How to Track User Registration Details in Entra ID using Microsoft Graph API! Let’s discuss how the Tracking MFA and Passwordless Adoption in Entra ID Using Microsoft Graph API would work. We will learn the automated method to Audit MFA and Passwordless Registration in Entra ID. Let’s have A deep Dive into userRegistrationDetails.
Microsoft Entra, formerly known as Azure Active Directory is a modern, cloud-native solution for identity and access management. As a robust directory and identity service, it delivers a comprehensive set of authentication and authorization capabilities across Microsoft services such as Office 365, Dynamics 365, Azure, and a wide range of cloud-based applications.
Microsoft Graph provides programmatic access to identity and access reports, enabling organizations to monitor user activity and troubleshoot issues across their Entra ID environment. These logs can be integrated with Azure Monitor and Log Analytics for deep analysis, or streamed to third-party SIEM platforms to support advanced threat detection and forensic investigations.
You can automate a wide range of identity and access reports, including AD FS application activity, authentication method registration and usage, and Microsoft Entra audit logs. Note that Graph activity logs are available only with Microsoft Entra ID P1 or P2 licenses. Additionally, data is not retained by default, it must be archived to a storage account or connected to analytics tools for long-term access and reporting.
Table of Contents
Working with the Entra ID User Registration Report
The User Registration report provides detailed insights into authentication method adoption across your organization. It shows how many users are registered for each method, including Multi-Factor Authentication (MFA), Self-Service Password Reset (SSPR), and passwordless authentication and highlights registration trends and failure rates. This data helps administrators assess readiness, identify gaps, and optimize user onboarding strategies.
Multi-Factor Authentication (MFA) adds an extra layer of protection by requiring users to verify their identity through multiple methods, such as entering a password and confirming a code sent to their phone. This change is designed to reduce the risk of unauthorized access and better protect sensitive information from potential cyber threats.
- Self-Service Password Reset (SSPR) empowers users to securely reset their own passwords using verified authentication methods, safeguarding account confidentiality without external intervention.
- By removing the dependency on IT administrators or help desk staff, SSPR streamlines support operations and redirects valuable resources toward strategic initiatives.
- This user-driven approach enables rapid account recovery, reduces downtime, and enhances overall productivity across the organization.

- Track All Intune Policy and App Assignments for Users Devices and Entra ID Groups with Assignment Checker
- How to Assign Custom Intune Role Based Access to Azure AD Groups using Microsoft Entra PIM
- Best Practices for Creating Entra ID Dynamic Groups for Intune
- Create AAD Dynamic Groups based on Domain Join Type Hybrid Azure AD and Azure AD
Learn more about userRegistrationDetails Properties
The userRegistrationDetails resource type provides a comprehensive view of a user’s authentication method status. It outlines which methods the user has registered, such as Multi-Factor Authentication (MFA), Self-Service Password Reset (SSPR), and passwordless options and indicates their capability and enrollment in these features.
| Property | Type | Description |
|---|---|---|
| id | String | User object identifier in Microsoft Entra ID. Inherited from entity. |
| isAdmin | Boolean | Indicates whether the user has an admin role in the tenant. This value can be used to check the authentication methods that privileged accounts are registered for and capable of. |
| isMfaCapable | Boolean | Indicates whether the user has registered a strong authentication method for multifactor authentication. The method must be allowed by the authentication methods policy. Supports $filter (eq). |
| isMfaRegistered | Boolean | Indicates whether the user has registered a strong authentication method for multifactor authentication. The method may not necessarily be allowed by the authentication methods policy. Supports $filter (eq). |
| isPasswordlessCapable | Boolean | Indicates whether the user has registered a passwordless strong authentication method (including FIDO2, Windows Hello for Business, and Microsoft Authenticator (Passwordless)) that is allowed by the authentication methods policy. Supports $filter (eq). |
| isSsprCapable | Boolean | Indicates whether the user has registered the required number of authentication methods for self-service password reset and the user is allowed to perform self-service password reset by policy. Supports $filter (eq). |
| isSsprEnabled | Boolean | Indicates whether the user is allowed to perform self-service password reset by policy. The user may not necessarily have registered the required number of authentication methods for self-service password reset. Supports $filter (eq). |
| isSsprRegistered | Boolean | Indicates whether the user has registered the required number of authentication methods for self-service password reset. The user may not necessarily be allowed to perform self-service password reset by policy. Supports $filter (eq). |
| isSystemPreferredAuthenticationMethodEnabled | Boolean | Indicates whether system preferred authentication method is enabled. If enabled, the system dynamically determines the most secure authentication method among the methods registered by the user. Supports $filter (eq). |
| lastUpdatedDateTime | DateTimeOffset | The date and time (UTC) when the report was last updated. The DateTimeOffset type represents date and time information using ISO 8601 format and is always in UTC time. For example, midnight UTC on Jan 1, 2014 is 2014-01-01T00:00:00Z. |
| methodsRegistered | String collection | Collection of authentication methods registered, such as mobilePhone, email, passKeyDeviceBound. Supports $filter (any with eq). |
| systemPreferredAuthenticationMethods | String collection | Collection of authentication methods that the system determined to be the most secure authentication methods among the registered methods for second factor authentication. Possible values are: push, oath, voiceMobile, voiceAlternateMobile, voiceOffice, sms, none, unknownFutureValue. Supports $filter (any with eq). |
| userDisplayName | String | The user display name, such as Adele Vance. Supports $filter (eq, startsWith) and $orderby. |
| userPreferredMethodForSecondaryAuthentication | userDefaultAuthenticationMethod | The method the user selected as the default second-factor for performing multifactor authentication. Possible values are: push, oath, voiceMobile, voiceAlternateMobile, voiceOffice, sms, none, unknownFutureValue. This property is used as preferred MFA method when isSystemPreferredAuthenticationMethodEnabled is false. Supports $filter (any with eq). |
| userPrincipalName | String | The user principal name, such as AdeleV@contoso.com. Supports $filter (eq, startsWith) and $orderby. |
| userType | signInUserType | Identifies whether the user is a member or guest in the tenant. The possible values are: member, guest, unknownFutureValue. |
The table above provides a detailed explanation of the userRegistrationDetails properties and their descriptions. Special thanks to Microsoft for the comprehensive reference. This data is essential for assessing identity readiness and enforcing secure access policies across your organization.
Permissions
Select the least privileged permission(s) required for this API. Only use higher-privileged permission(s) if your application specifically needs them. For more information on delegated and application permissions, refer to the beow table. Thank you, Microsoft, for providing the table.
| Permission type | Least privileged permissions | Higher privileged permissions |
|---|---|---|
| Delegated (work or school account) | AuditLog.Read.All | Not available. |
| Delegated (personal Microsoft account) | Not supported. | Not supported. |
| Application | AuditLog.Read.All | Not available. |
- Best Practices for Creating Entra ID Dynamic Groups for Intune
- Create AAD Dynamic Groups based on Domain Join Type Hybrid Azure AD and Azure AD
Get Entra ID Users Authentication Methods with Microsoft Graph API
Let’s learn how to retrieve the list of authentication methods registered for all users, as defined in the userRegistrationDetails object. This will display all relevant user details.
- Best Guide to Restart Intune Devices Remotely using Microsoft Graph API and PowerShell
- Best Guide to Run Intune Device Query with Microsoft Graph API
- Automate Microsoft Intune Device Compliance Report using Graph API
The below mentioned endpoint will retrieves the userRegistrationDetails details for you. Here, you should note down the userRegistrationDetails Properties
- Sign in to the Graph Explorer with your credentials.
- Click on Run query after typing the URL below. You should use the GET API request method
https://graph.microsoft.com/v1.0/reports/authenticationMethods/userRegistrationDetails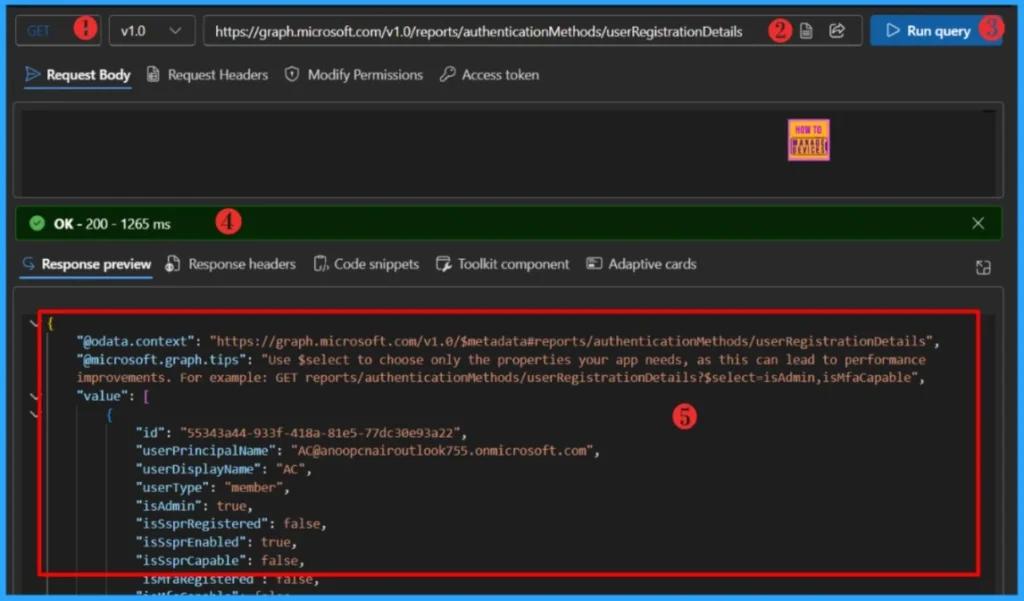
Within seconds of clicking Run query, you will receive a success message with the text OK -200. The output will be dispalyed in Response preview panel. The output format is shown below.
{
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#reports/authenticationMethods/userRegistrationDetails",
"@microsoft.graph.tips": "Use $select to choose only the properties your app needs, as this can lead to performance improvements. For example: GET reports/authenticationMethods/userRegistrationDetails?$select=isAdmin,isMfaCapable",
"value": [
{
"id": "55343a44-933f-418a-81e5-77dc30e93a22",
"userPrincipalName": "AC@anoopcnairoutlook755.onmicrosoft.com",
"userDisplayName": "AC",
"userType": "member",
"isAdmin": true,
"isSsprRegistered": false,
"isSsprEnabled": true,
"isSsprCapable": false,
"isMfaRegistered": false,
"isMfaCapable": false,
"isPasswordlessCapable": false,
"methodsRegistered": [],
"isSystemPreferredAuthenticationMethodEnabled": false,
"systemPreferredAuthenticationMethods": [],
"userPreferredMethodForSecondaryAuthentication": "none",
"lastUpdatedDateTime": "2025-09-11T12:20:36.5123459Z"
},Get a Specific Entra ID User’s Authentication Methods Using Microsoft Graph API
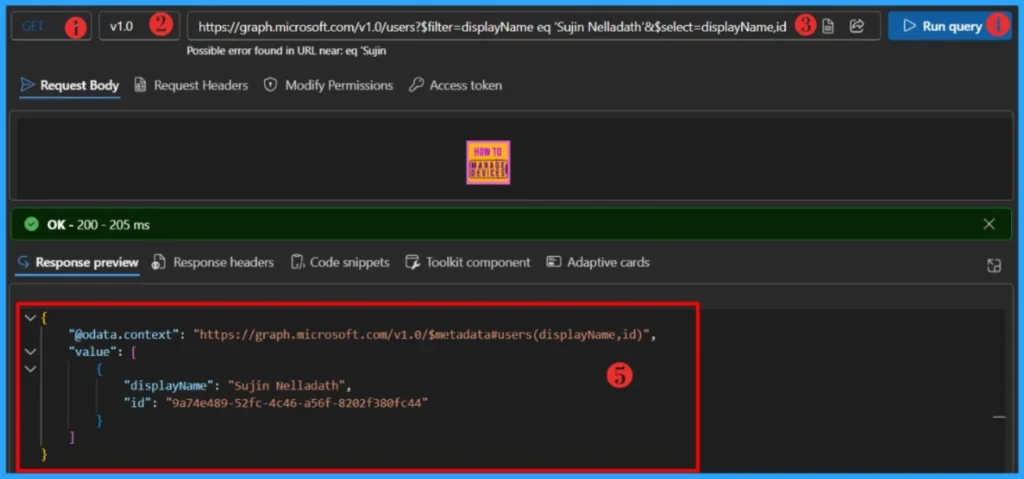
Let’s learn how to Get a Specific Entra ID User’s Authentication Methods Using Microsoft Graph API. We need to retrieve the user’s Object ID using the endpoint below. You should use the GET API request method.
https://graph.microsoft.com/v1.0/users?$filter=displayName eq 'User'&$select=displayName,idYou should replace the user’s name, i.e., User, with your user’s display name. When you click on Run query, you will receive a success message with the text ‘OK -200.’ The Response preview box will show the desired output.
- Time to use Microsoft Graph Device Management PS Module Instead of MS Graph Intune Module.
- Automate Intune App Deployment using Microsoft Graph API and PowerShell
- Manage Intune Tasks with PowerShell Part 1
You should have at least User.ReadWrite.All permission to run the query. Note down the Object ID of the target User.
The below mentioned endpoint will retrieves the userRegistrationDetails details of peticular user for you. Make sure replace the User-id.
https://graph.microsoft.com/v1.0/reports/authenticationMethods/userRegistrationDetails/{userId}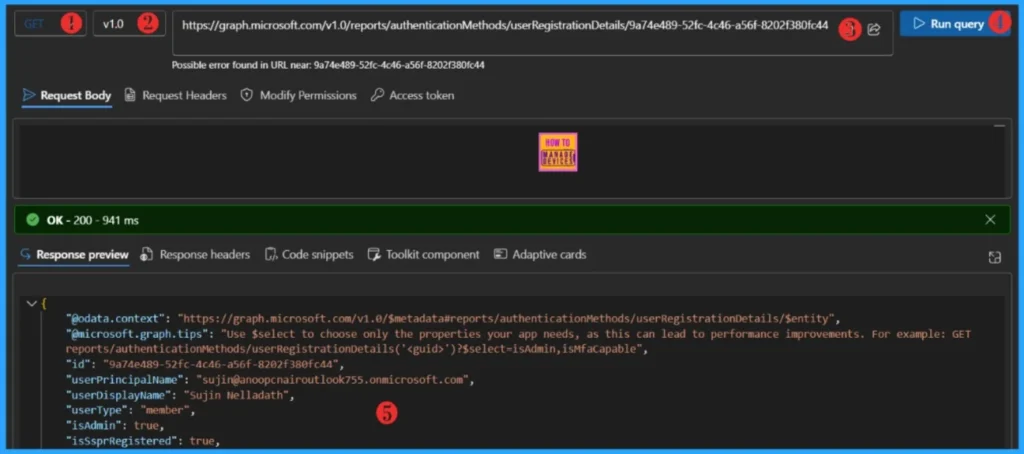
I trust that this article will significantly benefit you and your organization. I appreciate your patience in reading this post. I look forward to seeing you in the next post. Keep supporting the HTMD Community.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
About the Author: Sujin Nelladath, a Microsoft Graph MVP with over 11 years of experience in SCCM device management and Automation solutions, writes and shares his experiences with Microsoft device management technologies, Azure, DevOps and PowerShell automation.