In this guide, you’ll learn how to create a Local Admin Account using a PowerShell Script with the help of Intune. By using Microsoft Intune, you can easily deploy any script to your workstation. The recommended approach is to use new Windows LAPs to manage the Local Admin accounts.
If you ever need to create a new local Windows administrator account and join it with a local user group, You can do it using a PowerShell script or a custom profile in Microsoft Intune. On Windows devices, you cannot create an administrator account using the Settings Catalog.
The local administrator account that is pre-installed on Windows devices is typically disabled by most businesses as a security measure. This is done to prevent IT or other users from performing administrative tasks using the built-in administrator account. By default, the local admin account on Windows 11 is disabled, but it can be enabled using different techniques.
The default local user accounts are built-in accounts that are automatically created during the operating system installation. These accounts cannot be removed or deleted, and they do not provide access to network resources. Nonetheless, they are useful for various administrative purposes. It is important to bear in mind the limitations of these accounts when managing user access to resources on a Windows device.
The built-in local administrator account that accompanies Windows devices is typically disabled as a security measure by most organizations, with the aim of preventing IT or other users from executing administrative tasks using the built-in administrator account.
It is common practice for organizations to disable the built-in local administrator account that comes with Windows devices as a security measure in order to prevent unauthorized access to administrative tasks.

What are the Default local user accounts?
Default local user accounts are utilized to manage access to local device resources based on the permissions and rights assigned to the account. The default local user accounts and those created by the user are found in the Users folder, situated in the Local Users and Groups folder within the Microsoft Management Console (MMC) for Computer Management. This console is a suite of administrative tools that facilitate the management of local or remote devices.
The Administrator account is a crucial feature of every computer’s system administration. It is assigned a unique SID S-1-5-domain-500 and a display name “Administrator“. This account is created during the Windows installation process and is the first account to be set up. This account is endowed with full control over files, directories, services, and other resources available on the device. Additionally, the Administrator account has the capability to create other local users, assign user rights, and assign permissions. It can also take control of local resources at any time by altering user rights and permissions. Hence, the Administrator account is a critical asset for system administrators in effectively managing the resources and security of devices.
The Default Administrator account can’t be deleted or locked out, but it can be renamed or disabled.
| Account | Delete | Lock | Rename | Disable |
|---|---|---|---|---|
| Default Administrator | No | No | Yes | Yes |
- Rename Administrator Account Policy Using Intune
- Reset Windows 11 Password Local Admin Microsoft Account Standard User
- Setup New Windows LAPs using Intune Policies Local Admin Password Management Policy
It is noteworthy that members belonging to the Administrators group can execute applications with privileged permissions without utilizing the run as Administrator option. However, it is to be noted that the use of Fast User Switching is a more secure approach when compared to using the runas command or different-user elevation. The latter method may pose a potential threat to system security, while Fast User Switching provides a more secure and reliable option.
PowerShell Script to Create an Administrator Account
As explained above, You can create an Administrator Account using a PowerShell script or a custom profile in Microsoft Intune. On Windows devices, you cannot create an administrator account using the Settings Catalog.
I have a PowerShell script to create an Administrator Account and add it to the default Administrator group.
####################################################
# Script: New-Localadminaccount.ps1
# Scope: Creates new local admin account and add to Administrators group
####################################################
$Username = "HTMD Admin User" #Replace HTMD Admin User with your username
$Password = "Password@123"
$group = "Administrators"
$adsidetails = [ADSI]"WinNT://$env:COMPUTERNAME"
$usercheck = $adsidetails.Children | where {$_.SchemaClassName -eq 'user' -and $_.Name -eq $Username }
if ($usercheck -eq $null)
{
Write-Host "Creating the new local user $Username."
& NET USER $Username $Password /add /y /expires:never
Write-Host "Adding local user $Username to the $group."
& NET LOCALGROUP $group $Username /add
}
else
{
Write-Host "Setting the password for existing local user $Username."
$usercheck.SetPassword($Password)
}
Write-Host "Setting the password for $Username never expires."
& WMIC USERACCOUNT WHERE "Name='$Username'" SET PasswordExpires=FALSETo upload and run PowerShell scripts on Windows devices, you can use the Microsoft Intune management extension. Simply upload the script to Intune, and then it can be deployed and run on the managed devices. This can be a useful tool for managing and automating tasks across your Windows 10 device fleet. When you deploy a PowerShell script to devices in Intune, you will notice Intune Management Extension installed on the device. Look at the article below explaining the Best Way to Deploy Powershell Script using Intune.
Create a Local Admin Account in Intune
I will be using the above PowerShell Script to create a Local Admin Account in Intune. The script will add the newly created account to the Administrator group and make the Password never expire. If you don’t want your password to remain valid indefinitely, you have the option to modify the code at your convenience.
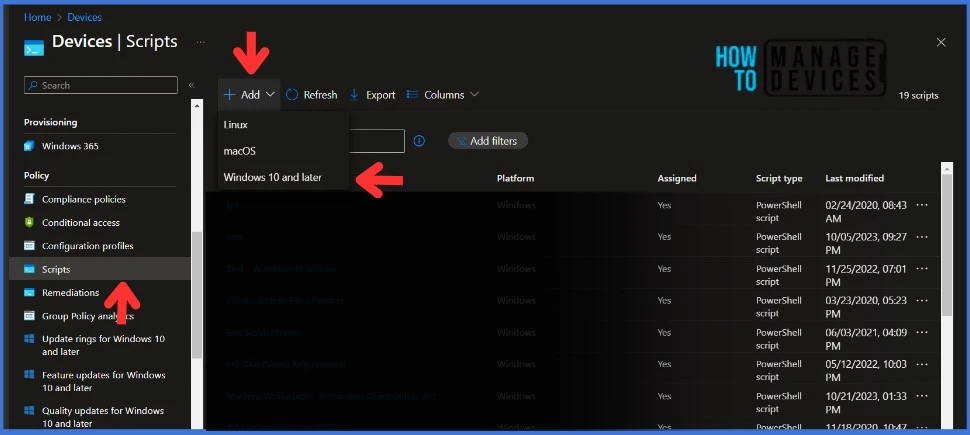
- Sign in to the Microsoft Intune Admin portal.
- Navigate to Devices > Scripts >Add and select Windows 10 and later. Click Next to go further.
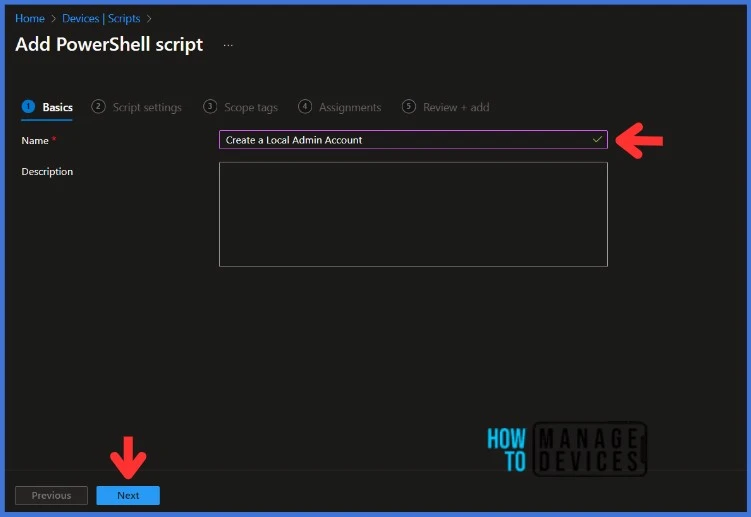
Navigate to the Basics tab and input the Name and Description for the script.
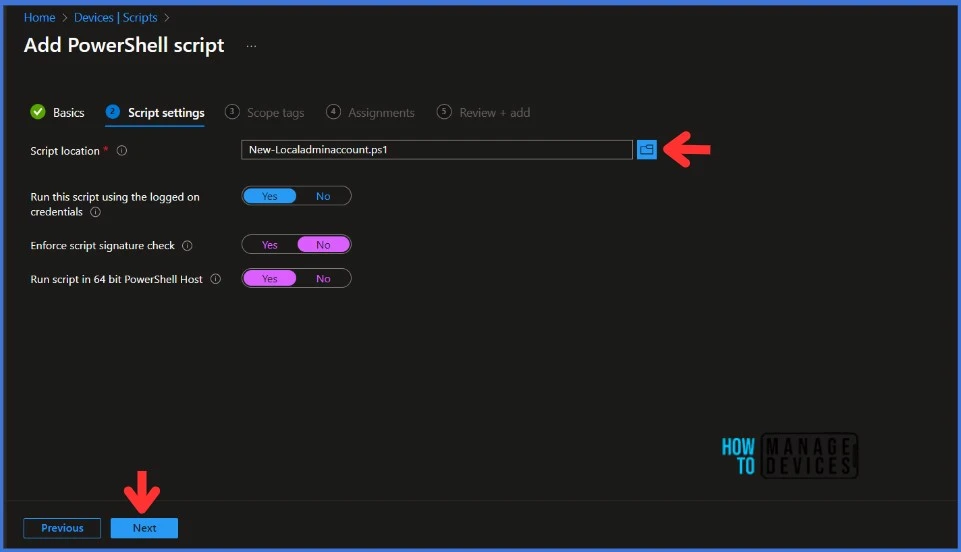
In Script Settings, enter the information below according to the requirement and click Next.
- Script Location: Browse the PowerShell script where you placed it, and the script must be less than 200 KB.
- Run the script using the logged-on credentials: Select Yes to run the script on the user credential. Otherwise, select No (default); it will run in a system context. The administrator must decide on this setting according to the requirements.
- Enforce script signature check: Select Yes if the script is signed by a trusted publisher, else, select No if there is no requirement.
- Run the script in a 64-bit PowerShell host: Select Yes to run the script in a 64-bit PowerShell host on a 64-bit client. Otherwise, select No (default) to run the script in a 32-bit PowerShell host.
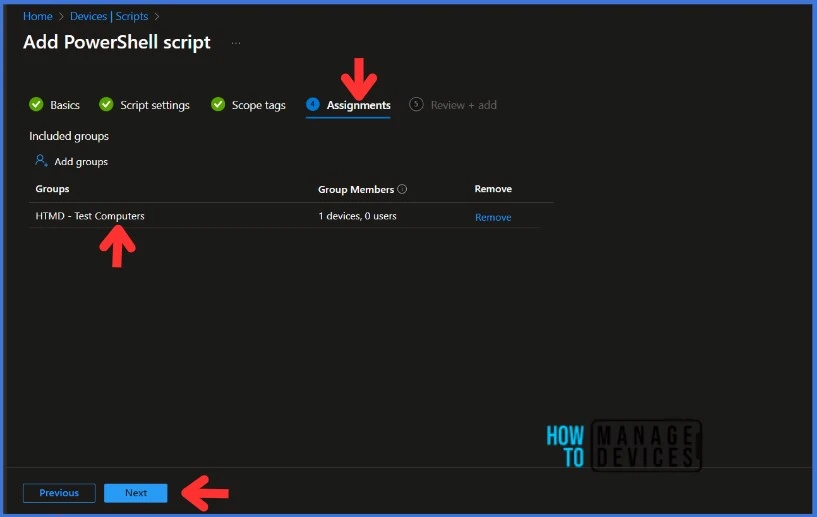
Click Next to display the Scope tags page. Add the Scope tags if you wish and click Next to assign the policy to computers. I will deploy it to the HTMD – Test Computers Group. Also, you can select multiple groups.
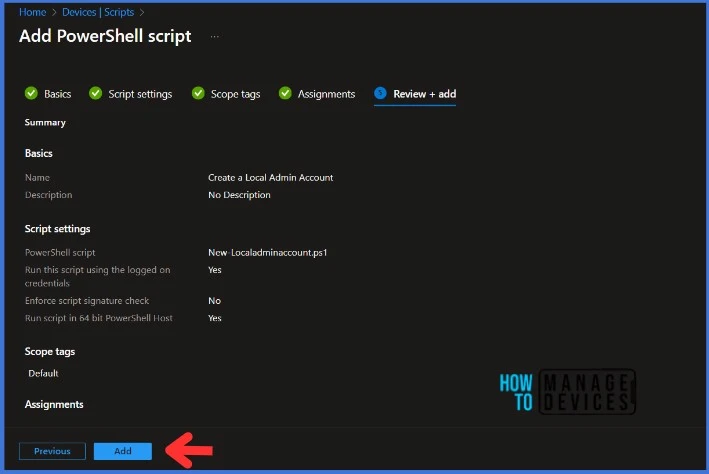
On the Review + Add page, carefully review all the settings that you have defined to Create a Local Admin Account. Once you have confirmed that everything is correct, select Add to implement the changes.
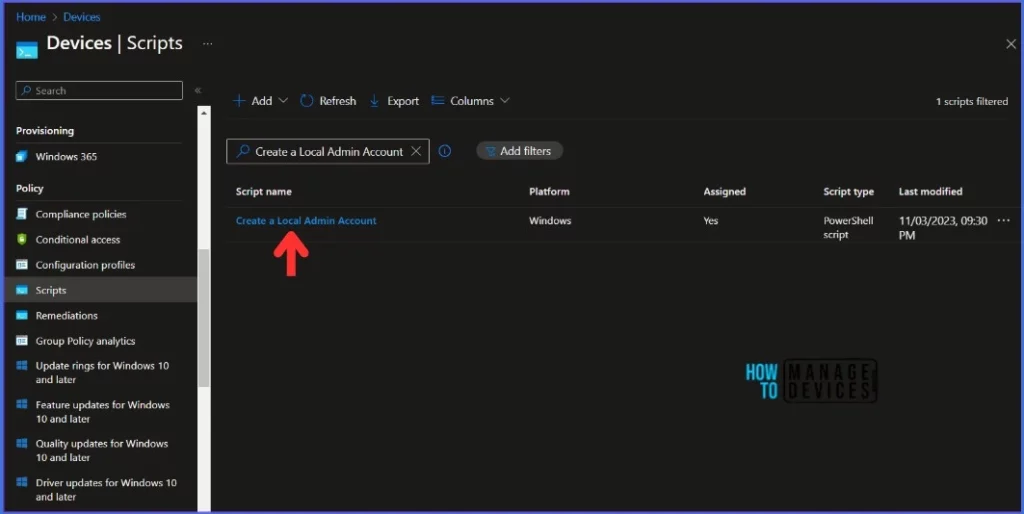
You can see the script which you just created in the Devices > Scripts section.
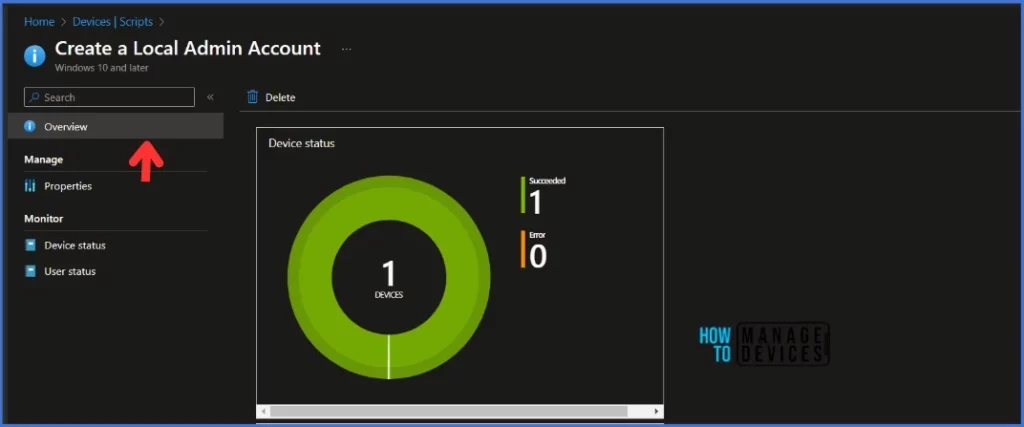
Monitor the Script Status in the Intune Portal
Let’s see how to monitor the run status of the PowerShell script. You can monitor the run status of the PowerShell scripts for users and devices in the Intune portal.
- Select the script which you just created under Devices > Scripts
- Check the device and user check-in status from here.
- If you click “Overview,” you can see additional details.
- You can also quickly check the update as devices/users check status reports.
Verify the Local Admin Account Created on the Workstation
As per the above report, the script that we developed to create a Local Admin Account is deployed to the workstation. Let’s verify it now.
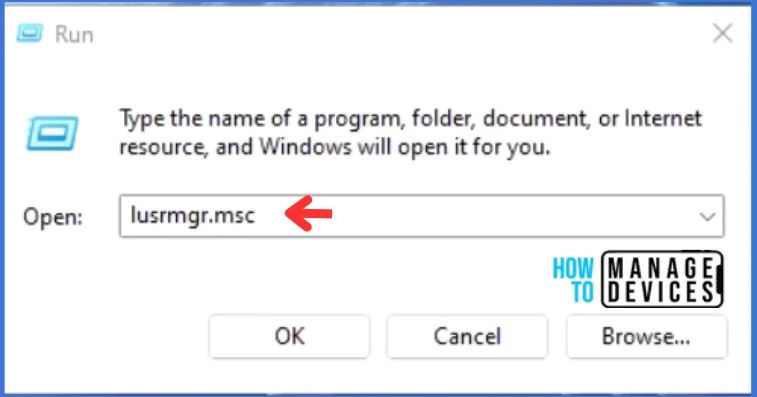
- Open the “Run” window with the Windows shortcut [Windows] + [R]. Type “lusrmgr.msc” and click OK.
- Go to Users in the Local Users and Groups menu on the left.
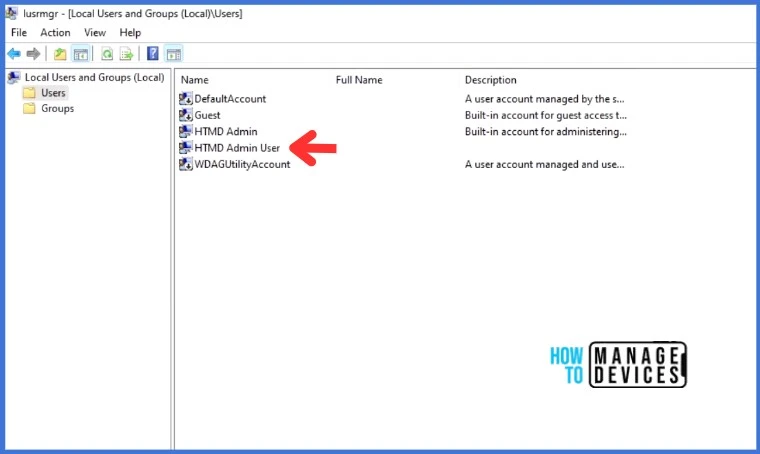
A new Local Admin Account HTMD Admin User is created. Go to Groups in the Local Users and Groups to verify whether HTMD Admin User is added to the Administrator group or not.
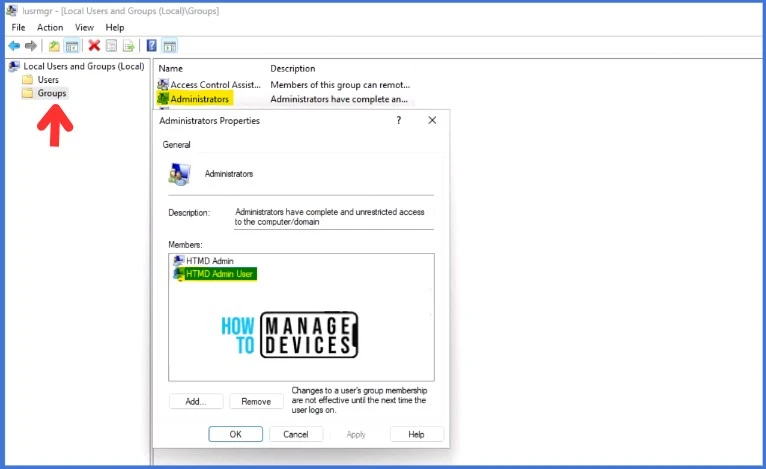
- Right-click on the properties of the Administrator group. This will open a new wizard. Next, you can verify if the newly created Local Admin Account has been added to the Administrator group or not.
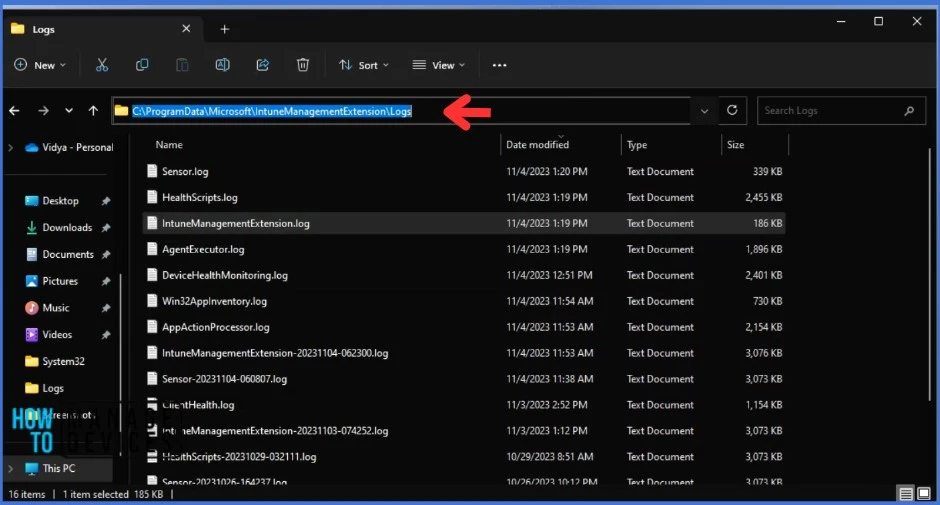
How to Check the Intune Management Extension Logs
The Intune management extension provides capabilities for Windows admins, including the ability to track and analyze logs related to the management add-on. The Intune Management Extension agent logs should be available under C:\ProgramData\Microsoft\IntuneManagementExtension\Logs on the client machine
You can refer to Intune Management Extension Deep Dive – Win32 App Deployment Troubleshooting Help Guide for more details.
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here – HTMD WhatsApp.
Thank you for your patience in reading this post. See you in the next post. Keep supporting the HTMD Community.
Author
About Author – Sujin Nelladath has over ten years of experience in SCCM device management and Automation solutions. He writes and shares his experiences with Microsoft device management technologies, Azure, and PowerShell automation.

Hey Sujin,
Powershell script giving an error message:
You cannot call a method on a null-valued expression.
At C:\temp\test.ps1:38 char:5
+ $existing.SetPassword($Password)
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (:) [], RuntimeException
+ FullyQualifiedErrorId : InvokeMethodOnNull
Hey, It appears that the $password variable is empty. Can you please double-check the code (refer to the script in the article) and try again?