Let’s discuss the Windows LAPs Smart-Card-only Policy Integration. Windows Local Administrator Password Solution (LAPS) is a tool for managing local administrator passwords on Windows machines.
A new feature has been added to LAPS in Windows Labs, integrating it with the smart card-only authentication policy. Integrating Windows LAPS with the smart-card-only policy is a security enhancement for devices with LAPS enabled. This feature adds an extra layer of protection to your Windows computers.
When someone tries to access the local administrator password on a computer, they need the usual credentials and a smart card. This makes it much harder for unauthorized users to get control of the local admin password, boosting the overall security of your Windows devices.
The latest feature in Windows Local Administrator Password Solution (LAPS) makes it simple to manage your LAPS-managed account, even in special situations like WinRE (Windows Recovery Environment) or Safe Mode.
- Windows LAPs Automatic Account Management
- Windows LAPS Configurations from Azure AD and Intune
- New Built-in LAPs Client for Windows 11 and 10 | Conflict with Old Version of LAPs
Why Does Windows LAPS Care about the Smart Card-only Authentication Policy?

Windows LAPS cares about the smart card-only authentication policy because it provides an additional layer of security to local administrator accounts. The smart card-only authentication policy requires users to use a physical smart card and regular credentials like a password to access certain accounts or features.
Windows LAPs Smart-Card-only Policy Integration
Discuss the “Interactive logon requires Windows Hello for Business or smart card” feature. When this is enabled, the system will only allow logins using certificate-based methods, like Windows Hello for Business or a smart card, and it blocks other logon types that don’t use these secure methods.
Enabling this feature in the past would cause problems with Windows LAPS. If you tried to log in with the built-in admin account, you would be allowed to log in but immediately prompted to change your password. For non-built-in accounts, enabling this policy would encourage you to change your password during login. However, changing the password would fail because Windows LAPS prevents others from changing local account passwords.
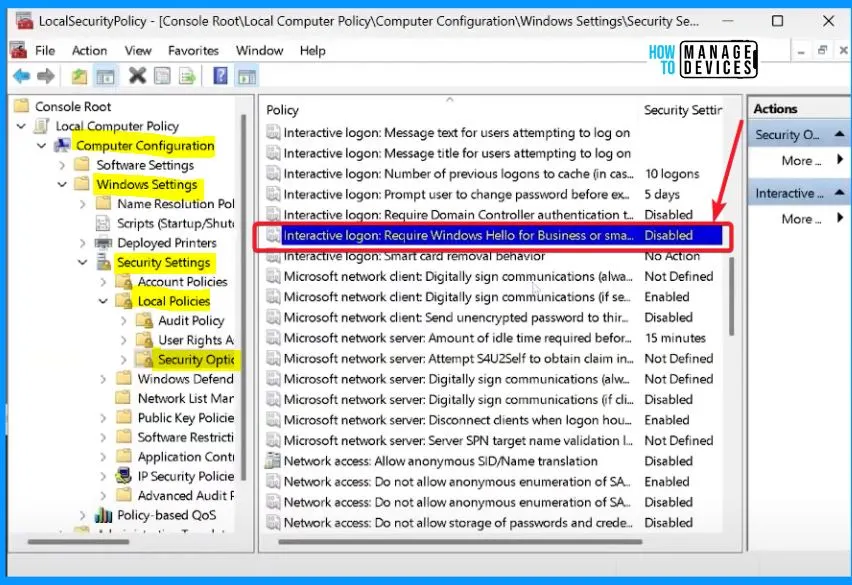
This is a significant security improvement for preventing password-based logins, but it posed challenges for tools like Windows LAPS. The issue is that Windows LAPS manages local account passwords and currently only supports password-based logins for local accounts.
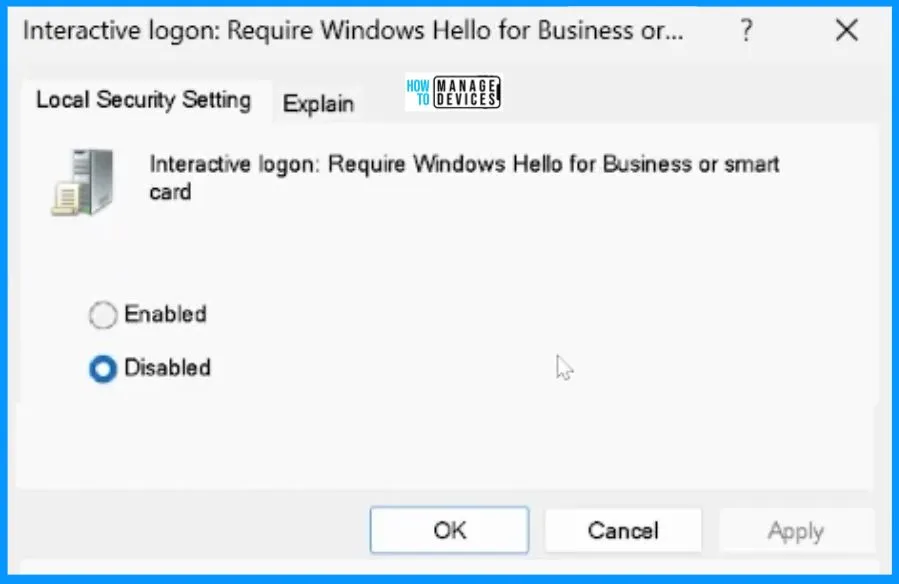
The setup does not rely on the default built-in administrator account. Instead, it has two local accounts: the LAPS admin account and the local admin account you can use for comparison.
The LAPS admin account is the one managed by Windows LAPS. This means LAPS takes care of changing and securing the password for this account automatically.
On the other hand, the local admin account is just a random account. You can easily use it to see and understand the differences in behaviour compared to the LAPS-managed account. This helps us observe and analyze how LAPS affects the management of passwords for these local accounts.
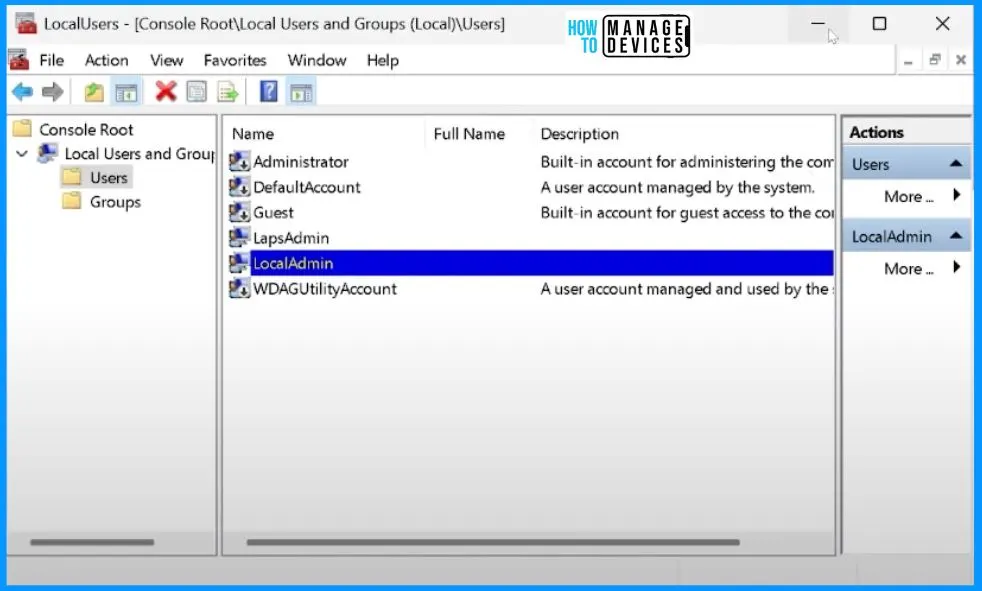
This policy configures post-authentication actions, which will be executed after detecting an authentication by the managed account. Grace period: specifies the time (in hours) to wait after an authentication before performing the specified post-authentication actions.
- If this setting is enabled and more significant than zero, the specified post-authentication actions will be executed upon expiration of the grace period.
- If this setting is disabled or not configured, the specified post-authentication actions will be executed after a default 24-hour grace period.
- If this setting equals zero, no post-authentication actions will be executed.
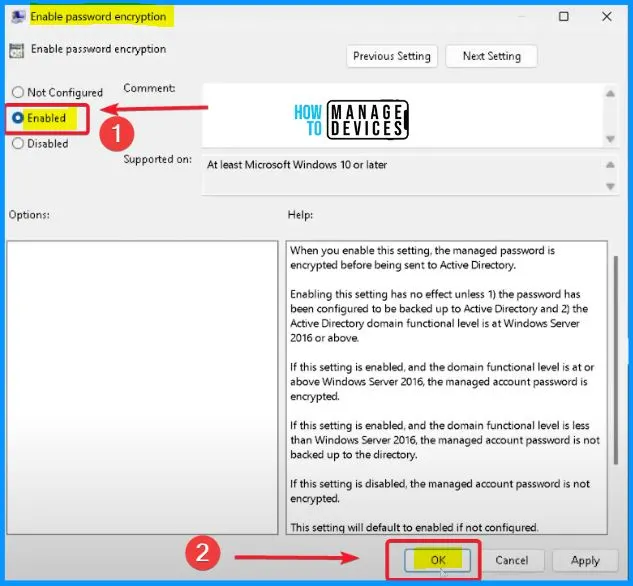
Enable Password Encryption
When you enable this setting, the managed password is encrypted before being sent to Active Directory. Enabling this setting has no effect unless 1) the password has been configured to be backed up to Active Directory and 2) the Active Directory domain functional level is at Windows Server 2016 or above.
- The managed account password is encrypted if this setting is enabled and the domain functional level is at or above Windows Server 2016.
- If this setting is enabled, and the domain functional level is less than Windows Server 2016, the managed account password is not backed up to the directory.
- If this setting is disabled, the managed account password is not encrypted.
- This setting will default to enabled if not configured.
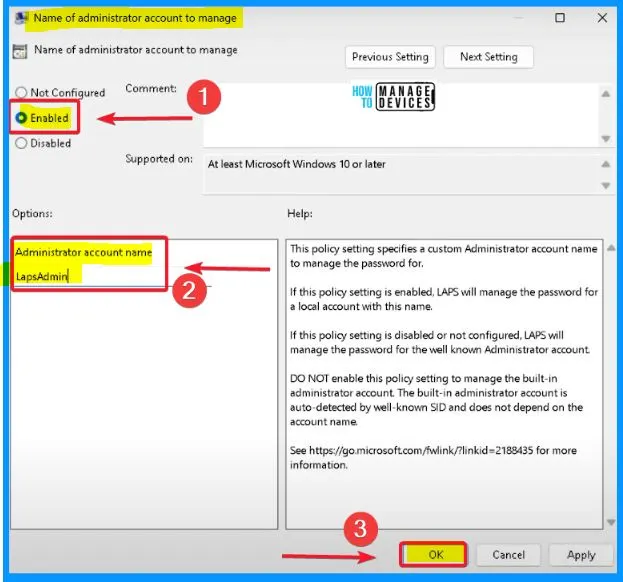
Name of Administrator Account to Manage
This policy setting specifies a custom Administrator account name to manage the password. LAPS will work the password for a local account with this name if this policy setting is enabled. If this policy setting is disabled or not configured, LAPS will manage the password for the well-known Administrator account.
- DO NOT enable this policy setting to manage the built-in administrator account. The built-in administrator account is auto-detected by a well-known SID and does not depend on the account name.
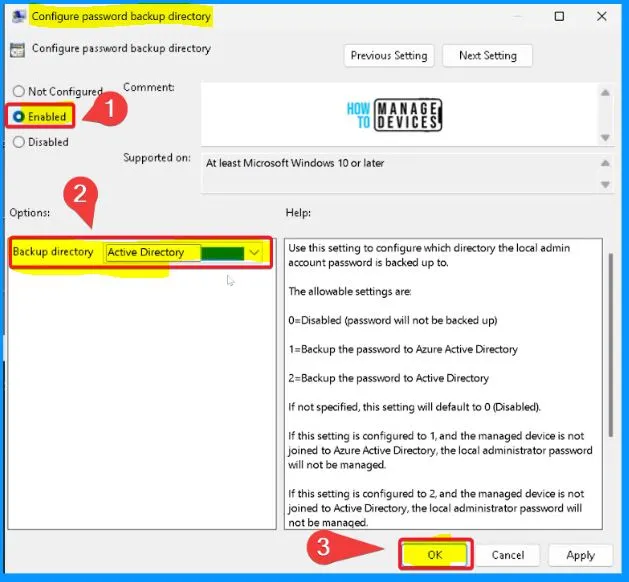
Configure Password Backup Directory
Use this setting to configure which directory the local admin account password is backed up. The allowable settings are as follows.
- 0=Disabled (password will not be backed up)
- 1=Backup the password to Azure Active Directory
- 2=Backup the password to Active Directory
| Configure Password Backup Directory |
|---|
| If not specified, this setting will default to 0 (Disabled). |
| If this setting is configured to 1, and the managed device is not joined to Azure Active Directory, the local administrator password will not be managed. |
| If this setting is configured to 2, and the managed device is not joined to Active Directory, the local administrator password will not be managed. |
It is essential to ensure that the LAPS is up to date and then retrieve the latest password stored in Active Directory, including the clear text version, for easy access.
Invoke-LapsPolicyProcessing
Get-LapsADPassword -Identity lapsDemoclient -AsplainText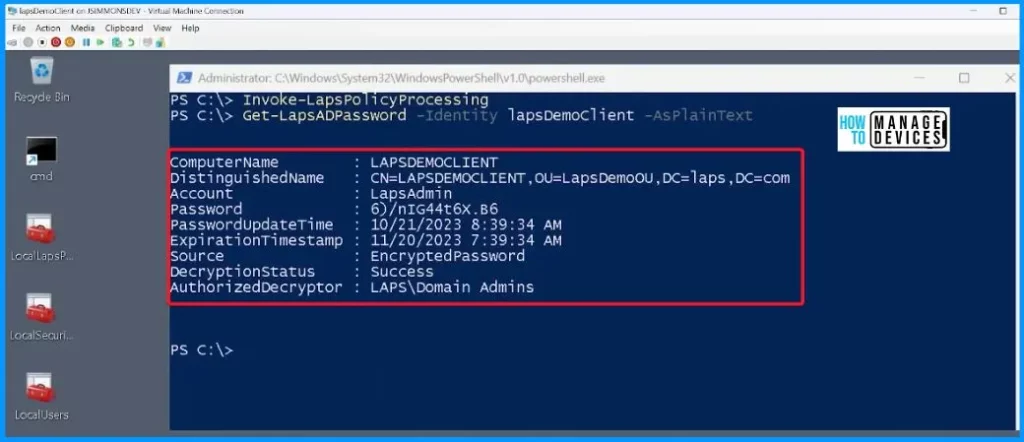
How to Run Commands as Different Accounts
Before implementing the smart card-only policy, let’s learn how to run commands as different accounts, using both the local and LAPS admin accounts. Firstly, you should run a command window as the local admin account, which is visible in the current session.
It would be best to do the same for the LAPS admin account, copying and pasting the password from the PowerShell window. Essentially, now you have a command window open and are operating within it as the LAPS admin account.
When you use the command “runas.exe /u: LocalAdmin cmd.exe“, it prompts you to enter the LocalAdmin password. Once you enter the password, the result will show as “Attempting to start cmd.exe as user ‘LAPSDEMOCLIENT\LocalAdmin’.”
runas.exe /u: LocalAdmin cmd.exe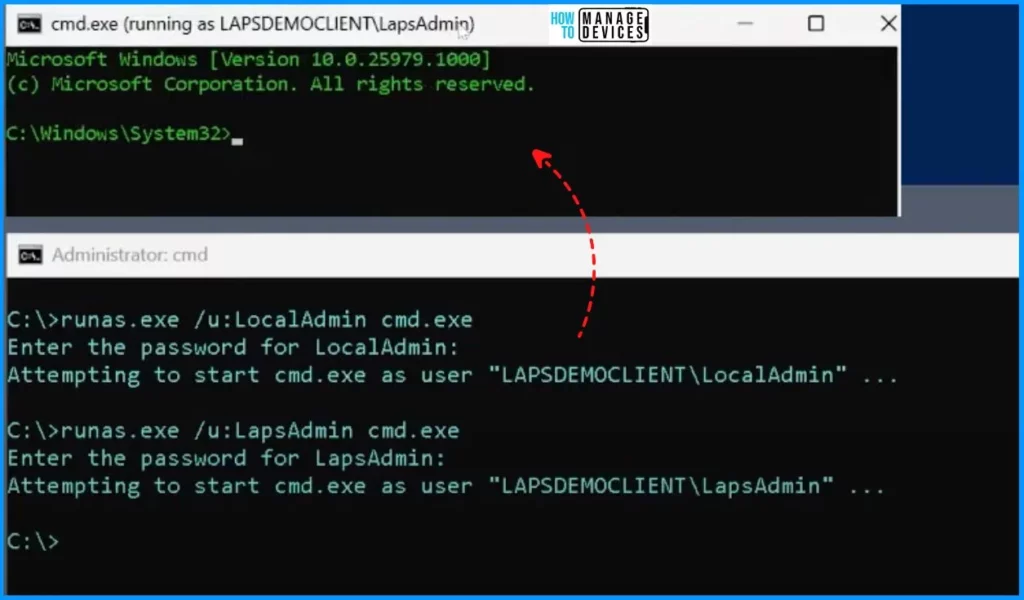
Now, let’s go back to that security policy and enable the smart card-only policy, and then let’s rerun those tests. After making this change, let’s rerun the tests. Firstly, you should test the local admin account, and you can see it failed. We can not log in with that account because the policy requires smart card authentication, and we used a password-based login.
On the other hand, the non-Windows LAPS-managed account is blocked due to the smart card-only policy. However, the Windows LAPS-managed account is exempted from this policy, allowing it to log in without a smart card and providing an exception to the rule.
When you use the command “runas.exe /u: LapsAdmin cmd.exe,” it prompts you to enter the LapsAdmin password. Once you enter the password, the result will show as “Attempting to start cmd.exe as user “LAPSDEMOCLIENT\LapsAdmin.”
runas.exe /u: LapsAdmin cmd.exe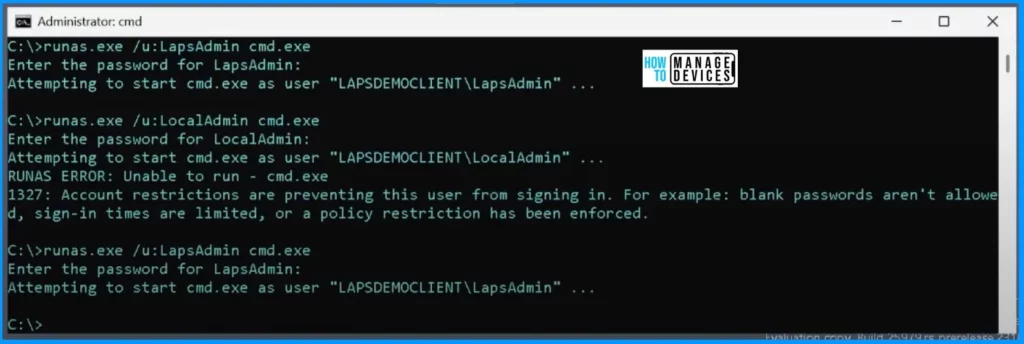
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
About the Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.

Insightful article! The integration of Windows LAPS with the Smart Card Only Policy is defined brilliantly. Clear and concise explanations. Great job!