Today we are discussing 7 Effective Ways to Secure Data in Zero Trust with Microsoft Intune. As you know that Organizational dta are very important. So, Organizations managing access to company data through Conditional Access policies. These policies help ensure that only trusted and compliant devices can connect to corporate resources.
By enforcing security requirements before granting access, organizations can protect sensitive information and reduce the risk of unauthorized entry or data misuse. Conditional Access supports a secure data environment. It checks both the user and device compliance before allowing access, helping prevent threats from unmanaged or noncompliant devices.
This ensures that only secure endpoints can communicate with oganizational systems. Using secure and encrypted Wi-Fi configurations helps protect corporate information during transmission and prevents unauthorized access. Centrally managing Wi-Fi profiles for devices such as iOS, macOS, and Android ensures secure connectivity.
In Microsoft Intune, IT administrators can configure authentication, encryption, and access settings in one place. This centralized approach reduces errors and simplifies onboarding for users. Combining Conditional Access with secure Wi-Fi management creates a strong security for organizational data.
Table of Contents

7 Effective Ways to Secure Data in Zero Trust with Microsoft Intune
Above we discussed an overall thing about the Data Security Through Conditional Access and Network Protection. Keeping data safe on different devices means making sure the same security rules are used everywhere. Whether it’s a phone, or laptop, using the same protection helps control how data is shared and who can access it. This consistency reduces risks and keeps the company’s information compliant and secure across all devices.
| Check | Minimum License Requirements |
|---|---|
| Data on Android is protected by app protection policies | Microsoft Intune Plan 1 |
| Data on iOS/iPadOS is protected by app protection policies | Microsoft Intune Plan 1 |
| Conditional Access policies block access from unmanaged apps | Microsoft Intune Plan 1 Microsoft Entra ID P1 (for Conditional Access) |
| Conditional Access policies block access from noncompliant devices | Microsoft Intune Plan 1 Microsoft Entra ID P1 (for Conditional Access) |
| Secure Wi-Fi profiles protect iOS devices from unauthorized network access | Microsoft Intune Plan 1 |
| Secure Wi-Fi profiles protect macOS devices from unauthorized network access | Microsoft Intune Plan 1 |
| Secure Wi-Fi profiles protect Android devices from unauthorized network access | Microsoft Intune Plan 1 |
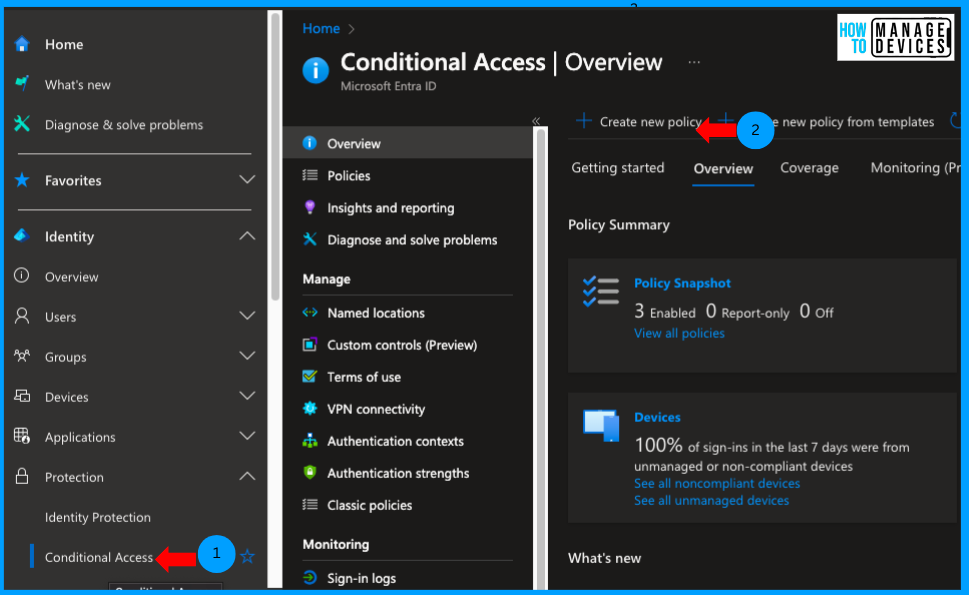
What is Conditional Access
Conditional Access is a security feature from Microsoft Entra. You can use it in both Microsoft Entra ID and Microsoft Intune. Since they share the same setup, you don’t need to switch between them to manage policies. In Microsoft Intune, Conditional Access helps protect apps and data.
It checks things like who the user is, where they’re signing in from, and whether their device is safe. Only users and devices that meet the rules can access company resources like cloud apps. This helps keep your organization secure while letting people work from different places and devices.
- In the below screenshot you will get to know Setup Conditional Access for Remote Help with Intune | RemoteAssistanceService.
See More in :Best Guide to Setup Conditional Access for Remote Help with Intune | RemoteAssistanceService
Data on Android is Protected by App protection Policies
App protection policies play a key role in keeping data safe on Android devices. They make sure only approved and secure apps can open or use company files. Without these protections, there’s a chance that sensitive data could be copied or shared through personal or unsafe apps.
- These policies also include rules like requiring passwords, using encryption, and blocking data sharing between personal and work apps.
- This helps protect company data even when employees use their personal Android phones for work.
- The below screeshot is an example for Authentication on Android Work Profile.
See More: Intune Policies Blocking Edge Browser Callback during SSO Authentication on Android Work Profile

Data on iOS/iPadOS is Protected by App Protection Policies
For iPhones and iPads, app protection policies ensure business data stays inside secure and trusted applications. These policies help organizations protect their data even when employees use personal Apple devices for work. The policies stop users from saving or sharing sensitive files in unprotected apps.
For Remediation: Configure Intune app protection policies for iOS/iPadOS devices to separate work data from personal data and reduce data leakage.
See More: How to Manage Apple Intelligence on iOS or iPadOS Devices using Intune

Conditional Access Policies Block Access from Unmanaged apps
Conditional Access helps control which apps can reach company data. It checks if an app is secure and managed before allowing access. If the app doesn’t meet security requirements, it is automatically blocked. This reduces the risk of data loss through unsafe or unapproved applications. Combining Conditional Access with app protection ensures that only trusted apps can connect to corporate systems and handle information safely.
- For Remediation Set up Conditional Access rules in Microsoft Entra ID to block access from unmanaged or unapproved apps.
See More: Deploy Unmanaged macOS App using Intune
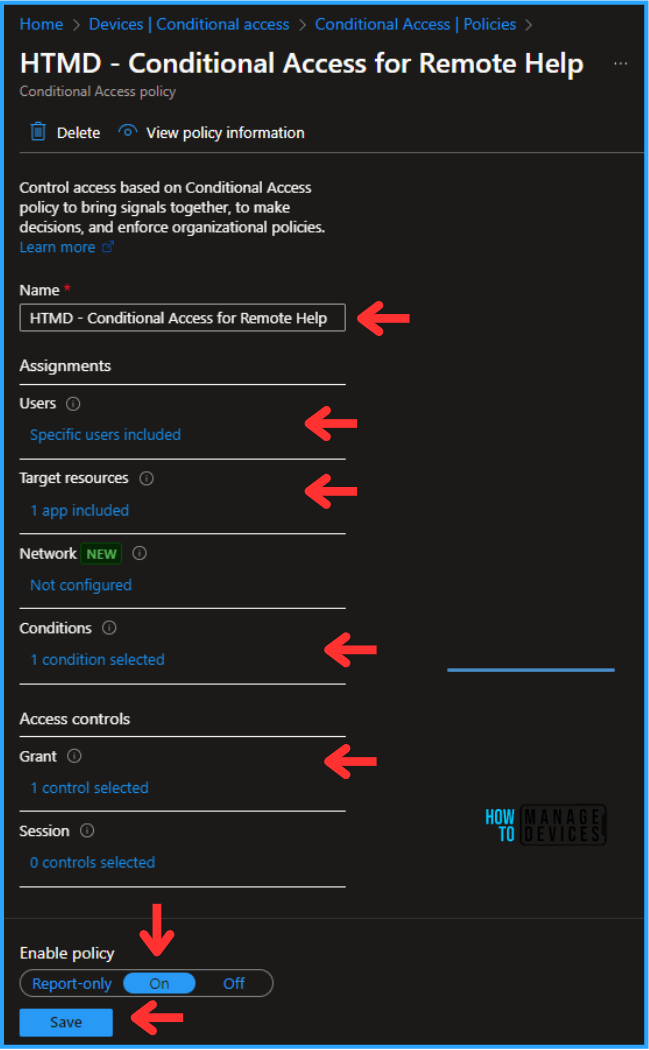
Conditional Access policies Block Access from Noncompliant Devices
Conditional Access also ensures that only secure and compliant devices can connect to company resources. A device that doesn’t follow security rules and missing updates, lacking encryption, or having weak settings will be denied access. This helps protect sensitive data from being reached through unsafe devices. Enforcing these rules supports a Zero Trust security approach, where every device and user must meet compliance standards before getting access.
- Remediation: You can use Intune compliance policies and Conditional Access to restrict access for noncompliant devices until they meet security requirements.
- Below is an example post for Noncompliant Device deployment.
See More Send Notifications for Noncompliant Devices in Intune
Importance Of Network Protection
Network protection through Intune is very important because it keeps devices connected only to safe and trusted networks. When Wi-Fi settings are not managed properly, users might connect to unsafe or fake networks where attackers can steal data or access company information.
See More : Network Protection Blocks DeepSeek on MacOS using Intune Enforcement Level Polic
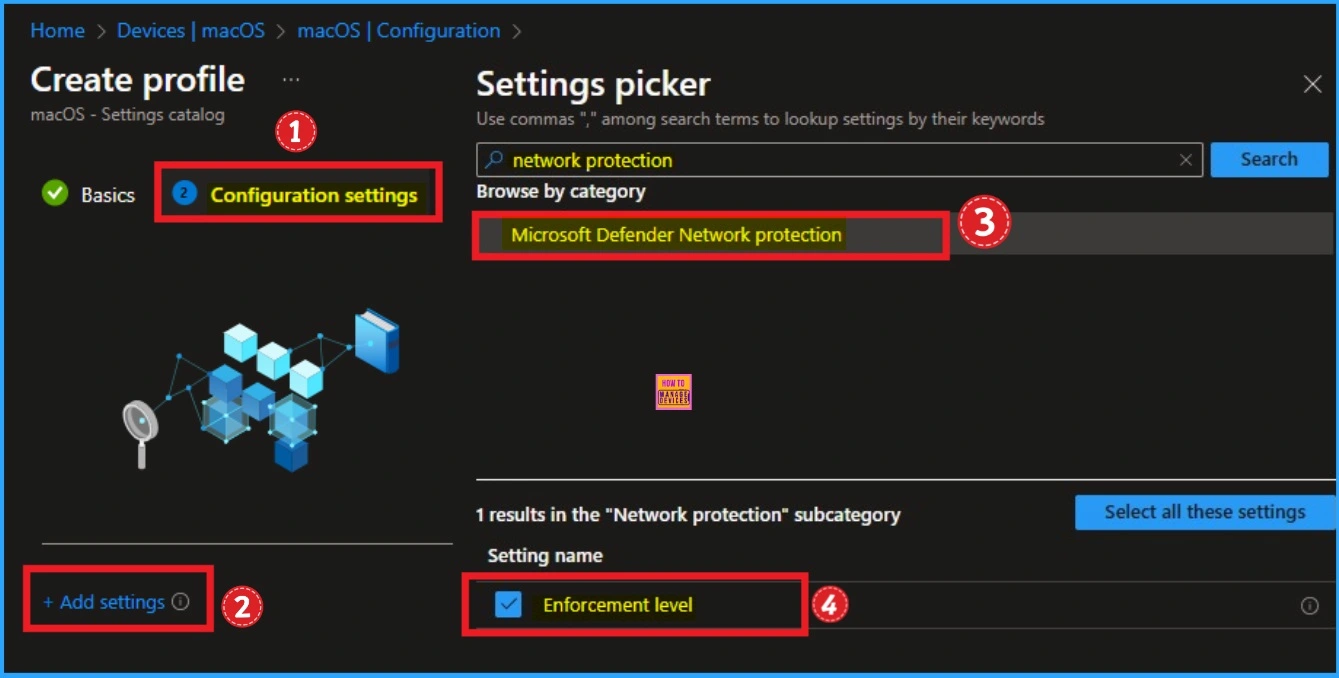
Secure Wi-Fi profiles Protect iOS Devices from Unauthorized Network Access
Wi-Fi protection helps ensure that iPhones and iPads connect only to safe and trusted networks. Secure Wi-Fi profiles managed through Intune prevent users from joining public Wi-Fi networks that could steal data. These profiles also make it easier for employees to connect to company Wi-Fi automatically, ensuring secure and encrypted connections every time.
- Deploy Wi-Fi profiles using Intune to automatically connect iOS devices to approved, secure networks.
- The below screenshot is for Setup Wi-Fi Profile for macOS devices using Intune.
Read More: Setup Wi-Fi Profile for macOS devices using Intune.

Secure Wi-Fi profiles Protect macOS Devices from Unauthorized Network Access
For Mac computers, secure Wi-Fi profiles are equally important. Managing Wi-Fi settings through Intune helps enforce encryption and authentication so that users only connect to trusted networks. This centralized setup reduces mistakes during manual configuration and keeps company data safe while employees work from different locations.
- For Remediation – Configure and push secure Wi-Fi profiles through Intune for all company-managed macOS devices.

Secure Wi-Fi profiles protect Android Devices from Unauthorized Network Access
Android devices also benefit from secure Wi-Fi profiles that ensure connections only to approved company networks. Without these profiles, there’s a risk of connecting to unsafe or public Wi-Fi, which could expose sensitive data. By using Intune to manage and assign Wi-Fi settings, organizations can maintain encrypted and protected connections that safeguard data during transmission.
- Remediation: Assign secure Wi-Fi profiles in Intune for Android devices to control access and maintain secure, encrypted connections.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.


