In this guide, you’ll learn how to Configure PowerShell Execution policy with Intune Configuration Profile. The present discourse aims to elucidate the process of setting up the PowerShell Execution policy using Intune.
In today’s business and academic world, automation has become an indispensable tool for every IT professional irrespective of their area of specialization. The ability to automate processes effectively and efficiently is crucial for organizations to remain competitive and sustain growth in the ever-evolving technological landscape. Therefore, it is imperative that IT professionals acquire the necessary knowledge and skills required to develop and implement automated processes to enhance productivity and improve workflow efficiency.
PowerShell is a versatile automation tool from Microsoft that can be used by Windows System Administrators to automate a wide range of tasks. PowerShell has become an indispensable tool for automation enthusiasts and system administrators alike. It is their go-to program for simplifying tasks and streamlining workflows.
As an automation enthusiast, I was eager to explore how Intune could manage PowerShell commands. This approach can offer a powerful means of automating tasks and streamlining workflows. Have you had the opportunity to delve into this area yet?
- Intune Policy Assignment Classification Easy Secrets of using Graph API with PowerShell
- Managing Windows Bitlocker Compliance Policy Using Intune | MS Graph | Grace Period
Understand the Potential Risks of Automation
This space is too limited to cover PowerShell and its automation capabilities in detail, but I have discussed enough about it. In order to fully appreciate the benefits of utilizing PowerShell, it is imperative to acknowledge the potential risks inherent in executing its code. Therefore, it is essential to exercise caution when running PowerShell code in order to prevent potentially harmful outcomes.
Using scripts for OS automation can pose a significant security risk, as they may contain malicious code that can harm your system, data, or network. Such malicious code can be embedded in scripts either deliberately by attackers, accidentally, or due to third-party sources. It is essential to be cautious while using scripts and ensure that they originate from trusted sources to prevent any potential harm to your system.

You should clearly understand your code and the changes it will make to your environment. It is possible that any modifications made through your code may be irreversible. Therefore, exercising caution while carrying out any changes is imperative to ensure that they align with the intended outcome. It is important to note that any changes made through the code should be thoroughly tested and reviewed before implementation to prevent any undesirable consequences.
- Best way to Deploy Shell Scripts using Intune
- Run Remediation Script on-demand for Windows Devices using Intune
- PowerShell Script to Create a Local Admin Account using Intune
About the PowerShell Execution Policy
PowerShell’s execution policy is a feature that controls how PowerShell runs scripts and loads configuration files to prevent malicious scripts from executing. It describes the PowerShell execution and explains how to manage them. On a Microsoft Windows-based computer, it is possible to configure an execution policy for the local computer, current user, or a specific session. The ability to set an execution policy is a valuable security feature for Windows users who wish to protect their system from unwanted or unauthorized changes.
- PowerShell Script to Create a Local Admin Account using Intune
- Manage Intune Tasks with PowerShell Part 1
- How to Retrieve PowerShell Scripts from Intune using Microsoft Graph
Note! As per Microsoft, The Execution policies for the local computer and current user are stored in the registry. You don't need to set execution policies in your PowerShell profile. The execution policy for a specific session is stored only in memory and is lost when the session is closed.It is worth remembering that the execution policy is not a security system that limits user actions. It is possible for users to bypass a policy by entering the script contents at the command line when they are unable to run a script. However, the execution policy allows users to establish fundamental rules and prevents them from unintentionally breaking them.
The default execution policy is Unrestricted on non-Windows computers and cannot be changed at any cost. Windows has different Execution policies; let’s learn more!
| PowerShell Execution policy | Description |
|---|---|
| Restricted | No scripts can be run, But it permits individual commands, This is the default execution policy. |
| AllSigned | Requires a digital signature from a trusted publisher on scripts and configuration files that are downloaded from the internet, which includes email and instant messaging programs. Doesn’t require digital signatures on scripts that are written on the local computer and not downloaded from the internet. |
| RemoteSigned | Requires a digital signature from a trusted publisher on scripts and configuration files downloaded from the internet, including email and instant messaging programs. Doesn’t require digital signatures on scripts that are written on the local computer and not downloaded from the internet. |
| Unrestricted | Any script can be run. There is a risk of running malicious scripts. This is the default execution policy for non-Windows computers and cannot be changed. |
| Undefined | If the execution policy in all scopes is Undefined, the effective execution policy is Restricted for Windows clients and RemoteSigned for Windows Server |
You can modify the execution policy using the Set-ExecutionPolicy cmdlet. For instance, to set the execution policy for the local machine to RemoteSigned, use:
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope LocalMachine -force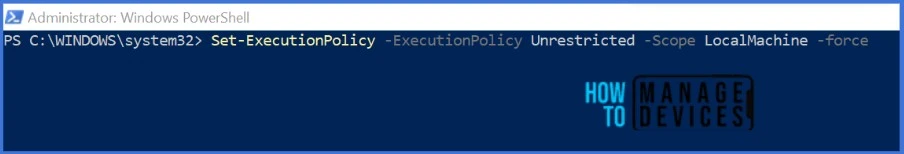
Use the Get-ExecutionPolicy cmdlet with the -List parameter to view execution policy settings.
Get-ExecutionPolicy -List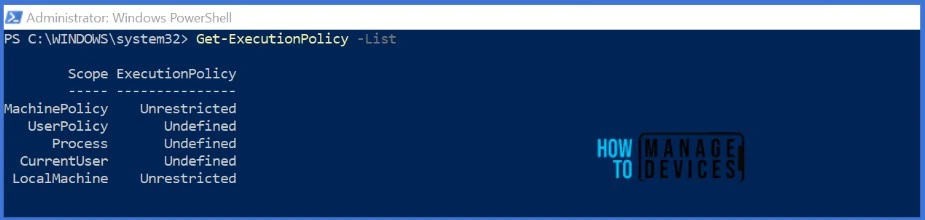
Configure PowerShell Execution Policy with Intune
Intune Configuration Profile can be utilized to establish the PowerShell Execution policy on corporate devices. This approach is particularly relevant when managing a large number of devices in your organisation. Group Policy is also an alternative option to configure the PowerShell Execution policy. Both methods can be effective in maintaining a secure environment for corporate devices. Let’s start..!
- Sign in to the Microsoft Intune Admin Portal.
- Select Devices > Windows > Configuration Profiles > Create > New Policy
You will open a new window when you click Create Policy. Select Windows 10 and later in Platform, Select Profile Type as Settings Catalog and click on Create
| Platform | Profile Type |
|---|---|
| Windows 10 and later | Settings Catalog |
Navigate to the Basics tab and input the Name and Description for the profile. Click Next to go further.
In the Configuration Settings section, under Settings Catalog, click Add Settings.
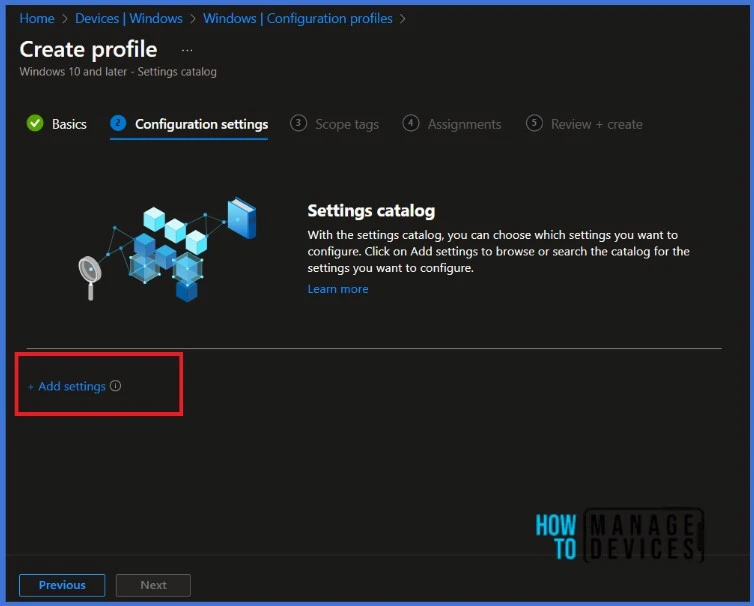
NOTE! Microsoft discovered that administrators may experience performance degradation when they add more than 400 settings to a single policy. However, Microsoft is working on making improvements to address this issue.When you click on Add Settings, you will get a Settings picker tab, as in bellow screenshot below. Search for Execution Policy in the search bar. Select Execution Policy (Device).
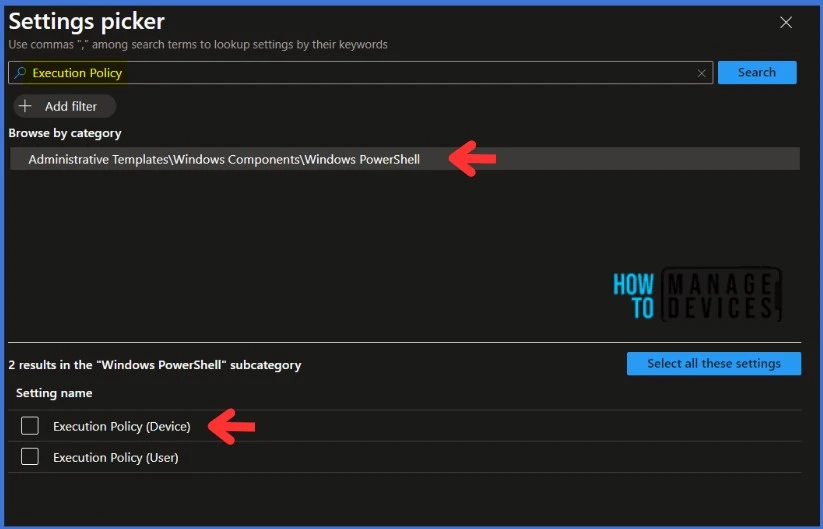
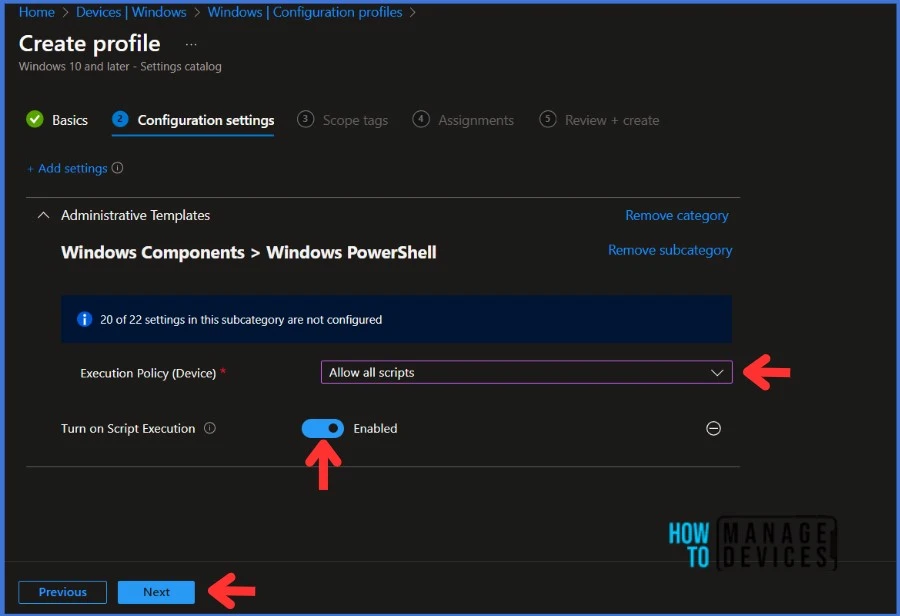
NOTE : If you set the Execution Policy for your device, any PowerShell scripts deployed using Intune will be affected.You must enable the Turn on Script Execution settings. You will have three Execution Policy options when you enable the settings. The Allow Only Signed Scripts policy setting allows scripts to execute only if they are signed by a trusted publisher. The Allow local scripts and remote signed scripts policy setting allows any local scrips to run; scripts that originate from the Internet must be signed by a trusted publisher. The Allow all scripts policy setting allows all scripts to run. If you disable this policy setting, no scripts are allowed to run.
In this example, I am setting the Execution Policy to Allow all scripts. Click Next to go further.
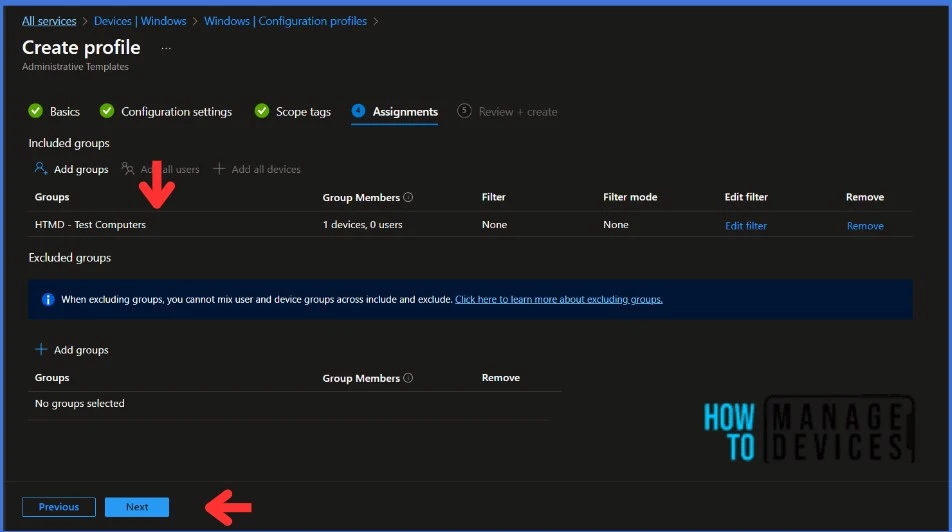
Click Next to display the Scope tags page. Add the Scope tags if you wish and click Next to assign the policy to computers. I will deploy it to the HTMD – Test Computers Group.
On the Review + Create page, carefully review all the settings you’ve defined to Configure the PowerShell Execution Policy. Once you’ve confirmed that everything is correct, select Create to implement the changes.
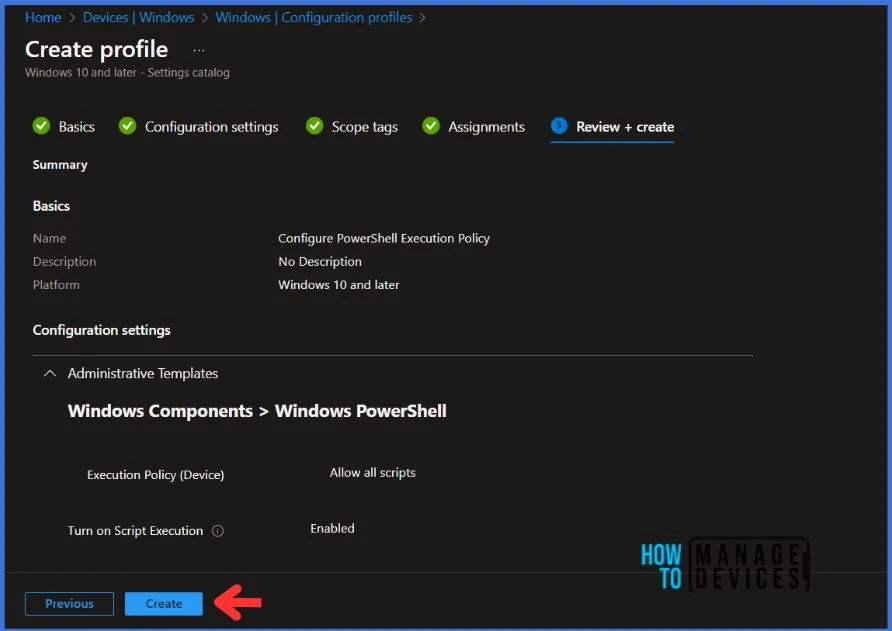
Monitor the Configuration Profile Deployment in Microsoft Intune
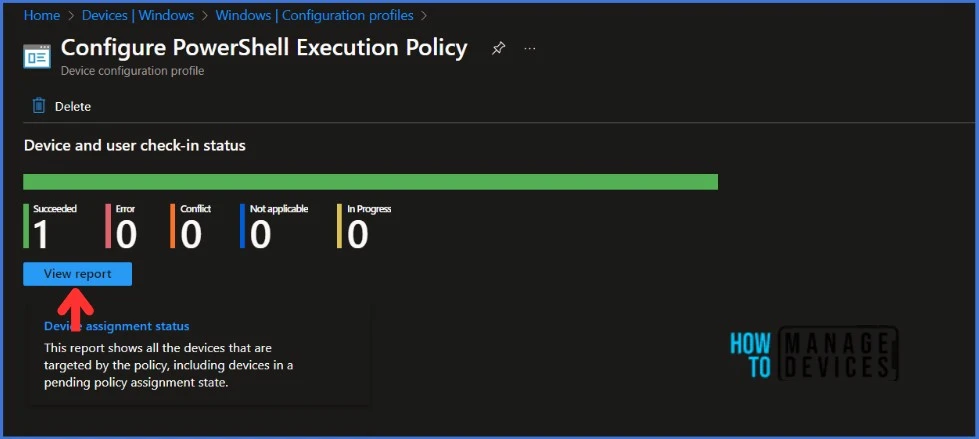
The configuration profile is deployed to Azure AD groups. Let’s see how we can monitor the deployment and status of installation from the Intune portal. To monitor the Intune policy assignment, follow these steps:
- Navigate to the list of Configuration Profiles and select the policy you targeted.
- Check the device and user check-in status from here.
- If you click “View Report,” you can see additional details.
End-User Experience After Configuring PowerShell Execution Policy
Based on the report, the policy has been successfully deployed to end-user devices. We need to verify if the policy is applied to these devices. There are multiple ways to check the deployment status on end-user devices.
I have deployed the Configuration Profile to the HTMD – Test Computers group. This AD group has only test devices. I recommend testing the deployment on pilot devices before implementing it in production. This can help identify any potential issues and ensure a smoother roll-out.
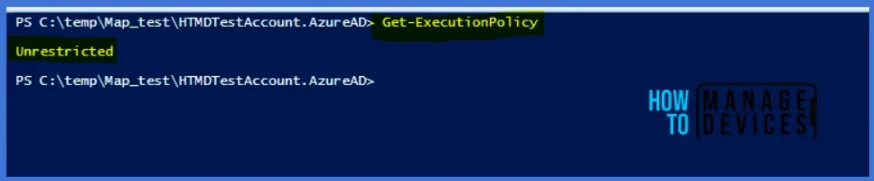
In this example, I have configured the Execution Policy to Allow all scripts. Run Get-ExecutionPolicy cmdlet on the end-user device to see the result.
Since we have configured the Execution Policy to Allow all scripts, Get-ExecutionPolicy cmdlet output should show Unrestricted. Let’s test it.
Thank you for your patience in reading this post. I look forward to seeing you in the next post. Keep supporting the HTMD Community.
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
About Author – Sujin Nelladath has over 10 years of experience in SCCM device management and Automation solutions. He writes and shares his experiences related to Microsoft device management technologies, Azure, and PowerShell automation.
