you want to exclude any user group, select the groups under Excluded Groups. Users in this group will not receive the Profile Click Next, review the settings, and click Create the Profile.
Configuration Profile to Monitor Restricted Apps Installed Devices
We can monitor applications on each device under Devices > Select the user device > Discovered apps. These discovered apps refresh every seven days, starting when the device was enrolled. Now let’s create a profile to monitor the devices which have installed Restricted apps.
- Sign in to Microsoft Intune Admin Center http://intune.microsoft.com/
- Click on Devices > iOS/iPadOS devices > Configuration Profiles
- Click on Create Profile> Select Template under profile type and select Device restriction template.
- Click on Create
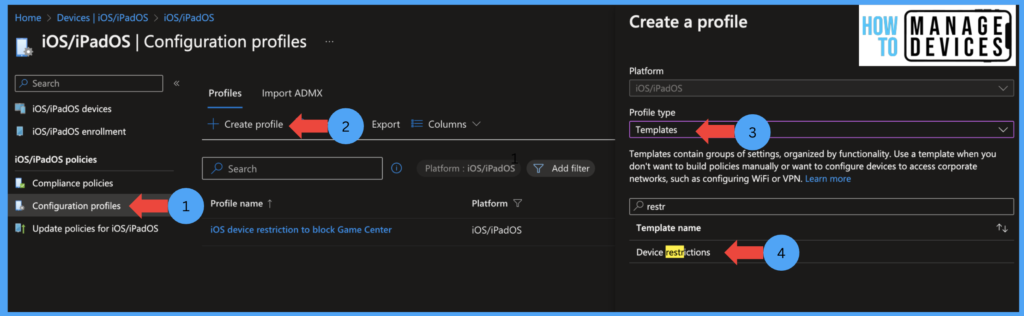
Now under the Basics page, provide the Name and Description for the configuration profile and click Next. Under the Configuration Settings page, select Restricted Apps and Select Prohibited Apps under the type of restricted apps. Now provide the App Store URL, App Bundle ID, App name, and Publisher. In our example, Notes is the application name, and other details are shown in the screenshot.
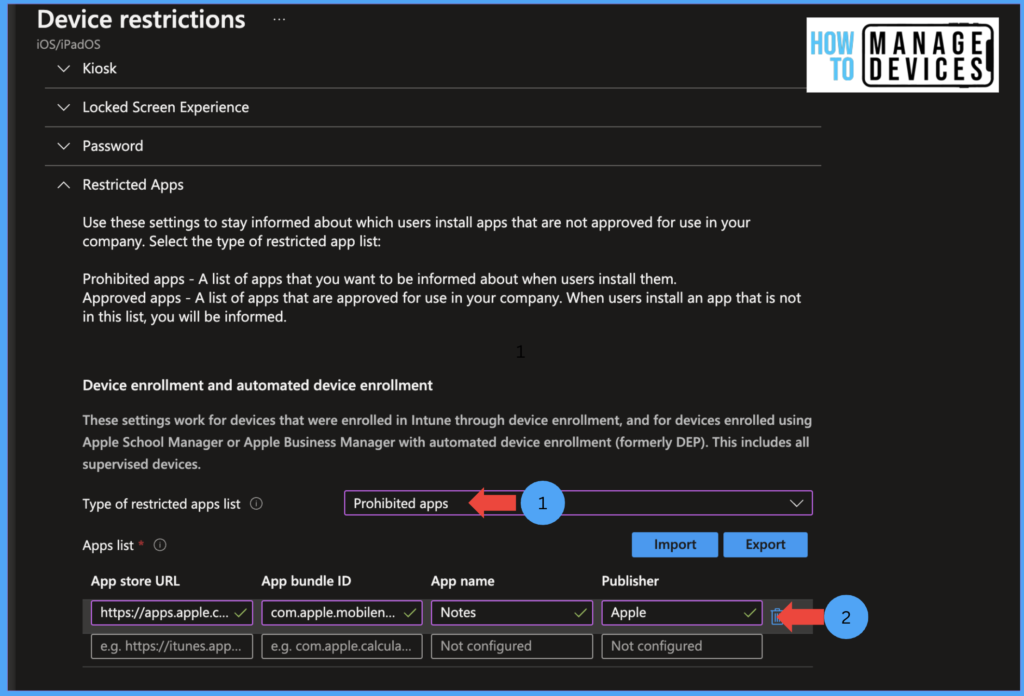
After defining the App, click Next and add groups under the Assignment page. This Profile can be assigned only to User groups. Click Next, review the settings, and Click on Create the Profile. Now if you want to view the devices which have installed restricted apps will be viewed under Devices with Restricted apps. Admin can view by navigating to Devices > Monitor > Devices with Restricted apps.
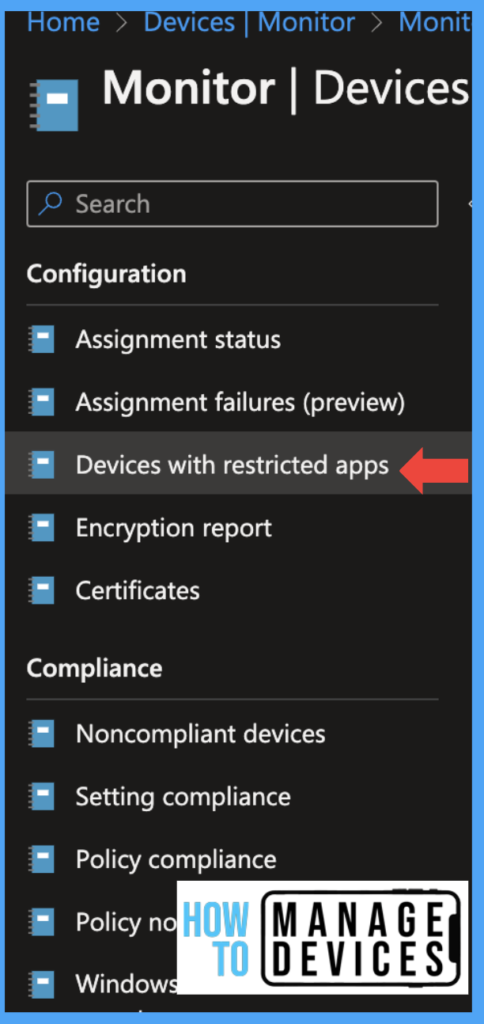
Few organizations don’t want apps to be installed on any device. Suppose the user installed before creating the Profile, and your Organization might want to uninstall the apps from the user’s device. This can be done easily on ABM/ADE enrolled devices in Intune.
Uninstall Blocked/Restricted Apps
To Uninstall any application on Supervised devices/Corporated devices enrolled under ADE, we need to publish the App first and assign the application to users in Uninstall mode. Let’s see how we can publish the apps in Uninstall mode.
- Sign in to Microsoft Intune Admin Center
- Click on App> All Apps > Add
- Now Select the iOS store app under App type
- Click Select
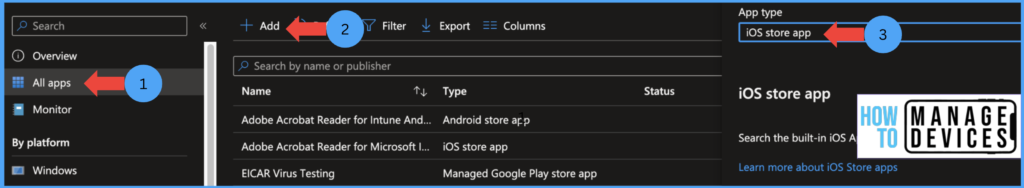
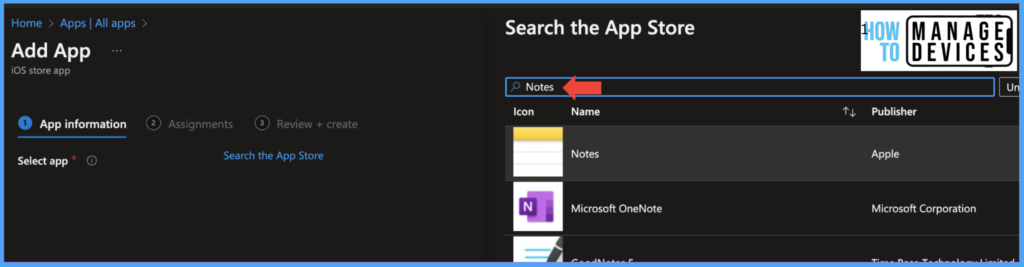
Now click Search the App Store, search for Notes App, select the App, and click Select. View the app information and click on the Next to the Assignment page.
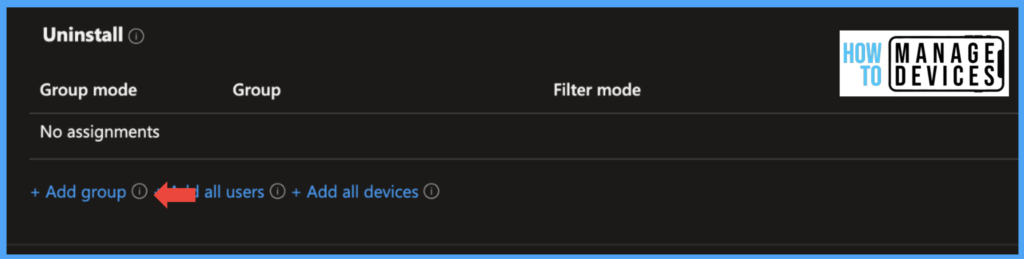
Here select any user group under Uninstall Intune will uninstall the App on user devices who are part of the user group under Uninstall. Click Next and Click on Create to create the App
Thus, we can create Configuration Profile for Restricted apps for Monitoring the restricted apps. We can also Uninstall the Restricted App from Managed/Supervised iOS devices. Let’s see how we can manage this on BYOD Enrolled iOS devices.
Block Malicious Apps on BYOD-enrolled iOS/iPad OS Devices.
On BYOD devices, Intune has limited access/control over the devices. This can be achieved by creating Compliance Policy and blocking access to corporate data on non-compliant devices with the help of Conditional access policies. Let’s see what options can be used to mark the device as Non-Compliant if the user has installed restricted apps.
- Sign in to Microsoft Intune Admin Center http://intune.microsoft.com/
- Click on Devices > iOS/iPadOS devices > Compliance Policies
- Click on Create Policy > Create
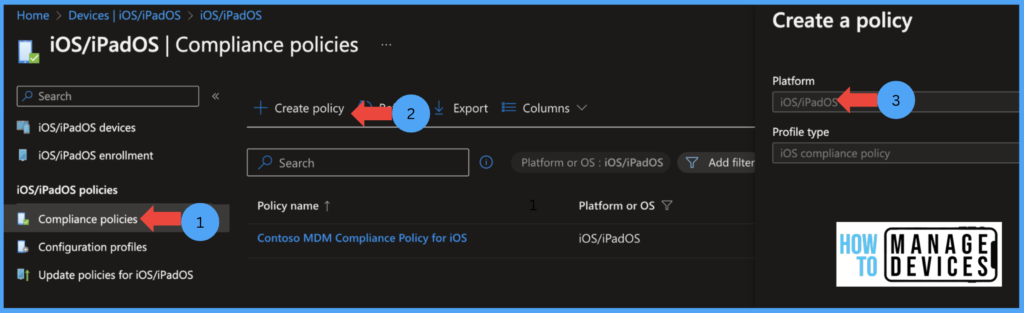
Under the Basics page, provide the Compliance policy’s name and Description and click Next. Under the Compliance Settings page, click on System Security and define the app name and app Bundle ID under the Device Security section. Click on Next, and under Actions for the non-compliance page, Select Mark device non-compliant Immediately, and click Next. Now Assign the compliance policy to user groups.
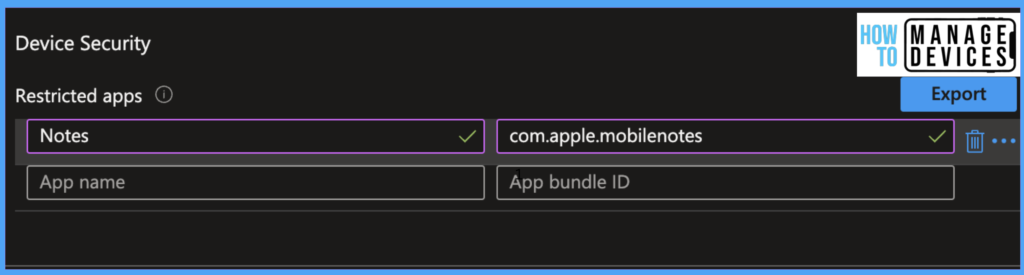
Click Next and review the settings configured and click on Create. Now devices with the Notes App installed are treated as Non-compliant.
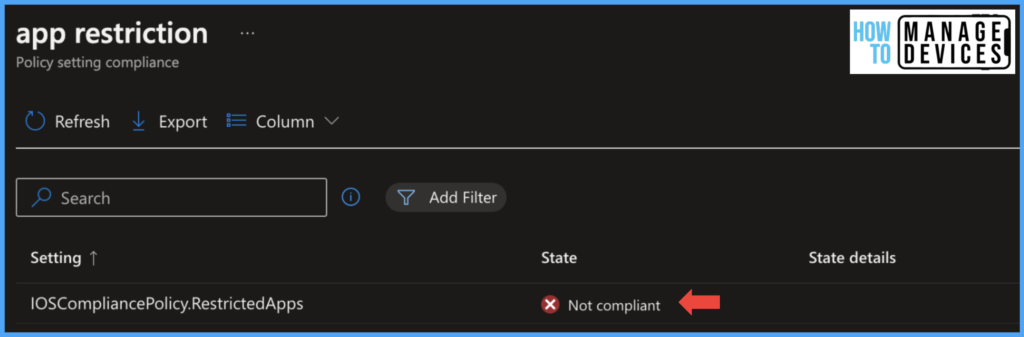
If we have a configured Conditional access policy, which requires the device to be compliant, then access to the corporate device will be blocked. If the user uninstalls the App, then the device will be Compliant, and the user will be access to the corporate data.
Block/Restrict Malicious Apps on Android Devices
Similar to iOS devices, users can enroll Android devices as BYOD devices with Work Profile, Corporate devices as Fully managed devices, and Corporate devices with Work profiles. Users will have only managed Google Play Store on Corporate Fully Managed devices rather than the normal Play Store.
Users will be able to download apps that are assigned to them by the admins. But, organizations always have the option to allow users to download all apps from Google Play Store. This can be achieved by creating a device restriction enabling users to download all apps from Google Play Store on Corporate Owned Fully Managed Devices. Let’s see how we can enable this restriction.
- Sign in to Microsoft Intune Admin Center http://intune.microsoft.com/
- Click on Devices > Android devices > Configuration Profile
- Click on Create Profile> Select Android Enterprise under Platform
- Select Device Restriction as the profile type under Fully Managed, Dedicated, and Corporate Owned Work Profile
- Click on Create
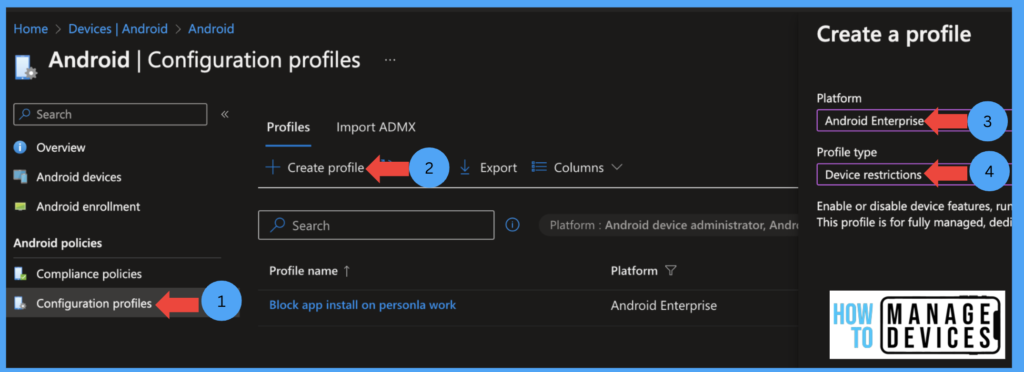
Under the Basics page, provide the Configuration Profile’s name and Description and click Next. Under the Configuration Settings page, click the Application category and click Allow for Allow access to all apps in the Google Play store. This setting will enable users to install any apps from Google PlayStore.
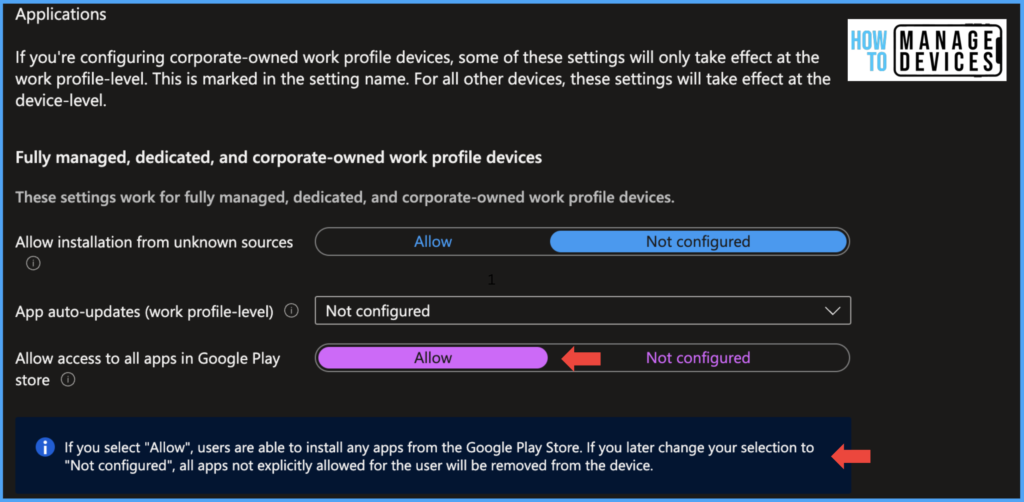
If you want to delete the apps which are malicious/unwanted and want to restrict app installation, we can achieve this in 2 ways. The Simplest way is to set Allow access to all apps in Google Play store value to Not Configured. When you change this, all apps installed on Corporate devices and not explicitly Approved by your Admin will be uninstalled. Users will be notified that the apps are removed/deleted by Admin.
If your Organization wants to allow users to download from Google Play Store and block a few apps which are required to be restricted, this can be achieved by uninstalling the apps from devices. To uninstall the App, we need to publish the App in Intune. Let’s see how we can uninstall the installed apps.
- Sign in to Microsoft Intune Admin Center
- Click on Apps > All Apps > Add > Managed Google Play App
- Click Select
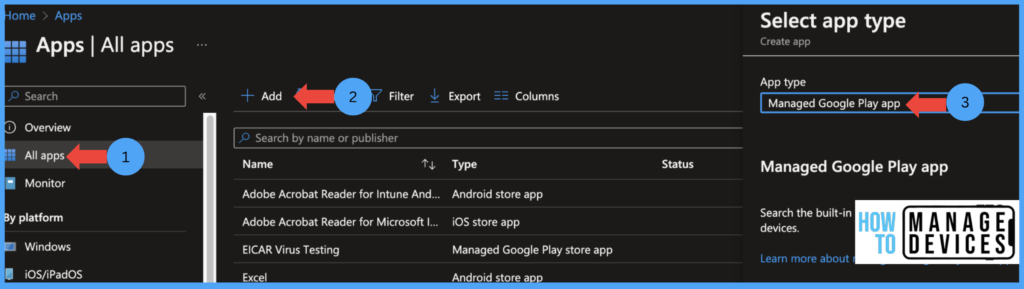
For our testing, I’m using the Microsoft Word application. Search for the Word app, Select the App, and click on Approve. Click on Sync. Syncing the App to Intune apps store may take a few minutes. Search for Word application.

Select the Word, click on Properties, scroll to the bottom, and click Edit next to Assignments. Now under uninstall, add the user group and click Review and Save. Once the device syncs to Intune, The Word application will be uninstalled from the user’s device, and users will get a notification regarding the uninstallation of the App.
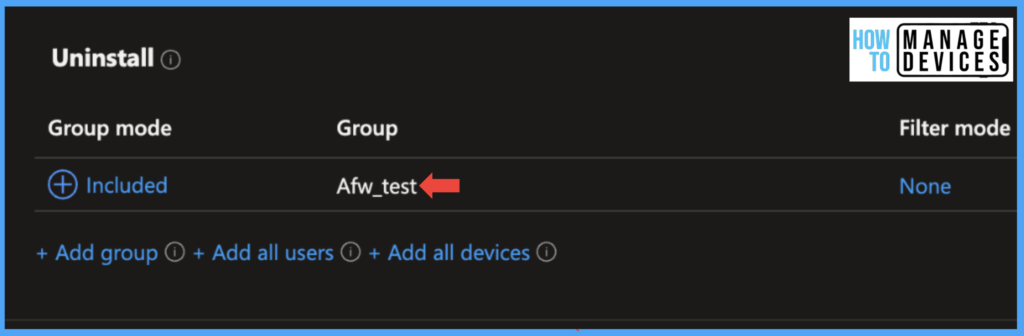
Suppose the user tries to install the restricted App. In that case, the user will be displayed an error message stating, “Your administrator has not given you access to this item,” so users cannot install the apps, even though they can install the rest.
Block Apps on Personal Android Devices Enrolled with Work Profile
Users can enroll their personal devices with Work Profile, and a separate Work container is created on their BYOD devices. Managed Google Play Store is created in the work profile. Users can download apps from this Managed Google Play Store, but the user has apps which approved and assigned by your admins. Users cannot download other apps from Managed Google Play Store. Thus most BYOD Android devices are safe.
Note: Intune does not have control over the Personal profile of BYOD devices as Intune cannot manage the apps installed on the personal profile.
Corporate Owned with Work Profile Devices
In the above section, we blocked/ restricted apps on Corporate owned dedicated devices, In this section, let’s see how we can do the same for Corporate Owned with Work Profile devices. On this type of device, users can install apps from normal Google PlayStore, unlike Corporate owned dedicated devices. To restrict the installation app, we can create a Device restriction profile.
- Sign in to Microsoft Intune Admin Center
- Click on Devices > Android devices > Configuration Profile
- Click on Create > Profiletypelect Android Enterprise under Platform
- Select Device Restriction as the profile type under Fully Managed, Dedicated, and Corporate Owned Work Profile
- Click on Create
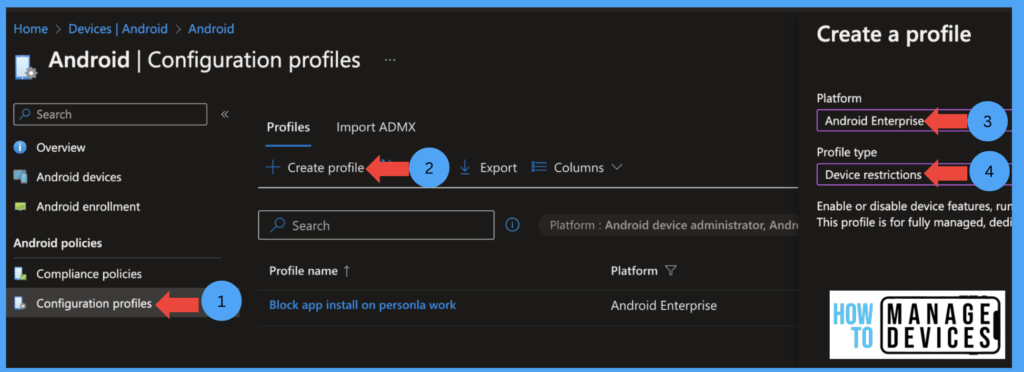
Give Configuration Profile’s name and Description under the Basics page, and click Next. Under the Configuration Settings page, click the Personal Profile category Select Blocked Apps under the Type of restricted apps, search for the App you want to block, and select the App.
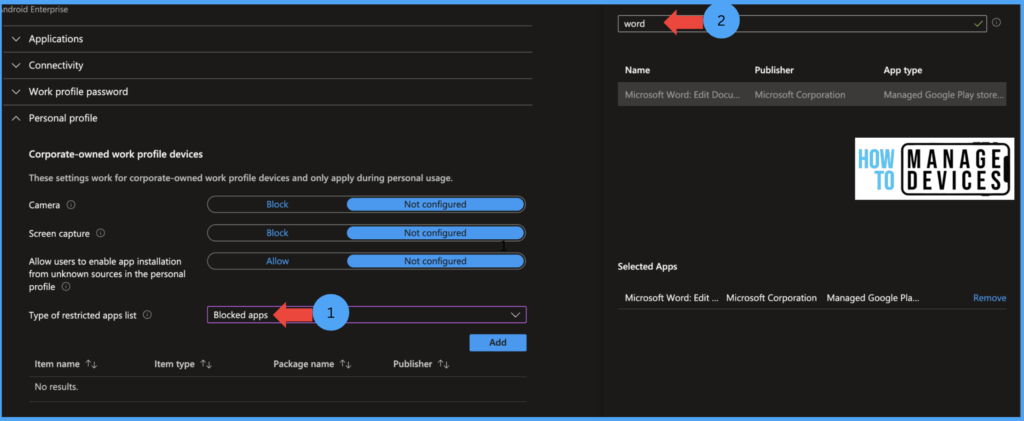
Click Next and assign the restrictions to the user group under the Assignment page, click Next and create the Device restriction. Once the device is synced, the user will get a notification ” Personal app removed. Your IT admin no longer allows Word in your personal profile“. If the user navigates Google PlayStore, they will be unable to install the App and get the error “Your administrator has not given you access to this item.”
Note: In Corporate Owned devices with Work Profiles, the personal profile is often treated as Work Profile.
I hope this article helps you keep unwanted or malicious apps off of your Android and iOS devices, whether personal or corporate devices, in Intune. Having extra security measures to keep your data and personal information safe is always good.
Author
About Author – Narendra Kumar Malepati (Naren) has 11+ years of experience in IT, working on different MDM tools. Over the last seven years, Naren has been working on various features of Intune, including migration from different MDMs to Intune. Naren mainly focuses on Android, iOS, and MacOS.

Hi there, so I was testing the Blocked App Bundle IDs setting, but it is correct that this will only apply to corporate devices, that means any personal iOS device enrolled in Intune, should be using compliance policies so when any unapproved app is detected, CA policies block access to, Office365, for example. Is this correct? Thanks,