In this article, we can check Intune Security Policy to Set Up Smart Screen Enhanced Phishing Protection. You can configure SmartScreen Enhanced Phishing Protection using Microsoft Intune to strengthen your organization’s security posture on Windows 11 devices. This feature is part of Microsoft Defender SmartScreen and provides real-time protection by detecting and warning users about phishing attempts, credential reuse, and insecure password storage.
By leveraging Intune’s configuration profile capabilities, admins can centrally manage and enforce these settings across enrolled devices. To deploy this, create a Settings Catalog profile in Intune targeting Windows 10 and later. Within the configuration settings, enable “Microsoft Defender SmartScreen,” and then configure the Enhanced Phishing Protection options such as “Notify Malicious,” “Notify Password Reuse,” and “Notify Unsafe App” to “Enabled.”
These settings ensure users receive warnings when entering credentials on suspicious websites, reusing passwords, or storing them in unsafe applications like Notepad. Once the profile is created and assigned to device groups, Intune delivers these settings to the endpoints, and you can monitor compliance and deployment success through the Intune Admin Center.
This proactive configuration significantly reduces the risk of credential theft and phishing attacks by alerting users at the point of risk and helping them avoid unsafe behaviours. The Enhanced Password Phishing Protection. Microsoft released the security baseline package for Windows 11 version 22H2 onwards.

Table of Contents
Smart Screen Enhanced Phishing Protection Settings
The table below provides a brief overview of the options available in the Intune Configuration Profile Settings Catalog, along with a short description for each.
| Settings Name | Description |
|---|---|
| Automatic Data Collection | Automatically collect website or app content when additional analysis is needed to help identify security threats. |
| Notify Malicious | Configures Enhanced Phishing Protection notifications for malicious content. |
| Notify Password Reuse | Configures Enhanced Phishing Protection notifications for protecting passwords from reuse. |
| Notify Unsafe App | Configures Enhanced Phishing Protection notifications for protecting passwords typed into M365 Office applications, Notepad, and Wordpad. |
| Service Enabled | Enables Enhanced Phishing Protection in audit mode for Windows 11 22H2 |
- Best way to Fix Classic Outlook Crashes using Intune PowerShell Remediation Script
- How to Install Microsoft Defender Browser Protection Extension using Intune PowerShell Script
- Windows LAPS Automatic Account Management using Microsoft Intune
Create a Configuration Policy to Set Up Smart Screen Enhanced Phishing Protection
To Set Up Smart Screen Enhanced Phishing Protection with Microsoft Intune, follow these steps. First, sign in to the Microsoft Intune Admin Center with your administrator credentials.
- Navigate to Devices > Windows > Manage devices > Configuration
- Click on +Create > +New Policy
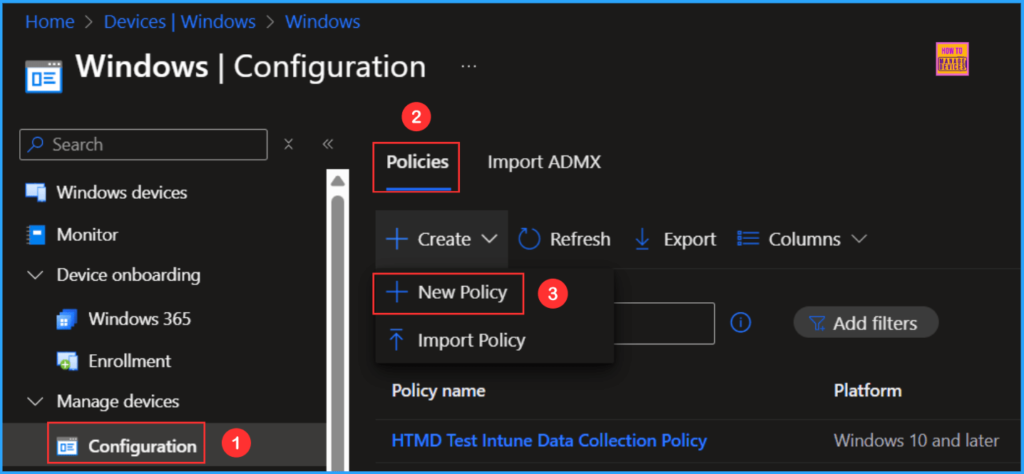
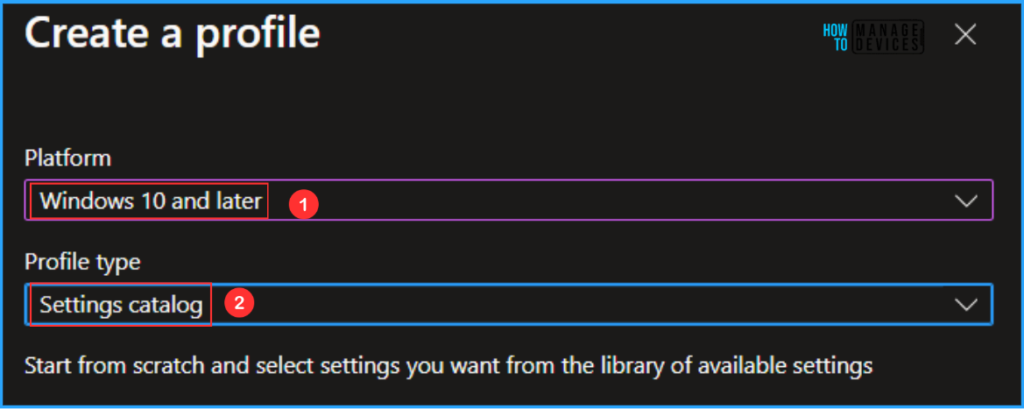
Next, we will create a new configuration profile from scratch. First, we need to provide the options mentioned below. The following bullet points provide more details.
- Platform: Windows 10 and later
- Profile type: Settings catalog
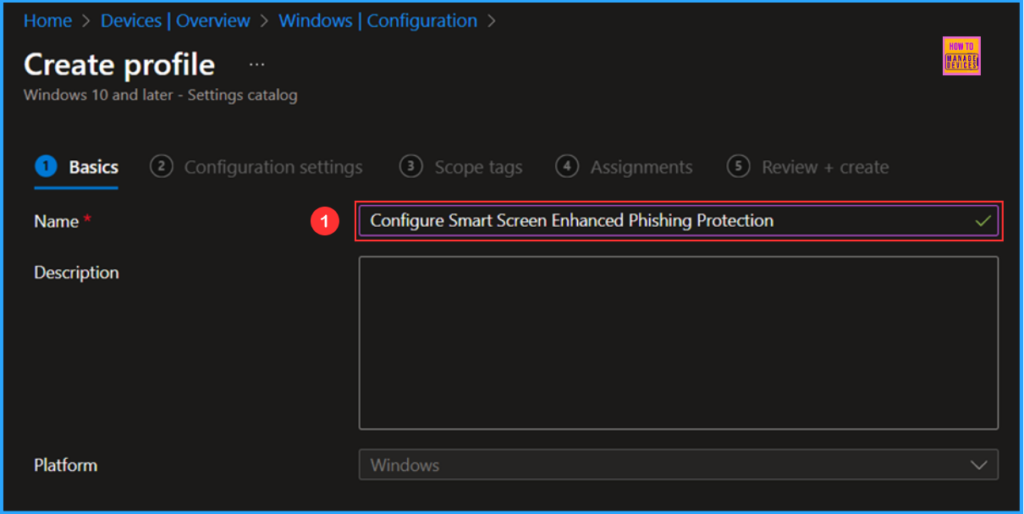
In the Basics details pane, you can name the configuration policy “Configure Smart Screen Enhanced Phishing Protection” If required, provide a brief description of the policy’s purpose and then click Next.
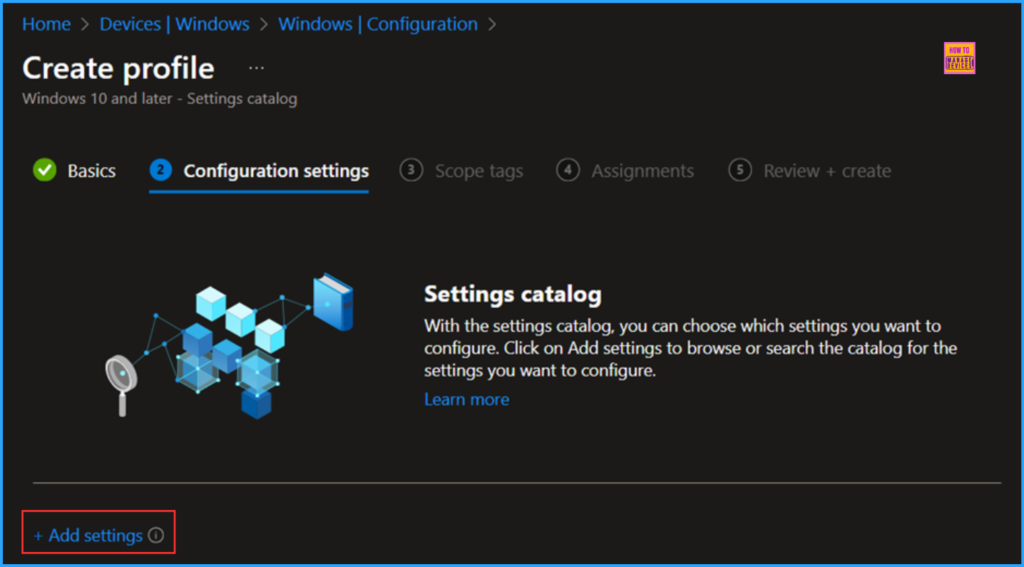
We can now add the necessary settings to the Configuration Settings pane. To do this, click on +Add settings in the bottom left corner of the page.
To find the appropriate policy based on your current needs, search for the keyword Enhanced Phishing Protection Once you have done that, go to the category labeled Smart Screen / Enhanced Phishing Protection Click on it, and then make sure to check all the following options: Automatic Data Collection, Notify Malicious, Notify Password Reuse, and Notify Unsafe App and Service Enabled. Finally, close the Settings picker window.
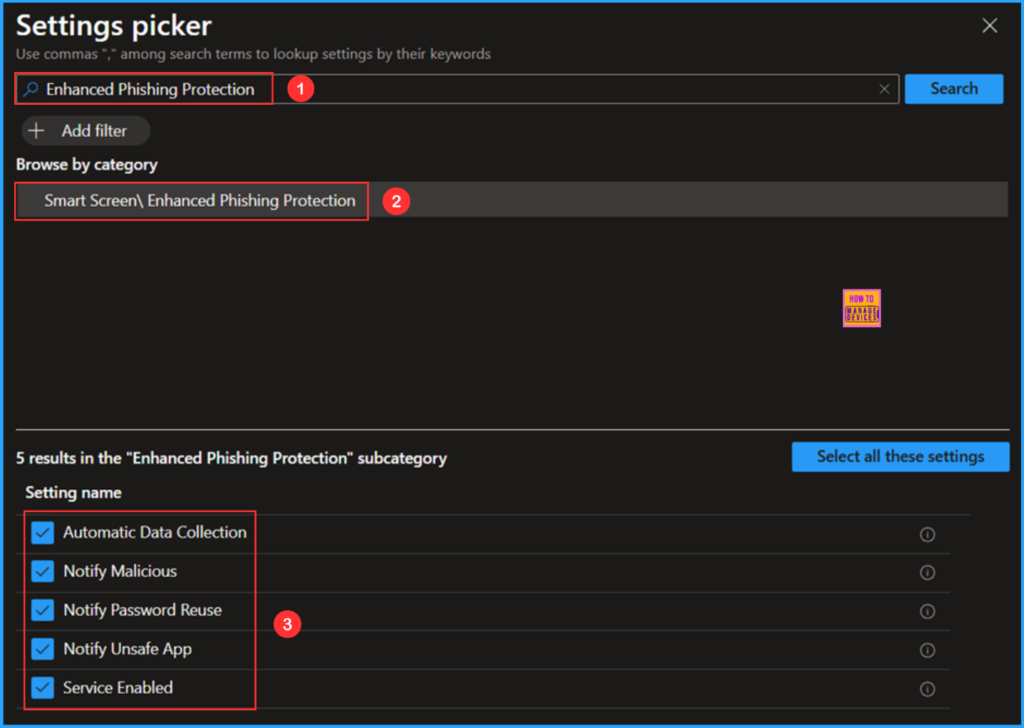
On the current page, set all these Smart Screen Enhanced Phishing Protection options to Enabled. then click Next.
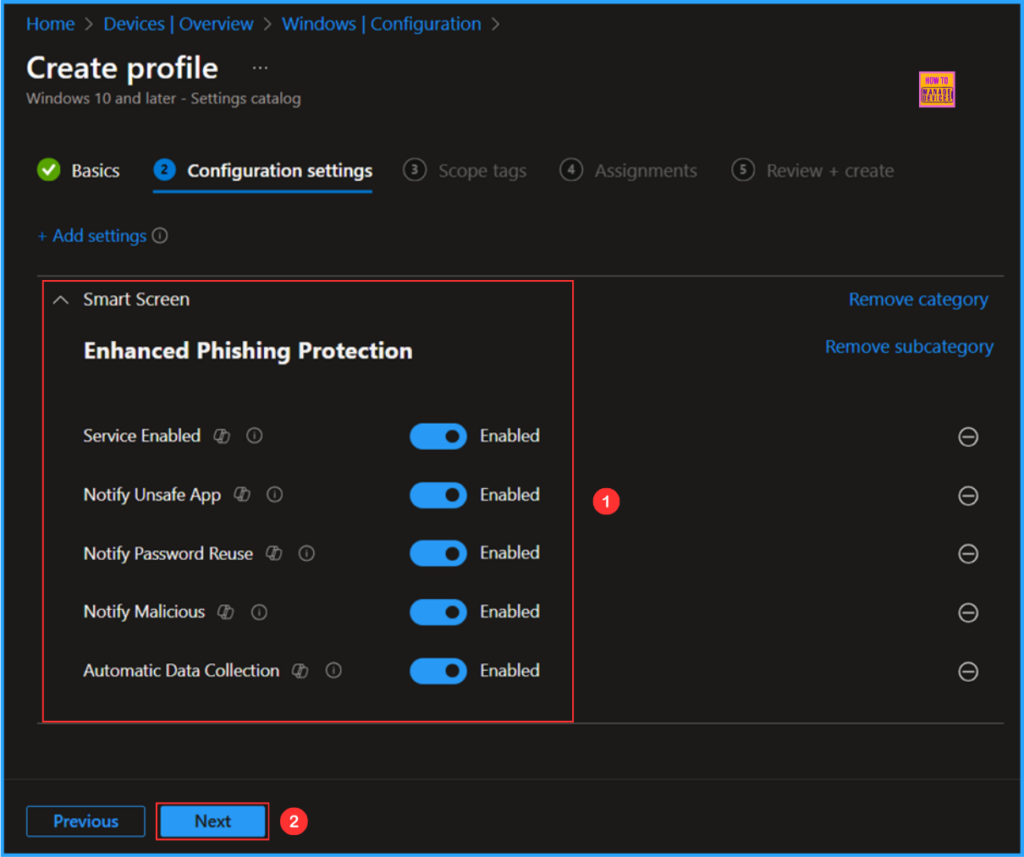
On the next page, leave the Scope tags as Default. If your tenant has custom scope tags, you can select them based on your policy needs, then click on Next.
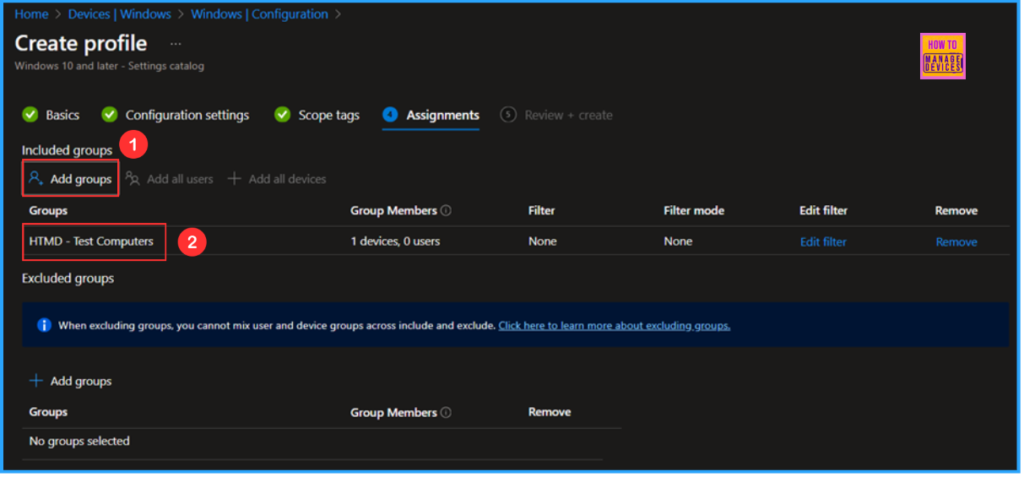
In this section, I will assign the configuration policy to the HTMD – Test Computers device group. To do this, click on Add group and select the desired device group under the Included groups option. In this example, I am not using any filters, and the Excluded groups option has been left empty.
On the Review + create page, review all settings for the Configure Smart Screen Enhanced Phishing Protection policy. Once confirmed, select Create to deploy the policy.
- Best way to Allow USB Access for Specific Devices using Intune
- Most Restrictive Elevation Behaviour with Intune Endpoint Privilege Management using Intune
- Enable or Disable App Install Control Policy using Intune Setting Catalog
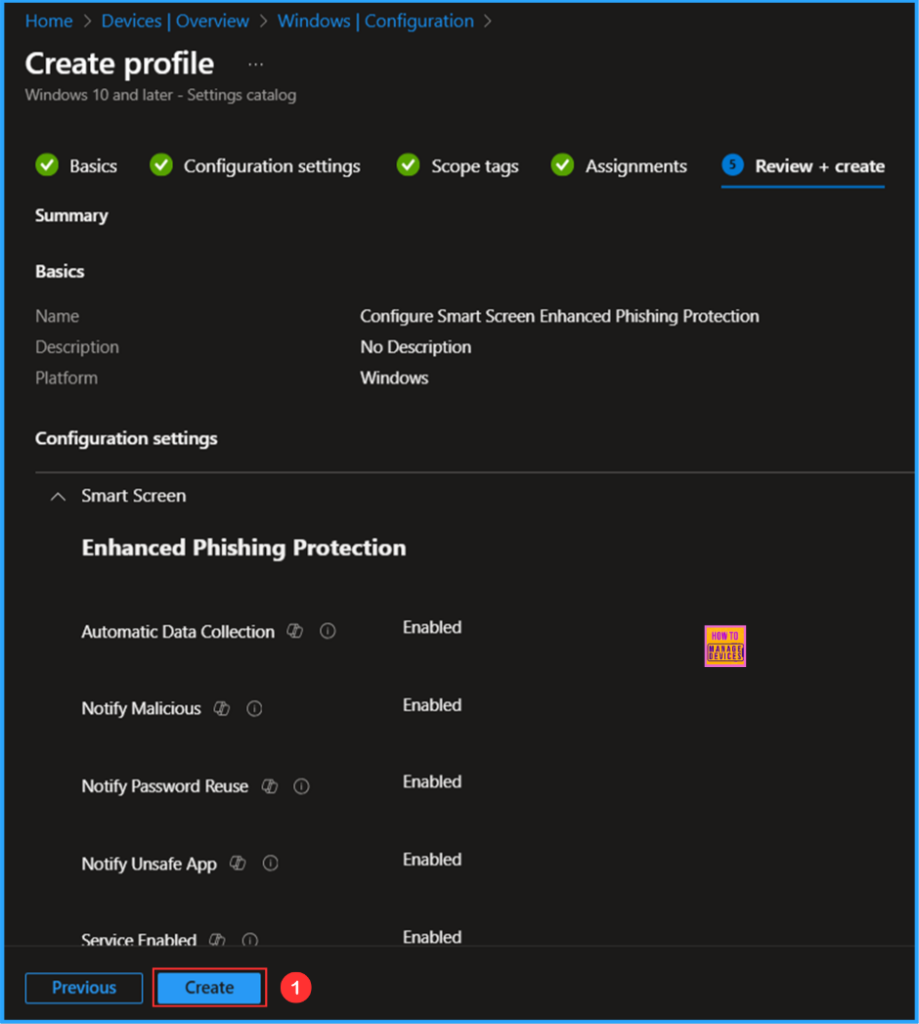
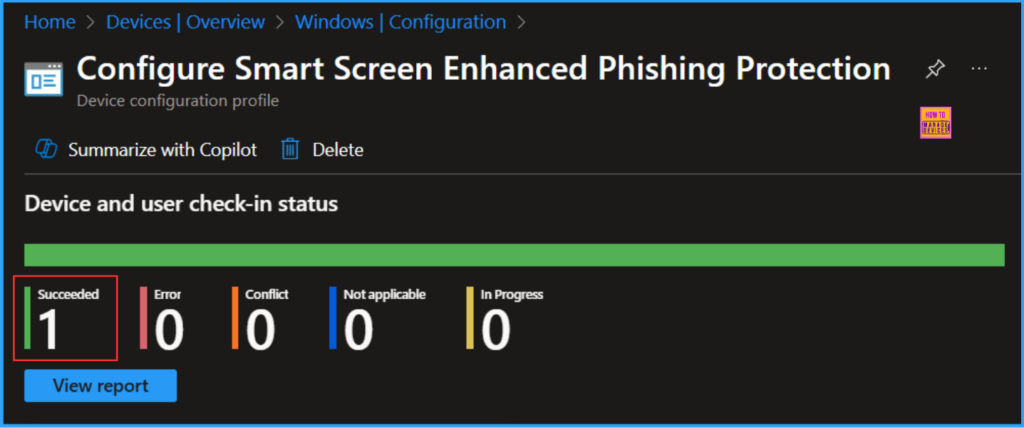
Monitor the Smart Screen Enhanced Phishing Protection Policy Deployment
The configuration policy has been deployed to the Microsoft Entra ID Device group for HTMD – Test Computers. Once the device is synchronized, the policy will take effect immediately. To monitor the status of the policy deployment, follow the steps below in the Intune Portal.
- Navigate to Devices > Windows > Configuration > Search for the “Configure Smart Screen Enhanced Phishing Protection” configuration policy.
- Under the Device and user check-in status, you can see the policy’s deployment status
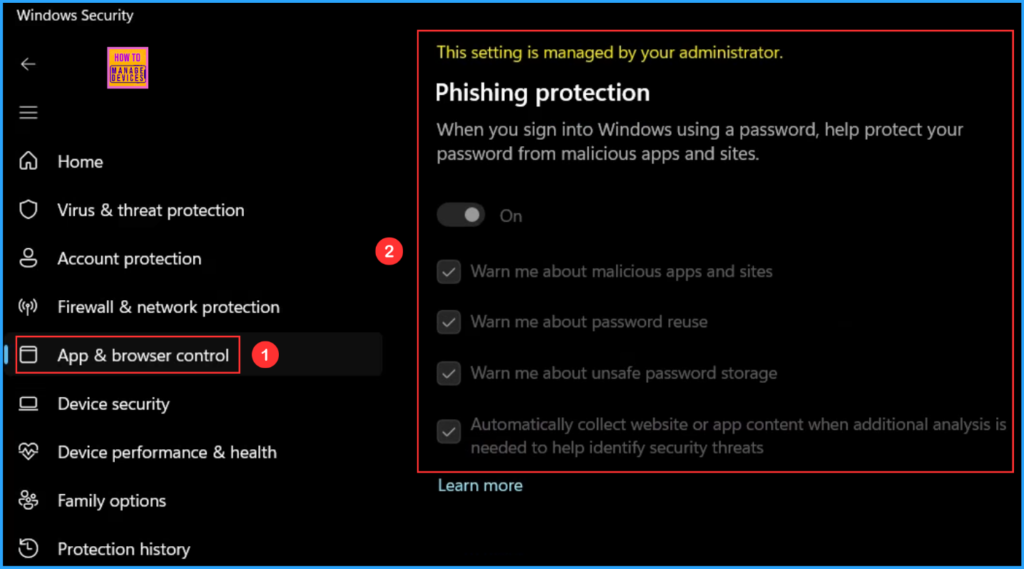
End User Experiance
To verify that the Enhanced Phishing Protection policy is functioning correctly, start by logging into the device that the policy affects. Once logged in click on start menu and search for Windows Security > App & browser control > Reputation-based protection.
You may notice the message “This setting is managed by your administrator” Phishing protection is turned on, and the following options are checked but grayed out:
- Warn me about malicious apps and sites
- Warn me about password reuse
- Warn me about unsafe password storage
- Automatically collect website or app content when additional analysis is needed to help identify security threats
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has over 11 years of experience in SCCM, Device Management, and Automation Solutions. Writes and imparts knowledge about Microsoft Intune, Azure, PowerShell scripting, and automation. Check out my profile on LinkedIn.


