Exciting News! New Built-in LAPs Client for Windows 11 and 10. You no longer have to install the LAP MSI client on Windows devices because LAPs is an Inbox feature. This feature was shared on April 12, 2023, via YouTube Short. The latest information on Intune and Azure AD policy configurations for Windows LAPS is explained in the following post. More details Windows LAPS Configurations From Azure AD and Intune.
Windows LAPS is a superior solution for safeguarding your local admin passwords. There are some issues related to the conflict between built-in LAPs clients and legacy LAPs clients, also discussed in this post. The latest LAPS capabilities are now available on your devices, shared by Jay Simmonson in the Techcommunity post referred to in the below section of this post.
There are some requirements for the new LAPs enhancements and new group policies, such as domain functional level to Server 2016 for AD Schema extension. Windows LAPS is available for Cloud and on-premises environments, providing greater flexibility and convenience.
Windows LAPS manages the password of a specified local administrator account by regularly rotating the password and backing it up to Active Directory (AD). LAPS has proven to be an essential and robust building block for AD enterprise security on premises.
- Setup New Windows LAPs Using Intune Policies
- Windows LAPS Role Based Access Controls Using Intune
- Windows LAPS Configurations from Azure AD and Intune
- Microsoft Intune 2304 April Update Windows LAPS Management
- New Built-in LAPs Client for Windows 11 and 10 | Conflict with Old Version of LAPs
- Azure AD LAPs Group Policy Settings for Windows 11 | Intune Policy for LAPs
- OLD LAPS for Windows 10 11 Privileged Access Management
What is LAPS?
LAPS is a Microsoft security product that IT pros have widely used for nearly a decade to secure Windows devices, aid in device recovery, and support helpdesk scenarios. Now Microsoft is modernizing and improving this technology. LAPS is available to Windows 10, 11, and Windows Server 2019 or 2022.
Do you need to Extend the AD Schema for Hybrid Scenario?
Yes, you need to extend the AD schema for Hybrid scenarios. But if you are only looking to support Azure AD joined scenarios, then Schema extension is not needed.
Event Logs for New Windows LAPs Client?
The following is the event log path for the new Windows LAPs Client! Applications and Services Logs – Microsoft – Windows – LAPS.
Whether the Password is stored in both Azure AD and On-Prem Active Directory?
Password is only stored in only one directory at a time, not both!
Are there any known issues with New Windows LAPS clients Vs Legacy Clients?

Microsoft confirmed that they have verified a reported legacy LAPS interop bug in the above April 11, 2023 update. If you install the legacy LAPS GPO CSE on a machine patched with the April 11, 2023 security update and an applied legacy LAPS policy, both Windows LAPS and legacy LAPS will break. Symptoms include Windows LAPS event log IDs 10031 and 10032, as well as legacy LAPS event ID 6. Microsoft is working on a fix for this issue. You can work around this issue by either: a) uninstalling legacy LAPS, or b) deleting all registry values under the HKLM\Software\Microsoft\Windows\CurrentVersion\LAPS\State registry key.
New Built-in LAPs Client for Windows 11 and 10
New LAPS capabilities are coming directly to your devices starting with April 11, 2023, security update. With the release of April 11, 2023, security update, users of the following Windows editions can take advantage of these new features.
- Windows 11 Pro, EDU, and Enterprise
- Windows 10 Pro, EDU, and Enterprise
- Windows Server 2022 and Windows Server Core 2022
- Windows Server 2019
Note! – The LAPS Client installation using Microsoft Intune. Since the Client is part Windows Operating system (April 2023 LCU or later) as an Inbox application, you don’t need to install any client separately.
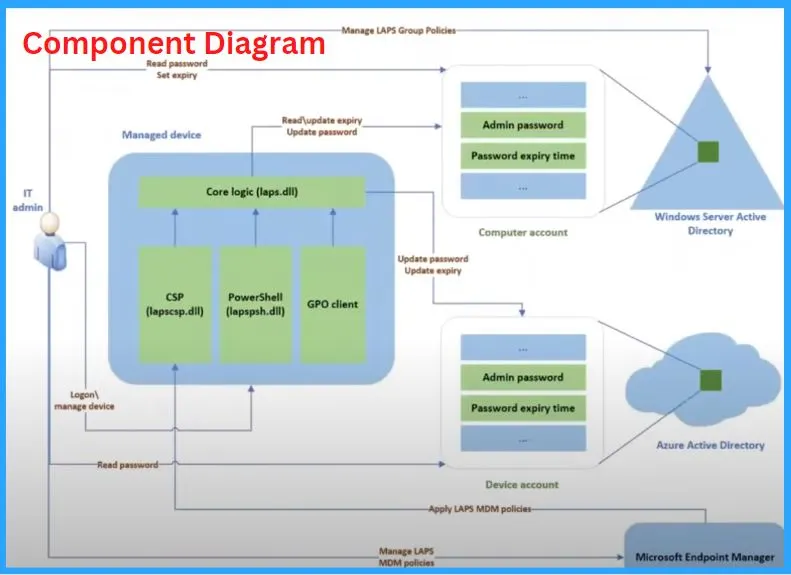
The conflict between Legacy and New LAPs Client after April LCU Patching
I thought of discussing the conflict between Legacy and New LAPs Client after April LCU Patching. Microsoft added the new built-in LAPs client to Windows 10 and Windows 11 devices as part of April LCUs, and this is causing issues for many organizations that are already using LAPs solutions.
Microsoft’s response on this issue via Twitter is “UPDATE: This only occurs when the legacy MSI is installed on top of April updates AND an existing legacy LAPS policy. We’ve figured out why this happens & are looking at a permanent fix.”
Workaround shared by Microsoft is given below:
- Don’t install Legacy LAPS MSI after installing April updates, OR
- Delete all values under the following reg key on machines with the issue:
- HKLM\Software\Microsoft\Windows\CurrentVersion\LAPS\State
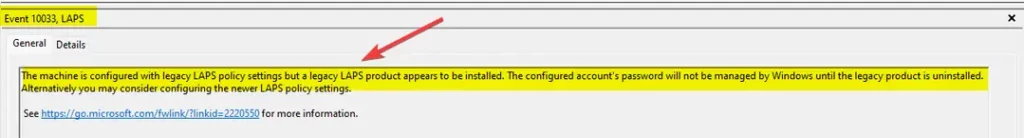
Event ID 10033, LAPS – The machine is configured with legacy LAPS policy settings, but legacy LAPS product appears to be installed. The configured account’s password will not be managed by Windows until the legacy product is uninstalled. Alternatively, you may consider configuring the newer LAPS policy settings.
Event 10031, LAPS – LAPS blocked an external request that tried to modify the password of the current manager account.
The New Windows LAPS Feature
Windows LAPS is a huge improvement in virtually every area beyond Legacy LAPS. Let’s discuss some exciting new capabilities in this latest Windows LAPS feature.
- Natively integrated into Windows
- LAPS supports Azure Active Directory (in private preview)
- New capabilities for on-premises Active Directory scenarios
- New features for both Azure AD and on-premises AD scenarios
1. Natively Integrated into Windows
LAPS is now natively integrated into Windows! This integration allows users to use LAPS directly from their Windows devices without additional software or downloads. This marks a significant milestone in our ongoing efforts to provide our customers with seamless and easy-to-use solutions for password management.
- With LAPS now natively integrated into Windows, users can enjoy a more streamlined and efficient experience managing their local administrator passwords.
2. LAPS Supports Azure Active Directory (in private preview)
LAPS supports Azure Active Directory, opening up new possibilities for password management and security in the Cloud. With LAPS support for Azure Active Directory, users can benefit from enhanced security features and greater control over their local administrator passwords.
This integration enables users to centrally manage their local administrator passwords in the Cloud, providing increased flexibility and ease of use. This integration will help us better serve our customers and provide them with the tools they need to keep their systems secure and protected against unauthorized access.
In combination with Azure AD, LAPS delivers various benefits for managing passwords in the Cloud. The benefits are as follows.
- Retrieves stored passwords via Microsoft Graph.
- Creates two new Microsoft Graph permissions for retrieving only the password “metadata” (i.e., for security monitoring apps) or the sensitive cleartext password itself.
- Provides Azure role-based access control (Azure RBAC) policies for authoring authorization policies for password retrieval.
- Includes Azure management portal support for retrieving and rotating passwords.
- It helps you manage the feature via Intune
- Automatically rotates the password after the account is used
3. New Capabilities for On-Premises Active Directory Scenarios
Let’s learn about the New Capabilities for On-Premises Active Directory Scenarios. What couldn’t previously do with legacy LAPS, now available on-premises?
| New Capabilities for On-Premises Active Directory Scenarios | Features Used to |
|---|---|
| Password encryption | It gives you the ability to log back into restored backup images |
| Password history | It helps keep your domain controllers secure by rotating these critical recovery passwords on a regular basis |
| Directory Services Restore Mode (DSRM) password backups | It helps keep your domain controllers secure by rotating these critical recovery passwords regularly |
| Emulation mode | Useful if you want to continue using the older LAPS policy settings and tools while preparing to migrate to the new features |
| Automatic rotation | Automatically rotate the password after the account is used |
New Features for Both Azure AD and On-premises AD Scenarios
The new features for Azure AD and on-premises AD scenarios are Rich policy management, Rotating the Windows LAPS account password on demand from Intune portal, a Dedicated event log, a New PowerShell module, and Hybrid-joined.
The LAPS scenario in Azure AD, now integrated into Microsoft Entra, is set to transition from a private preview to a public preview later this quarter. The below table shows the new features of LAPS for the Azure Active Directory
| New Features of LAPS for the Azure Active Directory |
|---|
| Store passwords in Azure (on Azure device object) |
| On-demand password rotation from Microsoft Endpoint Manager portal |
| Password retrieved via Microsoft Graph |
| Passwords retrieval via Azure portal |
| Settings configuration via Microsoft Endpoint Manager portal |
| On-demand password rotation from the Microsoft Endpoint Manager portal |
| On-demand password rotation from the Microsoft Endpoint Manager portal |
1. Rich Policy Management
Rich policy management is now available in Group Policy and Configuration Service Provider (CSP). It is an important feature in Local Administrator Password Solution.
- Group Policy: %windir%/PolicyDefinitions/LAPS.admx
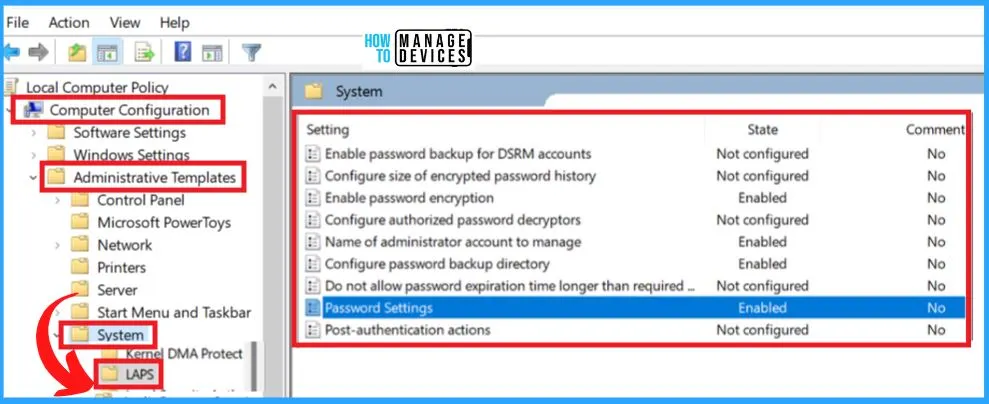
A configuration service provider (CSP) is a component of Windows client operating systems that helps you show IT professionals device configuration choices. There are a lot of LAPs CSP policies that are already available. It also allows them to apply the settings across multiple Windows OSes.
- CSP: ./Device/Vendor/MSFT/LAPS
Intune LAPs policies
The latest information on Intune and Azure AD policy configurations for Windows LAPS is explained in the following post. More details Windows LAPS Configurations From Azure AD and Intune.
- Intune Settings Catalog LAPs policies are explained in this post – Azure AD LAPs Group Policy Settings For Windows 11 | Intune Policy for LAPs.
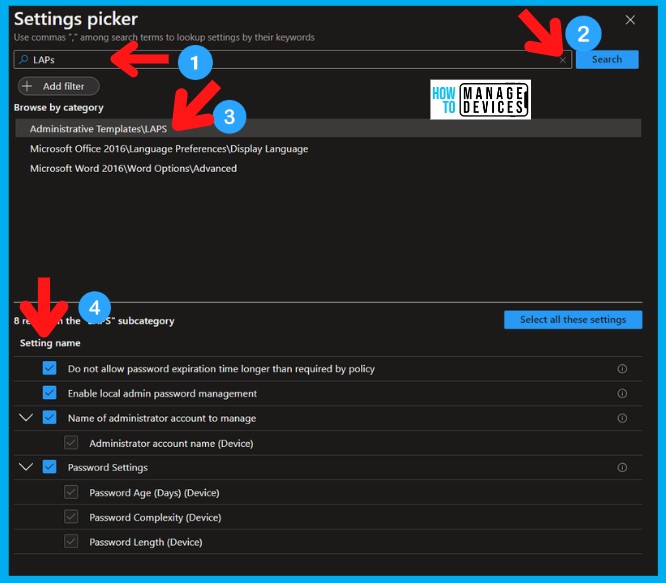
On the Settings Picker windows, use the search box and type LAPs, and click Search. Select the Administrative Templates\LAPs category and double-click on the category to see the settings name.
- Do not allow password expiration time longer than required by policy
- Enable local admin password management
- Name of administrator account to manage
- Administrator account name (Device)
- Password Settings
- Password Age (Days) (Device)
- Password Complexity (Device)
- Password Length (Device)
2. Rotating the Windows LAPS Account Password on Demand from Intune Portal
Rotating the Windows LAPS account password on demand from Intune portal is another important feature. Rotating the Windows LAPS account password on demand from Intune portal is very useful when, for example, handling a possible breach issue.
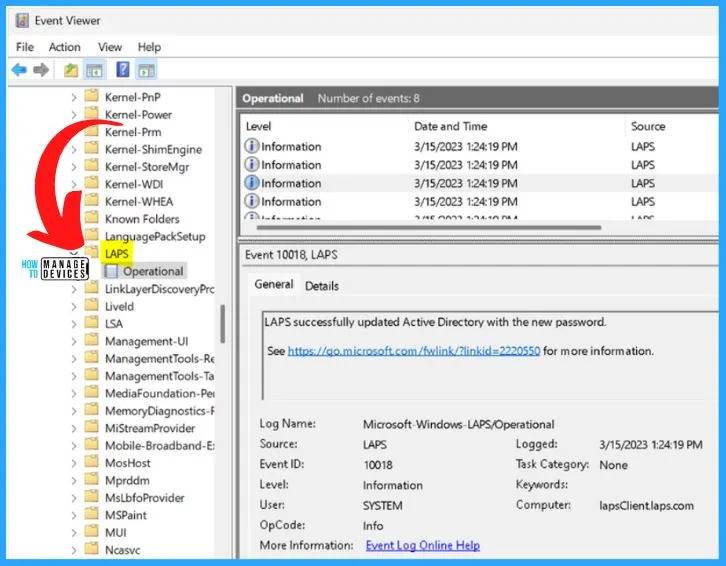
3. Dedicated Event Log
The dedicated event log is located under Applications and Services. The path of the Dedicated event log is Logs > Microsoft > Windows > LAPS > Operational for improved diagnostics.
4. New PowerShell Module
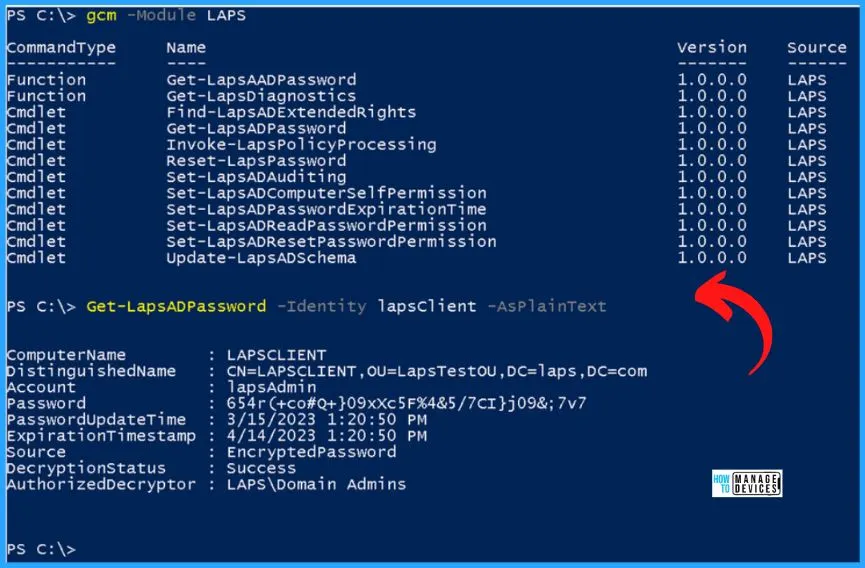
The New PowerShell module includes improved management capabilities. For example, you can now rotate the password on demand using the new Reset-LapsPassword cmdlet!
GCM -Module LAPS
| CommandType | LAPS CommandLets Name |
|---|---|
| Function | Get-LapsAADPassword |
| Function | Get-LapsDiagnostics |
| Cmdlet | Find-LapsADExtendedRights |
| Cmdlet | Get-LapsADPassword |
| Cmdlet | Invoke-LapsPolicyProcessing |
| Cmdlet | Reset-LapsPassword |
| Cmdlet | Set-LapsADAuditing |
| Cmdlet | Set-LapsADComputerSelfPermission |
| Cmdlet | Set-LapsADPasswordExpirationTime |
| Cmdlet | Set-LapsADReadPasswordPermission |
| Cmdlet | Set-LapsADResetPasswordPermission |
| Cmdlet | Update-LapsADSchema |
5. Hybrid-Joined
Hybrid Azure AD joined devices require network line of sight to your on-premises domain controllers periodically. The Hybrid-joined devices are fully supported.
How to Use LAPS Right Now to Manage Your Local Administrator Passwords
Microsoft highly recommends that you begin using the new Windows LAPS feature immediately. With the release of the April 11, 2023 security update, you can take advantage of the latest LAPS capabilities in your existing deployment.
- You may consider getting started by leveraging the new emulation mode and then migrating over to the new features in a phased manner.
- Or you can jump into the new features right away. Microsoft will let you know when the LAPS scenario in Azure AD will shift from private to public preview later this quarter.
- We strongly advise you to adopt the latest features of LAPS to take advantage of the new security improvements.
- By doing so, you can significantly increase the security of your sensitive passwords, especially when stored in Active Directory with encryption enabled or in Azure AD.
- The Additional testing on more machines has shown the behavior such as
- If Legacy LAPS pre-existed, new LAPS is just dormant with Legacy policies.
- It seems ok if Windows is a fresh install and gets Legacy policy.
- If Legacy LAPS is THEN installed after, we have breakage.
Learn more about LAPS or want to catch up on the LAPS story; watch the Managing local admin account passwords in AD and Azure AD Video presented by Jay Simmons a Software Engineer at Microsoft.
LAPS for Windows 10 11 AAD joined devices – Goals of the New Version of LAPS
There will no longer be a need to install a separate MSI package moving it into the operating system has a lot of advantages it normalizes the patching capability. So rather than relying upon customers doing periodic updates or patches, Microsoft can now do that via the normal Windows update channels.
It also helps normalize the support channels if we need support situations. Adding support for backing passwords up to Azure is the big goal of a new version of LAPS.
Microsoft adds some new features. Part of the Azure move is that Microsoft is modernizing the policy management experience for LABS. Now. This means that you will be able to manage the LAB’s policy settings from the Cloud.
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.

When i go to my Intune and configure a new device policy and go to the settings picker and enter in “LAPS” i do not get any options like you show in your image
I have noticed that the search is not working for LAPs, but if you browse through the Administrative Templates\LAPs category, it will show up.
I have noticed that the search is not working for LAPs, but if you browse through the Administrative Templates\LAPs category, it will show up.
Hi Vidya,
Can you guys create a new post for disk cleanup using Proactive Remediations?
Question: When disk space of less than 20% is detected, A Disk cleanup should be used as remediation.
I really appreciate your help on this.
Many Thanks,
Niranjan
Do you need to extend the AD schema for native AD (not hybrid) for Windows LAPs if already running the legacy version?
My other question is in emulation mode any 2012 OS machines would keep the client installed in order to work?
Thanks in advance!
ok which is old and which is new to create the policy I have configuration profiles and setup that way with machine being in the specific group. Is that the old way with intune or the new way – only so I can check which way I’m going..