Let’s discuss The Free Zero Trust Workshop, which explains the strategy and translates it into practical deployment. Zero Trust protects user accounts, devices, applications, and data. It adapts to modern challenges and ensures security no matter where those resources are located.
Microsoft is focused on keeping customers safe by addressing cybersecurity threats and promoting Zero Trust principles. Their Secure Future Initiative encourages consistent security practices across the company.
The Microsoft Security division supports customers using its products to protect against cyber threats, though many find it challenging to start their Zero Trust journey. Security works best when teams collaborate, and customers need partners to help them create and carry out their security plans.
In this post, I would like to give you an overview of the Zero Trust Workshop and explain how strategy is translated into practical deployment.

Table of Contents
What is Zero Trust?
Zero Trust is a security strategy, not a product or service. It is a method for designing and implementing the following security principles.
> Verify Explicitly
> Use Least Privilege Access
> Assume Compromise
Who should attend the Zero Trust workshop?
The workshop benefits Zero Trust leaders, Pillar Architects, Leads, Experts, Cybersecurity Team Members, and Enterprise Architects.
Zero Trust Workshop Strategy
The Zero Trust Workshop helps customers implement Zero Trust principles to their existing technology. It allows them to assess their current status and set aims for expanding their Zero Trust approach. Slalom uses this workshop to assist clients in strengthening their cyber resilience strategy. It provides a clear overview of the organization’s situation and a structured best practices plan. This easy-to-use tool has a major impact on clients how it simplifies and organizes complex operations.
- 2024 Cybersecurity Certifications For IT Professionals
- How To Prepare Microsoft Copilot With Zero Trust
- Top 75 Latest Intune Interview Questions And Answers
Steps to Start Zero Trust Journey Through the Workshop
The Zero Trust Workshop consists of two main parts, both downloadable files: the Zero Trust Basic Assessment (optional) and the Zero Trust Strategy Workshop. The following table shows the steps to start the Zero Trust Journey through the Workshop.
| Steps to Start Zero Trust Journey | Description |
|---|---|
| Step 1: Zero Trust Basic Assessment (optional) | This tool helps identify common misconfigurations and gaps, like having too many global admins, before starting your Zero Trust journey. |
| Step 2: The Zero Trust Strategy workshop | This Section provides a guided summary of the Zero Trust framework, focusing on its core pillars, Identity, Devices, Data, Networks, Infrastructure and Applications, and Security Operations. Each pillar has clear steps on what to do first, next, and later. |
| Step 3: Document results and create a plan | Identify improvements and update your security plan every six months. Upload results to your project management tool like ADO or JIRA. |
Upcoming Pillars
Microsoft is launching the Identity, Devices, and Data pillars. They will also introduce the Network, Infrastructure and Application, and Security Operations pillars in the coming months. The workshop website will provide updates as they become available.
The following image shows an example of the strategy and co-management areas of the Devices pillar of the workshop.
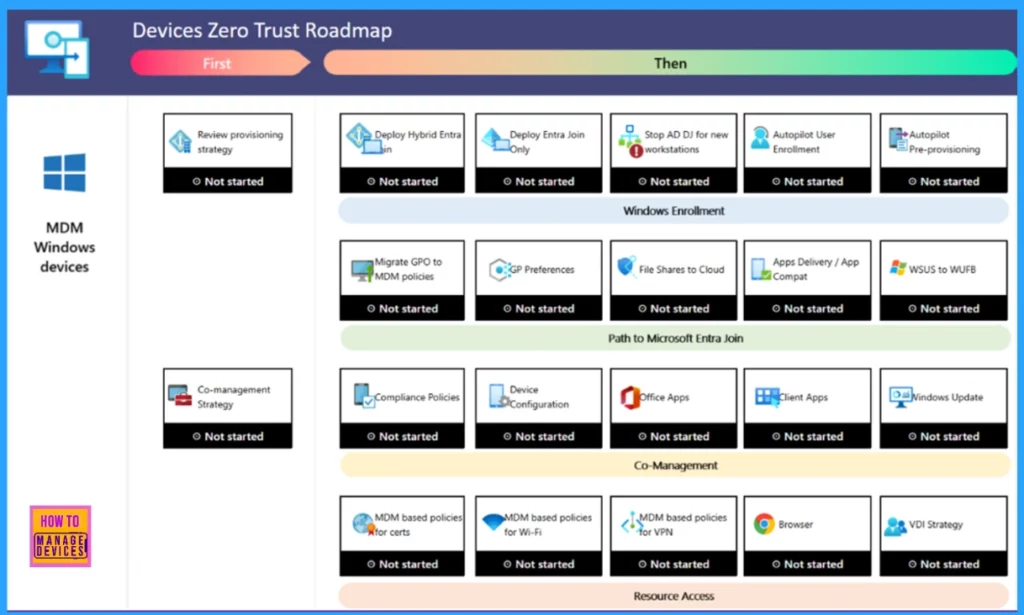
To learn more about the Zero Trust strategy, visit the Zero Trust Workshop site, which offers comprehensive training videos and resources.
The latest Microsoft Digital Defense Report shows that cyber threats are increasing. To improve protection, Microsoft joined with NIST’s National Cybersecurity Center of Excellence (NCCoE) and over 20 security vendors. They published a guide on how to adopt NIST’s Zero Trust reference architecture using Microsoft’s Security products.
Resources
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
