Let’s discuss Windows 11 Security Feature Blocking NTLM over SMB for Advanced Threat Protection. Microsoft has introduced an additional security measure in Windows 11. This allows administrators to block NTLM over SMB. This move aimed at preventing pass-the-hash, NTLM relay, and password-cracking attacks.
This update will change how Windows SPNEGO (SPNEGO is a security protocol that uses a GSS-API authentication mechanism)manages authentication discussions with destination servers. It will move away from the previous method that included Kerberos and NTLM (which encompasses LM, NTLM, and NTLMv2).
In the new Windows 11 Insider Preview Build 25951 (Canary), the SMB client can now stop NTLM for connections going out to remote servers. The new option lets an administrator stop Windows from using NTLM over SMB.
If a user or program accidentally sends NTLM information to a bad server, the attacker cannot use it to break into the system. This makes things safer for companies without completely turning off NTLM in the operating system.
We have an article highlighting the New Security Features for Windows 11. Microsoft is always working to make Windows more secure right from the start. Windows 11 helps organizations meet the new security challenges of the hybrid workplace, now and in the future.
- 5 Latest Features of Windows 11 Announced – July 2023 Dev and Canary Channel Updates
- Best Antivirus for Windows 11 Microsoft Defender | App Browser Protection | Firewall Protection
- Windows 10 Security Enhancements and Security Survey
What is the New Security Feature in Windows 11?

The new security feature in Windows 11 is the ability to block NTLM over SMB (Server Message Block) protocol. This helps you to provide advanced threat protection by preventing certain types of cyberattacks.
How Does this Security Feature Work?
It helps prevent Windows from using NTLM when connecting to remote servers via SMB. This also helps you to stop attackers from exploiting NTLM-based vulnerabilities.
What kind of Attacks Does this Feature Defend Against?
It defends against pass-the-hash attacks, NTLM relay exploits, and password-cracking attempts, which could potentially compromise system security.
Windows 11 Security Feature Blocking NTLM over SMB for Advanced Threat Protection
When someone tries to access an SMB share, their computer sends a response that includes a secret code derived from their password. This code can be intercepted by the server hosting the share. If the code is decrypted, it reveals the actual password or can be exploited in other attacks.
- This new feature allows an admin to block outbound NTLM over SMB.
- It prevents a user’s hashed password from being sent to a remote server.
- It effectively prevents these types of attacks.
- It’s an important security measure to keep user passwords safe.
Note! – This configuration does not impact the utilization of loopback SMB NTLM, such as when mapping a drive locally on a device that employs a local account.

Configuring SMB NTLM Blocking with Group Policy and PowerShell
You have the flexibility to set up this feature using Group Policy and PowerShell. You can instantly stop NTLM SMB connections when needed using the “NET USE” command and PowerShell.
Configuring SMB NTLM Blocking using Group Policy
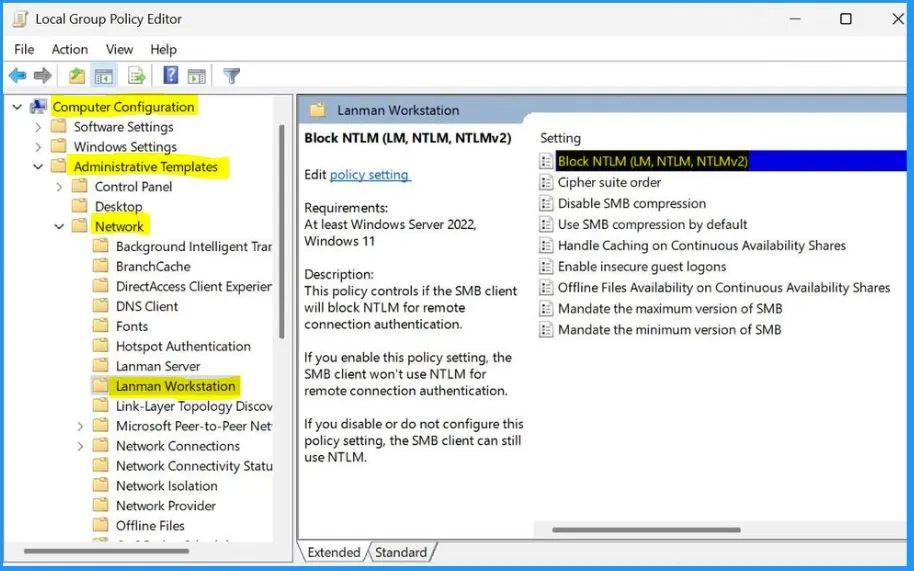
Enable some features in Group Policy settings to set up SMB NTLM blocking for the entire Windows machine. Block NTLM (LM, NTLM, NTLMv2) is the policy that controls if the SMB client will block NTLM for remote connection authentication.
- Navigate to the Group Policy settings by right-clicking from the Start menu and selecting the Run option or pressing Windows Key + R; this keyboard shortcut opens the Run dialogue box.
- Go to Computer Configuration > Administrative Templates > Network
- Within the Network section, find and select “Lanman Workstation.”
- Look for the specific policy named “Block NTLM (LM, NTLM, NTLMv2)” within the “Lanman Workstation” settings.
- Enable this policy to activate SMB NTLM blocking for enhanced security on the Windows machine.
- These settings will help strengthen your system’s security by preventing certain NTLM-related vulnerabilities.
| Policy Name | Enable | Disable | Requirements |
|---|---|---|---|
| Block NTLM (LM, NTLM, NTLMv2) | If you Enable this policy setting, the SMB client won’t use NTLM for remote connection authentication. | If you Disable or do not configure this policy setting, the SMB client can still use NTLM. | At least Windows Server 2022 Windows 11 |
Blocking NTLM over SMB in Windows 11
This new feature in Windows 11 allows administrators to stop Windows from using NTLM over SMB. This will no longer work if an attacker tries getting a user or application to send NTLM information to a bad server. This means they would be able to guess or steal passwords. It’s an extra layer of protection that doesn’t require turning off NTLM completely in the system.
- Starting with Windows 11 Insider Preview Build 25951, administrators can set up Windows to prevent sending NTLM information over SMB when connecting to remote servers.
- They can do this using Group Policy and PowerShell.
- They can also completely disable NTLM usage in SMB connections if needed using NET USE and PowerShell.
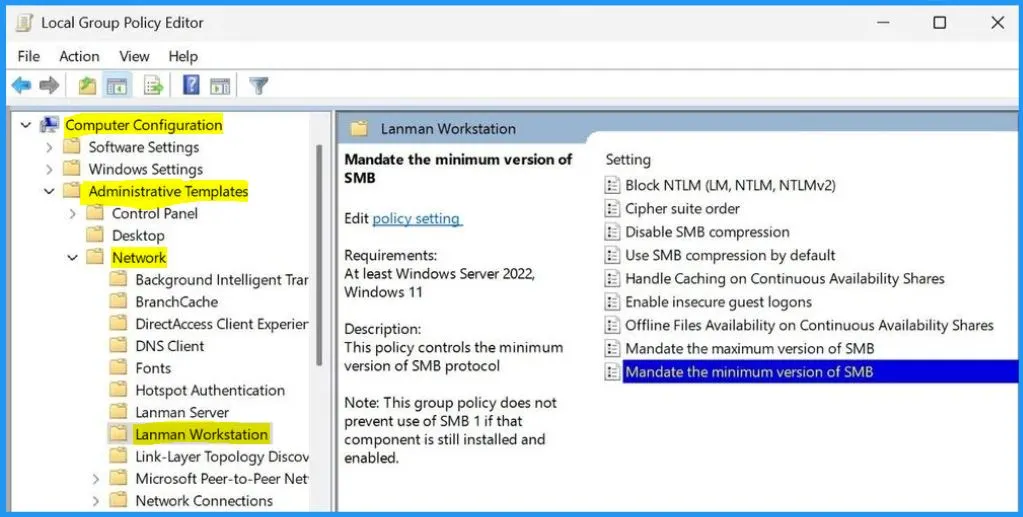
Mandate the Minimum Version of SMB
Mandate the Minimum Version of SMB policy helps you to control the minimum version of SMB protocol. This group policy does not prevent using SMB 1 if that component is still installed and enabled. The requirement of this policy is at least Windows Server 2022 Windows 11.
- Computer Configuration > Administrative Templates > Network > Lanman Workstation > Mandate the minimum version of SMB
Implementing SMB Signing for Attack Prevention
SMB signing requirement implemented in Windows 11 Insider Preview Build 25381 to enhance security. By default, SMB signing, or security signatures, is now mandatory for all connections. This measure serves as a defence against NTLM relay attacks, a malicious tactic used to gain control over a Windows domain.
- SMB signing verifies the identities of the sender and receiver through embedded signatures and hashes in each message.
- Available since Windows 98 and 2000, SMB signing has been updated in Windows 11 and Windows Server 2022 for improved protection and faster data encryption.
- In April 2022, Microsoft announced the final phase of disabling the outdated SMB1 file-sharing protocol for Windows 11 Home Insiders.
Configuring SMB NTLM Blocking for the Entire Windows Machine Using PowerShell
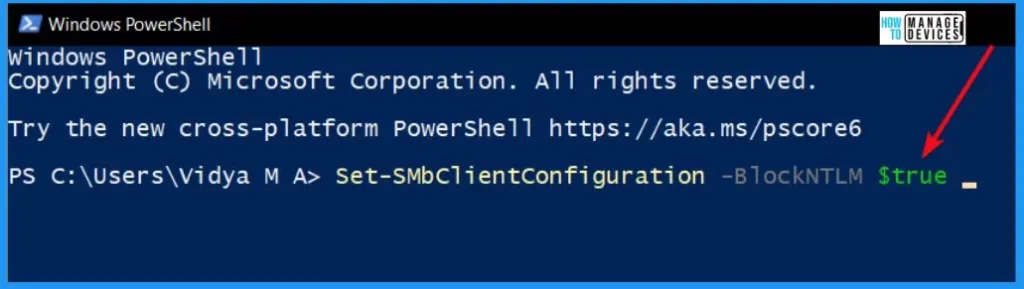
You can easily configure SMB NTLM blocking for the entire Windows machine with PowerShell. The syntax below helps you configure SMB NTLM blocking for the Windows machine with PowerShell. Open PowerShell and use the below-given syntax below.
- Once completed, the entire Windows machine will have SMB NTLM blocking enabled, providing an additional layer of security against potential attacks.
Set-SMbClientConfiguration -BlockNTLM $true
Configuring SMB NTLM Blocking with NET USE
You can easily use the NET USE command to Configuring SMB NTLM Blocking. The below syntax helps you to Configure SMB NTLM Blocking with NET USE.
NET USE \server\share /BLOCKNTLM
Configuring SMB NTLM Blocking with New-SmbMapping in PowerShell
When using the New-SmbMapping cmdlet in PowerShell to map a drive, you can specify SMB NTLM blocking with the following syntax.
New-SmbMapping -RemotePath \server\share -BlockNTLM $true
Resolving Issues with SMB NTLM Blocking
When you connect to computers part of the Active Directory using SMB with a domain user account, it’s supposed to use Kerberos for authentication. Blocking another method called NTLM shouldn’t cause any problems in this situation.
But if you are trying to use Kerberos and having trouble connecting, this section guides you through the troubleshooting process. It will help you determine why you are having difficulty connecting even though NTLM is blocked.
These potential error codes may appear when NTLM blocking hinders a connection.
- Error Code 67
- Hexadecimal Code: 0x43
- Error Message: ERROR_BAD_NET_NAME
- Description: The network name cannot be found
| Expected Scenarios for NTLM Usage |
|---|
| The client connects using an IP address |
| The Kerberos CIFS Service Principal Name is missing in AD for the SMB server. |
| The credential used for the SMB server is a local user account. |
Author
About the Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.
