Hello everyone, In this post, we will explore how to set the Restrict Unauthenticated RPC Clients Policy using Intune. We will check how to apply this policy using Intune’s Configuration Profiles. The main aspect of this policy is to acquire understanding and hands-on experience in configuring and setting the Restrict Unauthenticated RPC Clients Policy Using Intune.
Restrict Unauthenticated RPC Clients Policy Using Intune governs handling unauthenticated RPC clients that establish connections with RPC servers. The scope of this policy encompasses all RPC applications. When dealing with this policy within a domain environment, exercising caution is advised due to its potential to impact a broad array of functionalities, including processing group policies.
If you disable this policy, the RPC server runtime will utilize the “Authenticated” value for Windows Clients and the “None” value for Windows Server versions that support this policy. If this policy is left unconfigured, it remains in a deactivated state. The RPC server runtime will behave as if it were activated with the “Authenticated” value for Windows Clients and the “None” value for Server SKUs supporting this policy.
Upon enabling this policy, it instructs the RPC server runtime to restrict the connections of unauthenticated RPC clients to RPC servers operating on a given machine. There are three options you will get when you enable this policy. Those are:
- None – Grants permission for all RPC clients to connect to RPC Servers on the target machine where the policy is implemented.
- Authenticated – Permits only authenticated RPC Clients (as defined above) to connect to RPC Servers on the target machine, with possible exemptions for certain interfaces.
- Authenticated without exceptions – Allows solely authenticated RPC Clients (as defined above) to connect to RPC Servers on the target machine without any exceptions.
Note! It’s important to remember that this policy alteration will not take effect until the system is rebooted.

- Allow Network Connectivity During Connected-Standby Policy using Intune
- Don’t Allow Passwords to be Saved Policy using Intune
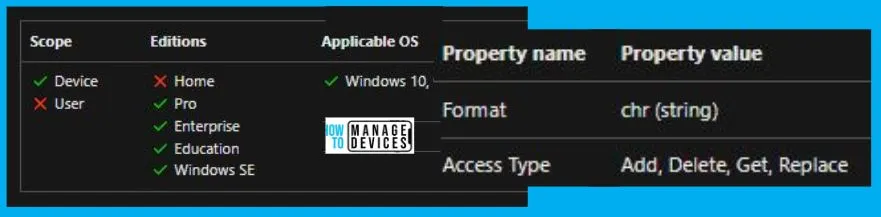
Windows CSP Details RestrictUnauthenticatedRPCClients
We will see Windows CSP Details for this Policy setting RestrictUnauthenticatedRPCClients. This policy revolves around managing Remote Procedure Call (RPC) connections in Windows environments. RPC is a protocol that allows software programs to communicate across a network. It’s fundamental for various tasks, including remote administration, file and printer sharing, and communication between software components.
The policy setting you described controls how the RPC server runtime handles unauthenticated RPC clients connecting to RPC servers. This policy helps you regulate RPC connections’ security and authentication level, ensuring that only authenticated clients can access specific RPC servers. Understanding the potential implications and testing policy changes in controlled environments is crucial before implementing them in production.
CSP URI – ./Device/Vendor/MSFT/Policy/Config/RemoteProcedureCall/RestrictUnauthenticatedRPCClients
Restrict Unauthenticated RPC Clients Policy using Intune
To set the Restrict Unauthenticated RPC Clients Policy Using Intune, follow the steps stated below:
- Sign in to the Intune Admin Center portal https://intune.microsoft.com/.
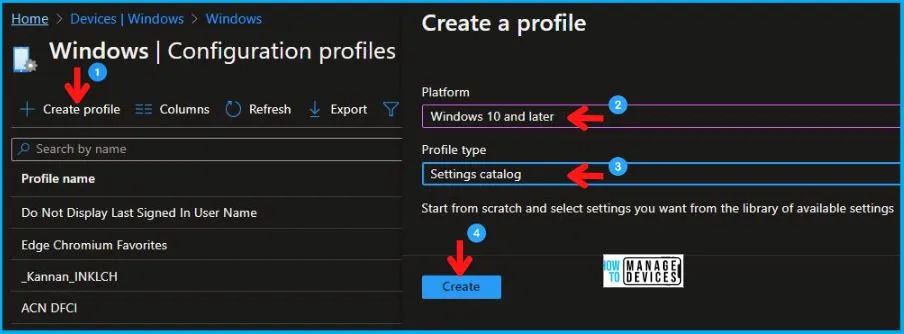
- Select Devices > Windows > Configuration profiles > Create a profile.
In Create Profile, Select Windows 10 and later in Platform, and Select Profile Type as Settings catalog. Click on Create button.
| Platform | Profile Type |
|---|---|
| Windows 10 and later | Settings Catalog |
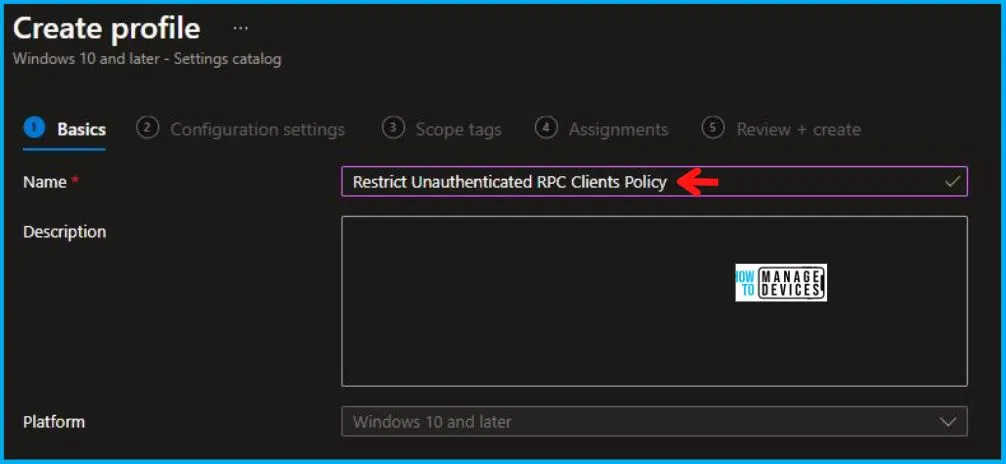
On the Basics tab pane, provide a name for the policy as “Restrict Unauthenticated RPC Clients Policy.” Optionally, you can enter a policy description and proceed by selecting “Next.“
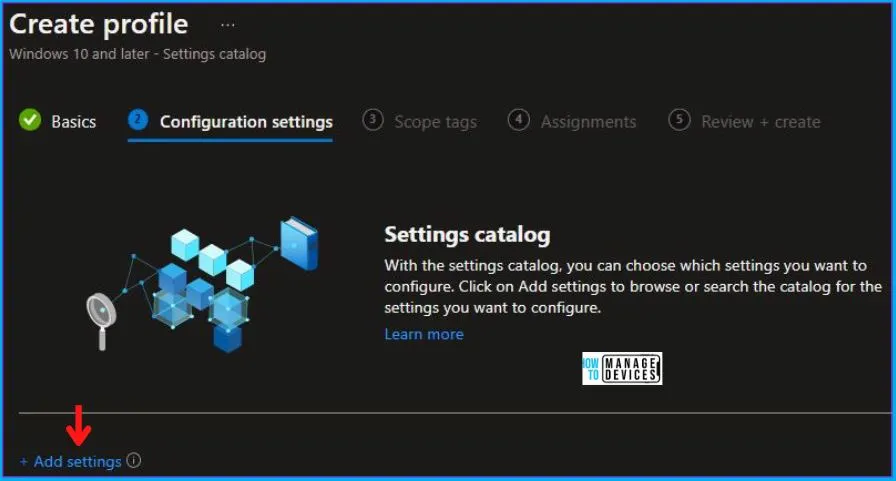
Now in Configuration Settings, click Add Settings to browse or search the catalog for the settings you want to configure.
In the Settings Picker windows, search by the keyword RPC, among many, you’ll get the category Administrative Templates\System\Remote Procedure Call, and select this.
When you select the option stated above, you will see one option: Restrict Unauthenticated RPC clients. After selecting your setting, click the cross mark at the right-hand corner, as shown below.
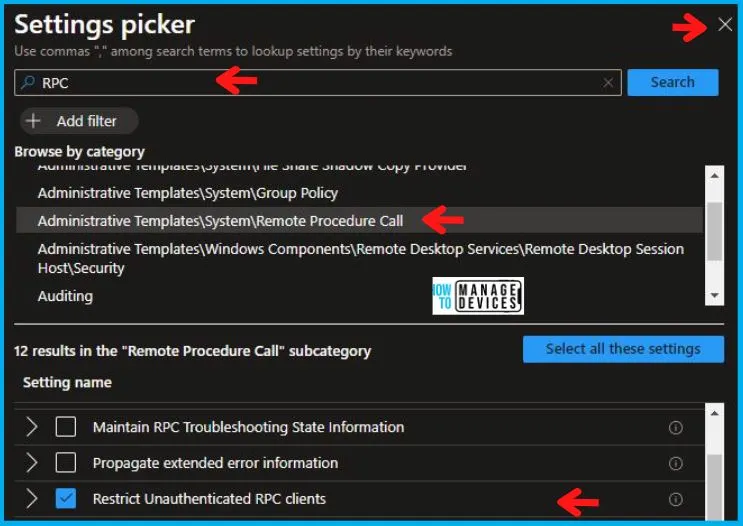
In the Administrative Templates, when you set Restrict Unauthenticated RPC clients to Enabled, you can set RPC Runtime Unauthenticated Client Restriction to Apply. This setting allows you three options, as described above in the post, which are as follows:
- None
- Authenticated
- Authenticated without exceptions
I have chosen Authenticated here and click on Next, as shown below in the image.
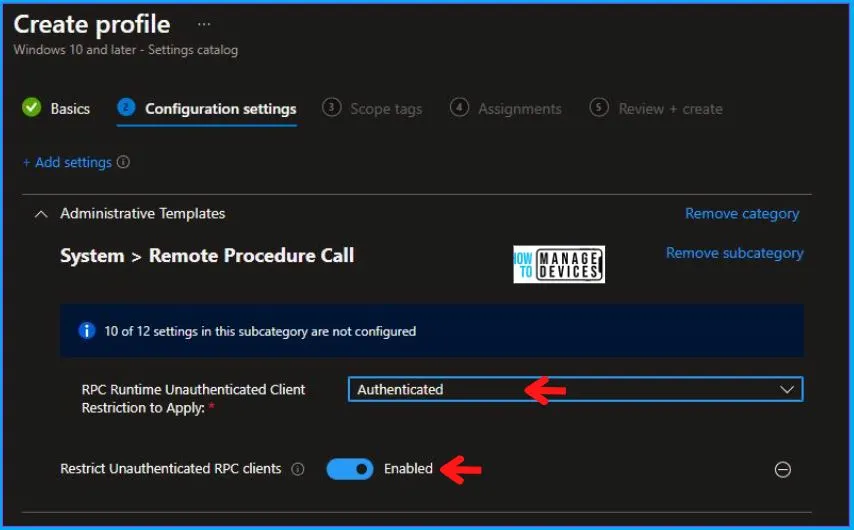
Using Scope tags, you can assign a tag to filter the profile to specific IT groups. One can add scope tags (if required) and click Next to continue. Now in Assignments, in Included Groups, you need to click on Add Groups, choose Select Groups to include one or more groups, and click Next to continue.
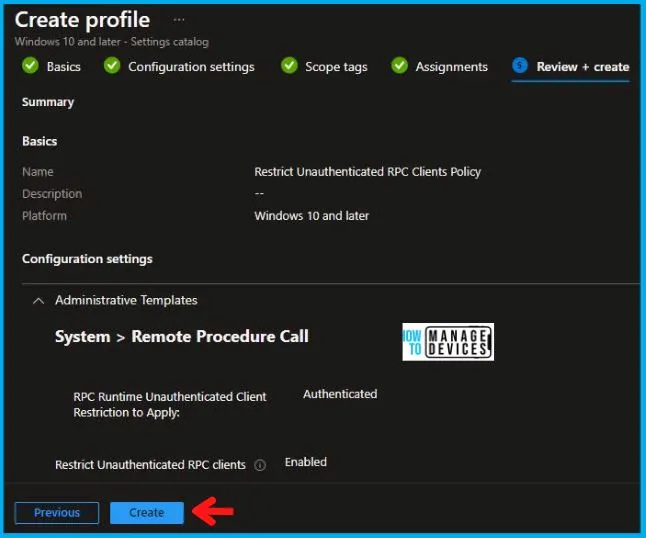
In the Review + Create tab, you need to review your settings. After clicking on Create, your changes are saved, and the profile is assigned.
Upon successfully creating the “Restrict Unauthenticated RPC Clients Policy,” notification will appear in the top right-hand corner, confirming the action. You can also verify the policy’s existence by navigating to the Configuration Profiles list, where it will be prominently displayed.
Your groups will receive your profile settings when the devices check in with the Intune service. The Policy applies to the device.
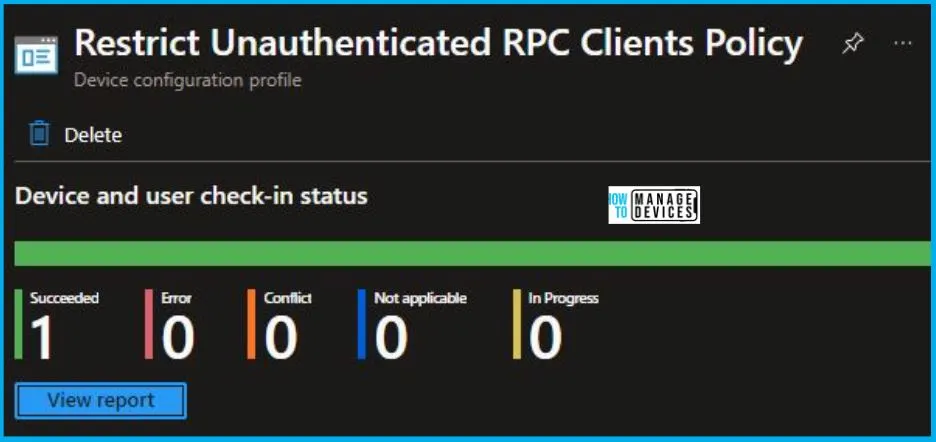
Intune Report for Restrict Unauthenticated RPC Clients Policy
From Intune Portal, you can view the Intune settings catalog profile report, which provides an overview of device configuration policies and deployment status.
To monitor the implementation of the policy, you must choose the appropriate policy from the Configuration Profiles list. Here I choose Restrict Unauthenticated RPC Clients Policy from the list. By examining the status of device and user check-ins, you can ascertain the successful application of the policy. If you need more comprehensive details, you can click the “View Report” option to access supplementary insights. As you can see, it is successfully implemented on the targeted device.
Registry-Key Verification for RestrictUnauthenticatedRPCClients
To access the registry settings that hold the group policy configurations on a specific computer, you can execute “REGEDIT.exe” on the target computer and navigate to the precise registry path mentioned below where these settings are stored.
- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\5B88AEF1-09E8-43BB-B144-7254ACBBDFF3E\default\Device\RemoteProcedureCall
When you navigate the above path in the Registry Editor, you will find the registry key RestrictUnauthenticatedRPCClients. Refer to the table and image below.
| Registry Name | Data |
|---|---|
| RestrictUnauthenticatedRPCClients | Enabled |
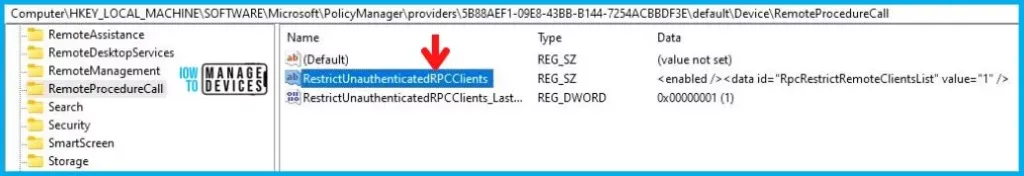
As you can confirm from the above image, the Registry key has been created, and we can confirm that the policy has been implemented on the target device successfully.
Author
Abhinav Rana is working as an SCCM Admin. He loves to help the community by sharing his knowledge. He is a B.Tech graduate in Information Technology.

Hi, thanks for the article,
What are the risks? if enabled this for windows clients in a hybrid domain network?