Microsoft Local Administrator Password Solution (LAPS) is part of a larger credential theft mitigation and monitoring strategy, but it’s also an important pillar in your credential threat mitigation strategy.
LAPS provides centralized storage of local admin account passwords in Active Directory without additional servers. LAPS for Windows 10 devices.
LAPS is a solution that provides secure administrative passwords for each managed computer. The password is stored in a protected Active Directory attribute and a timestamp.
When the password exceeds the configured limit, the managed computer will reset it, and the corresponding AD attribute will be updated accordingly. This ensures that the administrative passwords remain secure and up-to-date at all times.
The LAPS 6.2 was released recently, 3/4/2022, and many enhanced features are available in this solution.
- Setup New Windows LAPs Using Intune Policies
- Windows LAPS Role-Based Access Controls Using Intune
- Windows LAPS Configurations from Azure AD and Intune
- Microsoft Intune 2304 April Update Windows LAPS Management
- New Built-in LAPs Client for Windows 11 and 10 | Conflict with Old Version of LAPs
- Azure AD LAPs Group Policy Settings for Windows 11 | Intune Policy for LAPs
- OLD LAPS for Windows 10 11 Privileged Access Management
Need for LAPS in Windows 10 11 Management?
Microsoft LAPS is a stepping stone towards securing Windows 10 11 devices. This solution should be part of the Privileged Access Management architecture.
The LAPS tools allow local admin password management to be automated for all Windows 10 11 devices.
Do we have a solution similar to LAPS for Azure AD-joined Windows 10 11 devices? Continue reading. I will discuss this in more detail in the section below: LAPS for Windows 10 11 AAD-joined devices.
LAPS aims to secure the environment by ensuring all Domains that have joined Windows 10 11 devices have different local administrator passwords to comply with the enterprise password policy.
Each domain administrator, such as the help-desk administrator, determines which users can read the passwords. Paul Klerkx shared an overview of this new version in the Microsoft Answers.
Microsoft LAPS Use Case?
The diagram below helps to understand the use case of an attack within a standardized local admin password environment. And LAPS implementation can prevent these kinds of attacks.
LAPS for Windows 10 11 devices will help you here. Other mitigation options, such as Defender ATP, are also available.
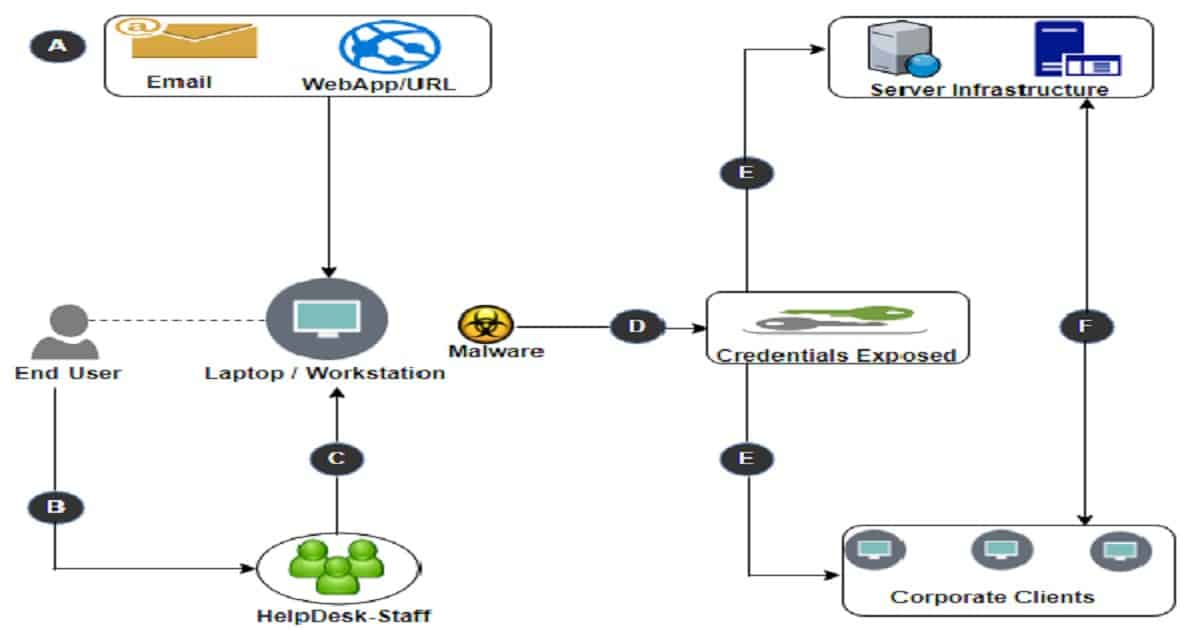
- Local user account profile infected with malware
- End-user approaches help-desk for remote assistance
- Help-Desk agent logs in using the local administrator account
- Malware obtained the credentials of the Local Administrator
- The malware starts spreading to other devices using the exact local account details
- Further malware distribution occurs with varying elevated accounts
How LAPS Helps to Rectify Windows 10 11 Security Challenges
In today’s IT security landscape, credential theft is a significant problem. Local admin password compromised in an environment often triggers targets for attackers.
Reusing valid credentials is one of the most common vulnerabilities in today’s networks. Hackers’ campaign includes Pass-the-Hash as an integral part.
Once a password is key logged or a password hash is harvested, there is little to stop an attack from spreading unabated across your entire network in a scenario where passwords are common. With ransomware and malware threats, this offers the potential for massive exposure.
LAPS (LAPS for Windows 10) takes a different approach and does not eradicate the ability to Pass the Hash. Rather, it reduces the impact of Pass-the-Hash by making each local administrator’s password unique. This effectively helps to limit the attack after a single machine is compromised.
Once the attacker gains access to a client workstation, they can no longer access every other workstation in the environment through the shared local admin account.
LAPS is designed to run in the least privileged model—there is no need to put a service account into the domain admins to manage the passwords. The password resets are done in the context of the computer/system. No additional server is required to install it, and the passwords are stored in the Active Directory.
Like many other security controls, LAPS should be part of an overall solution. Managing local administrator passwords is a great step toward controlling and reducing the broad attack surface.
Architecture – LAPS for Windows 10 11 Devices
The following diagram is the simplistic view of Microsoft LAPS architecture. Your IT admins can centrally manage the local admin passwords of all your Windows 10 11 devices.
This implementation will address most of the challenges explained in the above section. LAPS for Windows 10 11 devices will give you a more secure environment. Active Directory will store the admin password and password expiration time.
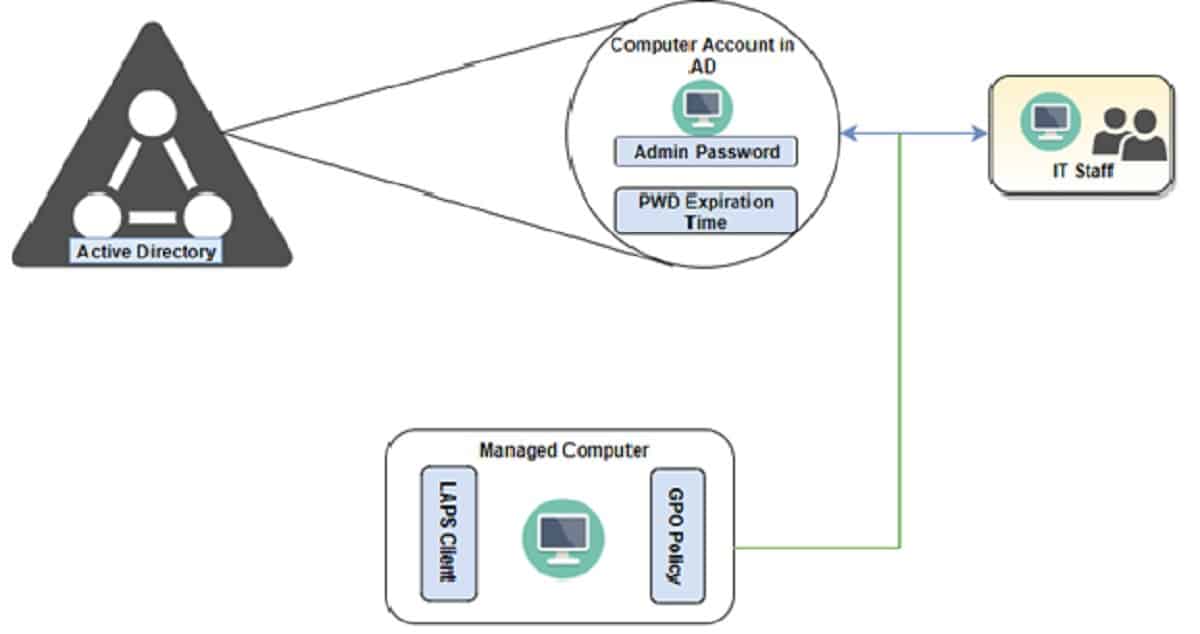
LAPS Architecture mainly includes two core design elements
- LAPS Components
- AD Infra Considerations
LAPS Components
The following list specifies all components of the solution and their responsibilities:
- LAPS Client (Client-Side Extension – CSE) component is installed on all domain-joined computers. CSE will be responsible for the following tasks:
- Management of Administrator password
- Logging activity to the Application Event Log
- IT Staff This solution contains the UI tools to retrieve passwords for IT staff:
- Simple fat client UI
- PowerShell module
Both types of UI offer the following functionality:
- Allow the user to enter the computer name
- Contact AD infrastructure in the security context of the user who runs the tool
- Show the computer name and password to the user
- Provide the user with UI to force the expiration of the password for the computer (immediate or planned for a specific time)
AD Infra Considerations
The Active Directory infrastructure will be responsible for the following tasks: It will be used as a password repository and will enforce a security and auditing model for passwords.
GPO Policy will be responsible for the following tasks: Triggering the execution of CSE on the managed computers. CSE will be triggered whenever a GPO refresh event occurs on the computer. LAPS ADMX templates ( admx and Ex-us\AdmnPwd.adml) will be used to define configuration options.
ADMX templates will be copied to the AD centralized GPO store. AD Schema Extension It is required to extend the AD schema that stores the password of a managed local Administrator account for each workstation and the timestamp of password expiration.
AD schema extension will be performed using the following PowerShell script provided by the LAPS solution:
Import-module AdmPwd.PS
Update-AdmPwdADSchema
AD Attributes Below, two attributes are added to the computer class as part of the AD schema extension
ms-Mcs-AdmPwd
ms-Mcs-AdmPwdExpirationTime
AD Delegation and Permission It is required to delegate and assign permission for Desktop admins to read/set the computer password. Desktop admins refer to themselves as security group members, which will have the extended rights holder’s permission on the OU level where computers reside.
LAPS Information Security
LAPS requires AD attributes (as mentioned above in the Architecture section) for managed custom local Administrator accounts in Active Directory.
By default, Domain administrators will have complete control over computer objects in AD to read and write local admin passwords. To prevent domain administrators from reading the LAPS password, “All extended rights” must be removed.
- Computers are joined to the domain using a service account configured in the SCCM task sequence; hence, standard users will not have permission to use ‘All Extended Rights’.
- When transferred over the network, both password and timestamp are encrypted by Kerberos encryption.
- When stored in AD, both password and timestamp are stored in cleartext.
LAPS Process Flow
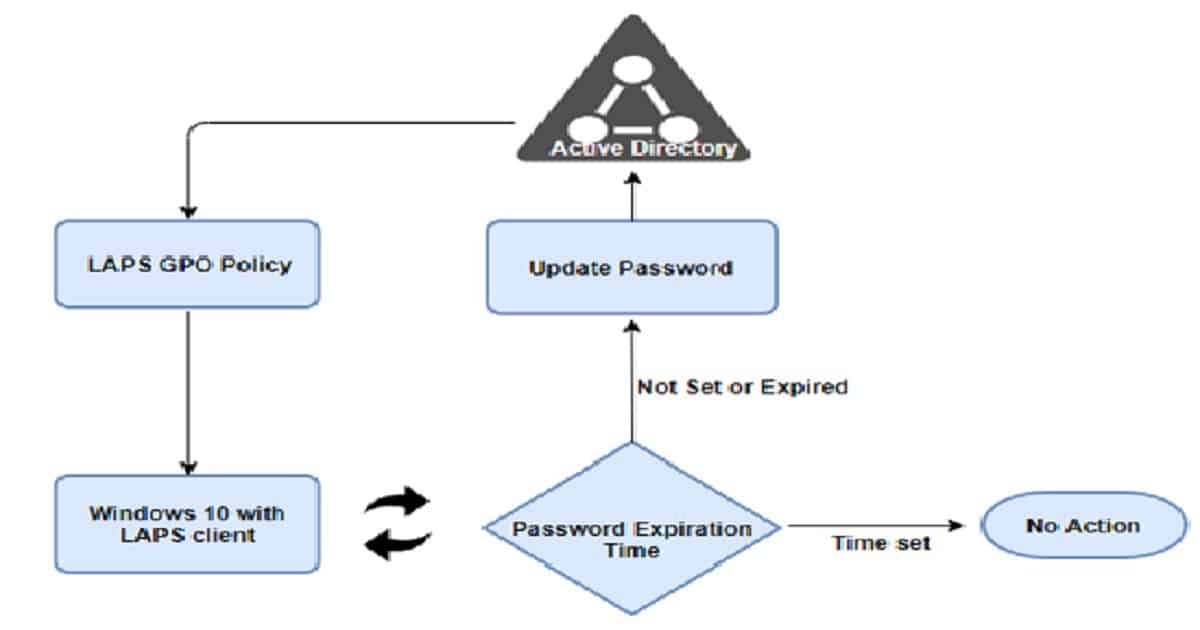
- The Windows 10 11 machine with LAPS client queries Group Policy and receives the defined LAPS policy settings.
- Machine queries “AdmPwdExpirationTime.” if not set or expired, it will generate a new password and securely write this value to the “AdmPwd” attribute in Active Directory.
- Password is now stored in Active Directory and is ready for use
- LAPS CSE will query this password expiration time value on each Group Policy update. When the AdmPwdExpirationTime is met or the attribute is not set. it will re-generate a new password
- If a machine cannot contact Active Directory, no changes are made
Azure AD Joined Windows 10 11 LAPS?
You don’t have a Microsoft solution for privilege access management on Azure AD-joined Windows 10 devices. I don’t know whether Azure AD will have some LAPS components in the future, but there are some scripted solutions available for Windows 10 LAPS Azure AD devices.
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
Gurudatt is a Technical Architect with 15 years of experience in the End-User Computing space. His main area of interest is the design and implementation of ConfigMgr Infrastructure. He has a vast knowledge of ConfigMgr infrastructure and client-side troubleshooting.

Good one !!
Interesting Blog! Thanks for the writeup Gurudatt..
Thank you for sharing detailed information.
Informative one
All the best
Thanks
Indeed a good overview and use case. This will definitely help orgs on PAM.
Thanks you to share this information about LAPS.
Thanks
There is an offering from Synergix that takes care of the Local Admin Password ( LAPS ) solution for Azure AD. In fact, it is Azure AD Hybrid joined device ready !
https://www.synergix.com/products/secrets-vault/features/laps-for-azure-ad/
Guru can permission to view/reset passwords be delegated on a sub-OU basis or must it be across the entire domain? For example:
Two OUs in same domain with computer objects
“Finance OU” and “Executives OU”
The idea is helpdesk could see/reset passwords for computer objects in Finance but only domain admins can see/reset for Executives
Can helpdesk be assigned to ONLY view and reset passwords for the “Finance OU” or will they be able to see passwords for ALL computers across all sub-OUs?
To secure access to passwords managed by LAPS you can use WebLAPS. It adds additional security features like 2FA, fine grained access control, audit log with SIEM integration, access rate limiting, rest API for external systems. Mobile app allows to get access to LAPS managed password from anywhere in a secure way. https://weblaps.pro
Nice article.
I have recently written and provided a LAPS solution for Azure joined devices, where the local admin passwords change on each enrolled device on a 90 day cycle and upload to Azure tables. I’ve also written a nice GUI for IT staff to retrieve passwords. Works well.
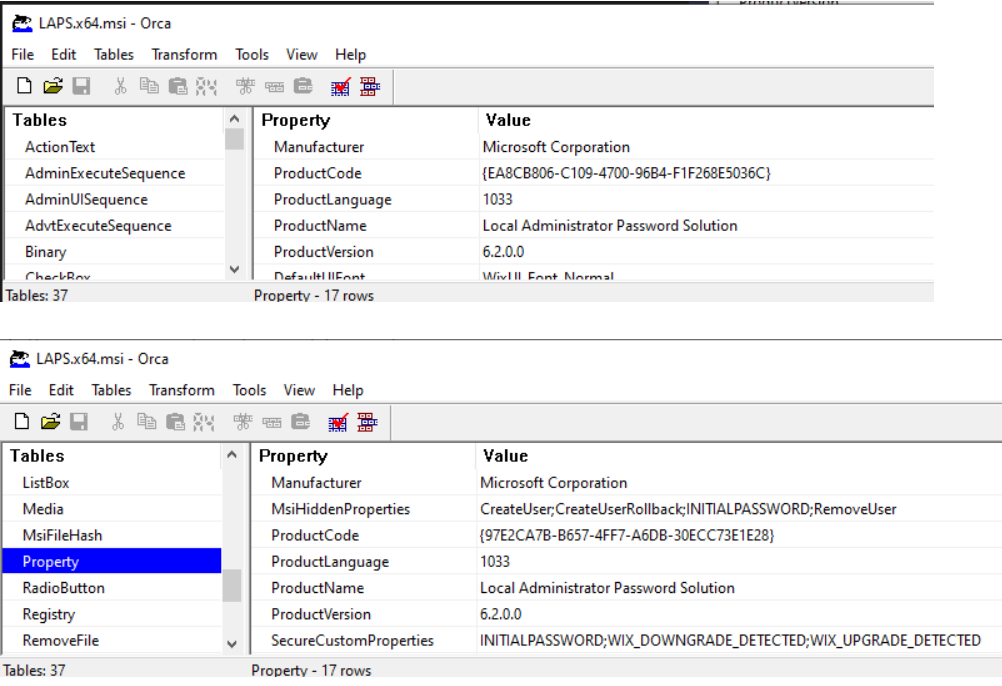
Hi, thanks for posting this, very informative. As a man in the know, would you know how the March release of Laps V6.2.0.0 is different to the Laps V6.2.0.0 that was available prior to that? The March release has the same version, but different product code and the file sizes have changed(gotten bigger).
I have posted more detail here if you aren’t sure what I mean. https://docs.microsoft.com/en-us/answers/questions/862795/laps-v6200-download-new-guid-for-march-2022-releas.html?childToView=866030#answer-866030
Thank you. We have updated the post to reflect this.